Understanding Vulnerability: Meaning, Types, and Factors affecting Vulnerability
This article explores the concept of vulnerability, including its meaning, types (physical and social), and factors that contribute to vulnerability. It discusses the impact of hazardous events on communities, infrastructure, and the environment, and highlights the importance of awareness and prepar
26 views • 31 slides
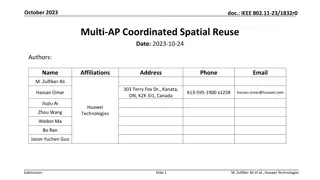
Coordinated Spatial Reuse in IEEE 802.11bn Standard
This contribution explores Coordinated Spatial Reuse (Co-SR) as a potential multi-AP feature for the IEEE 802.11bn standard. It discusses the trade-offs, proposes a method for downlink channel access, and evaluates its impact on goodput and packet delivery delay. The background highlights the gains
1 views • 17 slides
Understanding Risk Management in Environmental Geography and Disaster Management
Risk management in environmental geography and disaster management involves assessing the potential losses from hazards, evaluating vulnerability and exposure, and implementing strategies to mitigate risks. It includes calculating risk, dealing with risk through acceptance, avoidance, reduction, or
1 views • 10 slides
Comprehensive Guide to Vulnerability Mapping in Election Planning
Explore the significance of Vulnerability Mapping (VM) in empowering vulnerable voters, understand the concept, role of DEO/RO, and the objective of identifying and addressing voter vulnerability. The presentation emphasizes pre-poll and post-poll actions, remedial measures, and timelines, providing
3 views • 42 slides
Vulnerability Mapping (VM).Guidance Plan
Vulnerability Mapping (VM) is crucial in empowering vulnerable voters by identifying and addressing potential threats to their exercise of franchise. This guide explains the concept of vulnerability mapping, its role in ensuring free and fair elections, and the responsibilities of election officials
2 views • 42 slides
Understanding Telecom Security Testing: Vulnerability Assessment & Remediation
Telecom security testing is crucial for safeguarding infrastructure against hacks. Learn about vulnerability assessment, common weaknesses, types of vulnerabilities, severity scoring, and automated tools like Nessus and Nexpose. Explore network, web application, and host-based vulnerability testing
0 views • 18 slides
Leveraging Artifact Dependency Graphs for Software Vulnerability Detection
Explore how LLVM-GitBOM utilizes artifact dependency graphs to detect vulnerabilities in software dependencies. The presentation covers the overview of GitBOM, CVE detection, supply chain vulnerabilities, and the importance of precise build tools in vulnerability scanning. Learn about utilizing gito
0 views • 34 slides
Understanding Conflict of Interest in ACCME Accredited Activities
Conflict of Interest (COI) refers to financial relationships that may create biases in Continuing Medical Education (CME) activities when individuals have ties to commercial interests and can influence the content. ACCME requires disclosure to prevent potential bias in CME content. Non-disclosure ca
0 views • 18 slides
Understanding Coordinated Entry System (CES) in Homeless Services
Coordinated Entry is a strategic approach focusing on housing and service coordination to link individuals experiencing homelessness to appropriate resources. With a primary goal of quick identification and prevention of homelessness, the system assesses consumer needs and connects them to housing a
0 views • 12 slides
Understanding the Vulnerability Index for Small Island Developing States
This article discusses the concept of vulnerability in the context of countries, focusing on Small Island Developing States (SIDS). It explores the differences between vulnerability and poverty, the history of vulnerability index development from SIDS to Least Developed Countries (LDCs), and critiqu
8 views • 44 slides
Integrated Vulnerability Assessment and Human Security for Sustainable Livelihoods in the Solomon Islands
The approach to the Solomon Islands Integrated Vulnerability Assessment (SIIVA) and the Integrated Vulnerability and Adaptation Assessment (IVA) are key methodologies to assess climate change risks and prepare nations for adaptation. The objectives include informing national climate change policies,
0 views • 21 slides
Federal Agencies Guidance on Ethics, Compliance, and Audit Services under NSPM-33
The White House OSTP released guidance for federal agencies to implement NSPM-33 focusing on disclosure requirements, digital identifiers, consequences for violations, information sharing, and research security programs. The guidance emphasizes supporting open scientific inquiry and nondiscriminator
0 views • 10 slides
Economic Vulnerability Premium for SIDS - Webinar Insights
Presentation outlines applying Economic Vulnerability Index (EVI) for an Economic Vulnerability Premium in Small Island Developing States (SIDS) during ADF 13 cycle. Details ADF grants availability, grant allocation framework, performance-based allocation system, and modifications needed for SIDS.
0 views • 14 slides
Gender Considerations in Climate Vulnerability and Risk Assessments for Agriculture
This training workshop explores the intersection of gender, climate vulnerability, and risk assessments in adaptation planning for the agriculture sectors. It delves into how women and men may experience climate change effects differently and discusses ways to ensure gender considerations are includ
0 views • 6 slides
Understanding the Impact of the Insurance Act 2015 on Brokers and Insurers
The Insurance Act 2015 brings significant changes in insurance contract law, shifting from Duty of Disclosure to Fair Presentation. This Act influences both Brokers and Insurers, requiring clear and accessible disclosure of material circumstances. The remedies for misrepresentation and non-disclosur
0 views • 19 slides
Understanding Vulnerability and Capacity Issues in Civil Courts
Exploring vulnerability and capacity issues in civil courts, this content delves into the importance of addressing vulnerabilities of parties and witnesses for ensuring fair participation and quality evidence in legal proceedings. Topics covered include factors contributing to vulnerability, the rol
0 views • 21 slides
Updated Disclosure Rules for Financial Relationships in Continuing Education
ACCME updated its Standards for Integrity and Independence in Continuing Education, requiring disclosure of financial relationships with specific "ineligible companies" by all involved parties. The rules aim to enhance transparency and mitigate conflicts of interest in accredited continuing educatio
1 views • 5 slides
Understanding Disability Disclosure in Employment: Practical and Ethical Considerations
This presentation touches on the practical and ethical issues supported employment professionals face when dealing with disability disclosure. The agenda includes ADA provisions, successful disclosure strategies, the professional's role in the process, and available resources. The session covers dis
0 views • 33 slides
Understanding Disclosure of Adverse Clinical Events in Healthcare
Exploring the essential elements of disclosing adverse clinical events to patients and families in healthcare settings. It covers why disclosure is crucial, barriers to disclosure, triggers for disclosure, policies and procedures, and the other important aspects related to the disclosure process.
0 views • 8 slides
Coastal Vulnerability Assessment of Curacao, Netherlands Antilles
Conduct a comprehensive Coastal Vulnerability Audit of Curacao, Netherlands Antilles, using the Coastal Vulnerability Audit Tool (CVAT) to assess physical, human, and engineering infrastructure systems, as well as vulnerability, planning, and resiliency action plans. Consider factors such as climati
0 views • 10 slides
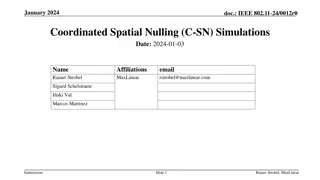
Coordinated Spatial Nulling (C-SN) Simulations in IEEE 802.11-24/0012r0
The document discusses the concept of Coordinated Spatial Nulling (C-SN) in IEEE 802.11-24/0012r0, focusing on spatial nulling feedback, synchronization needs, advantages of partial nulling, and comparison of half-coordinated versus fully coordinated scenarios. Simulation results are presented, anal
0 views • 19 slides
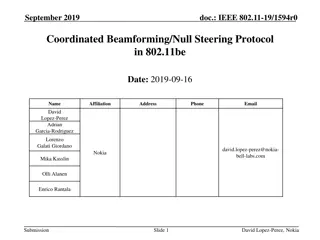
Coordinated Beamforming/Null Steering Protocol in IEEE 802.11be
Coordinated beamforming/null steering is a promising scheme in IEEE 802.11be for joint transmission/reception challenges. This protocol aims to efficiently realize gains by establishing semi-static inter-AP coordination, enhancing spatial reuse opportunities, implementing CSI acquisition, and managi
0 views • 15 slides
Evolution of Vulnerability Disclosure Practices
The history of vulnerability disclosure, from the early days of mailing lists and zines to the emergence of Full Disclosure and the debates around anti-disclosure groups. The timeline covers key events like the Morris worm, Code Red, the founding of Bugcrowd, and more, illustrating the evolution of
0 views • 11 slides
Impact of Management of Offenders Act on Disclosure Awareness Session
On 30 November 2020, new legislation including the Age of Criminal Responsibility (Scotland) Act 2019 and the Management of Offenders (Scotland) Act 2019 came into force, transforming the disclosure system in Scotland. These changes raise the age of criminal responsibility, reduce rehabilitation per
0 views • 10 slides
Reimagining Vulnerability: Rethinking the Body and Human Dignity
The notion of vulnerability is explored within the framework of the human body and dignity, challenging traditional concepts of autonomy and independence. Scholars like Martha Nussbaum and Fineman provide insights on the universal nature of vulnerability and advocate for a shift towards recognizing
0 views • 21 slides
Understanding Risks and Vulnerability in Risk Assessment
This module focuses on understanding risks, vulnerability, and conducting risk assessments in disaster risk management. It covers terminologies such as threats, hazards, vulnerability, and exposure, essential for prioritizing risks and initiating risk reduction measures.
0 views • 24 slides
Understanding Disclosure of Designs under CDR - Key Insights
The article explores the disclosure of designs under the Community Design Regulation (CDR) and Community Design Invalidity Regulation (CDIR). It discusses the criteria for public availability, evidence required for proving prior disclosure, and the basic rules for establishing the disclosure of a pr
0 views • 9 slides
Gamifying Vulnerability Reporting for Coordinated Disclosure at Microsoft Security Response Center
Christa Anderson, a Senior Security Program Manager at Microsoft's Security Response Center, discusses the importance of gamifying vulnerability report data to encourage coordinated disclosure. The MSRC Top 100, announced at Black Hat USA, plays a crucial role in the public credit strategy by recogn
0 views • 13 slides
Coordinated Request Process on OASIS for Multiple Transmission Systems
This presentation guides customers on using OASIS to establish and coordinate requests on multiple transmission systems. It covers steps such as submitting a Coordinated Request (CR), documenting requests, attesting to NAESB requirements, updating statuses, and approving or adjusting requests within
0 views • 9 slides
Governance Mechanisms and Financial Risks Disclosure in Developing Economies
Examining the impact of governance mechanisms on financial risk disclosure in developing economies, this study delves into theories, literature reviews, findings, policy implications, and conclusions. The research emphasizes the importance of adequate risk disclosure for investor trust and regulator
0 views • 9 slides
The Use of Self in Probation Practice: Understanding Self-Disclosure and Its Implications
Explore the concept of self-disclosure in probation practice, examining different methods, findings, and implications. Discover the two schools of thought regarding self-disclosure and delve into the various realms and subtypes of self-disclosure practices. Gain insights into the forms of self-discl
0 views • 25 slides
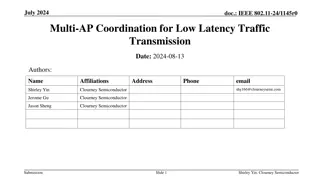
Multi-AP Coordination for Low Latency Traffic Transmission
The document discusses the integration of multi-access point (AP) coordination to enhance the transmission of low-latency traffic in wireless networks. It addresses the challenges and introduces modes of operation capable of reducing latency and improving reliability for low-latency (LL) traffic tra
0 views • 9 slides
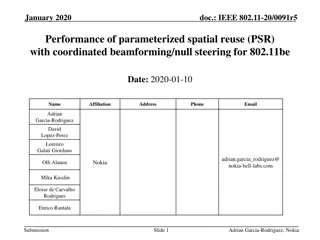
Performance Evaluation of Parameterized Spatial Reuse with Coordinated Beamforming for IEEE 802.11be
The study focuses on assessing the performance of parameterized spatial reuse (PSR) with coordinated beamforming/null steering for IEEE 802.11be. The framework allows coordinated sharing of uplink transmission opportunities among APs, demonstrating gains in synchronous coordinated beamforming system
0 views • 19 slides
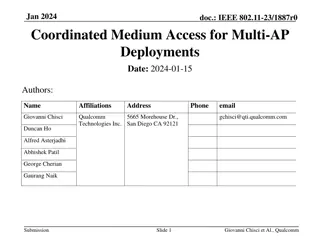
Coordinated Medium Access for Multi-AP Deployments in IEEE 802.11 Networks
The document discusses a solution to reduce latency, increase throughput, and improve reliability in networks with latency-sensitive traffic by introducing coordination between access points (APs). This involves leveraging mechanisms like Restricted TWT (rTWT) and Coordinated rTWT (C-rTWT) to facili
0 views • 12 slides
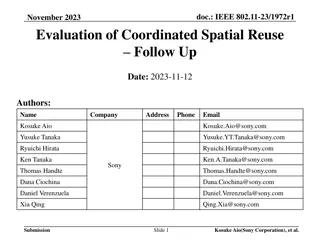
Evaluation of Coordinated Spatial Reuse in Multi-AP Scenarios for IEEE 802.11-23/1972r1
Evaluation of Coordinated Spatial Reuse (SR) in a 4AP scenario for IEEE 802.11-23/1972r1 in November 2023. The study focuses on improving throughput in multiple BSS environments through coordinated SR. The simulation parameters include AWGN channel, pathloss exponent, noise figure, and other key fac
0 views • 15 slides
Enhancing Nuclear Security Through Creative Vulnerability Assessment
Creative and effective vulnerability assessment and testing are essential in nuclear security to identify weaknesses and improve defense systems against intelligent adversaries. The need for in-depth assessment and realistic testing is emphasized to uncover vulnerabilities that adversaries may explo
0 views • 8 slides
Understanding Vulnerability in Research Populations
Vulnerability in research populations refers to being exposed to harm without the ability to protect oneself adequately. Factors contributing to vulnerability include intrinsic limitations like decision-making capacity and situational influences such as political or economic circumstances. Different
0 views • 22 slides
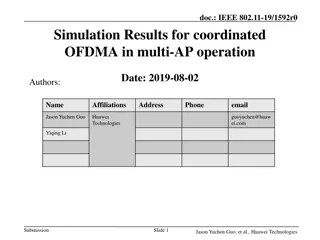
Simulation Results for Coordinated OFDMA in Multi-AP Operation
Multi-AP operation, specifically Coordinated OFDMA, is evaluated through system-level simulation results in a two-BSS scenario. The performance metrics include burst throughput and delay in a burst traffic model. Transmission procedure involves two APs sharing 160MHz bandwidth. The study aims to sho
0 views • 9 slides
Exploring Vulnerability and Power Dynamics in Imperial Rome: Phaedrus' Perspective
Delve into the intricate relationship between constructions of vulnerability in imperial Latin texts and the material reality of vulnerability in ancient Rome. Discover how cultural perceptions of male citizen invulnerability rely on affirming vulnerability in others. Uncover the strengths of vulner
0 views • 10 slides
New Disclosure Rules for Continuing Education
ACCME updated its Standards for Integrity and Independence in Accredited Continuing Education in December 2020, leading to changes in ACLP's disclosure reporting rules. Key changes include reporting only financial relationships with "ineligible companies," extending the reporting period to 24 months
0 views • 5 slides