Buy Australian counterfeit Notes for sale - hartogcounterfeitnotes.com
Australian counterfeit notes for sale, Buy Fake Australian Dollars, buy Australian dollars online, and Counterfeit Australian Dollars: we produce are also made of polymer plastic. They have advanced security features and a see-through window like the original bills. holograms have the 3D effect maki
5 views • 5 slides
Buy Adderall XR 25mg - trinexpharmacy.com
Australian counterfeit notes for sale, Buy Fake Australian Dollars, buy Australian dollars online, and Counterfeit Australian Dollars: we produce are also made of polymer plastic. They have advanced security features and a see-through window like the original bills. holograms have the 3D effect maki
7 views • 3 slides
Buy AED 100 Online - globcoff
Find the best Emirati Dirham for online sale by the best sellers of Globcoff, it\u2019s the counterfeit Docky. If you are looking for the cheapest price online to buy AED 100, you are in the right position because Counterfeit Docky is the leading brand to deliver the best Emitti Dirham online.\nCont
2 views • 2 slides
Buy Counterfeit British Pounds Online - @Eurosbillsnotes
Buy top-quality undetectable Buy Counterfeit British Pounds Online to cover most of your expenses. Get fake British bills to cover most of your expenses. The United Kingdom is one of the most expensive countries in the world, with a high standard of living that comes at a cost. With rising property
2 views • 1 slides
How Does Counterfeit Money Affect the Economy - geldbe.com
How does counterfeit money affect the economy? poses a significant threat to the stability and integrity of economies.\n\nWhatsapp: 49 176 93784298
1 views • 11 slides
Buy Counterfeit Notes Online - @Eurosbillsnotes
We have extensive experience in Bank Note production Undetectable Bank Notes we are on WHATSAPP Leave your mobile phone number and we will send you a message Whatsapp No: 1(424)242-2620Text on: 49 15510 365783Counterfeit Money For Sale US Dollar Notes Canadian Dollar Australian Dollar British Doll
2 views • 27 slides
Computer Peripherals and Interfacing
Computer peripherals are external devices that enhance the functionality of a computer. They include input devices like keyboards and mice, output devices like printers and monitors, and storage devices like hard disk drives and solid-state drives. Interfacing circuits connect these peripherals to t
1 views • 6 slides
Ascon: The Lightweight Cryptography Standard for IoT
The November 2023 document IEEE 802.11-23/2069r2 discusses the importance of secure data storage and communication in IoT devices due to the increasing number of connected devices and potential security threats. It introduces Ascon as a lightweight cryptography standard selected by NIST for protecti
0 views • 26 slides
Lightweight Cryptography Standard for IoT - November 2023 IEEE Presentation
IEEE 802.11-23/2069r1 presents Ascon as a lightweight cryptography standard for IoT devices. With the increasing number of connected devices, protecting data on IoT devices becomes crucial. NIST selects Ascon to safeguard small devices, offering authenticated encryption and hashing efficiently. Asco
3 views • 26 slides
Understanding Network Devices and Connectivity
Network devices play a crucial role in connecting computers and printers to networks, facilitating fast and secure data transfer. These devices, such as network interface cards and WiFi cards, help devices communicate effectively on the same or different networks. MAC addresses uniquely identify dev
6 views • 31 slides
Buy Counterfeit Money UK - undetectablecounterfeitbills.com
Buy Counterfeit Money UK, the demand for counterfeit money has seen a surge, especially in regions like the UK. However, navigating this market can be tricky due to the prevalence of scams and fraudulent activities. \nText\/ WhatsApp: 1 (507) 544-8062\nEmail: info@undetectablecounterfeitbills.com\n
0 views • 4 slides
Unveiling the Counterfeit Trinity in Revelation: A Revealing Revelation
Dr. Charles Zimmerman delves into the concept of the counterfeit trinity as depicted in Revelation, contrasting it with the genuine trinity of Father, Son, and Spirit. The images and descriptions provided shed light on the symbolic elements in the biblical narrative, including the dragon, the beast,
1 views • 26 slides
REAL COUNTERFEIT MONEY FOR SALE - UNDETECTABLECOUNTERFEITBILLS.COM
In the ever-evolving landscape of finance and commerce, the specter of counterfeit money looms as a persistent challenge. Counterfeit currency, often meticulously crafted to resemble genuine notes, poses a serious threat to the integrity of financial systems worldwide.\nContact: 1 (507) 544-8062\nE
1 views • 1 slides
HOW TO DETECT COUNTERFEIT NOTES - UNDETECTABLECOUNTERFEITBILLS.COM
How to detect counterfeit notes is a growing concern worldwide, posing significant risks to economies and individuals alike. Knowing how to detect counterfeit notes is crucial for both businesses and consumers to protect themselves from fraud. Contact: 1 (507) 544-8062 Email: info@undetectablecount
3 views • 1 slides
CAN YOU BUY COUNTERFEIT MONEY ONLINE - UNDETECTABLECOUNTERFEITBILLS.COM
The term \"counterfeit money\" describes counterfeit money that is created without official government approval and usually is an intentional attempt to mimic real money. The act of creating counterfeit money has a long history; the first instances can be found in ancient Greece and China. Contact:
1 views • 5 slides
How To Identify Counterfeit Money - undetectablecounterfeitbills.com
How To Identify Counterfeit Money is crucial not only for protecting your finances but also for maintaining the integrity of the economy. With counterfeiters becoming more sophisticated, it's essential to stay informed about the various methods and tools available to distinguish genuine currency fro
7 views • 1 slides
BUY COUNTERFEIT CAD ONLINE - UNDETECTABLECOUNTERFEITBILLS.COM
The demand for counterfeit money, particularly Canadian dollars (CAD), has increased recently. While some people may find it alluring to Buy Counterfeit CAD Online it\u2019s important to be aware of the dangers and repercussions involved in doing so. This article seeks to clarify the subject by prov
1 views • 1 slides
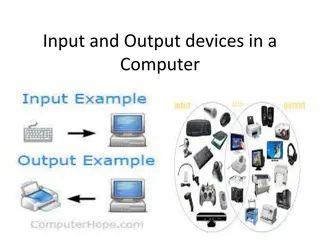
Understanding Input and Output Devices in Computing
In computing, input and output devices play a crucial role in enabling communication between users and computers. Input devices are used to enter data into a computer, while output devices display or provide the results of processed information. Common input devices include keyboards, mice, and joys
0 views • 17 slides
Understanding Basic Input/Output Operations in Computer Organization
Basic Input/Output Operations are essential functions in computer systems that involve transferring data between processors and external devices like keyboards and displays. This task requires synchronization mechanisms due to differences in processing speeds. The process involves reading characters
0 views • 11 slides
Understanding Electronic Components and Input/Output Devices
Explore the world of electronic components, input devices, and output devices through energy changes and symbol representations. Learn about LEDs, resistors, and energy conversions in a hands-on manner. Discover the role of various devices like microphones, solar cells, loudspeakers, and diodes in c
1 views • 24 slides
Counterfeit Detection Techniques in Currency to Combat Financial Fraud
Currency counterfeiting poses a significant challenge to the financial systems of countries worldwide, impacting economic growth. This study explores various counterfeit detection techniques, emphasizing machine learning and image processing, to enhance accuracy rates in identifying counterfeit curr
0 views • 15 slides
Understanding Computer Peripheral Devices: Definition, Examples, and Types
Learn about computer peripheral devices, which enhance a computer system's functionality. Examples include mice, keyboards, monitors, printers, and scanners. These devices can be categorized into input, output, and storage devices, each serving a specific purpose to expand the capabilities of your c
2 views • 13 slides
Understanding Programmable Logic Devices (PLD) in Digital Electronics
Programmable Logic Devices (PLDs) are versatile electronic components used to create reconfigurable digital circuits, distinct from fixed-function integrated circuits. PLDs require programming before use, enabling customization for specific functions. This article explores PLDs, digital electronic s
0 views • 10 slides
Automotive Grade 10 Joining Methods: Locking Devices Overview
Automotive Grade 10 explores joining methods using locking devices to prevent nuts from loosening due to movement and vibration. Friction-locking devices include lock nuts, stiff nuts, and special washers. Positive-locking devices tighten nuts securely with slotted nuts, crowned nuts, tab washers, a
1 views • 7 slides
Understanding Input and Output Devices in a Computer
Input devices play a crucial role in sending data to a computer, allowing users to communicate instructions for processing, display, storage, and transmission. Key input devices include keyboards and mice, each serving specific functions and enhancing data collection and accuracy. Discover the advan
0 views • 17 slides
Hepatitis B Vaccines: Genuine vs Counterfeit - Insights from Uganda National Drug Authority
Explore the difference between genuine and counterfeit Hepatitis B vaccines in Uganda, as detailed by the National Drug Authority. Learn about the authorized vaccine on the market, counterfeit batch numbers, fake addresses on invoices/receipts, and the availability of vaccines in private sectors. St
0 views • 8 slides
Perceptions of Medical Students on Point-of-Care Ultrasound Devices
This study evaluates medical students' perceptions of SonoSite Edge II and Butterfly iQ ultrasound devices for enhancing learning experiences in ultrasound and medicine. The research involved first-year medical students using both devices and providing feedback through pre- and post-session surveys.
3 views • 10 slides
Guide to Creating Access from Wired to Wireless Devices Using Airborne AP Ethernet Bridge
Explore a comprehensive guide on setting up access from wired to wireless devices using Airborne AP Ethernet Role Bridge. Learn how to connect a PLC and a wireless laptop to the same network, configure settings for both devices, and successfully ping between the devices. Follow step-by-step instruct
2 views • 7 slides
Overview of Computer Input and Output Devices
Input devices of a computer system consist of external components like keyboard, mouse, light pen, joystick, scanner, microphone, and more, that provide information and instructions to the computer. On the other hand, output devices transfer information from the computer's CPU to the user through de
0 views • 11 slides
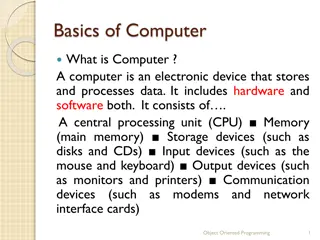
Understanding Basics of Computer Systems
A computer is an electronic device that stores and processes data using hardware and software components. It consists of a CPU, memory, storage devices, input/output devices, and communication devices. The CPU includes a Control Unit and Arithmetic Logic Unit, and the memory stores data in bytes. St
0 views • 57 slides
Unified Approach to Combat Counterfeiting with Digital Object Architecture
The talk discusses terminology, managing the supply chain, obtaining information about devices, and using digital object architecture to combat counterfeiting. It covers physical and digital entities, Internet resources, and the importance of unique persistent identifiers. The focus is on ICT device
0 views • 13 slides
Framework for Combatting Importation of Counterfeit Terminals in EACO Member States
This framework presentation by Mwende Njiraini from the Communications Authority of Kenya focuses on the definitions of counterfeit and substandard terminals, their impacts on industry, consumers, and governments, as well as proposed practical measures to combat the issue. It addresses challenges su
0 views • 26 slides
Addressing Counterfeit and Substandard ICT Devices in Brazil: The SIGA Project
The SIGA Project in Brazil aims to combat counterfeit and unauthorized ICT devices by implementing a centralized, automated, and scalable system to control the entrance of such devices into the market. Led by Anatel, the project involves key stakeholders to ensure the reliability and security of mob
0 views • 12 slides
Security Concerns and Future Challenges of Internet Connected Devices in Budva, Montenegro
With the increasing number of Internet-connected devices and IoT, the security concerns are escalating. In the past, communication was restricted to servers and terminals, but now everyone is connected globally. The future poses even greater risks with IoT becoming prevalent. Reasons for concern inc
0 views • 17 slides
Advancements in Drug Testing and Quality Control in Africa
This presentation discusses the use of near-infrared (NIR) spectral methods for rapid and reagent-free drug testing in Africa. The focus is on deploying low-cost infrared devices for verifying medicines, building databases on genuine medicines, and enhancing the capacities of drug professionals thro
0 views • 12 slides
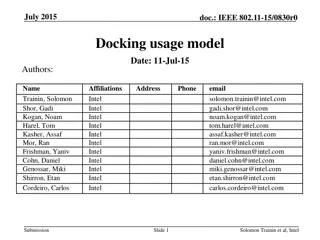
Wireless Office Docking Model for Multiple Devices
This document outlines a usage model for office docking involving wireless connections between mobile devices and various peripheral devices such as monitors, hard drives, printers, and more. It describes scenarios for single and multiple devices in both home and office settings, emphasizing the nee
0 views • 5 slides
Understanding I/O Systems and Devices
I/O systems and devices play a crucial role in computer operations. They can be categorized into block devices and character devices based on their functionalities. Block devices store information in fixed-size blocks with addresses, while character devices handle character streams. Some devices, li
0 views • 19 slides
Gait Device Selection for Children with Lumbar Level Myelomeningocele
This presentation discusses the considerations and choices of gait devices for children with lumbar level myelomeningocele. It covers the specific needs of pediatric patients, benefits and drawbacks of various devices, funding requirements, and clinical application through case studies. The material
0 views • 31 slides
Combatting Counterfeit and Substandard ICT Devices: IMEI Ecosystem & Its Role
The conference held in Geneva, Switzerland in November 2014 addressed the critical issue of combatting counterfeit and substandard ICT devices, focusing on the IMEI ecosystem and its significance in preventing the use of counterfeit devices. James Moran, Security Director at GSM Association, highlig
0 views • 12 slides
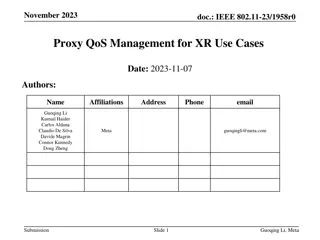
Proxy QoS Management for XR Devices in IEEE 802.11-23/1958r0 - November 2023
This document discusses the challenges faced by XR devices in terms of size, thermal constraints, cost, and power limitations leading to the proposal of Proxy QoS Management to enhance Wi-Fi performance. The aim is to leverage TGbn devices for improving legacy devices' connectivity within a Wi-Fi ne
0 views • 6 slides