Multiple Point Lightning Protection Accessories, Multiple Point, Electrolytic Co
We are a leading manufacturer, exporter and supplier of a wide range of Multiple Point Lightning Protection Accessories, Multiple Point, Electrolytic Copper Multiple Point, Earthing and Lightning Protection at very cheap prices for our clients from Mumbai, India.
1 views • 3 slides
Understanding AARCH64 Linux Kernel Memory Management
Explore the confidential and proprietary details of AARCH64 Linux kernel memory mapping, virtual memory layout, variable configurations, DDR memory layout, and memory allocation techniques. Get insights into the allocation of physically contiguous memory using Continuous Memory Allocator (CMA) integ
0 views • 18 slides
Understanding Single Entry System in Financial Accounting
Single Entry System is a simplified method used by small businesses to track their financial transactions. It lacks the rigor of double-entry bookkeeping and focuses on recording cash transactions and personal accounts. This system presents challenges in accurately determining profits and financial
0 views • 14 slides
Understanding Floating Point Representation of Numbers
Floating point representation is crucial in computer arithmetic operations. It involves expressing real numbers as a mantissa and an exponent to preserve significant digits and increase the range of values stored. This normalized floating point mode allows for efficient storage and manipulation of r
0 views • 12 slides
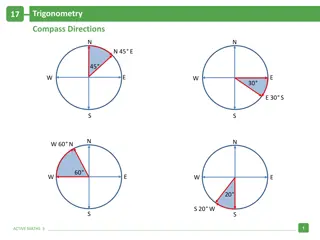
Trigonometry and Compass Directions Problem Solving
In this trigonometry problem, a ship travels from point A to point B and then to point C in specific directions. By applying the Pythagorean theorem, the distance from point C to A is calculated to be 7.2 km. The angle BCA is determined to be 34 degrees, and the direction of point C from A is found
0 views • 5 slides
Understanding Double Entry Accounting System in Finance
There are two commonly known systems of accounting - single entry system and double entry system. Double entry system is the basis of modern day accounting and ensures accuracy by recording every transaction with dual aspects of debit and credit. By maintaining personal and impersonal accounts, it h
1 views • 7 slides
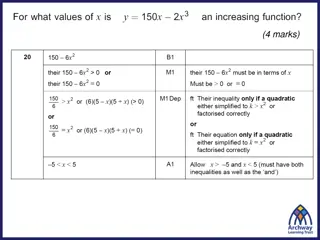
Understanding Points of Inflection in Calculus
Points of inflection in calculus refer to points where the curve changes from convex to concave or vice versa. These points are identified by observing changes in the curve's concavity, and they are not always stationary points. A stationary point can be a point of inflection, but not all points of
0 views • 14 slides
Understanding Generalized Discriminant Analysis (GDA) in Pattern Recognition
Generalized Discriminant Analysis (GDA) is a nonlinear form of Linear Discriminant Analysis (LDA) that utilizes kernel methods to find discriminatory features for optimal class separability. LDA aims to maximize the between-class covariance matrix while minimizing the within-class covariance matrix.
2 views • 17 slides
Understanding Entry and Exit Barriers in Industries
Entry and exit barriers play a significant role in shaping industry attractiveness and competitiveness. High entry barriers can deter new entrants, leading to stable returns but also higher risks. Conversely, low entry barriers may attract new players during economic upturns but result in intense ri
1 views • 15 slides
Optimizing User-Space Network Services with F-Stack and FreeBSD TCP/IP Stack
F-Stack, a user-space network service using DPDK and FreeBSD TCP/IP stack, addresses challenges in handling service traffic like CDN and live streaming. By leveraging 25GbE, 40GbE, and 100GbE NICs, coupled with multi-core CPUs and kernel bypass techniques, F-Stack overcomes bottlenecks between user
1 views • 17 slides
Understanding Kernel Tricks in Machine Learning
Kernel tricks in machine learning involve transforming inputs into higher-dimensional spaces to make linear models work for nonlinear data. Kernels can be applied to various algorithms like SVM, ridge regression, and more, allowing for better model performance with complex datasets.
0 views • 15 slides
Fundamentals of Operating Systems Explained
Explore the core concepts of operating systems, including kernel-userspace interactions, system calls, context switching, and virtual memory management. Delve into x86 assembly for system calls, hardware interrupts, and the flow of control during system call invocations. Gain insights into key compo
7 views • 19 slides
Understanding Floating Point Representation in Binary Systems
In computer systems, decimal numbers are represented in memory using scientific notation. This involves moving the decimal point and using mantissa and exponent to maintain precision and range. The transition to representing numbers in binary involves multiplying by 2 to the power instead of 10. Uti
2 views • 22 slides
Introduction to Floating Point Data Types and Operations
This content delves into the fundamentals of floating-point data types, focusing on single-precision floating-point formats like float, excess-127, and their characteristics. It also compares float and int32_t data types, detailing the representation and conversion of values between them. The materi
0 views • 46 slides
Understanding Colligative Properties in Solutions
Colligative properties in solutions depend on the total concentration of solute particles present, impacting properties such as boiling point elevation, freezing point depression, vapor pressure lowering, and osmotic pressure. Boiling point elevation is directly proportional to the number of solute
1 views • 19 slides
Impact of Rating-Based Platform Screening on New Complementor Entry
This study explores the effects of a platform design that ranks incumbent complementors based on review ratings on new complementor entry and overall complementor quality. The findings suggest that the rating-based platform screening reduces new complementor entry but enhances complementors' overall
1 views • 9 slides
Improving the Reliability of Commodity Operating Systems
This research paper discusses the challenges and solutions in enhancing the reliability of commodity operating systems by addressing system failures caused by kernel extensions. The Nooks approach isolates extensions within protection domains, allowing them to reside in the kernel address space with
0 views • 40 slides
Raspberry Pi 2 Boot Process Overview
Raspberry Pi 2's boot process involves a series of stages initiated by the GPU, loading essential firmware and enabling hardware components gradually, leading to the activation of the CPU and the kernel's entry point. The system transitions through various low-level processes before reaching a stabl
0 views • 9 slides
Understanding Entry and Exit Dynamics in Industries
Explore the fascinating world of entry and exit in industries, from the facts and barriers to Bain's typology of entry conditions and structural entry barriers. Learn about entry deterring strategies such as limit pricing, predatory pricing, and strategic bundling, and how they impact the market lan
0 views • 8 slides
Enhancing Civil Society Participation in TSD Chapters of EU PTAs through the Single Entry Point
The Single Entry Point (SEP) serves as a key mechanism for EU-based stakeholders to address violations in Trade and Sustainable Development (TSD) commitments. Through a centralized platform, stakeholders, including EU member states, NGOs, and citizen groups, can submit complaints regarding breaches
0 views • 10 slides
Multi-phase System Call Filtering for Container Security Enhancement
This tutorial discusses the importance of multi-phase system call filtering for reducing the attack surface of containers. It covers the benefits of containerization, OS virtualization, and the differences between OS and hardware virtualization. The tutorial emphasizes the need to reduce the kernel
0 views • 32 slides
Effective Strategies for Data Entry Integrity and Minimizing Errors
The chapter and subchapter discuss the importance of data integrity in the data management process, specifically focusing on data entry procedures, authenticity, and minimizing errors. It covers traditional manual data entry methods versus newer automated technologies, such as CAPI, and offers strat
0 views • 31 slides
Understanding User Mode, Kernel Mode, Interrupts, and System Calls in Computer Architecture
In modern computers following Von Newman Architecture, programs and data are stored in RAM. The CPU, RAM, ROM, and devices communicate via address and data buses. The system operates in both kernel and user modes, where kernel mode allows full system control, while user mode restricts access for sec
0 views • 29 slides
Understanding Freezing Point Depression and Molality for Solutions
Introduction to molality and freezing point depression in solutions. Molality is a way to measure solution concentration, calculated using moles of solute and kilograms of solvent. By calculating the moles of NaCl in a salt solution and the mass of the solvent (ice/water), the molality can be determ
0 views • 9 slides
Tracing Network Packets in Linux Kernel with eBPF
This presentation discusses the challenges of troubleshooting modern networking systems and proposes a solution using eBPF technology to trace the path of network packets in the Linux kernel. The goal is to develop a tool that provides detailed information about how network packets are processed in
0 views • 16 slides
Understanding Threats and Responses in the Mobile App Market
The study explores the impact of platform-owner entry on complementors in the mobile app market, examining evidence from platforms like Facebook, Uber, Android, Alibaba, iOS, and WeChat. Concerns from complementors about imitation by platform owners are discussed, along with views from platform owne
1 views • 19 slides
Nonparametric Tolerance Interval Approach to Immunogenicity Assay Cut Point Determination
This content discusses the importance of determining the cut point for immunogenicity assays to detect anti-drug antibodies (ADA) in large-molecule therapeutics. It highlights the need for well-developed and validated assays to ensure drug efficacy and safety. The approach involves multiple-tiered v
0 views • 26 slides
Insights on Entry and Exit Dynamics in Industries
Exploration of the entry and exit dynamics in industries, covering factors influencing the establishment of new firms, barriers to entry, Bain's typology of entry conditions, structural entry barriers, and entry-deterring strategies employed by incumbents. Insights include the impact on the market l
0 views • 7 slides
Analyzing Multimodality in Density Distributions Using JMP Scripting
Explore variability sources hidden in density distributions through JMP scripting. The analysis focuses on identifying and filtering distribution modes in semiconductor fab electrical measurements using kernel estimation and empirical rules. Antonio D'Angelo and Felice Russo from Lfoundry S.r.l. Ita
0 views • 6 slides
Understanding Remote Procedure Call (RPC) in Different Kernel Environments
Communication through Remote Procedure Call (RPC) plays a crucial role in facilitating seamless interaction between server and client processes, whether on the same machine or across different kernels. This technology streamlines local and cross-domain communication, optimizing performance while ens
0 views • 9 slides
Overview of the Pintos Instructional Operating System Kernel Project
Description of the Pintos Operating System Kernel project, including its use in educational settings at institutions such as Stanford University and Virginia Tech. The project aims to provide students with a hands-on experience in OS design, focusing on the internal workings of the kernel. Pintos fe
0 views • 33 slides
Understanding Pipes in Process Communication
Pipes in process communication allow for high-throughput data transfer between parent and child processes. The kernel creates a communication stream through file descriptors, enabling one process to send data to another. Processes can use pipes for efficient inter-process communication, with the ker
1 views • 15 slides
Understanding Floating Point Numbers in Computer Science
Exploring the concepts of floating point format, normalization, conversion processes, and IEEE 754 standard for representing floating point numbers in computer systems. Learn about two's complement, excessive notation, and the components that make up a floating point number. Dive into examples of co
0 views • 18 slides
Understanding User and Kernel Modes in Operating Systems
The content provided discusses various aspects of user and kernel modes in operating systems through a set of true/false questions related to user programs, CPU interrupts, heap management, and process behavior in different modes. It touches on the role of the kernel in managing virtual memory, hand
0 views • 10 slides
Hyper-Parameter Tuning for Graph Kernels via Multiple Kernel Learning
This research focuses on hyper-parameter tuning for graph kernels using Multiple Kernel Learning, emphasizing the importance of kernel methods in learning on structured data like graphs. It explores techniques applicable to various domains and discusses different graph kernels and their sub-structur
0 views • 20 slides
Overview of UNIX and Linux Operating Systems
The UNIX brand encompasses a range of powerful multitasking, multiuser operating systems used by various organizations to develop IT technologies. UNIX internals consist of kernel space and user space, with programs accessing system services rather than hardware directly. The Unix filesystem is a ke
0 views • 36 slides
BioLock Biometric Home Entry System Overview
BioLock is a biometric home entry system developed by Mavis Chan, Brent Erickson, and Sydney Bitner of Group 9. It features a fingerprint-enabled lock for secure home access, allowing homeowners to check access history remotely and receive alerts for unauthorized entry attempts. The system utilizes
0 views • 12 slides
Understanding Point-to-Point Protocol (PPP) and Serial Communications in WANs
This content explores the Point-to-Point Protocol (PPP), outlining its components, establishment of sessions, authentication protocols, and configuration. It also delves into WAN connection options, serial and parallel ports communication, and serial communication standards for LAN-to-WAN connection
0 views • 31 slides
Stress Ulcer Prophylaxis in ICU Data Entry System - SUP-ICU Overview
Dive into the Stress Ulcer Prophylaxis in the Intensive Care Unit (SUP-ICU) data entry system led by Dr. Soeren Marker Jensen. Explore screening, randomization, site overview, and data entry processes. Access participant details, edit submitted data, and learn about data entry guidelines. Enter the
0 views • 28 slides
Understanding Context Switching and User-Kernel Interaction in Operating Systems
Context switching in operating systems involves a seamless transition between user-level threads without the kernel's awareness. User-level code manages register state and stack pointers, while user-kernel mode switching requires changing processor privilege levels and agreement on information excha
0 views • 25 slides