Gradual Fine-Tuning for Low-Resource Domain Adaptation: Methods and Experiments
This study presents the effectiveness of gradual fine-tuning in low-resource domain adaptation, highlighting the benefits of gradually easing a model towards the target domain rather than abrupt shifts. Inspired by curriculum learning, the approach involves training the model on a mix of out-of-doma
0 views • 17 slides
Importance of Timely Verification in Care After Death
Understanding the verification process and importance of timely verification in care after death is crucial for improving the experience of death and dying for families. This session covers the definitions, process, and care after death, emphasizing the significance of timely verification in end-of-
2 views • 15 slides
Domain Adaptation in Machine Learning
Domain adaptation in machine learning involves transferring knowledge from one domain to another. It addresses the challenge of different data distributions in training and testing sets, leading to improved model performance. Techniques like domain adversarial training and transfer learning play a k
0 views • 16 slides
Electors Verification Programme Overview
The Electors Verification Programme (EVP) is a campaign initiative encouraging citizens to verify and authenticate electoral details, including family members. Various methods such as NVSP, Mobile App, and 1950 helpline are utilized for verification. Citizens can also submit details through BLOs to
2 views • 25 slides
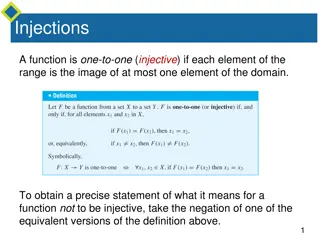
Injective and Surjective Functions
Injective functions map elements from the domain to the range uniquely, while surjective functions ensure every element in the co-domain has a corresponding element in the domain. The negation of injective means finding x1 and x2 in the domain with the same function value but not equal, whereas for
2 views • 26 slides
Criticisms and Defenses of Verification and Falsification Principles
Explore the criticisms and defenses of the Verification and Falsification Principles in religious language. Understand how believers defend the use of religious language and analyze challenges posed to the Verification Principle by notable thinkers like Swinburne, Hare, and Mitchell. Delve into resp
3 views • 15 slides
GLP.BBBEE.(PTY).LTD - Your Trusted BEE Verification Agency
GLP.BBBEE.(PTY).LTD is a level 3 SANAS accredited BEE verification agency with 9 years of experience specializing in complex ownership structures. They offer professional BEE verification services with a team of technical signatories ensuring fair ratings for clients across various sectors. Their ef
0 views • 7 slides
Integrated Verification and Repair in Control Plane
Modern networks face challenges from incorrect configurations affecting millions of users. This presentation discusses the integration of verification and repair processes into the control plane, aiming for consistent and policy-compliant network operations. It explores the complexities of network c
0 views • 16 slides
Formal Verification and Automata Abstraction in Esterel
This content delves into the applications of formal verification and automata abstraction in Esterel, focusing on techniques such as verification by abstraction of automata, boolean verification using BDDs, bounded model checking in SAT/SMT, and more. The work of Gérard Berry at the Collège de Fra
0 views • 38 slides
Program Verification via an Intermediate Verification Language
Dive into the world of program verification through an intermediate verification language with a focus on static program verification, reasoning about programs, and separation of concerns. Explore tools like Dafny and verification architectures like Boogie and Why3, along with key concepts including
1 views • 36 slides
Software Bugs and Formal Verification in Critical Systems
Software bugs have caused catastrophic events like radiation overdoses and rocket explosions, emphasizing the importance of formal verification in ensuring software correctness. Formal verification uses mathematical models to prove software correctness, offering higher assurance, especially in safet
1 views • 26 slides
Country Names in the Domain Name System (DNS)
The Domain Name System (DNS) plays a crucial role in attributing top-level and second-level domains to country names. This system is global and managed by ICANN, not national offices, allowing for unique attribution to one person. Examples of country names registered as second-level domains are prov
2 views • 7 slides
Formal Verification of Cyberphysical Systems and Future Certification Methods
Explore the formal verification techniques and tools used in cyberphysical systems, including KeYMaera verification tool, applications in distributed car control and adaptive cruise control, and the formal verification of ACC algorithms. The future work section highlights considerations for sensor d
0 views • 17 slides
Comprehensive Solution for EU Digital COVID Certificate Verification
This solution offers face recognition, temperature monitoring, and verification of EU Digital COVID Certificates for personnel. It includes products like DHI-ASI7213X-V1-T1 and ASF172X-T1, with various unlocking modes and support for certificate verification. The system allows for accurate and fast
1 views • 7 slides
Automated Static Verification of Higher-order Functional Programs
Explore the automated static verification of higher-order functional programs, focusing on Haskell code. Learn about denotational semantics, program assertions, and tools like GHC for verification. Discover the emphasis on simplicity and structural properties for easy proofs. Consider utilizing exis
0 views • 22 slides
Gradual Program Verification and its Techniques
Gradual Program Verification introduces a method where static verification is combined with dynamic verification to ensure program correctness gradually. This approach allows for partial specifications and runtime checks to be gradually applied, reducing the risk of errors and overhead in software d
0 views • 18 slides
Warning Verification and Scoring Guidelines in Weather Forecasting Workshop
Learn about the verification of warnings, classical contingency scoring, false alarm ratio, hits, false alarms, missed alarms balance, threshold-based warning verification, and impact-based warning verification discussed in the IMS Warning workshop at KNMI Block III. Understand the importance of mai
0 views • 13 slides
Verification Modulo Versions: Towards Usable Verification
Explore the challenges and solutions in compile-time verification with CodeContracts in Visual Studio. Delve into addressing warnings, improving analysis precision, and managing syntactic baselines for a more reliable verification process.
1 views • 33 slides
SKA1 Low Assembly Integration & Verification Plan
The SKA1 Low Assembly, Integration, and Verification (AIV) Plan outlines the responsibilities of the AIV Consortium, consortium partners, and the roll-out plan for the SKA1 Low telescope. The plan encompasses user requirements validation, system verification, operational concepts, and more. It detai
2 views • 12 slides
ICAO Strategic Objective: Economic Development of Air Transport Verification and Validation Overview
This content provides an in-depth analysis of the ICAO Strategic Objective focusing on the economic development of air transport through verification and validation processes for air carriers. It includes details on forms verification, economic analysis, and policy considerations discussed at the IC
1 views • 22 slides
Securing Domain Control with BGP Attacks and Digital Certificates
Exploring the vulnerabilities of domain control verification in the context of BGP attacks and the role of digital certificates in ensuring security. The process of domain control verification, issuance of digital certificates by Certificate Authorities (CAs), and the significance of Public Key Infr
0 views • 53 slides
Overview of Program Verification Tools and Techniques
Explore the pillars of program verification, early mechanical verification systems, software quality assurance, and a spectrum of verification tools used for ensuring functional correctness, safety-critical systems, and more. Discover the role of proof assistants and automatic decision procedures in
1 views • 21 slides
Introduction to UVM: Verification Methodologies Overview
Explore the Universal Verification Methodology (UVM) for writing modular, scalable, and reusable testbenches. Learn about UVM's key technical highlights, its support for migration towards Coverage Driven Verification (CDV), and the advantages of Constrained Random Verification (CRV) in functional ha
1 views • 20 slides
DeepFace: Advancements in Face Verification Technology
DeepFace by Yaniv Taigman, Ming Yang, Marc Aurelio Ranzato, and Lior Wolf from Facebook AI Group and Tel Aviv University presents a breakthrough in face verification technology. The system achieves human-level performance by utilizing deep neural networks for face recognition, detection, alignment,
1 views • 12 slides
Basic Hardware Verification Flow
This content delves into the significance of verification in hardware design, emphasizing the need for meticulous code review, skilled engineers, and comprehensive testing practices. It explores the Universal Verification Methodology (UVM) and various effective protocols for ensuring robust verifica
0 views • 54 slides
Verification Job Aid
The Real Time Interface page in KEES allows users to track the status of their verification calls and view responses. Learn how to navigate the History List for call records and the Detail List for request and response details. Make sure to select the appropriate verification type before making requ
0 views • 23 slides
Conformance Verification of Privacy Policies
In this detailed presentation, Xiang Fu, an Assistant Professor at Hofstra University, explores the conformance verification of privacy policies and the framework for privacy properties in temporal logic verification. The content covers the challenges, PV framework, data models, examples, and action
0 views • 23 slides
Automatic Program Verification Concepts
This content delves into various aspects of automatic program verification, exploring topics such as dynamic frames, separation of concerns, verification architecture, Boogie language overview, translation basics, and unstructured control flow in .NET bytecode. The detailed explanations and examples
0 views • 22 slides
Automatic Program Verifier and Boogie Language Overview
This content explores the concepts of automatic program verification through Separation of Concerns, Intermediate Verification Language, and Boogie language overview. It delves into the verification architecture using tools like Boogie and SymDiff, emphasizing the importance of structured verificati
0 views • 27 slides
Understanding Domain Name System (DNS) and Content Delivery Networks (CDNs)
Explore the fundamentals of DNS and CDNs in computer networks, covering topics such as domain organization, address conversion protocols, the importance of domain names, and the process of translating domain names to IP addresses. Discover the challenges and complexities involved in navigating, cach
1 views • 59 slides
Optimal Information Verification in Market Dynamics
Explore the challenges and strategies involved in optimal verification of information in market dynamics, including uncertainty, party responsibility, verification efforts, and the impact of prior communication. Realistic settings and case examples shed light on balancing verification costs with eff
0 views • 11 slides
End-to-End Crypto and Identity Verification Protocols at University College London
Explore topics such as end-to-end cryptography, anonymous communications, zero-knowledge data protection, and identity verification protocols at University College London through lectures and labs. Understand the procedures for non-interactive proof verification and the significance of identity as a
0 views • 33 slides
Understanding Program Verification Techniques
Dive into the world of program verification through Decision Procedures as outlined in Chapters 12.1-12.3 of the book "Decision Procedures: An Algorithmic Point of View" by Kroening and Strichman. Explore topics such as software verification, program analysis, bug checking, formal verification, and
0 views • 29 slides
Religious Responses to the Verification Principle and Eschatological Verification
Explore how believers defend religious language against the Verification Principle, with a focus on responses to challenges and the concept of eschatological verification. Evaluations of the Verification Principle are discussed, highlighting the limitations and strengths in relation to religious tru
0 views • 16 slides
Runtime Verification Inc.: Innovating Reliable Software Solutions
Discover how Runtime Verification Inc., founded by Grigore Rosu, pioneers runtime verification technology to ensure reliable software development. Explore their cutting-edge tools like RV-Match, RV-Predict, and RV-Monitor. Join the forefront of computing systems verification with this top-tier start
0 views • 12 slides
Solving Problems in Classic Blocks World Domain
Explore the Classic Blocks World domain starting with BW domain file, solving problems using planning domains, and extending the domain with predicates and constants. Learn about basic add and delete effects in actions, defining predicates and actions, and executing pick-up, put-down, stack, and uns
0 views • 11 slides
Understanding the Market for Instagram Verification Badges
Explore the demand and business tactics behind Instagram verification badges, from the evolution of verification badges to methods of obtaining them. Discover the thriving market for verification badges and insights on their acquisition in this insightful presentation.
0 views • 7 slides
Differential Program Verification: Understanding Differences
Explore the concept of differential program verification, where properties of differences instead of programs are verified. Learn about the motivation, research questions, applications, and ongoing progress in this domain. Discover how differential verification can impact software engineering tasks,
0 views • 33 slides
Modular Primal-Dual Fixpoint Logic Solving for Temporal Verification
Explore the innovative approach of solving temporal verification using modular primal-dual fixpoint logic to address non-safety verification challenges. Learn about constraint-based verification with constrained Horn clauses and extensions for non-safety verification in this cutting-edge research wo
0 views • 27 slides
DVCon Taiwan 2024 Design and Verification Contest - Authors, Design Scope, and Verification Plan
Explore the details of the DVCon Taiwan 2024 Design and Verification Contest, including information about authors, design scope, verification plan, methods, report, and conclusions. Get insights into the proposed verification strategy, integration process, evaluation metrics, and more.
0 views • 6 slides