Entry Requirements for Higher National Diploma & Bachelor Degree Programmes at UNISSA
Applications are open for admission to UNISSA's programmes, with applicants required to meet general and specific entry requirements. Equivalents like Higher National Diploma are considered, but meeting requirements does not guarantee entry. Various criteria apply, including qualifications, health s
2 views • 25 slides
Multiple Point Lightning Protection Accessories, Multiple Point, Electrolytic Co
We are a leading manufacturer, exporter and supplier of a wide range of Multiple Point Lightning Protection Accessories, Multiple Point, Electrolytic Copper Multiple Point, Earthing and Lightning Protection at very cheap prices for our clients from Mumbai, India.
1 views • 3 slides
Overcome Denied Entry to Canada
Experience the expertise of Northvistaimmigration.com and overcome the heartache of being Denied Entry to Canada. Let us help you navigate the immigration process with compassion and success.\n\n\n\/\/northvistaimmigration.com\/denied-entry-to-canada\/
4 views • 1 slides
Understanding Single Entry System in Financial Accounting
Single Entry System is a simplified method used by small businesses to track their financial transactions. It lacks the rigor of double-entry bookkeeping and focuses on recording cash transactions and personal accounts. This system presents challenges in accurately determining profits and financial
0 views • 14 slides
Understanding Coordinated Entry System (CES) in Homeless Services
Coordinated Entry is a strategic approach focusing on housing and service coordination to link individuals experiencing homelessness to appropriate resources. With a primary goal of quick identification and prevention of homelessness, the system assesses consumer needs and connects them to housing a
0 views • 12 slides
Understanding Entry-Level Driver Training (ELDT) Requirements
Entry-Level Driver Training (ELDT) is mandatory for entry-level commercial motor vehicle (CMV) operators in interstate and intrastate commerce who are obtaining a Class A or Class B CDL for the first time, upgrading their CDL, or adding specific endorsements. ELDT must be completed from a provider l
0 views • 9 slides
Understanding Floating Point Representation of Numbers
Floating point representation is crucial in computer arithmetic operations. It involves expressing real numbers as a mantissa and an exponent to preserve significant digits and increase the range of values stored. This normalized floating point mode allows for efficient storage and manipulation of r
0 views • 12 slides
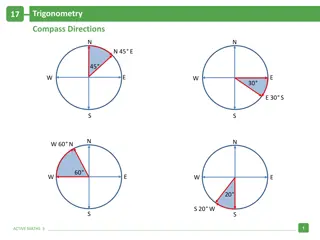
Trigonometry and Compass Directions Problem Solving
In this trigonometry problem, a ship travels from point A to point B and then to point C in specific directions. By applying the Pythagorean theorem, the distance from point C to A is calculated to be 7.2 km. The angle BCA is determined to be 34 degrees, and the direction of point C from A is found
0 views • 5 slides
Understanding Double Entry Accounting System in Finance
There are two commonly known systems of accounting - single entry system and double entry system. Double entry system is the basis of modern day accounting and ensures accuracy by recording every transaction with dual aspects of debit and credit. By maintaining personal and impersonal accounts, it h
1 views • 7 slides
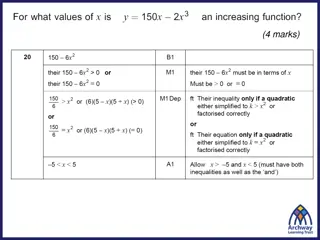
Understanding Points of Inflection in Calculus
Points of inflection in calculus refer to points where the curve changes from convex to concave or vice versa. These points are identified by observing changes in the curve's concavity, and they are not always stationary points. A stationary point can be a point of inflection, but not all points of
0 views • 14 slides
Understanding Entry and Exit Barriers in Industries
Entry and exit barriers play a significant role in shaping industry attractiveness and competitiveness. High entry barriers can deter new entrants, leading to stable returns but also higher risks. Conversely, low entry barriers may attract new players during economic upturns but result in intense ri
1 views • 15 slides
Comprehensive Confined Space Entry Training Guide
This training guide covers all aspects of confined space entry, including employee proficiency, safe performance, permit requirements, authorized entrants' duties, emergency services, and more. You'll learn about OSHA regulations, confined space definitions, examples, hazards, and general requiremen
0 views • 41 slides
Understanding Globalization and the Evolving Entrepreneurial Environment
Globalization is the increasing economic interdependence among countries worldwide, leading to cross-border transactions, technology diffusion, and international capital flows. It facilitates business expansion, erases market differences, and encourages global strategic orientations. Factors influen
0 views • 9 slides
Understanding Floating Point Representation in Binary Systems
In computer systems, decimal numbers are represented in memory using scientific notation. This involves moving the decimal point and using mantissa and exponent to maintain precision and range. The transition to representing numbers in binary involves multiplying by 2 to the power instead of 10. Uti
2 views • 22 slides
Introduction to Floating Point Data Types and Operations
This content delves into the fundamentals of floating-point data types, focusing on single-precision floating-point formats like float, excess-127, and their characteristics. It also compares float and int32_t data types, detailing the representation and conversion of values between them. The materi
0 views • 46 slides
New UCAS Tariff for Higher Education Entry Overview
UCAS has introduced a new Tariff for higher education entry starting from September 2017. This toolkit is designed to assist teachers and advisers in understanding the changes, timeline, points system, university examples, myth debunking, and available resources. The aim is to prepare educators and
0 views • 32 slides
Exploring Web Application Vulnerabilities and JavaScript Worms
Web applications face pervasive vulnerabilities, with Cross-site Scripting (XSS) leading the threats. The domination of XSS and buffer overruns has enabled the propagation of JavaScript worms, exemplified by infamous cases like Samy's MySpace outbreak. These exploits, marked by obfuscation and polym
1 views • 20 slides
Location Privacy Protection Strategies: A Comprehensive Overview
This study delves into optimal strategies to safeguard location privacy against localization attacks in the realm of location-based services. Discussing the shortcomings of anonymization and obfuscation as standalone defenses, it explores the challenges and pitfalls in designing effective protection
0 views • 26 slides
Understanding Colligative Properties in Solutions
Colligative properties in solutions depend on the total concentration of solute particles present, impacting properties such as boiling point elevation, freezing point depression, vapor pressure lowering, and osmotic pressure. Boiling point elevation is directly proportional to the number of solute
1 views • 19 slides
Impact of Rating-Based Platform Screening on New Complementor Entry
This study explores the effects of a platform design that ranks incumbent complementors based on review ratings on new complementor entry and overall complementor quality. The findings suggest that the rating-based platform screening reduces new complementor entry but enhances complementors' overall
1 views • 9 slides
Comprehensive Malware Analysis Techniques
This detailed guide covers basic static techniques, malware analysis in virtual machines, and basic dynamic analysis. It includes information on static analysis, such as examining payloads without execution, file signatures, and signatures generated via analysis. Additionally, it delves into counter
0 views • 17 slides
Understanding Weird Machines in Transient Execution
Weird machines refer to models exhibiting unintentional behaviors triggered by adversarial inputs. They serve as computation primitives, enabling tasks like program obfuscation and secret computations. TSX weird machines, computing with time, manipulate cache states through gates like Assign, AND, O
0 views • 18 slides
Understanding Entry and Exit Dynamics in Industries
Explore the fascinating world of entry and exit in industries, from the facts and barriers to Bain's typology of entry conditions and structural entry barriers. Learn about entry deterring strategies such as limit pricing, predatory pricing, and strategic bundling, and how they impact the market lan
0 views • 8 slides
Enhancing Civil Society Participation in TSD Chapters of EU PTAs through the Single Entry Point
The Single Entry Point (SEP) serves as a key mechanism for EU-based stakeholders to address violations in Trade and Sustainable Development (TSD) commitments. Through a centralized platform, stakeholders, including EU member states, NGOs, and citizen groups, can submit complaints regarding breaches
0 views • 10 slides
Effective Strategies for Data Entry Integrity and Minimizing Errors
The chapter and subchapter discuss the importance of data integrity in the data management process, specifically focusing on data entry procedures, authenticity, and minimizing errors. It covers traditional manual data entry methods versus newer automated technologies, such as CAPI, and offers strat
0 views • 31 slides
Encrypted Data Deletion for Cloud Storage Servers
Explore the concept of software with certified deletion for private cloud storage servers. Discover how data recoverability is influenced by secret key leaks and encryption scheme vulnerabilities. Learn about techniques for computing on encrypted data and ensuring provable deletion, with a focus on
0 views • 29 slides
Understanding Freezing Point Depression and Molality for Solutions
Introduction to molality and freezing point depression in solutions. Molality is a way to measure solution concentration, calculated using moles of solute and kilograms of solvent. By calculating the moles of NaCl in a salt solution and the mass of the solvent (ice/water), the molality can be determ
0 views • 9 slides
Understanding Threats and Responses in the Mobile App Market
The study explores the impact of platform-owner entry on complementors in the mobile app market, examining evidence from platforms like Facebook, Uber, Android, Alibaba, iOS, and WeChat. Concerns from complementors about imitation by platform owners are discussed, along with views from platform owne
1 views • 19 slides
Advanced Security Concepts in SNARGs Using iO and Lossy Functions
Explore the latest research on Adaptive and Selective Soundness in Succinct Non-interactive Argument of Knowledge (SNARGs), presenting theorems and the inclusion of subexponentially secure techniques like indistinguishability obfuscation, one-way functions, and very lossy functions. Discover the pot
0 views • 20 slides
Understanding Anti-Anti-Virus Techniques and Retroviruses
Explore the world of anti-anti-virus techniques including Retroviruses and Entry Point Obfuscation. Learn about the methods used by viruses to evade detection and damage anti-virus software. Discover how Retroviruses like Ganda virus operate stealthily to hinder anti-virus programs. Delve into strat
0 views • 24 slides
Techniques for Protecting Web User Identity: Part 2 Overview
Explore offensive, defensive, and forensic techniques for safeguarding web user identity in this detailed guide by Zachary Zebrowski. Learn about obfuscation methods, browser protection, and important caveats to enhance online privacy. Discover strategies like borrowing a neighbor's network, using s
0 views • 45 slides
Nonparametric Tolerance Interval Approach to Immunogenicity Assay Cut Point Determination
This content discusses the importance of determining the cut point for immunogenicity assays to detect anti-drug antibodies (ADA) in large-molecule therapeutics. It highlights the need for well-developed and validated assays to ensure drug efficacy and safety. The approach involves multiple-tiered v
0 views • 26 slides
Insights on Entry and Exit Dynamics in Industries
Exploration of the entry and exit dynamics in industries, covering factors influencing the establishment of new firms, barriers to entry, Bain's typology of entry conditions, structural entry barriers, and entry-deterring strategies employed by incumbents. Insights include the impact on the market l
0 views • 7 slides
Evaluating Android Anti-malware Against Transformation Attacks
This study evaluates the effectiveness of Android anti-malware solutions against transformation attacks, focusing on the resistance to various types of malware obfuscations. It explores different transformations such as repacking, trivial changes, and sophisticated obfuscation techniques. Ten popula
0 views • 23 slides
Exploring SMT Solvers for Malware Unpacking
In this informative content, we delve into the world of malware analysis, binary packers, and the challenges posed by obfuscation techniques. The article discusses tools like UPX and Themida, as well as the complexities of virtualization and handler obfuscation in unpacking malware. Understanding th
0 views • 24 slides
Understanding Floating Point Numbers in Computer Science
Exploring the concepts of floating point format, normalization, conversion processes, and IEEE 754 standard for representing floating point numbers in computer systems. Learn about two's complement, excessive notation, and the components that make up a floating point number. Dive into examples of co
0 views • 18 slides
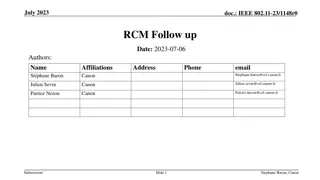
RCM Procedure for Secure Parameter Obfuscation in IEEE 802.11 Networks
The document discusses the RCM procedure within IEEE 802.11 networks, focusing on obfuscating parameters like MAC addresses for enhanced security during CPE Client and CPE AP association. It outlines mechanisms for changing MAC addresses, SN, PN, AID, and TID without connection loss. The proposal su
0 views • 12 slides
BioLock Biometric Home Entry System Overview
BioLock is a biometric home entry system developed by Mavis Chan, Brent Erickson, and Sydney Bitner of Group 9. It features a fingerprint-enabled lock for secure home access, allowing homeowners to check access history remotely and receive alerts for unauthorized entry attempts. The system utilizes
0 views • 12 slides
Understanding Point-to-Point Protocol (PPP) and Serial Communications in WANs
This content explores the Point-to-Point Protocol (PPP), outlining its components, establishment of sessions, authentication protocols, and configuration. It also delves into WAN connection options, serial and parallel ports communication, and serial communication standards for LAN-to-WAN connection
0 views • 31 slides
Stress Ulcer Prophylaxis in ICU Data Entry System - SUP-ICU Overview
Dive into the Stress Ulcer Prophylaxis in the Intensive Care Unit (SUP-ICU) data entry system led by Dr. Soeren Marker Jensen. Explore screening, randomization, site overview, and data entry processes. Access participant details, edit submitted data, and learn about data entry guidelines. Enter the
0 views • 28 slides