Structural Design Using Finite Elements - Introduction to Safety Margins
In the field of structural design using finite elements, understanding safety margins is crucial. Factors of safety, response vs. capacity, sufficiency factors, and excess capacity are explained to ensure structural integrity and performance optimization.
1 views • 36 slides
Computability: Exploring Theoretical Limits of Computation
Delve into computability theory, focusing on what is computable and the limits of computation. Explore concepts like Rice's Theorem, the Halting Problem, and classes of expressiveness in computability theory, such as combinational logic, finite-state machines, pushdown automata, and Turing machines.
5 views • 43 slides
Introduction to Regular Expressions and Equivalence to Finite Automata
Regular expressions (REs) are used to describe languages by algebra and are equivalent to finite automata. They define regular languages precisely using operations like union, concatenation, and Kleene star. The concatenation of languages combines strings from two languages, while the Kleene star re
9 views • 106 slides
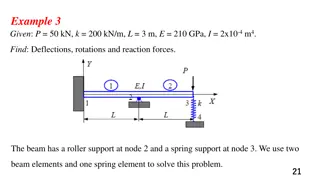
Engineering Beam Analysis using Finite Element Method
Solve beam analysis problems involving deflections, rotations, and reaction forces using the finite element method. The examples provided cover scenarios with roller supports, spring supports, and internal hinges. Learn how to determine displacements, rotations, and element forces in beams of varyin
2 views • 42 slides
Enhanced Security in Multiparty Computation
Explore the improved black-box constructions of composable secure computation, focusing on definitions, objectives, and the formalization basics of multiparty computation (MPC). Learn about the motivating security aspects in MPC and the real/ideal paradigm. Discover how MPC security involves compari
1 views • 68 slides
Enhancing Finite Element Analysis with Overlapping Finite Elements in Julia
Finite Element Methods (FEM) play a crucial role in solving complex PDEs in various domains. Overlapping Finite Elements in Julia aim to minimize reliance on mesh quality, improving solution accuracy. By leveraging Julia's matrix capabilities and efficient implementations, users can achieve faster c
1 views • 19 slides
Secure Computation Techniques in RAM Models with Efficient Automation
Explore the automation of efficient RAM-model secure computation techniques, including examples such as secure binary search. Discover how traditional solutions using circuit abstractions can be improved for sub-linear time computation through methods like Oblivious RAM. Learn about techniques such
0 views • 37 slides
Introduction to Digital Filter Design in Signal Processing
Discrete time filters play a crucial role in signal processing, with finite impulse response (FIR) and infinite impulse response (IIR) systems being two key types. FIR filters have finite duration unit sample responses, while IIR filters have infinite duration responses. FIR filters are implemented
1 views • 12 slides
Equivalence of Regular Expressions and Finite Automata
Regular expressions are an algebraic method to describe languages, specifically the regular languages. They are defined recursively based on symbols and operations such as concatenation and closure. Precedence rules and examples are also provided. The equivalence between regular expressions and fini
1 views • 25 slides
Secure Multiparty Computation for Department of Education Data Sharing
This report discusses the use of Secure Multiparty Computation (SMC) to enable sharing of sensitive Department of Education data across organizational boundaries. The application of SMC allows for joint computation while keeping individual data encrypted, ensuring privacy and security within the Nat
0 views • 15 slides
Advancements in Active Secure Multiparty Computation (MPC)
Delve into the realm of secure multiparty computation under 1-bit leakage, exploring the intersection of DP algorithms, MPC, and the utilization of leakage for enhanced performance. Discover the overhead implications of achieving active security, as well as the evolution of secure computation protoc
0 views • 43 slides
Chapter 5: Filter Implementation and Finite Word-Length Problem Overview
This chapter delves into the implementation challenges of digital filters, particularly focusing on the finite word-length problem. It discusses issues such as coefficient quantization, arithmetic operations, quantization noise, statistical analysis, limit cycles, and scaling. Various realizations a
1 views • 32 slides
COMET: Code Offload by Migrating Execution - OSDI'12 Summary
The research paper discusses COMET, a system for transparently offloading computation from mobile devices to network resources to improve performance. It outlines the goals of COMET, its design, and evaluation, focusing on distributed shared memory and bridging computation disparity through offloadi
0 views • 31 slides
Actively Secure Arithmetic Computation and VOLE Study
Exploring actively secure arithmetic computation and VOLE with constant computational overhead at Tel Aviv University. Understanding how functions are represented in secure computation using arithmetic circuits over boolean circuits. Efficiently evaluating arithmetic circuits over large finite field
0 views • 36 slides
Enhancing Multi-Party Computation Efficiency Through ORAM Techniques
Explore the realm of efficient random access in multi-party computation through the reevaluation of classic schemes and the introduction of new approaches. Discover the potential of ORAM in improving performance and reducing costs in various computational tasks, such as secure multi-party computatio
0 views • 22 slides
Finite Automata and Regular Functions in Computer Science
Exploring the concepts of regular functions, languages vs functions, finite-state computation, finite automata with cost labels, finite automata with cost registers, and examples of Cost Register Automata. These topics delve into the theoretical and practical aspects of defining functions and comput
1 views • 46 slides
Finite and Non-finite Verbs in English Grammar
Explore the concept of finite and non-finite verbs through examples and explanations. Learn to identify different types of verbs, their relationship with subjects and tenses, and how they function in sentences. Enhance your understanding of English grammar with practical insights and tips provided i
1 views • 19 slides
Basic Concepts in Number Theory and Finite Fields for Cryptography
In this presentation, the basic concepts of number theory, including divisors, properties of divisibility, the division algorithm, and the greatest common divisor (GCD), are explored in the context of cryptography and network security. The importance of finite fields in cryptographic operations such
0 views • 38 slides
Finite Element Analysis Using Abaqus: Basics and Methods
Learn about the basics and methods of Finite Element Analysis using Abaqus. Explore topics such as preprocessing, interactive mode, analysis input files, components modeling, FEM modeling, and more. Understand the advantages and disadvantages of using GUI versus Python scripting, and how to create F
0 views • 33 slides
Secure Computation in the Age of Information
Welcome to Secure Computation Lecture 1 by Arpita Patra. The course covers evaluation policies, projects, and references in the realm of secure computation. The content delves into the significance of information security across various sectors, emphasizing the importance of safeguarding sensitive d
0 views • 36 slides
Finite State Machines in Computing
Discover the world of Finite State Machines (FSMs) in computing through images and explanations. Learn about base elements, software complexity, DFA terminology, high reliability proofs, and practical examples like the Fox Chicken Grain Problem. Dive into FSM specifications and explore Java code gen
0 views • 18 slides
Finite and Non-Finite Verbs in English Grammar
This content introduces the concept of finite and non-finite verbs in English grammar through examples and explanations. It covers the definitions, identification, and usage of finite and non-finite verbs, with practical examples provided for better understanding. The tips mentioned help in distingu
4 views • 20 slides
Secure Two-Party Computation and Basic Secret-Sharing Concepts
In today's lecture of "Foundations of Cryptography," the focus is on secure two-party and multi-party computation, emphasizing semi-honest security where Alice and Bob must compute without revealing more than necessary. Concepts such as real-world vs. ideal-world scenarios, the existence of PPT simu
0 views • 27 slides
Linear Communication in Secure Multiparty Computation for Efficient and Fast Processing
The research focuses on achieving perfectly secure multiparty computation (MPC) with linear communication and constant expected time. It explores efficient approaches using a broadcast-hybrid model and P2P communication, aiming to balance speed and efficiency in MPC. The study highlights the importa
0 views • 23 slides
Finite State Machines in Digital Logic Design
Finite state machines play a crucial role in digital logic systems, allowing for the implementation of sequential circuit designs. These machines consist of states and transition functions, determining system behavior based on inputs and current state. The output function generates outputs based on
0 views • 35 slides
Data-Parallel Finite-State Machines: A Breakthrough Approach
This research discusses a new method for breaking data dependencies in data-parallel finite-state machines. It highlights the importance of FSMs in various algorithms and the need for parallel versions in processing large data sets. The study explores breaking data dependences with enumeration and t
0 views • 19 slides
Secure Computation Challenges and Solutions in Data Mining
Exploring the intersection of secure computation and data mining, this content uncovers key challenges such as improving algorithms, converting programs for secure computation, and addressing parallelizability issues. It highlights the importance of cryptography in ensuring data privacy and presents
0 views • 30 slides
Covert Computation: Ensuring Undetectable Engagement
Covert computation aims to conceal the fact that computation is occurring and hide engagement in certain tasks like secure computation, authenticated key exchange, and more. By making messages indistinguishable and utilizing steganographic channels, it becomes possible to keep the activities covert
0 views • 16 slides
Overview of Turing Machines: Introduction, Tape, and Computation
Turing Machines are fundamental in the theory of computation, capable of recognizing all computable languages. They consist of a Finite State Machine combined with an infinite tape. The tape is initialized with input on the left end, and a TM's computation can either halt by entering special accept
0 views • 29 slides
Computation for Real Estate Sector in Bangalore Branch of ICAI
Practical overview of GST computation for real estate transactions in Bangalore, with details on old rates with ITC and new rate regime effective from April 1, 2019. The content discusses different transactions, conditions for new rates without ITC, and provides insights on the 80:20 computation met
0 views • 39 slides
Fides: A System for Verifiable Computation Using Smart Contracts
Fides presents a system for verifiable computation using smart contracts, focusing on blockchain basics, Ethereum, smart contracts, and outsourcing computation. It explores key components of blockchain, Ethereum's decentralized computing platform, properties of smart contracts, and the concept of ve
1 views • 25 slides
Insights into Secure Computation with Minimal Interaction
This paper revisits the concept of secure computation with minimal interaction, focusing on the challenges and possibilities of achieving secure multiparty computation in 2 rounds. Specifically exploring scenarios with 3 and 4 parties, the study delves into the reasons for choosing n=3, n=4, and t=1
0 views • 23 slides
Overview of Income Computation and Disclosure Standards (ICDS)
The Income-tax Act, 1961 introduced Income Computation and Disclosure Standards (ICDS) to be followed by certain assesses for computation of income. ICDS applies to taxpayers using the mercantile system of accounting from the Assessment Year 2016-17 onwards. Non-compliance with ICDS can lead to Best
0 views • 49 slides
An Overview of Finite Element Method in Mechanical Engineering
Finite Element Method (FEM) in mechanical engineering is a powerful numerical technique involving dividing a domain into finite elements, establishing relations between variables, and assembling elements to analyze a system. This method is fundamental for solving one-dimensional problems and approxi
0 views • 63 slides
Theory of Automata: Introduction and Regular Languages Overview
This course delves into the fundamentals of Theory of Automata, exploring topics such as regular languages, finite state models, grammars, Turing machines, and more. Instructor Mr. Muhammad Arif guides students through essential concepts like finite automata, pumping lemma, decidability, and Chomsky
0 views • 95 slides
Blackbox Verifiable Computation Scheme Overview
This summarized content discusses the concept of blackbox verifiable computation, focusing on the challenges faced by clients and servers, the role of helper oracles, positive results utilizing homomorphic encryption, and background information on Random Self Reducible (RSR) functions. The protocol
0 views • 20 slides
Parallel Computation for Matrix Multiplication
Matrix multiplication is a fundamental operation with diverse applications across scientific research. Parallel computation for matrix multiplication involves distributing the computational workload over multiple processors, improving efficiency. Different algorithms have been developed for multiply
0 views • 36 slides
Comprehensive Guide for Teaching Computation in Senior Design - Cal State LA
Join Michael Thorburn at Cal State LA as he introduces senior design students to simulation and computational techniques. Explore the role of computation in engineering senior design, ABET requirements fulfillment, project-based learning, industrial partnerships, and workforce preparation. Discover
0 views • 18 slides
Finite Groups on Compact Surfaces with Boundaries
Illustrating the concept of finite group structures on compact surfaces with boundaries, this presentation showcases transformations, orientations, and color-coding used to represent group elements. By identifying regions in the hyperbolic plane and applying inversions, the images provide insights i
1 views • 28 slides
Advanced Techniques in Multi-Party Computation
Explore cutting-edge methods in Multi-Party Computation (MPC), including leveraging Fully Homomorphic Encryption (FHE) for minimal round complexity, constructing MPC directly via FHE techniques, and simplifying multi-key FHE constructions for efficient decryption. Learn about key concepts such as di
0 views • 17 slides