Buckley & Surrounding Areas: 20mph Speed Limit Information Session
The information session covers the implementation of the Restricted Roads Order 2022 in Buckley and surrounding areas, introducing a 20mph speed limit. It includes details on the legislation, criteria, and place criteria for applying the new speed limits. Residents can provide feedback to help infor
1 views • 14 slides
Implementing Address Spaces: Base + Limit Registers
Address spaces, base + limit registers, and contiguous allocation are essential concepts in operating systems. Real mode memory addresses lack isolation between processes and pose limitations on multitasking. Virtual memory introduces virtual address spaces, requiring translation to physical address
3 views • 11 slides
Limit Test of Iron Based on Color Reaction with Thioglycollic Acid
The limit test for iron involves the reaction of iron in ammoniacal solution with citric acid and thioglycollic acid to form a reddish-purple color. By comparing the color produced with a standard solution, the presence of iron is determined. Citric acid prevents precipitation of iron, while thiogly
1 views • 5 slides
Wind Plant Telemetry and Web Services Issues Update
In early January 2023, certain wind plants experienced inaccuracies in their telemetry and web services data, impacting downstream processes. ISO Operating Procedure 14-F outlines requirements for wind plant telemetry, including Real Time High Operating Limit (RTHOL), Wind Plant Future Availability
0 views • 10 slides
Understanding Memory Management in Computer Systems
Explore Carnegie Mellon University's concepts on heap management and memory allocation strategies as detailed in "Computer Systems: A Programmer's Perspective." Dive into topics such as extending the heap, free blocks, and common problems with throughput and memory utilization.
0 views • 21 slides
Dunn County Board of Supervisors Proposed 2023 Budget Overview
Overview of the Dunn County Board of Supervisors Proposed 2023 Budget including details on County Levy Limit, Debt, General Fund Balance, Executive Committee's Directive, and Proposed Budget Summary. It discusses the Levy Limit increase and current debt status, General Fund Balance update, managemen
1 views • 9 slides
Understanding Heaps in Binary Trees
Heaps are binary trees that adhere to specific properties, such as being complete and satisfying the heap-order property. This involves nodes having keys smaller than or equal to their children. Key operations like removeMin and insert can be performed on heaps efficiently. Array implementations all
0 views • 10 slides
Understanding the Central Limit Theorem in Statistics
This lesson covers the Central Limit Theorem, which states that the sampling distribution of a sample mean becomes approximately normal as the sample size increases, regardless of the population distribution. It explains how the distribution of sample means changes shape and approaches a normal dist
0 views • 7 slides
Machine Learning Framework for Algo Trading in Limit Order Book Prediction
Explore the use of machine learning algorithms for predicting market trends in a limit order book setting. Financial exchanges rely on transparent systems like the Limit Order Book to match buy and sell orders efficiently. Researchers have delved into using deep learning and statistical methods to f
0 views • 16 slides
Runtime Checking of Expressive Heap Assertions
Motivated by the unreliability of large software systems due to concurrency bugs and limitations of static analysis, the goal is to enable runtime analysis of deep semantic properties with low overhead. This involves checking expressive heap assertions at runtime with minimal impact on performance,
0 views • 15 slides
Understanding the New SNAP Time Limit for ABAWDs: Webinar Overview
Explore the basics of the SNAP time limit rule for Able-Bodied Adults without Dependents (ABAWDs) in Pennsylvania, including exemptions, work/volunteer requirements, and ways to assist clients. Gain insights into the impact on vulnerable residents and learn about the key aspects of this federal rule
0 views • 34 slides
Data Structures and Heaps in Computer Science - Lecture 10 Overview
Explore the concept of heaps and heapsort in data structures, focusing on the binary heap data structure as an array object that resembles a nearly complete binary tree. Learn about binary tree representations, heap properties, and vertex assignments in a linear array to enhance search efficiency. U
1 views • 33 slides
Soft Heap and Soft Sequence Heaps: Properties and Applications
Explore the properties and applications of Soft Heap and Soft Sequence Heaps, discussing how corruption handling and selection functions are optimized in these data structures. The concept of car-pooling and the simplification of heap operations are highlighted, along with references to relevant res
1 views • 10 slides
Overview of Soft Sequence Heaps in Algorithms
Soft sequence heaps are a specialized data structure designed to handle corruptions in heap operations efficiently. This technology, introduced at Aarhus University, simplifies heap manipulation, particularly in car-pooling and other applications, with a focus on minimizing corruptions during extrac
0 views • 10 slides
Understanding Heap Sort in Data Structures
Heap Sort, a sorting algorithm based on the concept of a heap data structure, is explained in detail. The properties of a heap, its implementation using a complete binary tree, and its application in priority queues are discussed. The process of building a heap, inserting elements, and sorting them
0 views • 7 slides
Understanding Heap Overflows: An Introduction to Exploit Development
Learn about heap overflows in exploit development, including heap structure, memory maps, exploiting vulnerabilities, and controlling writes in the heap. Understand the difference between stack and heap, viewing heap in gdb, targeted exploit techniques, and the challenges of controlling EIP in the h
0 views • 17 slides
Understanding Priority Queues and Heap Data Structures
Priority queues play a key role in computer science algorithms by managing data based on priority levels. The use of heap data structures enhances the efficiency of priority queue operations. This tutorial covers the basics of priority queues, their applications, different implementations such as li
0 views • 30 slides
Abstract Domains for Lists and Heap Structures: A Comprehensive Overview
Explore the concepts of quantified data automata on skinny trees, automatic shapes in static analysis, universally quantified properties on lists, heap configurations with skinny trees, and the extension of quantified data automata over lists. Dive into the abstract domain of automata to capture inf
1 views • 20 slides
Heapsort and Heaps: A Generic Algorithm for Sorting
This content discusses the concept of heapsort and heaps in the context of sorting algorithms. It covers a generic algorithm for sorting a sequence of numbers in non-decreasing order, detailing different implementations and time requirements for inserting and removing elements from a set. A clever c
0 views • 50 slides
Understanding Heap Data Structure Implementation
Explore the implementation of a heap data structure through a complete binary tree concept, array representation, adding elements, removing elements, and avoiding swaps. Learn the steps involved in adding, removing, and organizing elements within a heap for efficient data storage and retrieval.
0 views • 17 slides
Understanding Heap Sort and Binary Search Tree Concepts
Learn about Heap Sort for sorting elements in ascending or descending order, Priority Queue as a data structure supporting key operations, Binary Trees with recursive definitions, and exercises involving priority queue operations. Explore the concepts through visual aids and examples provided in the
0 views • 18 slides
Understanding ACL Determination Steps for Fisheries Management
Learn about the key parameters involved in maintaining sustainable fishing practices, such as Maximum Sustainable Yield (MSY), Optimum Yield (OY), Overfishing Limit (OFL), Allowable Biological Catch (ABC), and Annual Catch Limit (ACL). Discover how these values are determined and the actions require
0 views • 15 slides
Understanding Heap Overflow Attacks
A heap is a collection of variable-size memory chunks managed by the program. Heap overflow attacks occur when malicious actors corrupt heap memory, potentially allowing them to overwrite data and execute arbitrary code. This poses a significant security risk. The process involves manipulating heap
2 views • 19 slides
Implementing Heaps: Node Operations and Runtime Analysis
Understanding the implementation of heaps involves knowing various node operations like finding the minimum node, last node, next open space, children, and parent. The runtime analysis of heap operations such as peekMin, removeMin, and insert are crucial for optimizing performance. This recap covers
0 views • 9 slides
Understanding Priority Queues and Heaps in CSE 373 Lecture
Today's lecture in CSE 373 covers the Priority Queue Abstract Data Type (ADT), the properties of heaps, and their implementations. Key topics include the completeness property of heaps, different priority queue implementations such as the binary search tree for faster insert and find operations, and
0 views • 21 slides
A Comparative Analysis of Heap Specification Approaches
This presentation discusses various approaches to heap specification, including ownership systems, dynamic frames, permissions, and capabilities. It explores challenges related to invariants and frames, showcasing examples from RockBand and Object state specifications. The discussion covers tools li
0 views • 11 slides
Understanding Memory Management Tradeoffs in Web Browsers
Explore the tradeoffs between memory usage, CPU cost, and performance in web browsers. Learn about setting heap limits, Pareto optimality, and compositional heap limit rules to optimize memory usage efficiently.
1 views • 18 slides
Binary Trees and Heap Implementation in Java
Explore the concepts of binary trees, heap implementation, and traversal techniques in Java through engaging peer instruction materials by Cynthia Lee. Learn about heap uniqueness, in-place heapsort, and generic binary trees. Test your knowledge with reading quizzes and analyze heap outcomes based o
0 views • 27 slides
Overview of SB 850 Homeless Emergency Aid Program (HEAP)
SB 850 establishes the Homeless Emergency Aid Program (HEAP) to provide flexible block grant funds to address immediate homelessness challenges in California. The program moves the Homeless Coordinating and Financing Council (HCFC) to the BCSH Agency and designates the BCSH Secretary as the HCFC Cha
0 views • 33 slides
Dynamic Memory Management Overview
Understanding dynamic memory management is crucial in programming to efficiently allocate and deallocate memory during runtime. The memory is divided into the stack and the heap, each serving specific purposes in storing local and dynamic data. Dynamic memory allocators organize the heap for efficie
0 views • 31 slides
Understanding Memory Management in C Programming
The discussion covers various aspects of memory management in C programming, including common memory problems and examples. It delves into memory regions, stack and heap management, and static data. The examples illustrate concepts like static storage, heap allocation, and common pitfalls to avoid.
0 views • 24 slides
Wind and Solar Energy Conversion Model Guidelines Consultation Update September 2016
Presented by Marcelle Gannon, this update covers the status of the consultation process, local limit and wind speed changes, extreme wind cut-out, possible power, estimated power proposal, and next steps. It provides insights into the current status of the consultation process, issues paper, draft r
0 views • 13 slides
Effectiveness of Lower BAC Limits in Reducing Impaired Driving
Lowering the BAC limit for driving to .05 has been shown to reduce impaired driving incidents significantly. Virtually everyone is impaired at .05 BAC, leading to a marked increase in crash risk. While most states adhere to the .08 BAC limit, some like Utah have already adopted the .05 limit. Even t
1 views • 21 slides
Role of Shale Gas in Annex 1 Climate Commitments
Shale gas, including natural gas, is not a low-carbon fuel according to Prof. Kevin Anderson and Dr. John Broderick from Tyndall Manchester. The International Energy Agency's view on climate change indicates a worrying trend towards a 3.5°C rise by 2040, with catastrophic consequences if not addres
0 views • 12 slides
Understanding Spinal Orthoses: Types, Uses, and Benefits
Spinal orthoses are back braces used to treat spinal disorders and injuries. They provide support, limit movement, and aid in healing. Orthoses are prescribed to realign the spine, immobilize it, limit mobility, and support weakened areas. Various types of orthoses are available based on the segment
0 views • 38 slides
CSE 545 Heap Challenges Overview
In CSE 545, students can expect a series of challenges related to heap exploitation techniques. The assignments involve releasing new challenges with specific deadlines and combining the points earned from previous challenges. The grading system is structured to allocate percentages to each assignme
0 views • 32 slides
Understanding CPU and RAM Relationship in Memory Segments
A program's address space consists of four segments - code, static data, stack, and heap. Each segment plays a crucial role in memory allocation and management. The OS and C++ runtime handle the allocation and deallocation of memory in the heap segment. Garbage collectors in certain languages aid in
0 views • 22 slides
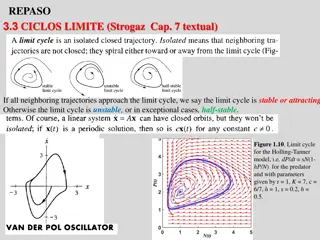
Understanding Limit Cycles and Bifurcations in Dynamical Systems
Explore the stability of limit cycles and bifurcations in dynamical systems through examples like the Holling-Tanner model. Discover the significance of stable limit cycles and the role of Liapunov functions in forbidding closed orbits. Delve into the intriguing behavior of trajectories in bottlenec
0 views • 16 slides
Understanding Heap Exploitation Techniques in CSE 545 Fall 2020
This collection of images covers various heap exploitation techniques discussed in CSE 545 Fall 2020, such as fastbin use-after-free vulnerabilities, tcache poisoning, double-free exploits, metadata manipulation, and more. The images depict scenarios involving tcache, fast bins, unsorted bins, and f
0 views • 72 slides
Understanding User and Kernel Modes in Operating Systems
The content provided discusses various aspects of user and kernel modes in operating systems through a set of true/false questions related to user programs, CPU interrupts, heap management, and process behavior in different modes. It touches on the role of the kernel in managing virtual memory, hand
0 views • 10 slides