Clean Energy Transition, Scarcity and Urban Mining
Explore strategies to sustain the clean energy transition amidst limited resources. Model a producer's decisions and regulatory alignment in maximizing clean energy generation with profitability considerations. Utilize benchmarks for material efficiency, urban mining, and systemic leakage to address
0 views • 23 slides
Semi-Supervised Credit Card Fraud Detection via Attribute-Driven Graph Representation
Explore a novel approach for detecting credit card fraud using a semi-supervised attribute-driven graph representation. The technique leverages temporal aggregation and attention layers to automatically unify heterogeneous categorical attributes and detect fraudulent transactions without label leaka
1 views • 23 slides
Carbon Pricing Overview and EU Green Deal Agenda
The overview of carbon pricing inside the EU highlights key aspects such as the EU Green Deal, revision of the EU ETS, and the Carbon Border Adjustment Mechanism. The EU aims for carbon neutrality by 2050 with a 55% reduction target. The Fit for 55 initiative emphasizes relevance for the Energy Comm
4 views • 16 slides
Do Input Gradients Highlight Discriminative Features?
Instance-specific explanations of model predictions through input gradients are explored in this study. The key contributions include a novel evaluation framework, DiffROAR, to assess the impact of input gradient magnitudes on predictions. The study challenges Assumption (A) and delves into feature
0 views • 32 slides
J S PLUMBING
In an ordinary house, where repairs and upgrades are needed, plumbing is among the most core issues. Water supply is a daily routine and essential for such things as plumbing and appliances like water heaters. Plumbing is responsible for the house's comfort and convenience. In the Cheyenne communit
1 views • 8 slides
Challenges and Opportunities in Township Economic Development
South African townships face significant challenges such as low investment, high levels of financial leakage, limited infrastructure, and high unemployment rates. Despite these obstacles, townships also serve as vibrant hubs of entrepreneurship with a variety of thriving activities. However, there i
0 views • 12 slides
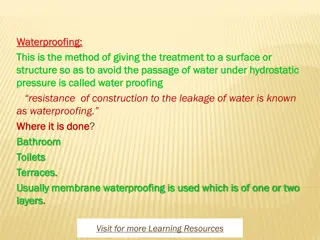
Understanding Waterproofing for Construction
Waterproofing is essential for preventing water leakage in structures like bathrooms, toilets, and terraces. It helps maintain a habitable environment, protect building components, and increase the building's lifespan. Causes of leaks include structural movement and temperature variations. Different
0 views • 6 slides
Efficient Operation and Maintenance of Evaporators in Dairy Industry
Learn about the operation and maintenance of evaporators in the dairy industry from Dr. J. Badshah's expertise. Discover key steps like preparation, leakage testing, energy-saving designs, and care tips for optimal performance. Understand factors affecting operations and design to enhance efficiency
1 views • 9 slides
Water Balance Calculations and Losses Analysis
Water balance calculations involve assessing commercial and physical losses in a water distribution system. The process includes basic calculations, evaluation of commercial losses such as metering inaccuracies and non-revenue water, as well as physical losses like leakage in transmission lines. Add
0 views • 21 slides
European Commission's Proposal for Carbon Border Adjustment Mechanism
The European Commission's proposal for a Carbon Border Adjustment Mechanism aims to address carbon leakage and reduce emissions through a comprehensive industrial policy known as the European Green Deal. The Fit For 55 Package under the EU Climate Law sets ambitious targets for emission reduction an
7 views • 8 slides
Proposed Relaxation of VHT LO Leakage Limits in IEEE 802.11-19/1561r4
VHT LO Leakage limits in the IEEE 802.11-19/1561r4 standard are deemed unrealistic under reduced TX power scenarios. This document proposes a relaxation of these limits under certain conditions, suggesting amendments for a more realistic approach to addressing LO leakage. The proposal aims to ensure
0 views • 13 slides
Comprehensive Guide to Transformer Buchholz Relay by Prof. V. G. Patel
Understanding the significance of Buchholz relay in protecting transformers from incipient faults that can develop into serious issues. Developed by Max Buchholz in 1921, this gas-operated device detects faults such as core insulation failure, short-circuited core laminations, and loss of oil due to
3 views • 14 slides
Memory Trace Oblivious Program Execution for Cloud Computing
This research delves into the intersection of programming languages, cryptography, and architecture to address privacy concerns in cloud computing. It discusses the risks posed by physical attacks on sensitive data and explores solutions like secure processors and Oblivious RAM to safeguard informat
2 views • 40 slides
Clinical Diagnosis and Assessment of Pre-Labour Rupture of the Membranes
Pre-Labour Rupture of the Membranes (RROM) is characterized by the leakage of amniotic fluid before the onset of labor, particularly when the gestational age is less than 37 weeks. Clinical diagnosis involves a thorough history evaluation and examination, including sterile speculum examination to co
0 views • 18 slides
Advancements in Active Secure Multiparty Computation (MPC)
Delve into the realm of secure multiparty computation under 1-bit leakage, exploring the intersection of DP algorithms, MPC, and the utilization of leakage for enhanced performance. Discover the overhead implications of achieving active security, as well as the evolution of secure computation protoc
0 views • 43 slides
Immobilization of Enzymes in Biochemistry
Enzyme immobilization involves confining enzyme molecules to a distinct phase from substrates and products, attaching them to solid matrices for enhanced specificity and reduced inhibition. Inert polymers or inorganic materials are used as carrier matrices with methods like physical adsorption onto
0 views • 24 slides
Secure Memory Encryption Techniques for Virtual Machines across Multiple Hosts
Virtual machines with large memory capacities are common in cloud environments. To enhance security during VM migrations and data transmissions, techniques like split migration, encrypted split migration, and encrypted remote paging are employed. However, challenges such as data leakage, high CPU ut
0 views • 16 slides
Understanding Schottky Diodes: Advantages and Disadvantages
Schottky diodes, similar to regular PN junction diodes, allow current to flow in one direction only. They are highly efficient and useful for switch mode power supplies, offering advantages such as fast switching action, high-frequency handling capability, low voltage drop, and higher efficiency. Ho
3 views • 5 slides
Enhancing NAND Flash Memory Lifetime Through Data Retention Optimization
Characterization, optimization, and recovery methods are explored to extend the lifespan of MLC NAND flash memory. Challenges such as high raw bit error rates and charge leakage leading to retention loss are addressed. Techniques like ECC and threshold voltage adjustment are employed to improve memo
0 views • 53 slides
Understanding Side Channels in Software Security
This content delves into the topic of side channels in software security, focusing on the leakage of sensitive information through timing side channels. It discusses the concept of covert channels, reference monitors, limitations of analysis, and prevention strategies to mitigate the risks associate
0 views • 25 slides
Energy Auditor & General Construction Learning Program
This specialized curriculum from the Weatherization Assistance Program covers essential topics for energy auditors and construction professionals working on single-family homes. Participants will learn about residential construction terminology, structural framing, different foundation types, air le
0 views • 33 slides
Energy Escaping Study in GRAiNITA Electromagnetic Calorimeter
Study by Denys Klekots focuses on analyzing energy escaping from the GRAiNITA electromagnetic calorimeter, using Geant4 simulations to investigate energy deposition, escaped energy fluctuations, and non-uniformity in the ECAL setup. The research delves into the impact of leakage and non-uniformity o
0 views • 10 slides
Analysis of ESEv3 in Comparison with PisaEcalBDT - Study and Findings
Our analysis compares PisaEcalBDT with ESEv3 in proton detection. The study evaluates various factors such as side leakage, shower axis direction, and potential corrections using a new function. Uncertainty in antiproton detection is discussed along with current studies' status and future plans for
1 views • 16 slides
Earth leakage Relay | Vteke.com.tr
VTEKE Elektrik'in g\u00fcvenilir ve verimli Toprak Ka\u00e7ak R\u00f6lesi ile end\u00fcstrinizi ve konutunuzu elektrik tehlikelerinden koruyun. G\u00fcvenlikten \u00f6d\u00fcn vermeyin; VTEKE Elektrik'i se\u00e7in.
6 views • 1 slides
Leakage-Resilient Key Exchange and Seed Extractors in Cryptography
This content discusses the concepts of leakage-resilient key exchange and seed extractors in cryptography, focusing on scenarios involving Alice, Bob, and Eve. It covers non-interactive key exchanges, passive adversaries, perfect randomness challenges, and leakage-resilient settings in symmetric-key
6 views • 35 slides
Real-time Monitoring and Detection of Android Privacy Leakage
PrivacyShield is a groundbreaking solution developed by Yan Chen's Lab at Northwestern University to address the critical issue of private data leakage from Android apps. Through extensive research and evaluations, they have identified vulnerabilities in popular anti-malware tools and uncovered alar
0 views • 19 slides
Slab Leak Repair in Orange County_ Why Early Detection Saves You Thousands
Slab leaks are one of the most damaging and costly plumbing problems that homeowners in Orange County may face. These leaks occur when the pipes beneath a concrete slab foundation start to deteriorate or develop cracks, leading to water leakage. Con
0 views • 5 slides
Overview of DARE22 Test Vehicle Design on FD SOI 22nm Process
This detailed presentation explores the test structures and components inside the TV, including combinatorial logic, sequential logic, clock gating, ring oscillators, input-output cells, analog IPs, and more. It covers various test scenarios such as irradiation testing, SET/SEU measurements, functio
1 views • 32 slides
Efficient and One-Pass Leakage-Resistant Modes of Operation: Triplex Design
Triplex design, a collaborative effort by Yaobin Shen and others from UCLouvain Crypto Group, presents an efficient and leakage-resistant mode of operation. The design focuses on improving performance, enhancing protection against side-channel attacks, and implementing DPA-protected KDF/TGF for subs
0 views • 16 slides
RF Leakage Investigations & Atomic Clock Signal Phase Drift Analysis
RF signals ranging from 100 kHz to 150 MHz are utilized for achieving resonance in optical cavities. DC Ground Isolation Units help decouple DC grounds and shield leakage. Spectrum analysis using RF analyzers reveals peaks possibly from neighboring balun leakages. Solutions involve increasing capaci
0 views • 14 slides
Understanding Information Leakage in Cloud Computing
Explore the threats of multi-tenancy in cloud computing, focusing on determining instance location, co-residency, and potential information exploitation. Research questions investigate these aspects using Amazon EC2 as a case study.
0 views • 28 slides
Enhancing Security of PLM and Supply Chain Data in Modern Enterprises
Modern enterprises rely on globally distributed supply chains and PLM systems to manage sensitive information, posing security challenges due to outsourcing and information flow complexities. Security threats such as data leakage can lead to financial losses, reputational damage, and criminal activi
0 views • 36 slides
Scatter-and-Gather Revisited: High-Performance Side-Channel-Resistant AES on GPUs
This research focuses on enhancing the security of AES encryption on GPUs by introducing the Scatter-and-Gather (SG) approach, aimed at achieving side-channel resistance and high performance. By reorganizing tables to prevent key-related information leakage, the SG approach offers a promising soluti
0 views • 34 slides
Operation and Maintenance of Multiple Effects Evaporators with TVR
Preparations required for the operation and maintenance of multiple effects evaporators include ensuring the availability of utilities like electricity, water, compressed air, and steam at the required pressure. Proper maintenance steps such as vacuum tests, checking for leakages, and conducting air
0 views • 14 slides
Importance of Security in Web Development
Our perception of security has evolved to acknowledge the presence of malicious actors and potential vulnerabilities in web applications. To write secure code, developers must assume the worst-case scenario and adopt a security mindset that trusts no one. Attackers have various goals, such as steali
0 views • 18 slides
Secure Out-of-Band Remote Management Using Encrypted Virtual Serial Consoles in IaaS Clouds
IaaS clouds provide virtual machines for users to manage through SSH. In scenarios where in-band remote management is not feasible, out-of-band remote management using Virtual Serial Consoles (VSC) offers a secure solution. However, challenges such as untrusted admins and potential attacks exist, wh
0 views • 22 slides
Cyber Security Engineering: Understanding the Importance and Examples
Cyber security is crucial due to the uncontrollable nature of digital devices and the potential for unauthorized access and manipulation, leading to severe consequences like data leakage, information distortion, and unauthorized access. Two examples illustrate the real-world implications of cyber th
0 views • 20 slides
Privacy Challenges in Online Social Networks
Online Social Networks (OSNs) like Facebook, Twitter, and LinkedIn have gained immense popularity with millions of users worldwide. However, these platforms present significant privacy issues, from protecting user data against unwanted exposure to the leakage of sensitive information. Challenges inc
0 views • 18 slides
Revenue Leakage in Air Cargo- How RTSCorp Helps Plug the Gaps
In the competitive world of logistics, air cargo remains a vital lifeline for global trade. However, with its complexities come challenges, and one of the most pressing issues is revenue leakage. Defined as the loss of potential earnings due to ineff
1 views • 5 slides
Partial Key Exposure Attacks on BIKE, Rainbow, and NTRU
Explore the vulnerability of PQC candidates to partial key exposure attacks in schemes like BIKE, Rainbow, and NTRU. Learn about leakage resistance, modeling leakage, practical bounds, and secret key decoding methods. Dive into the erasure and error models, analyzing the security of secret keys in v
0 views • 19 slides