Parliamentary Procedure
Learn about the role, principles, and importance of parliamentary procedure in running effective meetings. Explore the basics of Robert's Rules of Order, agenda building, the relationship between parliamentary procedure and the Brown Act, and tools for chairs to facilitate discussions and decision-m
1 views • 25 slides
Doula Billing Procedure Update for Oregon Health Plan Providers
Understand the new billing procedure for doula services under the Oregon Health Plan, including the new procedure code T1033, modifiers HD and 22, and the importance of the update. Learn about correct billing and coding, global billing examples, and different billing scenarios for doula services. Qu
2 views • 8 slides
Overview of Common Procedure for Requesting COAMU Advice
This content provides information on the common procedure for requesting COAMU advice in the Brabant Wallon, Hainaut, Namur, Liège, and Luxembourg regions. It covers topics such as the legal basis, reasons for procedure reform, principles of the new procedure, and steps for implementation. Key poin
10 views • 16 slides
Computational thinking as 21st Century skill
Computational thinking is a critical skill for the digital age, involving problem-solving techniques that enable computers to process information effectively. It precedes programming and requires breaking down complex problems into manageable steps. Educators emphasize computational thinking exercis
7 views • 4 slides
Master's Program in Computational Drug Discovery and Development - Fall 2024 Curriculum
This Master's program offers a comprehensive curriculum focusing on Artificial Intelligence, Computational Drug Discovery, and Development. With a blend of cutting-edge technologies and practical applications, students delve into techniques, AI/ML, big data mining, modeling, and more. Through intens
1 views • 7 slides
Understanding Computational Linguistics and Natural Language Processing
Explore the fascinating fields of Computational Linguistics and Natural Language Processing (NLP), delving into their development, applications, and significance. Learn about the study of human languages in computational models, the importance of corpora in linguistic research, and the various types
3 views • 33 slides
Harvard Procedure Guidelines and Rules for Model United Nations
In this guide, you will explore the rules and procedures specific to the Harvard Procedure in Model United Nations. It covers general rules, guidelines on resolutions and voting, language requirements, courtesy expectations, rules of procedure, motions, points of order, and parliamentary inquiries.
6 views • 20 slides
Understanding Parliamentary Procedure for Effective Meetings
Parliamentary procedure is a set of rules and customs that govern meetings in various organizations. This system ensures fair and efficient decision-making by outlining the proper conduct of meetings, including making and handling motions, and the role of the presiding officer. By following parliame
0 views • 21 slides
IEEE 802.11-21/1321r1 WLAN Sensing Procedure Proposal
This document by Solomon Trainin from Qualcomm presents a proposal on aligning the SFD for the WLAN sensing procedure. It aims to resolve contradictions, optimize behavior, and introduce a structured WLAN sensing procedure. The content outlines phases, terminology, setup, measurement, and reporting
0 views • 8 slides
Tepid Sponging Procedure in Patient Care
Tepid sponging is a technique used to reduce body temperature in patients with fever. This procedure involves applying lukewarm water to the skin surface to promote heat dispersal. Key steps include preparing the patient, collecting equipment, sponging with tepid water, and monitoring the patient's
0 views • 7 slides
Worksafe Procedure NR/L2/OHS/00112 Safety Hour Overview
The Worksafe Procedure NR/L2/OHS/00112 was introduced in 2009 to empower Network Rail employees to raise safety concerns and stop work if necessary. This procedure ensures a safe work environment by allowing employees to assess risks, establish safe work practices, and receive support from managemen
0 views • 8 slides
Briefing on the Criminal Procedure Amendment Bill [B12-2021] to the Portfolio Committee on Justice and Correctional Services
The Criminal Procedure Amendment Bill aims to address the constitutional invalidity of section 154(3) of the Criminal Procedure Act by enhancing protection for child victims, accused, and witnesses in criminal proceedings. The Bill proposes prohibiting the publication of information revealing their
0 views • 12 slides
Evolution of Procedural Law in Continental European Legal History
The journey of procedural law in Continental European legal history, from the challenges faced by glossators in creating Romano-canonical procedure to the discussions on canonic procedure in canon law. Explore the intricacies of legal procedure development and the influences of historical texts such
0 views • 36 slides
Understanding Computational Complexity Through Statistical Physics
In the age of vast data growth, tackling complex computational problems is crucial. Statistical physics can provide insights into handling the new challenges arising from the exponential increase in data. As we delve into understanding the complexity of computational tasks, it becomes evident that e
0 views • 24 slides
Introduction to Priority Search Trees in Computational Geometry
This lecture outlines the structure and query process of Priority Search Trees (PST) in computational geometry. It covers heap-based point queries, range trees for windowing queries, handling query ranges in 1D and 2D spaces, and using heaps to efficiently handle query ranges. The content discusses
1 views • 18 slides
Lumbar Puncture: Procedure, Complications, and Clinical Applications
Lumbar puncture, also known as LP, is an invasive procedure used to obtain cerebrospinal fluid (CSF) for diagnostic and therapeutic purposes. This procedure has a long history dating back to ancient times, with modern techniques developed in the late 19th century by Heinrich Quincke. LP is crucial f
2 views • 11 slides
Lumbar Puncture: Indications, Contraindications, and Post-procedure Considerations
Lumbar puncture is a medical procedure involving the insertion of a needle into the spinal subarachnoid space to collect cerebrospinal fluid for diagnostic or therapeutic purposes. Indications for performing a lumbar puncture include suspicion of meningitis, subarachnoid hemorrhage, CNS diseases lik
0 views • 17 slides
Understanding Procedure Texts and their Structure
Procedure texts are instructional pieces of writing that explain how something works or how to perform a specific activity. They typically consist of three main definitions: texts that explain how to use something, texts that provide instructions for a particular activity, and texts that address hum
0 views • 10 slides
Update on HV Tuning Procedure for KM3NeT Group Meeting
Recap and updates on the HV tuning procedure for the KM3NeT group meeting include moving to a procedure based on gain estimates, implementing HV-fitting routines in JFitHV, and addressing issues related to linear behavior, fit ranges, and outliers. Solutions for maximizing the ToT-fits efficiency ar
0 views • 11 slides
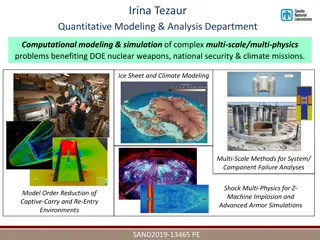
Advancing Computational Modeling for National Security and Climate Missions
Irina Tezaur leads the Quantitative Modeling & Analysis Department, focusing on computational modeling and simulation of complex multi-scale, multi-physics problems. Her work benefits DOE nuclear weapons, national security, and climate missions. By employing innovative techniques like model order re
0 views • 6 slides
Basis Production Procedure for AGATA through GRETINA Signal Decomposition
This presentation outlines the detailed procedure for generating basis signals in the context of AGATA data processed through GRETINA signal decomposition. It covers the generation of pristine basis signals, superpulse analysis, and the creation of cross-talk corrected basis files. The process invol
0 views • 19 slides
A-29 Emergency Landing Gear Procedure
This emergency procedure outlines steps to follow in case of low pressure in the landing gear accumulator of the A-29 aircraft. It details actions to take for the emergency gear situation, including the response for low emergency brake accumulator pressure and the procedure to follow when the landin
0 views • 4 slides
Understanding Computational Biology: Proteins, DNA, RNA, Genetics, and Evolution
Computational Biology combines computational methods with molecular biology to solve biological problems. Explore topics like proteins, DNA, RNA, and genetics, learning about amino acids, nucleotides, and the genetic code. Understand the evolutionary processes of mutation and natural selection.
0 views • 21 slides
Trial of Warrant Cases by Magistrates under the Code of Criminal Procedure 1973
The Code of Criminal Procedure 1973 Chapter 19 outlines the procedure for trial of warrant cases by magistrates where the prosecution presents evidence to support the case against the accused. Section 244 requires the magistrate to hear the prosecution and take all evidence presented. If the evidenc
0 views • 12 slides
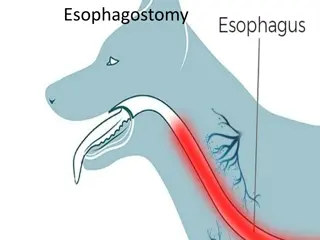
Esophagostomy Surgical Procedure Overview
Esophagostomy is a surgical procedure mainly performed to address foreign bodies or esophageal diverticula in animals like horses, cattle, dogs, and cats. The operation involves accessing the esophagus, removing the foreign body, and suturing the esophageal wall. Key steps include making an incision
0 views • 14 slides
Introduction to Computational Number Theory in Cryptography
Practical private-key cryptography can be done without advanced math, but understanding computational number theory is essential for public-key encryption. This field focuses on the computational difficulty of problems, analyzing algorithms' running times, classifying problems as easy or hard based
0 views • 27 slides
Uniform Procedure for Preemption in IEEE 802.11-24 Standard
The presentation discusses a uniform procedure for preemption in the IEEE 802.11-24 standard, focusing on different cases where a STA preempts another's TXOP to transmit low latency (LL) traffic. It proposes a simplified design and implementation approach for handling preemptions efficiently. The pr
0 views • 12 slides
Understanding the Essence of Computer Science and Computational Thinking
Delve into the fundamentals of Computer Science and Computational Thinking through chapters discussing the nature of science, predictions in physics, and the distinction between Computer Science and Computer Information Systems. Explore the relationships between Math, Physics, and Computer Science i
0 views • 29 slides
Advancing Auditory Enhancement: Integrating Spleeter with Advanced Remixing Techniques in The Cadenza Challenge 2023
Our project for The Cadenza Challenge 2023 focused on improving audio for headphone users with hearing loss by integrating Spleeter's deep learning capabilities. We utilized N-ALR prescriptions, Butterworth bandpass filters, and Dynamic Range Compression to enhance audio quality. By leveraging advan
0 views • 19 slides
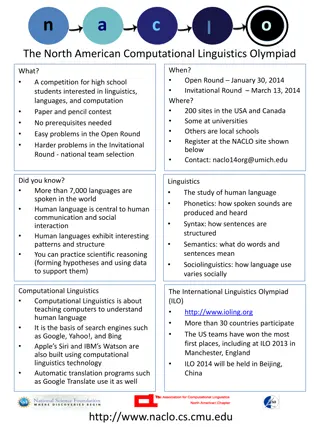
North American Computational Linguistics Olympiad: A Competition for High School Students
The North American Computational Linguistics Olympiad (NACLO) is a competition for high school students interested in linguistics, languages, and computation. It consists of an Open Round in January and an Invitational Round in March, with no prerequisites needed. Participants tackle easy problems i
0 views • 4 slides
A-29 Emergency Procedure: Overpressure (CAB PRES)
An overview of the emergency procedure for overpressure (CAB PRES) in the A-29 aircraft. The procedure outlines actions to take when cockpit differential pressure exceeds 5.75 psi, including switching off the air conditioning, maintaining a maximum altitude of 25,000 ft, and following the SUPPLY FAI
0 views • 4 slides
Fundamentals of Criminal Law and Procedure
Explore the key aspects of criminal law and procedure, including definitions of crime, the role of criminal procedure, sources of law, phases of the criminal process, participants involved, and rules of evidence in legal proceedings. Gain insight into how criminal law is distinct from civil law and
0 views • 24 slides
Mississippi Center for Supercomputing Research (MCSR) Overview
The Mississippi Center for Supercomputing Research (MCSR) supports computational research in various fields like Chemistry, Bioinformatics, Physics, Engineering, and Computer Science for Mississippi IHLs. They provide training to optimize computational resources, offer classes for computational trai
0 views • 23 slides
Exploring Computational Theories of Brain Function
In this series of images and text snippets, the discussion revolves around the emerging field of computational theories of brain function. Various aspects such as symbolic memories, the relationship between the brain and computation, the emergence of the mind from the brain, and computational thinki
0 views • 53 slides
Computational Earth Science Course Overview
Explore the world of Computational Earth Science with Bill Menke as the instructor and Emily Glazer as the teaching assistant. The course aims to help you become proficient in applying Python-based computational methods to understand dynamic Earth Science phenomena. Through modeling, you will gain i
0 views • 34 slides
UL Sync Channel Access Procedure in IEEE 802.11-20/1730r1
The document discusses the UL sync channel access procedure in IEEE 802.11, focusing on the conditions under which an STA affiliated with an MLD can initiate transmission, manage its backoff counter, and follow specific rules for accessing the channel. It proposes a straw poll to gather support for
0 views • 8 slides
Exploring Computational Play in Early Childhood Education: DLI 2023 Workshop
The workshop at the 8th EAI International Conference on Design, Learning & Innovation (DLI 2023) in Aalborg aims to delve into the application of computational play with mathematics in early childhood education. Through live sessions and discussions, opportunities and challenges in utilizing computa
0 views • 7 slides
Slum Infrastructure Upgradation Standard Operating Procedure
This standard operating procedure outlines the process for identifying, listing, and upgrading slums in Odisha. It includes steps such as Participatory Infrastructure Needs Assessment, benchmarking, I-GAP preparation, slum intervention identification, and completion of upgradation projects. The proc
0 views • 16 slides
Understanding Client-Server Communication and Remote Procedure Calls
Developing client-server applications involves using socket programming for communication between processes on different machines. Remote Procedure Calls (RPC) enable calling procedures on remote machines as if they were local. Explore how parameters are passed in local and remote procedure calls, a
0 views • 22 slides
Emergency Procedure for Brake Accumulator Low Pressure in A-29 Aircraft
This emergency procedure outlines the steps to address low pressure in the brake accumulator of the A-29 aircraft. It explains the implications of low pressure, the actions to take, and the importance of using chocks in the aircraft parking area. The procedure ensures the safe braking of the aircraf
0 views • 4 slides










![Briefing on the Criminal Procedure Amendment Bill [B12-2021] to the Portfolio Committee on Justice and Correctional Services](/thumb/157093/briefing-on-the-criminal-procedure-amendment-bill-b12-2021-to-the-portfolio-committee-on-justice-and-correctional-services.jpg)