Deepfake: How To Countermeasures IT In 2024
Our recent research across 9 countries reveals some surprising findings on public awareness and concerns.\n \nAre deepfakes a threat? What impact will they have on society?
2 views • 9 slides
Overview of Computer and Network Security Fundamentals
Computer and network systems provide opportunities for cost reduction, efficiency improvement, and revenue increase but also expose us to security risks. This lecture covers encryption, authentication, security services, threats, and countermeasures related to network and computer security. It empha
0 views • 56 slides
Web App Security: Common Attacks and Preventive Measures
Explore common web application attacks like eavesdropping, SQL injection, and packet sniffing, along with their countermeasures like encryption with SSL. Learn how to prevent data breaches and secure your online platforms effectively.
1 views • 29 slides
Understanding Anti-Countermeasures in Credibility Assessment
Explore the world of anti-countermeasures in credibility assessment, including proactive and reactive actions to prevent or detect countermeasures. Learn how to behaviorally differentiate between guilt and innocence, and the importance of clear warnings against countermeasures. Discover the strategi
0 views • 17 slides
Introduction to Database Security and Countermeasures
Database security is essential to protect data integrity, availability, and confidentiality. Countermeasures such as access control, inference control, flow control, and encryption can safeguard databases against threats. Access control restricts user access, inference control manages statistical da
0 views • 26 slides
Database Security Measures and Controls
Database security is crucial to protect against threats like loss of integrity, availability, and confidentiality. Countermeasures such as access control, inference control, flow control, and encryption are important for safeguarding databases. Access control involves creating user accounts and pass
0 views • 35 slides
Understanding OPSEC: Protecting Critical Information in Military Operations
OPSEC is crucial in military operations to safeguard critical information from adversaries. This involves identifying vulnerable actions, analyzing threats, and implementing countermeasures. Soldiers must be aware of what information to protect and how to enforce OPSEC effectively.
0 views • 17 slides
Understanding Buffer Overflow Attacks at Carnegie Mellon
Learn about the Carnegie Mellon 15-213 Recitation Attack Lab, where you can hijack programs using buffer overflow attacks. Gain insights into stack discipline, stack frames, and defeating secure programs through return-oriented programming. Dive into topics like stack smashing attacks, buffer overfl
8 views • 24 slides
Comprehensive Overview of E-Commerce Application Development and Computer Security
Delve into the world of e-commerce application development with insights on asset protection from unauthorized access and the critical aspects of computer security and risk management. Explore concepts like risk management models, elements of computer security, and the importance of establishing a r
1 views • 61 slides
Defeating Vanish: Low-Cost Sybil Attacks Against Large DHTs
Explore the vulnerabilities of Vanish, a self-destructing data system, to low-cost Sybil attacks in large Distributed Hash Tables (DHTs). Learn about the potential risks, costs, countermeasures, and security implications associated with transient data storage in DHT networks.
0 views • 38 slides
Decoy Routing: A Tool Against Internet Censorship
Modern censorship resistance tools like decoy routing provide a new approach against web censorship at a nation-state level. Decoy routing involves placing a proxy in the middle of paths to hide user packets from detection by adversaries. The use of decoys helps in avoiding the enumeration of censor
0 views • 20 slides
Effective Countermeasures Against Cyber Attacks
Explore various defense mechanisms to prevent cyber attacks, including proper bounds checking, system defenses like NX bit, Canaries, ASLR, DEP, and techniques like ROP chains. Learn about compiler-level techniques such as inserting canaries on the stack to detect overflows and separating executable
0 views • 23 slides
Analysis of McEliece Vulnerabilities in Escher's World
In this detailed study by Ray Perlner and Dustin Moody from NIST, the vulnerabilities of McEliece in Escher's world are explored. The research covers error sets, commonalities with other variants, private key operations, decoding algorithms, encryption, and more. The findings shed light on potential
0 views • 25 slides
Understanding Internet Threat Landscape and Countermeasures
Delve into the complexities of identifying and mitigating threats in cyberspace at scale. Explore the challenges of detecting malicious activities, the need for broad-based blocklists, and the importance of tracking provider abuse percentages. Learn about the Pwnage Cycle, ICANN's efforts in measuri
0 views • 32 slides
Comprehensive Cloud Security Measures and Solutions
A comprehensive overview of cloud security challenges and countermeasures, addressing issues such as unrestricted outbound traffic, lack of inventory management, encryption failures, and more. The provided solutions include nonpartisan research, strategic partnerships, compliance frameworks, and mod
0 views • 15 slides
Understanding Security Threats and Countermeasures
Explore the diverse threats posed by attackers in the information security landscape, ranging from employee sabotage to hacking incidents. Learn about fundamental security terminology, types of security compromises, and countermeasure strategies to prevent, detect, and correct security breaches. Gai
0 views • 32 slides
Research on Polygraph and Deception Detection
The research focuses on the use of polygraph tests for deception detection, highlighting concerns about accuracy when facing major security threats. It discusses the impact of countermeasures on polygraph screening effectiveness, emphasizing the value of research in detecting deception despite chall
0 views • 13 slides
Road Safety Countermeasures and Resources
The Proven Safety Countermeasures showcase a brief history and practical applications such as roadside design improvements, reduced left-turn conflicts, and systemic low-cost measures at intersections. The PSCi 3.0 introduces innovative strategies like local road safety plans and the use of multiple
1 views • 4 slides
Understanding Financial Risks and Mitigation Strategies
Explore the concept of financial risks, learn how to identify and mitigate them, and improve your financial decision-making skills. This module covers definitions, typical risks, and strategies to safeguard your finances. Discover the four main clusters of financial risks and how to implement counte
0 views • 17 slides
Troubleshooting AC Input Voltage Variations in UCC28056EVM-296 and UCC25630-1EVM-291
Addressing issues with input voltage fluctuations in UCC28056EVM-296 and UCC25630-1EVM-291, where the voltage slowly decreases under different load conditions. Problems include output stopping at varying AC voltages based on load and hunching behavior at different load levels. Countermeasures are ne
0 views • 7 slides
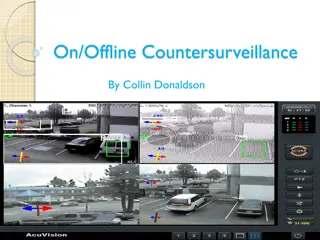
Privacy and Countersurveillance: Steps to Protect Your Data
Explore the challenges of modern countersurveillance and discover actionable steps to enhance your privacy online and offline. Learn how to assess your digital footprint, identify tracking entities, and implement countermeasures to safeguard your personal information effectively.
0 views • 13 slides
Understanding Unix/Linux Hacking Techniques
Explore Unix/Linux hacking techniques including footprinting, scanning, enumeration, vulnerability mapping, remote access, data-driven attacks, buffer overflow, input validation, and countermeasures. Discover methods to gain root access, exploit vulnerabilities, perform brute force attacks, and secu
0 views • 6 slides
Understanding Intrusion Detection Systems (IDS)
Intrusion Detection Systems (IDS) are software pieces that monitor computer systems to detect unauthorized intrusions and misuse, responding by logging activity, notifying authorities, and taking appropriate countermeasures. IDS help address security challenges, aiming to find and fix serious securi
0 views • 40 slides
Defending Against Cache-Based Side-Channel Attacks
The content discusses strategies to mitigate cache-based side-channel attacks, focusing on the importance of constant-time programming to avoid timing vulnerabilities. It covers topics such as microarchitectural attacks, cache structure, Prime+Probe attack, and the Bernstein attack on AES. Through d
0 views • 25 slides
Understanding Malware: Types, Symptoms, and Countermeasures
Malware is malicious software that can alter computer settings, behavior, files, services, ports, and speed. Sources of malware include insufficient security, honeypot websites, free downloads, torrents, pop-ups, emails, and infected media. Symptoms of malware include unusual computer behavior, slow
0 views • 9 slides
Mitigating Client Frame Tracking in IEEE 802.11 Networks
Unencrypted and predictable frame fields in IEEE 802.11 networks can lead to client frame tracking, compromising user privacy. The Client Frame Tracking Countermeasures (CFTC) proposal aims to prevent tracking across epoch boundaries by obfuscating critical fields like PN, SN, and AID. Each epoch, l
0 views • 17 slides
Antidotes and Screening Capacities for Dirty Bomb Attack Preparedness
Explore the preparedness strategies for dealing with the aftermath of a dirty bomb attack, focusing on antidotes, screening capacities, and medical countermeasures. Learn about the types of injuries, national stockpiles for radiological and nuclear emergencies, and different approaches to decorporat
0 views • 14 slides
Nuclear Security and Regulatory Oversight in the Slovak Republic
The Nuclear Regulatory Authority of the Slovak Republic is addressing new challenges in nuclear security, including threats such as drones and cyber attacks. They are working on updating legislation and implementing countermeasures to safeguard nuclear facilities. The focus is on enhancing cyber sec
0 views • 17 slides
Understanding Enumeration in Windows Networks
Enumeration in Windows networks involves obtaining information about accounts, network resources, shares, users, groups, applications, and banners. Techniques such as Telnet, netcat, Registry enumeration, Windows sources of information like protocols CIFS/SMB and NetBIOS, NetBIOS enumeration, SNMP e
1 views • 7 slides
Understanding Malicious Software in Data Security
Malicious software, or malware, poses a threat to the confidentiality, integrity, and availability of data within systems. It can be parasitic or independent, with examples like viruses, worms, Trojan horses, and e-mail viruses. Understanding the different types of malware and their modes of operati
0 views • 5 slides
Understanding Software-Defined Networking (SDN) Threats and Countermeasures
Software-Defined Networking (SDN) revolutionizes network management by separating control and data planes, providing flexibility, and enabling innovative flow handling. This presentation explores SDN concepts, OpenFlow protocol, operational distinctions from legacy networks, and the importance of to
0 views • 27 slides
Windows Security Overview and Best Practices
Windows operating system security overview focusing on preventing unauthorized access, privilege escalation, and password vulnerabilities. Includes countermeasures such as setting proper permissions, implementing strong passwords, and detecting vulnerabilities. Covering topics like remote password g
0 views • 6 slides
Advanced Safety Visualization Tool for Crash Countermeasures
UTMOST is a sophisticated tool designed for visualizing safety countermeasures and their impact on crash populations. It allows evaluation of various safety scenarios, exploring the potential benefits of advanced technologies and safety laws in reducing fatalities and injuries on the road. Through d
0 views • 24 slides
MATILDA Project Kick-Off Meeting Summary
The MATILDA Project, launched under the 2014 Call for Proposals for Prevention and Preparedness Projects, focuses on creating a multinational macro-module for post-earthquake building safety assessment and countermeasures in international emergencies. The project involves partners from Italy, Sloven
0 views • 17 slides
Understanding Human Authentication and Digital Identity
Explore the complexities of human authentication, classes of countermeasures, principles, personal and digital identity, and aspects of digital identity. Dive into the philosophical problem of personal identity, different types of identities, attributes, identifiers, verifiers, and the process of id
0 views • 33 slides
Web Application Security: Uncovering Common Attacks and Countermeasures
Explore common web application attacks such as eavesdropping and injection, along with effective countermeasures like encryption through SSL. Learn how to prevent attacks and secure your web apps.
0 views • 29 slides
Understanding Cross-Site Scripting (XSS) Attacks
Learn about the dangers of Cross-Site Scripting (XSS) attacks, including Reflected and Persistent XSS types. This malicious practice allows attackers to inject harmful code into websites, potentially compromising user data and security measures. Discover how XSS attacks work, their impact on online
0 views • 38 slides