Public key encryption, Digital signature and authentication
Understand the concept of public key encryption, asymmetric encryption, and the widely used RSA algorithm. Explore how public key cryptography revolutionized the field of encryption and its applications in confidentiality, authentication, and key distribution.
4 views • 12 slides
Unlock the full potential of Windows 10 with a best Genuine Activation Key
Unlocking the full potential of Windows 10 requires a genuine activation key that provides access to all the features and functionalities of the operating system. A genuine activation key not only ensures compliance with Microsoft's licensing terms but also guarantees security updates, technical sup
3 views • 8 slides
Common Issues and Solutions with Finding Office Product Key after Installation
Let's shout it from the rooftops people: The Office product key is SUPER important! It's like the golden key, the magic ticket, the secret code that unlocks everything fantastic about your Office software. Without your product key, you can say goodbye to accessing all the dazzling features of Word,
8 views • 9 slides
The Importance of Lifetime Validity for Your Windows Key
The importance of lifetime validity for your Windows key cannot be overstated. A lifetime validity ensures that you have uninterrupted access to the latest updates, features, and security patches for your operating system. It eliminates the worry of your key expiring or needing to renew it in the fu
0 views • 3 slides
How to Find and Update QuickBooks License Number And Product Key
Finding and updating your QuickBooks license number and product key is essential for maintaining legal use of the software and ensuring access to updates and support from Intuit. The license number and product key are unique identifiers that authenticate your copy of QuickBooks. This guide will walk
1 views • 5 slides
Understanding Security Threats and Public-Key Cryptosystems
Explore the world of security threats, passive and active attacks, and the importance of asymmetric encryption through the terminology related to asymmetric encryption, public-key cryptosystems, and public-key cryptography. Learn about the key components of public-key encryption schemes and the proc
0 views • 46 slides
Introduction to RSA Cryptography and Public Key Encryption
Explore the fundamentals of RSA cryptography and public key encryption, including shift ciphers and affine ciphers. Learn how public key encryption solves the challenges of implementing secure communication on a large scale. Discover the key components of RSA, its development history, and the mathem
2 views • 37 slides
Race Equality Data Metrics & Key Indicators in Workplace: An Anti-racism Toolkit
Race Equality Data Metrics & Key Data Indicators play a crucial role in assessing workplace race equality. Developed by Naveed Sharif, this toolkit provides 6 essential metrics focusing on leadership, recruitment, and formal workplace processes. The toolkit aims to address disparities and promote eq
2 views • 11 slides
Understanding Keys and SQL Commands in Database Management Systems
Explore different types of keys used in databases such as Candidate Key, Super Key, Composite Key, Primary Key, Alternate Key, Unique Key, and Foreign Key. Learn about SQL commands categorized into DDL, DML, and DCL and various query languages like Create, Alter, Rename, Drop, Comment, Truncate, Ins
0 views • 11 slides
Key Management and Distribution Techniques in Cryptography
In the realm of cryptography, effective key management and distribution are crucial for secure data exchange. This involves methods such as symmetric key distribution using symmetric or asymmetric encryption, as well as the distribution of public keys. The process typically includes establishing uni
1 views • 27 slides
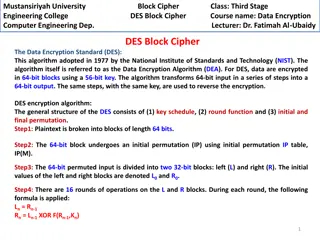
Understanding DES Block Cipher in Computer Engineering at Mustansiriyah University
Data Encryption Standard (DES) is a widely used algorithm for encrypting data in 64-bit blocks with a 56-bit key. This course at Mustansiriyah University covers the key components of DES, including the key schedule, round function, and initial/final permutation. Students learn about the encryption p
1 views • 8 slides
Introduction to Public Key Cryptography
Public key cryptography, exemplified by algorithms like Diffie-Hellman and RSA, revolutionizes secure communication by allowing users to encrypt messages with public keys known to all and decrypt them with private keys known only to the intended recipient. This advanced encryption method ensures sec
1 views • 44 slides
Understanding Diffie-Hellman Key Exchange Algorithm
The Diffie-Hellman key exchange algorithm, a pioneering public-key cryptography method introduced by Diffie and Hellman in 1976, enables secure key exchange between two users to facilitate subsequent message encryption. The algorithm relies on the complexity of computing discrete logarithms and invo
0 views • 24 slides
RSA Algorithm in Public-Key Cryptography
The RSA algorithm is a crucial public key cryptography method used for key exchange, digital signatures, and data encryption. It involves generating public-private key pairs using prime numbers, encryption with the public key, and decryption with the private key. The algorithm's strength lies in the
0 views • 5 slides
Effective PowerPoint Presentation Essentials
Learn key takeaways for creating impactful presentations: visualize key points, pay attention to design, highlight key information, and use keyboard shortcuts for efficiency. Enhance slides with principles like focusing on key messages and selecting appropriate evidence. Follow design steps to tailo
0 views • 6 slides
Best Car key replacements in Pendleton
Are you looking for the Best Car key replacements in Pendleton? Then contact EAM Diagnostics Ltd. They specialises in auto key programming services should be able to help. Lucky for you, no one can offer you key programming services faster or more re
0 views • 6 slides
Understanding Symmetric Key Block Ciphers - Overview and Implementation
Delve into the world of symmetric key block ciphers through a detailed exploration of classical ciphers like substitution and transposition, modern cryptography advancements, DES encryption, Simplified DES, key scheduling, expansion functions, S-Box usage, and more. Discover the intricacies of encry
0 views • 40 slides
Understanding Public-Key Cryptography and Its Applications
Public-Key Cryptography revolutionized secure communication by introducing the concept of using separate keys for encryption and decryption. Initially explored by researchers like Diffie, Hellman, and Merkle in the 70s, it addressed key distribution challenges faced by symmetric cryptography. This m
0 views • 34 slides
Leakage-Resilient Key Exchange and Seed Extractors in Cryptography
This content discusses the concepts of leakage-resilient key exchange and seed extractors in cryptography, focusing on scenarios involving Alice, Bob, and Eve. It covers non-interactive key exchanges, passive adversaries, perfect randomness challenges, and leakage-resilient settings in symmetric-key
6 views • 35 slides
Understanding Methodological Choice and Key Categories Analysis in Greenhouse Gas Inventory Management
Methodological choice and key categories analysis play a crucial role in managing uncertainties in greenhouse gas inventories. By prioritizing key categories and applying rigorous methods where necessary, countries can improve the accuracy and reliability of their emissions estimates. Key categories
0 views • 24 slides
Gender Pay Gap Analysis in Jordan: Trends and Sector Disparities
This paper delves into the gender pay gap (GPG) in Jordan, analyzing data from the 2011 Employment and Compensations survey. It explores the factors contributing to the GPG within various sectors and occupations, emphasizing the persistent structural issue despite some narrowing over the years. The
2 views • 11 slides
Protecting Your Business with Key Person Cover from Fidelity Life
Key Person Cover from Fidelity Life provides financial protection for businesses by helping replace key staff members unable to work due to sickness or injury. Established businesses and newly self-employed individuals can benefit from this cover, with options for benefit amounts, waiting periods, a
0 views • 12 slides
Understanding the Origins of Abrahamic Faiths
Explore the key concepts and knowledge related to the origins of Judaism, Christianity, and Islam through tasks focusing on key words, key knowledge outcomes, and comprehension of Genesis. Topics covered include the common founder, key events, beliefs, and influences of these faiths.
0 views • 38 slides
Enhancing Biological Context Annotation for AOPs: A Comprehensive Approach
Manual creation and homogenization of biological context annotations for AOPs and key events help in interlinking different AOPs to understand possible connections between pathways. The process involves compiling AOPs for various organisms, including humans and model species, annotating key events w
0 views • 13 slides
Key Principles in Cryptography: Kerckhoff's and Key Space
Understanding fundamental principles in cryptography, including Kerckhoff's principle, key space requirements, and the importance of secure private-key encryption. Exploring the Shift Cipher's security, key space size considerations, and the need for heuristic constructions for proving scheme securi
0 views • 51 slides
Understanding Public Key Cryptosystems in RSA Encryption
Public key cryptosystems, like RSA, use two keys for encryption and decryption, with one key made public and the other kept secret. This asymmetric system allows secure communication, where the encryption key (E) is used to encrypt messages into ciphertext (C), which can only be decrypted back to th
0 views • 11 slides
Secure Key Distribution Methods in Public Key Infrastructure
Explore the various methods of secure key distribution in Public Key Infrastructure, including the use of signatures, certificate authorities, roots of trust, and the web of trust. Understand how Bob can securely obtain public keys and certificates to establish trust in the system.
0 views • 11 slides
Key Access Services Audit Process Overview
This document provides a detailed guide on the Key Access Services Audit Process, including key steps for certifying signatories, assigning Key Auditors, and completing Key Audits. It covers processes for assigning auditors to departments, completing audits, and verifying audit results. Instructions
1 views • 14 slides
Key Distribution and Management in Cryptography
This presentation discusses key distribution and management in cryptography, covering symmetric and asymmetric key cryptography, methods for sharing symmetric and public keys, as well as key distribution techniques such as manual delivery, initial key distributions, and the use of trusted third part
0 views • 30 slides
Understanding Python Dictionaries: Key-Value Mapping
Python dictionaries are key-value mappings where elements are stored as key-value pairs instead of being indexed by numbers like in sequences. Dictionaries allow unique keys and provide efficient ways to create, access, and update key-value pairs in Python programming. Learn how to utilize dictionar
0 views • 10 slides
Key Driver Diagrams in Continuous Quality Improvement
Key Driver Diagrams are essential tools in Continuous Quality Improvement (CQI) to help organizations achieve their goals by identifying key drivers and their relationships. These diagrams aid in understanding complex systems, setting SMART aims, and implementing effective change strategies. Through
0 views • 24 slides
Understanding Public Key Cryptography in Network Security
Explore the concepts of public key cryptography, key distribution challenges, solutions to secret key schemes, and the importance of secure communication in network security. Learn about cryptology, cryptography, cryptanalysis, block ciphers, stream ciphers, and more in this informative content.
0 views • 21 slides
Enhancing Cryptographic Key Generation with High-Quality Randomness
This presentation discusses the critical aspect of ensuring high-quality randomness in cryptographic key generation processes. It explores key vulnerabilities and common failure modes, emphasizing the importance of incorporating strong randomness. The content delves into various methods and issues r
0 views • 45 slides
Quantum Key Agreements and Random Oracles
This academic paper explores the impossibility of achieving key agreements using quantum random oracles, discussing the challenges and limitations in quantum communication, cryptographic protocols, quantum computation, and classical communication. The study delves into the implications of quantum ra
0 views • 29 slides
HIV/AIDS Update in Latin America: Trends and Key Findings
This update provides insights into the HIV/AIDS situation in Latin America from 2000 to 2018, covering aspects such as new infections, AIDS-related deaths, incidence-prevalence ratio, and key population demographics. The data reflects changes in policies, prevalence among key populations like sex wo
0 views • 17 slides
Armando Fox - Computer Science Faculty at UC Berkeley
Armando Fox, a prominent Computer Science professor at UC Berkeley, provides contact information, office details, and GPG key ID for secure communication. He offers advice on designing business cards and maintaining GPG key integrity for digital security.
0 views • 5 slides
Understanding Gender Pay Gap Report at Abbeycroft Leisure
Gender Pay Gap (GPG) Report at Abbeycroft Leisure reveals a mean gender pay gap of -13.52% and a median gap of -3.81%. While women earned more on average than men, there was no bonus gender pay gap due to no bonuses paid in the relevant period. The composition of the workforce, bonus gender pay gaps
0 views • 7 slides
Key Exchange and Public-Key Cryptography Overview
Explore the challenges of key management, the use of trusted third parties in generating shared keys, the limitations of toy protocols in secure key exchange, and the evolution of public-key cryptography techniques like Merkle Puzzles, Diffie-Hellman, and RSA. Learn how to achieve secure key exchang
0 views • 36 slides
Understanding Cryptographic Protocols and Key Exchange
This content delves into the world of cryptographic protocols, discussing the importance of security measures such as symmetric cryptography, hash functions, and public-key cryptography. It explores the field's various studies, goals, Diffie-Hellman key exchange, and the significance of key size in
0 views • 28 slides
Advances in Functional Encryption for Secure Data Handling
Explore the evolution from Cryptomania to Obfustopia through Secret-Key Functional Encryption, Public-Key Encryption, and the power of Secret-Key Functional Encryption. Discover the significance of different encryption schemes such as Public-Key Functional Encryption, Secret-Key Functional Encryptio
0 views • 36 slides