National Small Enterprise Amendment Bill
Parliamentary Portfolio Committee on Small Business Development covers the National Small Enterprise Amendment Bill. It includes insights on the Small Enterprise Development Finance Agency, dispute resolution mechanisms, and transitional arrangements. The discussion highlights the importance of smal
3 views • 13 slides
Top Crypto Launchpads To Watch In 2024
At BlockchainX tech, we help startups, medium-sized enterprises, and large-sized businesses by providing end-to-end blockchain development services such as token creation, token sale distribution, landing page design, whitepaper writing, and smart contract creation. \nhttps:\/\/www.blockchainx.tech\
4 views • 7 slides
GB0-510 Exam Prep: A Comprehensive Study Plan | Sample Questions
Start Here --- https:\/\/bit.ly\/3wDbi6i --- Unlock the secrets to acing the H3C GB0-510 exam and becoming a certified Security Network Engineer! This PDF is your ultimate guide to mastering the H3CNE-Security certification, focusing on the planning, design, configuration, and maintenance of securit
4 views • 16 slides
Overview of U.S. General Services Administration's Office of Small and Disadvantaged Business Utilization (OSDBU)
This overview discusses the role of the Office of Small and Disadvantaged Business Utilization (OSDBU) within the U.S. General Services Administration (GSA). It highlights the advocacy for small businesses in federal acquisitions, inclusion of small businesses as contractors, and management of small
3 views • 51 slides
Understanding the Role of Security Champions in Organizations
Security Champions play a vital role in decision-making concerning security engagement, acting as a core element in security assurance processes within a team. They foster a security culture, reduce dependency on the CISO, and promote responsible autonomy and continuous security education in the org
3 views • 13 slides
Unveiling the Power of User Experience Services for Startups and Small Businesses
In today's highly competitive marketplace, small and small-sized businesses face many obstacles to establishing their presence and building an advantage. In this scenario, investing in user experience (UX) services is an imperative strategy to stand out, improve customer satisfaction and drive your
0 views • 9 slides
The Role of a Blockchain Development Company
At BlockchainX tech, we help startups, medium-sized enterprises, and large-sized businesses by providing end-to-end blockchain development services such as token creation, token sale distribution, landing page design, whitepaper writing, and smart contract creation. https:\/\/www.blockchainx.tech\/
1 views • 8 slides
Scaling BI Dashboards for Small to Medium-Sized Enterprises in the UK
Scaling BI dashboards is crucial for small to medium-sized enterprises (SMEs) in the UK to effectively manage their growing data needs. This blog delves into the unique challenges and best practices for implementing scalable Business Intelligence (BI) solutions.
1 views • 6 slides
Pedagogical Shift in Physical Science: Constructing Knowledge Through Learner-Centered Experiences
There is a significant pedagogical shift in physical science education from viewing science as a fixed body of knowledge to emphasizing the process of constructing knowledge. Learners are now placed at the center stage, engaging in inquiry-based learning, critical thinking, and collaborative interac
3 views • 21 slides
Effective Strategies for Overcoming Test Anxiety
Learn practical methods to combat test anxiety in this 1-hour workshop by CCAMPIS Kayla Taylor. Topics covered include avoiding test anxiety, preparing effectively for tests, identifying and reducing sources of anxiety, quelling anxiety, test-taking strategies, and stress management. The PASS method
0 views • 13 slides
AEP Enterprise Security Program Overview - June 2021 Update
In the June 2021 update for the Kentucky Interim Committee on Natural Resources and Energy, American Electric Power (AEP) addresses recent ransomware events, their security program updates, and details about their enterprise security measures. AEP, one of the largest electric utilities in the U.S.,
0 views • 12 slides
Understanding Artificial Neural Networks From Scratch
Learn how to build artificial neural networks from scratch, focusing on multi-level feedforward networks like multi-level perceptrons. Discover how neural networks function, including training large networks in parallel and distributed systems, and grasp concepts such as learning non-linear function
1 views • 33 slides
Survival Strategies for Medium-Sized Orthopedic Group Practices
Understanding the challenges faced by medium-sized orthopedic group practices and implementing strategies such as high-quality specialized care, leveraging mid-level providers, and diversifying revenue streams are key to survival in the changing healthcare landscape.
0 views • 26 slides
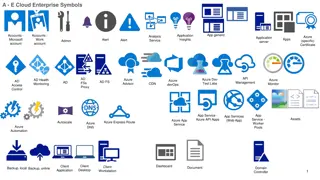
Symbolic Representation of Azure Cloud Enterprise Services
The images depict a variety of symbols representing different Azure cloud enterprise services, including application insights, analysis, monitoring, security, storage, virtual networks, and more. Each symbol represents a specific aspect or component of Azure services, such as VPN gateways, firewalls
0 views • 6 slides
Understanding Plant Tissue Culture Media and Their Importance in In Vitro Growth
Plant tissue culture media play a crucial role in the in vitro growth and morphogenesis of plant tissues. The composition of culture media depends on the specific plant species and the type of material used for culture. Various types of media, such as White's medium, MS medium, B5 medium, N6 medium,
0 views • 6 slides
Understanding Software Testing: Test Cases, Selection, and Execution
Software testing plays a crucial role in identifying and resolving issues within software products. Test cases, selection, and execution are fundamental aspects of the testing process. Test cases define conditions for testing software functionality, with a focus on repeatability and data specificity
2 views • 36 slides
University Math Placement Test Overview
The University Math Placement Test is a tool to help place students accurately into math courses, ensuring their success. It consists of three practice tests - Algebra, Trigonometry, and Precalculus. Students start with the Practice Algebra Test and have the opportunity to advance based on their sco
0 views • 13 slides
Observing Optimization of IEEE 802.11be Release 1 for Enterprise AP Use Cases
IEEE 802.11be is being optimized for enterprise use cases due to existing features that can be enhanced. The focus is on educating about enterprise Wi-Fi operations and increasing awareness within the wider community. Various enterprise use cases such as call centers, events, hospitals, and office d
0 views • 13 slides
Coordinated AP-Assisted Medium Synchronization Recovery in IEEE 802.11-23/1980r0
This document discusses the proposal for medium synchronization recovery leveraging multi-AP coordination for multi-link devices in IEEE 802.11be EHT networks. It introduces the concept of AP-assisted medium synchronization recovery to assist non-AP STAs in transmitting frames without causing collis
0 views • 7 slides
Understanding Computer Communication Networks at Anjuman College
This course focuses on computer communication networks at Anjuman College of Engineering and Technology in Tirupati, covering topics such as basic concepts, network layers, IP addressing, hardware aspects, LAN standards, security, and administration. Students will learn about theoretical and practic
0 views • 72 slides
Constructing Perpendiculars: Shortest Distance to a Point
Learn how to find the shortest distance from a point to a line, ensuring the path taken is efficient and direct. By constructing a perpendicular from the point to the line, you guarantee the shortest possible route, creating a right angle with the line. Explore the process of constructing perpendicu
2 views • 17 slides
Introduction to Neural Networks in IBM SPSS Modeler 14.2
This presentation provides an introduction to neural networks in IBM SPSS Modeler 14.2. It covers the concepts of directed data mining using neural networks, the structure of neural networks, terms associated with neural networks, and the process of inputs and outputs in neural network models. The d
0 views • 18 slides
Overview of GEF Project and Program Cycle
The Global Environment Facility (GEF) operates through key policies and partnerships to support projects and programs targeting global environmental impacts. The GEF cycle includes project modalities like Full-Sized Projects and Medium-Sized Projects, alongside enabling activities. The process invol
0 views • 9 slides
Test Security Guidelines for 2015-16 CAASPP Administration
This content provides detailed information on the test security guidelines and procedures for the California Assessment of Student Performance and Progress (CAASPP) 2015-16 administration. It covers requirements in the testing regulations, test security agreements, affidavits, and the purpose and go
2 views • 42 slides
IT Solutions for Small to Medium Businesses
Flamingo Computer Services and Networking offers comprehensive IT support and solutions for small to medium business networks. Challenges in backup solutions are addressed with the Symantec Backup Exec System Recovery, ensuring reliable and fast recovery from various threats. The impact of longer re
0 views • 13 slides
Understanding Enterprise Network Security and Firewalls
Exploring key aspects of enterprise network security, this presentation delves into topics such as perimeter control, host-based security, intrusion detection, and various types of firewalls. It highlights filtering rulesets, requirements for outbound traffic, and the importance of dynamic packet fi
0 views • 19 slides
NSCAS Test Administration Orientation 2022-2023 Overview
The Nebraska Student-Centered Assessment System (NSCAS) Test Administration Orientation for 2022-2023 provides information on the assessments, security procedures, training goals, and administration guidelines for ensuring fairness and equity in testing. It outlines the security measures, contact in
0 views • 28 slides
Oregon Statewide Assessment System (OSAS): Test Security Training Overview
This information outlines the test security training requirements for Designated Test Coordinators (DTCs), School Test Coordinators (STCs), and Test Administrators (TAs) in Oregon's Statewide Assessment System (OSAS). It covers topics like ensuring a secure testing environment, handling printed test
0 views • 20 slides
Enhancing Medium Access Efficiency in IEEE 802.11 Networks
This presentation discusses the utilization of chirp signals for Ultra High Rate (UHR) STAs to access the medium efficiently, transmit reliably at reduced power levels, and handle interference challenges in IEEE 802.11 networks. It explores the concept of chirps, their differentiation from other pro
0 views • 20 slides
Wireless Sensor Networks: Medium Access Protocols Overview
This collection of images presents key concepts in wireless sensor networks, focusing on medium access protocols, the ISO/OSI reference model, types of conflict resolution, contention-free protocols, Bitmap protocol, ALOHA algorithm, and its analysis and efficiency. Various protocols and algorithms
0 views • 83 slides
Enhancing Hardware and Software Security in Public Communications Networks
This presentation highlights the objectives, deliverables, and members of Working Group 6 focused on improving the security of hardware and software in public communications networks. The group aims to develop best practices, recommendations, and voluntary mechanisms to enhance overall security. Mem
0 views • 13 slides
Digitalization Impacts on Smart Places: A Focus on Small and Medium-sized Towns
The webinar explores the implications of digitalization for Small and Medium-sized Towns (SMSTs) within the context of cultural geography. It delves into the evolving debates surrounding digital inequalities, the challenges of addressing local (rural) needs through digital adoption, and the role of
0 views • 6 slides
Understanding Network Analysis: Whole Networks vs. Ego Networks
Explore the differences between Whole Networks and Ego Networks in social network analysis. Whole Networks provide comprehensive information about all nodes and links, enabling the computation of network-level statistics. On the other hand, Ego Networks focus on a sample of nodes, limiting the abili
0 views • 31 slides
Challenges and Initiatives in VA Research Enterprise
The VA Research Enterprise faces institutional challenges in conducting industry and other studies, requiring collaboration and dedication from its diverse workforce. With a focus on advancing Veteran well-being, the enterprise upholds core values such as operational excellence, engaged people, and
0 views • 20 slides
Understanding the Nocebo Effect in Communicating Nuclear Waste Disposal with SME Communities
This research explores the impact of the nocebo effect on ethical practices when communicating nuclear waste disposal to small and medium-sized enterprise (SME) communities. It aims to evaluate and reduce potential fears caused by misinformation on radioactive waste management. The study delves into
0 views • 10 slides
Starting an Enterprise in Finland: A Comprehensive Guide for Entrepreneurs
Entrepreneurship in Finland is thriving, with a significant number of small and medium-sized enterprises making up the business landscape. This guide provides insights into the types of companies you can establish, support available for start-up companies, and key factors to consider such as funding
0 views • 9 slides
Advancing Enterprise Solutions Presentation for Discussion
This presentation focuses on advancing enterprise solutions within the Government of Canada, particularly in the context of whole-of-government approaches and digital transformation. It discusses the importance of a holistic enterprise approach, governance solutions, and how enterprise is addressed
0 views • 17 slides
Comprehensive DevOps Security Training Overview
This Certified DevOps Security Practitioner course provides a deep dive into implementing DevSecOps, integrating security into the DevOps processes. Covering topics like security testing, Docker security, automation, and more, the training aims to equip participants with the necessary skills to embe
0 views • 5 slides
Essential Guidelines for Statewide Assessment Security Training
This resource outlines key objectives for successful test administration, test security standards, accommodation resources, and responsibilities for building coordinators and test administrators. It emphasizes the importance of adhering to test security measures to ensure the accuracy and integrity
0 views • 20 slides
Comprehensive Integrated Security Solution Overview by Microsoft
Ponemon Institute's Cost of Data Breach Study reveals the significant financial impacts of data breaches. Microsoft offers an intelligent, unified enterprise defense solution through Microsoft Threat Protection, Azure Security Center, and Azure Sentinel. This comprehensive array of integrated securi
0 views • 6 slides