Adversarial Machine Learning in Cybersecurity: Challenges and Defenses
Adversarial Machine Learning (AML) plays a crucial role in cybersecurity as security analysts combat continually evolving attack strategies by malicious adversaries. ML models are increasingly utilized to address the complexity of cyber threats, yet they are susceptible to adversarial attacks. Inves
2 views • 46 slides
Understanding Bacterial Pathogenesis: Key Concepts and Factors
Bacterial pathogenesis involves the ability of certain bacteria to cause disease by attributes such as transmissibility, adherence, motility, invasion, and toxigenicity. Pathogens can exploit host defenses, while virulence determines the severity of infection. Learn about opportunistic pathogens, no
7 views • 36 slides
Understanding Host Bibliographic Records in Alma/Primo VE
Explore the concept of Host Bibliographic Records in the Alma/Primo VE system, which address the issue of linking single items to multiple bibliographic records. Learn how host bibs work, their creation during data migration, implications for library services, and the various types of host bibs used
0 views • 24 slides
Exploring Adversarial Machine Learning in Cybersecurity
Adversarial Machine Learning (AML) is a critical aspect of cybersecurity, addressing the complexity of evolving cyber threats. Security analysts and adversaries engage in a perpetual battle, with adversaries constantly innovating to evade defenses. Machine Learning models offer promise in combating
0 views • 43 slides
Mechanisms of Immune Evasion by Parasites in Immunoparasitology
Understanding how parasites evade the immune system of their hosts is crucial in the field of immunoparasitology. Parasites have developed various strategies such as anatomical seclusion, antigenic variation, and intracellular living to avoid host immune responses. Examples include Plasmodium within
0 views • 26 slides
Understanding Virus-Cell Interactions and Infections
Viral infections exhibit diverse cellular tropism based on receptor interactions, impacting cell function through modulation and potential host defense responses. Infections can lead to various outcomes, from cell death to persistent or latent states, with nuanced effects on cellular behavior. Diffe
0 views • 8 slides
Unified Volunteering Platform: Host Entity Account Management Training Update
Explore the recent updates in the Unified Volunteering Platform focusing on Host Entity account management training, webinars for UN Host Entities, and the launch of new self-service features. Learn about the roles within Host Entity accounts and the transition to the new system. Contact support for
0 views • 7 slides
Understanding Host-Parasite Relationship in Microbiology
In microbiology, the host-parasite relationship is crucial for understanding diseases caused by pathogens. This lecture covers definitions of terms like pathogenicity, pathogen, disease, resistance, susceptibility, infection, virulence, and transmissibility. It also delves into the division of host
0 views • 16 slides
Criticisms and Defenses of Verification and Falsification Principles
Explore the criticisms and defenses of the Verification and Falsification Principles in religious language. Understand how believers defend the use of religious language and analyze challenges posed to the Verification Principle by notable thinkers like Swinburne, Hare, and Mitchell. Delve into resp
2 views • 15 slides
Understanding the Normal Flora of the Gastrointestinal Tract and Infectious Diarrhea
Explore the common normal flora of the gastrointestinal tract (GIT) and how they play a role in health and disease, specifically focusing on infectious diarrhea. Learn about different types of acute diarrheal illnesses, epidemiology, host defenses against GI infections, and the pathogenesis of bacte
0 views • 38 slides
Understanding Host Stars and Their Importance in Exoplanet Research
Host stars play a crucial role in determining the physical parameters of planets they host, impacting exoplanet characterization and planet formation understanding. Data from astrometry, photometry, and spectroscopy, combined with stellar evolutionary models, help derive host star properties critica
0 views • 51 slides
Location Privacy Protection Strategies: A Comprehensive Overview
This study delves into optimal strategies to safeguard location privacy against localization attacks in the realm of location-based services. Discussing the shortcomings of anonymization and obfuscation as standalone defenses, it explores the challenges and pitfalls in designing effective protection
0 views • 26 slides
Exploring the Impact of Randomness on Planted 3-Coloring Models
In this study by Uriel Feige and Roee David from the Weizmann Institute, the effect of randomness on planted 3-coloring models is investigated. The research delves into the NP-hard nature of 3-coloring problems, introducing a hosted coloring framework that involves choices like the host graph and th
0 views • 55 slides
Buffer Overflow: Understanding, Defenses, and Detection
Dive into the world of buffer overflow attacks with insights on understanding the concept, implementing defenses, and detecting stack smashing using techniques like canary values. Discover how to protect against vulnerabilities and grasp the significance of elements such as EIP, ASLR, DEP, and NX bi
0 views • 10 slides
Protective Measures Against Stack Overflows
Host-based defenses such as Canaries, DEP, ASLR, and CFI play a crucial role in safeguarding systems against malicious attacks. Canaries act as early warning systems, alerting to stack overflows by monitoring changes in sensitive data. By implementing stack canaries, developers can prevent buffer ov
0 views • 51 slides
Understanding Control Hijacking Attacks and Defenses
Control hijacking attacks pose a significant threat by allowing malicious actors to manipulate data and control flow within a system. This article explores common attack methods like stack smashing and heap spraying, along with defenses such as fixing bugs, implementing platform defenses, and markin
1 views • 36 slides
Understanding Mechanisms of Viral Infection and Spread
Viral infection involves a replicative cycle within the host, leading to a range of cellular responses from no apparent effect to disease. Factors such as virulence genes, host characteristics, and viral genome influence the pathogenicity and virulence of a virus. The process includes entry into the
0 views • 16 slides
Land Tort Elements: Liability and Defenses
Key elements of tort law related to bringing onto land, foreseeability of mischief, requirement of escape, non-natural use, defenses like statutory authority and consent, as well as exemptions such as acts of God are explored through case law examples like Giles v. Walker and Rylands v. Fletcher.
0 views • 9 slides
Understanding Criminal Defenses and Legal Concepts
Explore the intricate realm of criminal defenses, from Mens Rea to Actus Reus, and delve into various defense strategies such as alibi, excuse defense, defense of self, property, and others. Uncover the nuances of legal concepts like infancy and not criminally responsible excuses in the context of c
3 views • 19 slides
Student Programmes Ireland Ltd: Providing Quality Secondary School Programmes in Ireland
Student Programmes Ireland Ltd is a renowned company with over 21 years of experience in organizing Secondary School Programmes in Ireland. They offer high-quality programs focused on studying English in a natural way, collaborating with international agencies and governments. The company selects sc
0 views • 31 slides
Understanding the Health Effects of Silica Exposure
Silica exposure poses serious health risks as respirable crystalline silica particles can penetrate the body's natural defenses, leading to conditions like silicosis, tuberculosis, lung cancer, and chronic bronchitis. The silica particles that bypass initial defenses can cause inflammation and fibro
0 views • 17 slides
Enhancing Server State Detection in OpenStack for Immediate Host Fault Reporting
This blueprint proposes the development of a new API in Nova to promptly update the server state in OpenStack when a host fault occurs. The intention is to ensure reliability and real-time updates of server and host states for Telco-grade VIM, allowing users to take necessary actions swiftly in case
0 views • 5 slides
Understanding Radiation Pressure Confinement in Quasars and Their Host Galaxies
Jonathan Stern's research explores the implications of radiation pressure confinement on the interaction between quasars and their host galaxies, focusing on photo-ionized gas systems. Through modeling and analyzing various properties of these systems, the study offers insights into quasar feedback
0 views • 35 slides
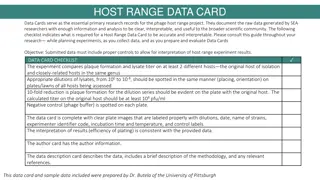
Guidelines for Host Range Data Card Creation in Phage Research
Essential checklist for creating accurate and interpretable Host Range Data Cards in phage host range projects, detailing required experiment components, controls, data documentation, and analysis. The provided checklist ensures the inclusion of necessary information and proper formatting for clear
0 views • 6 slides
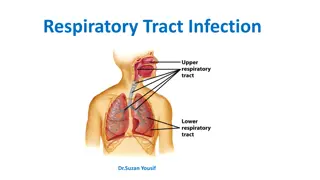
Understanding Respiratory Tract Infections: Causes and Prevention
Respiratory tract infections are commonly caused by viruses, bacteria, rickettsia, and fungi, leading to various health issues. These infections can be transmitted through droplets, droplet nuclei, and dust, emphasizing the importance of maintaining respiratory health through specific and non-specif
0 views • 34 slides
Security Issues in Parallel and Distributed Computing - Side Channel Attacks and Defenses
Explore various security threats in parallel and distributed computing, focusing on side channel attacks and defenses. Learn about microarchitecture, cache hierarchy, popular attacks, defense mechanisms, and more. Discover how hardware vulnerabilities can lead to the compromise of sensitive data and
1 views • 30 slides
Understanding the Complexities of Parasite Life Cycles and Host Interactions
Parasites exhibit diverse life cycles and behaviors, with cycles ranging from domestic to sylvatic environments. Factors influencing parasite diseases include host specificity, immunity, and host-parasite interactions. Parasitism can alter host behavior, impacting ecological dynamics. Immunology pla
0 views • 9 slides
Understanding the Immune System: Defenses Against Pathogens
Delve into the intricate workings of the immune system as it fights off pathogens to protect the body. Explore how external defenses like tears, saliva, and skin, along with internal defenses like inflammation and white blood cells, work together to maintain homeostasis and safeguard against sicknes
0 views • 21 slides
Eviction Mediation Training Updates and AB486 Overview
Explore the latest updates on eviction mediation training featuring AB486 and AB141. AB486 covers designated eviction proceedings, provides new affirmative defenses for tenants, and allows defenses to be raised at any time during the process. Learn about the impact of these changes on eviction cases
0 views • 25 slides
Illinois Accident Defenses and McAllister Decision Overview
Illinois accident defenses encompass fraud, occurring in the course of employment, and arising out of employment. Fraudulent claims often exhibit signs like delayed reporting and inconsistencies. Claims must be examined for their alignment with the context of employment. Illinois law requires a demo
0 views • 26 slides
Understanding Plant-Nematode Interaction: Defense Mechanisms and Parasitism
In the intricate relationship between plants and parasitic nematodes, plant defenses play a crucial role in combating biotrophic pathogens. The nematodes exploit various strategies to suppress these defenses and establish successful parasitism. The defense mechanisms of plants involve pre-existing b
0 views • 13 slides
Targeted Deanonymization via the Cache Side Channel: Attacks and Defenses
This presentation by Abdusamatov Somon explores targeted deanonymization through cache side-channel attacks, focusing on leaky resource attacks and cache-based side-channel attacks. It discusses the motivation behind these attacks, methods employed, potential defenses, and the evaluation of such att
0 views • 16 slides
Evaluating Adaptive Attacks on Adversarial Example Defenses
This content discusses the challenges in properly evaluating defenses against adversarial examples, highlighting the importance of adaptive evaluation methods. While consensus on strong evaluation standards is noted, many defenses are still found to be vulnerable. The work presents 13 case studies o
0 views • 9 slides
Analysis of CSRF Defenses in Web Frameworks
This study delves into CSRF attacks, a long-standing web vulnerability, and evaluates the effectiveness of CSRF defenses in popular web frameworks. It addresses the lack of knowledge about the security of CSRF defense implementations and their susceptibility to misuse, aiming to enhance understandin
0 views • 37 slides
Life Cycle of Ascaris lumbricoides in Human Host
Ascaris lumbricoides, commonly known as roundworm, is a human parasite found in the intestine. The life cycle involves copulation, egg development, and infection of a new host through ingestion of eggs. It does not require an intermediate host. The larval stages undergo migration within the body. Th
0 views • 14 slides
Immune Responses in Plants and Animals: A Comprehensive Overview
Plants and animals have evolved a variety of chemical defenses to combat infections and maintain homeostasis. Innate immunity provides immediate protection through barrier and internal defenses, while acquired immunity offers specific responses involving humoral and cell-mediated mechanisms. Plants
0 views • 26 slides
Understanding Acute Diarrheal Illness and Gastrointestinal Infections
Acute diarrheal illness is a common issue globally, leading to significant morbidity and mortality. This lecture covers the types of acute diarrhea, host defenses, pathogens like E. coli, Campylobacter, and Yersinia, and their management. It also discusses microbiological diagnosis methods, food poi
0 views • 30 slides
Understanding Parasitology: The Study of Organisms Living on or within Hosts
Parasitology is the study of parasites, which are organisms that live on or within a host and derive nutrients from them without benefiting the host. Parasites can be classified as ectoparasites or endoparasites based on their location in or on the host. Hosts play a crucial role in the life cycle o
0 views • 23 slides
Housing Court Advice Clinic Volunteer Training Highlights
Explore an insightful housing court advice clinic volunteer training program covering legal aspects of eviction laws, scenarios, court procedures, and defenses. Delve into topics like housing court basics, eviction reasons, defenses, important laws, rules, and grounds for eviction. Gain valuable adv
0 views • 36 slides
Formal Security Evaluation for Microarchitectural Modeling
This content discusses the challenges and defenses in evaluating formal security for microarchitectural modeling. It covers topics such as constant-time programs, speculative machines, post-quantum cryptography, side-channel attacks, and defense proposals against vulnerabilities like Spectre and Gho
0 views • 20 slides