Dynamic Buffer Sizing using Passive Measurements from P4 Switches
This study explores the dynamic modification of router buffer sizes by leveraging passive measurements from P4 switches. By dynamically adjusting buffer sizes based on factors like the number of long flows, average round-trip time, queueing delays, and packet loss rates, network performance can be o
3 views • 14 slides
Protein Sample Clean-Up Methods for MALDI Analysis
Protein sample clean-up for MALDI involves removing various contaminants like buffer, salts, urea, guanidine, EDTA, glycerol, DMSO, and detergents through methods such as dilution, washing, drop dialysis, cation exchange, and solid phase extraction using Zip tips. The process aims to reduce interfer
0 views • 8 slides
Understanding Circular Buffers and Linked Lists in Data Structures
Circular Buffers are data structures designed to efficiently manage streams of data while maintaining a fixed amount of memory usage. The buffer consists of a fixed-length array with head and tail indexes, allowing data to loop back to the beginning when the end of the buffer is reached. It is cruci
0 views • 24 slides
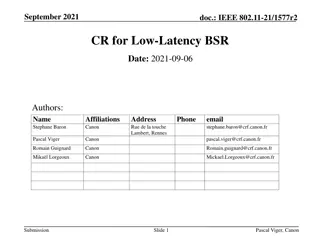
Improving Low-Latency Buffer Status Reporting in IEEE 802.11
Proposal for enhancing the Buffer Status Report (BSR) mechanism in IEEE 802.11 to include timing constraints for transmitting latency-sensitive traffic. Suggestions involve adding TSPEC-based signaling and efficient mechanisms for Enhanced Traffic APs to ascertain low-latency traffic status. The cur
0 views • 12 slides
Understanding Buffer Overflow Attacks at Carnegie Mellon
Learn about the Carnegie Mellon 15-213 Recitation Attack Lab, where you can hijack programs using buffer overflow attacks. Gain insights into stack discipline, stack frames, and defeating secure programs through return-oriented programming. Dive into topics like stack smashing attacks, buffer overfl
8 views • 24 slides
Understanding Buffer Solutions: Properties and Applications
Buffer solutions are essential in resisting pH changes and consist of mixtures of weak acids or bases with their salts. They maintain constant pH levels despite dilution or addition of acids/bases. Buffer capacity measures the amount of acid/base needed for a pH change. Biological systems and pharma
3 views • 4 slides
Reactor Sizing and Conversion in Chemical Engineering
This chapter explores the sizing of Continuous Stirred Tank Reactors (CSTR) and Plug Flow Reactors (PFR) using conversion values and overall conversion. It covers the definition of conversion, batch reactor design equations, design equations for flow reactors, and more. The content delves into the m
0 views • 17 slides
FPGA Centric Dataflow Buffer Management Overview
This overview discusses buffer management for FPGA-centric dataflow systems, including the use of DDR4 RAM, solid-state storage, FIFO structures, and trigger commands for efficient data processing and storage. It also covers the handling of compressed and uncompressed data volumes, proposed hardware
0 views • 12 slides
How to Use Buffer to Increase Your Affiliate Marketing Revenue
How to Use Buffer to Increase Your Affiliate Marketing Revenue
0 views • 5 slides
Understanding Buffer Solutions and pH Indicators
Buffer solutions resist changes in pH upon the addition of acids or bases, maintaining a stable pH level. They consist of a weak acid and its conjugate base or a weak base and its conjugate acid. pH indicators are weak acids or bases that exhibit color changes based on their degree of dissociation a
0 views • 21 slides
Understanding Buffer Overflow Vulnerabilities in Programming
Buffer overflow vulnerabilities pose serious security threats by allowing attackers to execute arbitrary code on victim machines. This issue arises from overwriting memory in a way that manipulates the program's behavior. Learn about the dangers of buffer overflow bugs, how they can be exploited, an
2 views • 33 slides
Understanding Buffers in Chemistry
The concept of buffers in chemistry plays a crucial role in maintaining stable pH levels in solutions. Buffers consist of components that neutralize acids and bases, helping prevent drastic pH changes. Weak acids or bases are ideal buffer components due to their ability to react with both acids and
1 views • 15 slides
Buffer Overflow: Understanding, Defenses, and Detection
Dive into the world of buffer overflow attacks with insights on understanding the concept, implementing defenses, and detecting stack smashing using techniques like canary values. Discover how to protect against vulnerabilities and grasp the significance of elements such as EIP, ASLR, DEP, and NX bi
0 views • 10 slides
Understanding Computer System Exploits and Prevention
Exploring program exploitation, stack buffer overflows, vulnerability analysis, and exploit prevention strategies in computer systems. Learn about setting the stage for exploits, exploiting stack buffer overflows, and the challenges faced in executing shellcode attacks. Dive into the world of cyber
0 views • 36 slides
Understanding Buffer Overflows and Exploits in C Programs
Explore the concepts of buffer overflows and exploits in C programming, covering memory layout, program details, and examples of stack smashing and implicit casting bugs. Learn how attackers manipulate code sequences and take control through vulnerabilities like the misuse of functions like memcpy.
0 views • 39 slides
Buffer Overflows in CSE351 Autumn 2017
Explore buffer overflows in CSE351 Autumn 2017, covering topics like memory layout, stack, heap, and defenses against buffer overflows. Learn about important concepts such as input buffers, code injection, and memory allocation examples, with insights into x86-64 Linux memory layout.
0 views • 33 slides
Market Data Analytics Methodology Overview
MarketLine produces market sizing data for retail Consumer Packaged Goods (CPG) markets through a comprehensive research methodology that includes thorough industry review, primary and secondary research, extensive data analysis, and forecasting models driven by macro-economic and socio-demographic
0 views • 13 slides
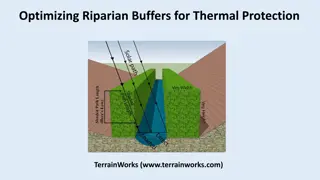
Optimizing Riparian Buffers for Thermal Protection in Teanaway River Watershed
Explore the study comparing optimized riparian buffer designs with fixed-width buffers in non-fish bearing streams of the Teanaway River watershed, focusing on maximizing thermal energy reductions with considerations for channel orientation and forest density. By utilizing NetMaps and thermal energy
0 views • 24 slides
Understanding Buffer Overflow in Computer Programming
This content delves into the intricacies of buffer overflow vulnerabilities in computer programming, showcasing real-world examples such as the Internet Worm and IM War incidents. It covers topics like stack buffer overflow exploits, Unix function implementations prone to buffer overflow, and the re
1 views • 35 slides
Visible Surface Detection in Computer Graphics
Understanding the importance of Visible Surface Detection (VSD) in computer graphics, focusing on techniques like backface culling and the Depth-Buffer Method to determine visible surfaces in a scene. Limitations of back-face culling and the Depth-Buffer Algorithm are addressed along with practical
0 views • 24 slides
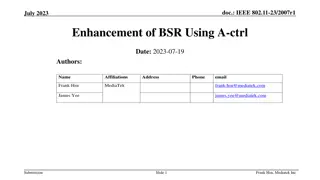
Enhancement of Buffer Status Reporting in IEEE 802.11 - A Solution Proposal
This document proposes enhancements to the Buffer Status Reporting (BSR) mechanism in IEEE 802.11, particularly addressing the issue of inaccuracies in reporting queue sizes exceeding 2,147,328 octets within PPDU frames. The proposal suggests adding an additional field in the A-ctrl frame to accommo
0 views • 9 slides
Efficient Buffer Management Strategies in Database Systems
Buffer management is a crucial aspect of database systems, ensuring optimal data storage and retrieval. This involves intelligent shuffling of data between memory and disk, guided by replacement policies like LRU and Clock algorithm. Understanding how buffer managers operate and make decisions is ke
2 views • 38 slides
Efficient Buffer Replacement Algorithms for NAND Flash Storage Devices
NAND flash storage devices are increasingly replacing traditional HDDs in modern computing systems due to their technical advantages such as low latency, low power consumption, and shock resistance. However, as flash density increases, challenges like decreased lifetimes due to random writes persist
0 views • 20 slides
Issues and Tests in Data Analysis at IHEP Experimental Center
Data analysis issues and tests were found by Tingxuan Zeng at the TDAQ Group within the Experimental Center at IHEP. Various issues were identified during the last data taking session, including discrepancies in GEMDC packet counts, incorrect packet lengths, and buffer pile-up. Analysis and testing
0 views • 4 slides
Understanding Buffers in Chemistry
Buffers play a crucial role in maintaining stable pH levels in solutions. They are composed of a weak acid and its conjugate base or a weak base and its conjugate acid. This summary covers the definition of buffers, differentiation between buffer and non-buffer systems, the behavior of buffers when
3 views • 23 slides
Understanding Buffer Overflow in C and C++ Programs
Buffer overflow is a common vulnerability in C and C++ programs where the allocated memory buffer is overwritten, causing unpredictable behavior. This vulnerability allows attackers to exploit the program by injecting malicious code. The lack of automatic bounds checking in these languages makes it
0 views • 6 slides
Understanding Stack Buffer Overflow Vulnerabilities
Stack buffer overflow is a critical security issue caused by writing more data to a buffer than allocated, leading to bugs, crashes, and potential attacks. This vulnerability, exemplified by the Twilight Hack, allows executing arbitrary code. Learn about its causes, implications, and mitigation stra
0 views • 7 slides
Buffer Overflow Attack and Vulnerable Programs
Understanding buffer overflow attacks and vulnerable programs, the consequences of such attacks, how to run malicious code, and the setup required for exploiting vulnerabilities in program memory stack layouts. Learn about creating malicious inputs (bad files), finding offsets, and addressing shellc
0 views • 36 slides
Understanding Control Hijacking Attacks in Computer Systems
Explore the concept of control hijacking attacks in computer systems, including buffer overflows, format string vulnerabilities, and use-after-free exploits. Learn about the attacker's goal, examples of attacks, and the importance of understanding C functions, the stack, and the heap. Delve into sys
0 views • 39 slides
Understanding Buffer Overflow in Stack: SEED Workshop Lab
This content provides a comprehensive overview of buffer overflow in stack focusing on SEED Workshop Lab scenarios. It covers principles, practice, high-level pictures, program memory layout, function stack layout, function call chains, vulnerable program examples, and more. Through detailed images
0 views • 34 slides
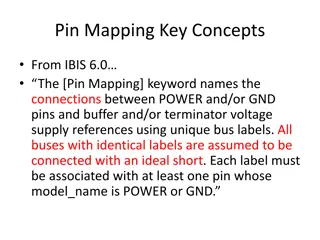
Understanding Pin Mapping and Interconnect in IBIS 6.0
Pin Mapping in IBIS 6.0 defines the connections between POWER/GND pins and buffer/terminator voltage supplies using unique bus labels. Interconnects between VDD pins and buffer supply terminals are crucial, with all pins associated with a named supply being shorted together. Draft 9 Interconnects an
0 views • 6 slides
Preliminary Wing Sizing and Design Process Overview
Explore the preliminary design process for wing sizing in aircraft engineering, including key topics, weight estimation spreadsheets, configuration layouts, propulsion system options, and structural considerations. Dive into sensitivity studies, takeoff thrust, aspect ratios, payloads, and more to r
0 views • 9 slides
High-Performance Gate Sizing with Signoff Timer: VLSI Design Challenges
This study delves into the intricate realm of gate sizing in VLSI design, focusing on optimizing power and delay through effective approaches and addressing challenges such as interconnect delay, inaccurate internal timers, and critical paths. Previous gate sizing techniques are evaluated, and a met
0 views • 34 slides
Non-Preemptive Buffer Management for Latency Sensitive Packets
Moran Feldman and Seffi Naor from Technion present a non-preemptive buffer management approach for handling latency-sensitive packets in communication networks. The model focuses on deadlines for packet arrival and associated values that diminish over time. The competitive ratio is used as a perform
0 views • 19 slides
Understanding Buffers in Pharmaceutical Formulations
Buffers in pharmacy play a critical role in maintaining constant pH levels essential for drug stability and efficacy. They resist pH changes by neutralizing added acids or bases, ensuring proper drug delivery and patient comfort. Common buffer systems, such as acetic acid/sodium acetate and boric ac
4 views • 18 slides
Efficient UL Buffer Status Reporting in IEEE 802.11 Networks
IEEE 802.11-16/0856r1 discusses the importance of UL buffer status reporting in 11ax for efficient resource allocation. The document addresses managing unmanaged P2P flows to enhance buffer status reporting accuracy. It proposes solutions to prevent misallocation of resources due to large data amoun
0 views • 11 slides
Proposed Buffer Mitigation Rules Overview
The proposed buffer mitigation rules aim to address nutrient loading by adopting alternative measures to replace lost riparian buffers. The rules include options for location of mitigation, accounting for buffer and nutrient offset, and various optional methods like coastal headwater stream mitigati
0 views • 21 slides
Understanding Buffers: A Comprehensive Overview
Explore the concept of buffers, their role in resisting pH changes, and how they differ from non-buffer systems. Learn about buffer solutions like acetate buffer and how they react to acids and bases. Discover the importance of pH indicators in understanding the pH of buffer solutions.
0 views • 24 slides
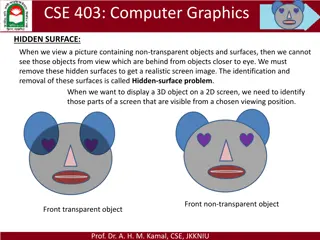
Hidden Surface Removal in Computer Graphics
In computer graphics, the hidden-surface problem refers to identifying and removing surfaces that are not visible in a given view to create a realistic screen image. Different methods like Depth Buffer (Z-Buffer) and Scan-Line are used to address this issue by determining the closest visible surface
0 views • 14 slides
Insights into DNS Flag Day 2020 Trends and Analysis
Delve into the DNS Flag Day 2020 observations and trends, including changes in buffer sizes, UDP fragmentation, and the selection of threshold points for DNS to switch to TCP. Explore the impact of varying buffer sizes on users and the DNS system, highlighting shifts in usage percentages and implica
0 views • 29 slides