Comprehensive Sexual Harassment Prevention Training Overview
This presentation provides a detailed overview of sexual harassment prevention training for employees, covering important topics such as recognizing sexual harassment, understanding company policies and procedures, and outlining employee responsibilities. It explains the different forms of sexual ha
3 views • 22 slides
Recognizing and Preventing Sexual Harassment: Supervisor Training Program
This sexual harassment prevention training for supervisors covers the importance of recognizing, responding to, and preventing sexual harassment in the workplace. It outlines what constitutes sexual harassment, the two forms of harassment (quid pro quo and hostile work environment), and the legal ob
1 views • 36 slides
Enhancing Cybersecurity with Bluedog VAPT Services
Bluedog Security Monitoring offers essential cybersecurity services, including Vulnerability Assessment and Penetration Testing (VAPT). Their automated VAPT combines External Vulnerability Scanning and WebApp Scanning to provide comprehensive testing solutions that help businesses prioritize risks,
0 views • 16 slides
Understanding Employment Discrimination and Retaliation Laws
This informative content delves into the nuances of employment discrimination and retaliation, outlining types of cases, stages of legal proceedings, protected classes under M.G.L. ch. 151B, elements of prima facie cases, and burden-shifting frameworks in proving discrimination or retaliation. It ex
2 views • 23 slides
Understanding the Basic Principles of Surveying for Building and Structural Projects
Surveying plays a crucial role in ensuring accurate positioning and alignment of structures such as buildings, bridges, and roads. This article delves into the definition of surveying, stages in the surveying process including reconnaissance, field work and measurement, and office work. Understandin
1 views • 60 slides
Understanding Illegal Harassment in the Workplace
In the workplace, illegal harassment goes beyond just sexual harassment. It includes unwelcome conduct based on various protected characteristics such as race, religion, age, disability, and more. This prevention training covers the definition of illegal harassment, its impact on work environments,
0 views • 27 slides
Convoy Commander Certification Program Overview
The Convoy Commander Certification Program introduces the agenda, requirements, duties, and responsibilities of convoy commanders in detail. It covers aspects such as conducting risk assessments, safe driving practices, operational hazards, and convoy planning procedures. The program emphasizes the
7 views • 35 slides
The Battle of Vimy Ridge in the First World War
The Battle of Vimy Ridge in 1917 was a significant event where all 4 Canadian Divisions joined forces, marking a historic victory and symbolizing the birth of Canada. The battle was a breakthrough for Britain and France, as Vimy Ridge was a crucial German stronghold that had resisted previous attack
9 views • 22 slides
Drone Detection Using mmWave Radar for Effective Surveillance
Utilizing mmWave radar technology for drone detection offers solutions to concerns such as surveillance, drug smuggling, hostile intent, and invasion of privacy. The compact and cost-effective mmWave radar systems enable efficient detection and classification of drones, including those with minimal
0 views • 8 slides
Insights into Application Security Testing and Best Practices
Dive into the world of application security testing with a seasoned practitioner's advice and musings. Explore the basics, types of testing, initial steps like reconnaissance, user inputs, test cases, attack strategies, and useful tools. Learn about code reading techniques and key hints for securing
0 views • 27 slides
Understanding Cold War Tensions: Causes, Events, and Decisions
Explore the complex dynamics of the Cold War era through a series of questions and analyses. Uncover the factors behind the hostile relations between the USA and the Soviet Union from 1945 to 1949, including the Berlin Blockade and key conferences like Yalta and Potsdam. Delve into the breakdown of
0 views • 33 slides
Chapter 5: Beast from the Water - Insights into Human Nature
In Chapter 5 of the book, "Lord of the Flies," Jack and Piggy hold contrasting beliefs about the existence of a beast on the island. While Jack is convinced there isn't a beast, Piggy suggests they should fear other things instead. William Golding's experiences and the characters in the story shed l
0 views • 9 slides
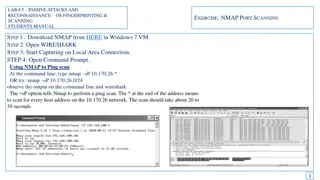
Passive Attacks and Reconnaissance using NMAP for Network Scanning
Learn how to use NMAP for passive attacks and reconnaissance through port scanning techniques like ping scan, TCP port scan, and stealth scan. Understand how to analyze the output in Wireshark to identify open ports and version numbers on target systems.
2 views • 7 slides
Passive Attacks and Reconnaissance in Network Security
Passive attacks involve monitoring target systems through port scanning or other means to locate vulnerabilities. Scanning is the first active action taken against a target network based on information gathered through footprinting, allowing deeper penetration. It includes scanning ports and service
0 views • 24 slides
Conflict Between Soul and Body in Andrew Marvell's Poem
Andrew Marvell's poem "A Dialogue Between the Soul and Body" depicts the ongoing conflict between the human Soul and Body. The Soul feels trapped within the Body, while the Body perceives the Soul as a tyrant imposing restrictions. This hostile debate sheds light on the deep dissatisfaction both ent
3 views • 20 slides
Understanding Force Protection and FPCON Levels in the US Military
Force Protection (FP) involves preventive measures in the US military to mitigate hostile actions. FPCON is a system to respond to terrorist threats against military facilities by determining security levels. FPCON levels vary from Normal to Delta based on the assessed threat level. The purpose of F
1 views • 13 slides
Understanding Aggression: Causes and Solutions
Aggression is any intentional behavior aimed at harming others, whether physically, verbally, or emotionally. It can be instrumental or hostile. Biological factors like hormones and neural substrates, social/cultural factors such as frustration and provocation, and environmental/situational factors
0 views • 10 slides
Nature as a Monster in Canadian Literature
Margaret Atwood, a renowned Canadian author, explores the theme of nature as a monster in Canadian literature. The prose delves into the changing perceptions of nature by poets over the centuries, from a kind mother figure to a hostile force. The discussion includes the different types of death port
1 views • 9 slides
Understanding Sexual Harassment in the Workplace
Sexual harassment is a prevalent issue at workplaces, with a significant percentage of women experiencing unwanted behaviors such as physical contact, stalking, and abusive communication. Despite this, many incidents go unreported due to fear of poor outcomes or worsened situations. It is crucial to
1 views • 30 slides
Understanding Triangulation Survey in Land Surveying
Triangulation survey is a method used to determine precise coordinates of fixed points in the field, especially in hilly areas. It involves establishing stations at reasonable distances apart to form a framework of triangles covering the entire survey area. Key operations include reconnaissance, ere
1 views • 20 slides
Understanding Sexual Harassment in the Workplace
Sexual harassment is a form of discrimination that is prohibited by laws such as Title VII of the Civil Rights Act of 1964. It includes any unwelcome sexual advances, requests for sexual favors, or other conduct of a sexual nature. An environment becomes hostile when the behavior is both viewed as a
0 views • 17 slides
Understanding Stress and Anxiety in Sports
Stress and anxiety play significant roles in sports performance. Stress can be positive (eustress) or negative (distress), affecting athletes differently. Common stressors in sports include playing through injury, competing in hostile environments, facing local rivals, and high-pressure match situat
0 views • 50 slides
Creating a Respectful and Inclusive Environment: Combating Harassment
Understanding sexual harassment, its impact on individuals, the importance of diversity and inclusion, and ways to proactively prevent harassment in lodge environments. Explore examples of hostile work environments, discrimination, and ways to differentiate between intent and impact in interactions
7 views • 14 slides
Challenges and Trends in Respectful Workplace Practices
Explore the dynamics of creating a respectful workplace, including defining characteristics, recognizing disrespectful behaviors, and promoting a culture of fairness, communication, and empowerment. Discover the importance of addressing biases, making sound judgments, and staying away from hostile e
0 views • 29 slides
Comprehensive Guide to Hacking Techniques & Intrusion Detection
This guide by Ali Al-Shemery provides insights into reconnaissance, intelligence gathering, target selection, and open-source intelligence for successful attacks. It covers the importance of OSINT, rules of engagement, and different forms of information gathering in the realm of cybersecurity.
2 views • 46 slides
Tactical Combat Casualty Care: Casualty Collection Point Operations
Learn about setting up and running casualty collection points (CCPs) in tactical field care, including key factors in selecting locations, responsibilities, and procedures for operating CCPs. Explore the correct procedures for managing wounded hostile combatants and the ongoing threats and care cons
0 views • 19 slides
Understanding Malware: Types, Usage, and Protection
Malware, short for malicious software, encompasses various forms of hostile software designed to disrupt computer operation, steal sensitive information, or gain unauthorized access. It includes viruses, trojan horses, worms, spyware, phishing, ransomware, and more. Malware is often used to steal pe
1 views • 49 slides
Sensor References and Procedures for NBCRV Operations
This document provides a detailed guide on sensor references, startup, and shutdown procedures for the Nuclear, Biological, and Chemical Reconnaissance Vehicle (NBCRV). It includes information on various sensors, deployment techniques, operating under different conditions, and mission planning consi
0 views • 25 slides
Wake Island: Strategic Importance and Military Defense in World War II
Wake Island, located in the Northern Pacific Ocean, played a crucial role in World War II as a strategic outpost for both the United States and Japan. The island's military significance was highlighted by its defensive capabilities, long-range reconnaissance opportunities, and potential for offensiv
0 views • 18 slides
Hostile M&A Tactics and Approaches in Investment Banking
Explore the world of hostile M&A tactics in investment banking, focusing on approaches used in public M&A situations. Learn about the pros and cons of hostile takeovers, including advantages such as seizing PR initiative and disadvantages like reputational damage. Dive into key steps and options in
0 views • 33 slides
Understanding Workplace Harassment and Prevention
Workplace harassment, a form of employment discrimination, violates various laws and creates hostile work environments. It includes unwelcome conduct based on protected characteristics and can be classified into different types such as sexual harassment, quid pro quo harassment, hostile work environ
0 views • 30 slides
Exploring Water on the Moon: Research Insights from Lunar Missions
Uncover the intriguing research on water presence on the Moon through the Lunar Reconnaissance Orbiter and the Lunar Exploration Neutron Detector. Discover how remote sensing and neutron detection technologies have shaped our understanding of lunar water distribution, challenging previous theories.
0 views • 23 slides
Employee Vigilance Campaign: Strengthening Security Awareness in the Workplace
This employee vigilance campaign emphasizes that security is everyone's responsibility. It aims to raise awareness about hostile reconnaissance, educate staff on identifying suspicious behavior, and promote a culture of vigilance. Through various mediums like briefings, posters, and reminders, the c
0 views • 7 slides
Understanding Reconnaissance in Cybersecurity: Methods and Techniques
Reconnaissance is a crucial initial step in cyber attacks, involving gathering information about targets through active or passive methods. Active reconnaissance techniques include host discovery, port scanning, service version detection, and OS fingerprinting. This process aids in identifying vulne
0 views • 14 slides
Selecting Landing Sites for Humans on Mars: HLS2 Study Update
The Human Landing Sites Study (HLS2) aims to identify suitable landing sites for human exploration on Mars, focusing on Exploration Zones (EZs) that meet scientific, engineering, and human criteria. Leveraging data from the Mars Reconnaissance Orbiter (MRO), the study establishes a database of high-
0 views • 15 slides
Fascinating Minecraft Facts and Survival Tips
Explore interesting facts about the creation of Minecraft in just 6 days by Markus Persson. Learn essential tips on surviving a night in Survival Mode, including distinguishing between hostile and non-hostile mobs, crafting recipes, finding resources, and why knowing your mobs is crucial. Delve into
0 views • 11 slides
Defensive Tactics Against Hostile Takeovers in Mergers and Acquisitions
Hostile takeovers in mergers and acquisitions involve one company acquiring another directly from shareholders without board approval. Tactics include tender offers, proxy fights, poison pills, crown jewels defense, golden parachutes, and Pac-Man defense to deter or resist takeovers.
0 views • 15 slides
Comprehensive Guide to Hacking Techniques and Intrusion Detection
This guide by Ali Al-Shemery provides insights into hacking techniques, intrusion detection, fingerprinting, external and internal footprinting, passive reconnaissance, WHOIS lookups, and various online tools for intelligence gathering during penetration tests. It covers identifying customer externa
0 views • 29 slides
Understanding Weak Points in Web Application Architecture
Information collected during the reconnaissance process can unveil critical aspects of a web application's architecture, including technologies used, API endpoints, functionality, domains, configurations, and authentication systems. Vulnerabilities in web applications often stem from poorly designed
4 views • 13 slides
Essential Steps in Attackers Incident Response Process
Explore the crucial phases of Attackers Incident Response, starting from Information Gathering to Post-Exploitation techniques. Learn about Passive and Active Reconnaissance, OSINT resources, DNS fundamentals, and Google Dorks for reconnaissance. Gain insights into gathering actionable intelligence
0 views • 29 slides