Understanding Hydraulics and Pneumatics in Industrial Applications
This chapter explores the structure, advantages, and disadvantages of hydraulic and pneumatic systems utilized in industries for power transmission. Fluid power technology involving liquids or gases confined in systems like hydraulic (using liquid petroleum oils) and pneumatic (using compressed air)
1 views • 18 slides
TOP 10 COMPANIES IN ELECTROLYZERS MARKET
Hydrogen is either stored as a compressed gas or liquefied, and since hydrogen is an energy carrier, it is used to power any hydrogen fuel cell electric application such as trains, buses, trucks, or data centers. The three main types of electrolyzers are proton exchange membrane (PEM), alkaline, and
3 views • 3 slides
Why Refrigerated Air Dryers Are Essential for Your Compressed Air System
If you want a proper air supply, then you need to maintain quality and efficiency in your air compressors. One essential component for maintaining peak performance and efficiency is the refrigerated air dryer. These devices remove moisture from compressed air, preventing damage to equipment and ensu
3 views • 6 slides
Impact of Burning Firewood vs. Compressed Logs on PM2.5 Concentrations
Study comparing the effects of burning firewood and compressed logs on PM2.5 concentrations. Results show that compressed logs produce significantly lower particulate matter pollution. Recommendations include using compressed wood for reduced smoke emission. Various brands and types of compressed lo
0 views • 10 slides
Understanding Suffix Trees: A Comprehensive Overview
Explore the concept of suffix trees through detailed explanations, diagrams, and examples. Learn about tries, compressed tries, suffix tree construction algorithms, and more. Discover how suffix trees are used to efficiently store and search for substrings in a string.
1 views • 21 slides
Adaptations of Aquatic Specimens, with a Focus on Sea Snakes
Aquatic specimens, particularly sea snakes of the subfamily Hydrophiinae, exhibit fascinating adaptations for their fully aquatic lifestyle. These marine snakes are uniquely adapted for life in the sea, with specialized features such as paddle-like tails, compressed bodies, and the ability to respir
0 views • 16 slides
Diverse Approaches to Modern Work Environment
Explore alternative ways of working, including permanent full-time positions, part-time roles, flextime arrangements, and compressed workweeks. Delve into job creation, the impact of AI, and examples of varied work setups. Discover how these methods can influence your career planning and meet contem
0 views • 27 slides
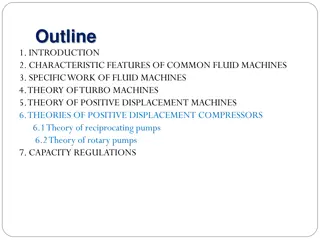
Understanding Positive Displacement Compressors in Fluid Machinery
Study the theoretical principles and operation of positive displacement compressors, focusing on reciprocating compressors in the Chemical Process Industry. Learn about indicator diagrams and the unique characteristics of reciprocating compressors. Explore the main components in compressed air syste
1 views • 32 slides
Compression-Driven Point Set Pattern Discovery in Music
Compression-driven point set pattern discovery in music explores the principle of parsimony in data representation. By applying compression-based algorithms, researchers aim to simplify the description of musical data, leading to better performance in tasks such as classification of folk songs, simu
0 views • 12 slides
Microbiological Quality Control in Pharmaceutical Environment
Microbiological products in pharmaceutical settings are influenced by the quality of materials and the environment. Good Manufacturing Practices (GMP) are essential to minimize contamination risks, with control points focused on the ecology of microorganisms. Sources of contamination include the atm
1 views • 128 slides
Understanding Weird Logs in Zeek for Network Security Analysis
Dive deep into the world of "Weird" logs in Zeek with Fatema Bannat Wala, a Security Engineer from the University of Delaware. Discover the motivation behind analyzing over 200 types of Weirds triggered in network traffic, explore common types of Weirds, and learn how these logs can reveal crucial i
1 views • 29 slides
Understanding Boyle's Law in Physics
Boyle's Law explains the relationship between the volume and pressure of a gas. When pressure increases on a fixed mass of gas at constant temperature, the volume decreases. This inverse proportion between pressure and volume can be explained by the Kinetic Theory, where the speed of gas particles a
0 views • 12 slides
Nitrogen Asphyxiation Hazards and Safety Tips
This safety moment highlights the dangers of nitrogen asphyxiation through a tragic incident and provides essential safety tips to prevent such accidents. It emphasizes the importance of proper ventilation in confined spaces, awareness of oxygen levels, and handling precautions for compressed gases.
0 views • 4 slides
Understanding Dimensionality Reduction and Principal Component Analysis
Dimensionality reduction techniques like Principal Component Analysis (PCA) help in transforming high-dimensional data into a lower-dimensional space, leading to efficient storage and better understanding of underlying patterns. By capturing maximum variance in the data, PCA learns projection direct
5 views • 16 slides
Managing Microbiological Quality in Pharmaceutical Environments
The quality of microbiological products is influenced by the pharmaceutical environment materials. Good Manufacturing Practices (GMP) play a crucial role in minimizing contamination risks. Various sources of contamination include the atmosphere, water, persons, raw materials, packaging, buildings, a
0 views • 128 slides
Visualization of Process Behavior Using Structured Petri Nets
Explore the concept of mining structured Petri nets for visualizing process behavior, distinguishing between overfitting and underfitting models, and proposing a method to extract structured slices from event logs. The approach involves constructing LTS from logs, synthesizing Petri nets, and presen
0 views • 26 slides
Understanding File Extraction Methods: Tech Skills 201 Overview
Learn to extract files from compressed or archive formats, navigate command line interfaces, and understand virtual machines in digital preservation workflows. Discover how to handle compressed files on Windows, Mac, and Linux, including popular formats like .zip, .tar, and .dmg. Detailed instructio
0 views • 27 slides
Graph Connectivity and Single Element Recovery via Linear and OR Queries
The content discusses the concepts of graph connectivity and single element recovery using linear and OR queries. It delves into the strategies, algorithms, and tradeoffs involved in determining unknown vectors, edges incident to vertices, and spanning forests in graphs. The talk contrasts determini
0 views • 28 slides
Enhancing Memory Cache Efficiency with DRAM Compression Techniques
Explore the challenges faced by Moore's Law in relation to bandwidth limitations and the innovative solutions such as 3D-DRAM caches and compressed memory systems. Discover how compressing DRAM caches can improve bandwidth and capacity, leading to enhanced performance in memory-intensive application
0 views • 48 slides
Challenges and Potential of Certified and Renewable Natural Gas
Limited potential for decarbonization through compressed natural gas due to challenges in measuring and verifying emissions reductions. Renewable natural gas also faces technical and economic limitations. Synthetic methane and thermal gasification technologies are not widely available or cost-compet
0 views • 8 slides
Understanding Kennings in Poetry: Examples and Significance
Kennings are compressed metaphors using two nouns to describe a subject, popular in Anglo-Saxon poetry like Beowulf. They add depth and imagery, with examples like "sky-climber" for a mountain. Explore how kennings enhance poetic expression and try creating modern kennings.
1 views • 5 slides
Sparse Millimeter-Wave Imaging Using Compressed Sensing and Point Spread Function Calibration
A novel indoor millimeter-wave imaging system based on sparsity estimated compressed sensing and calibrated point spread function is introduced. The system utilizes a unique calibration procedure to process the point spread function acquired from measuring a suspended point scatterer. By estimating
2 views • 26 slides
Understanding Speed Logs and Their Evolution in Maritime Navigation
Speed logs play a crucial role in measuring a vessel's speed and distance traveled through water. The evolution from primitive chip logs to modern RPM counters has significantly improved accuracy and efficiency in maritime navigation. Learn about the history, types, and working principles of speed l
0 views • 17 slides
Compressed Gas Safety Training Overview
This presentation covers various aspects of compressed gas safety including regulations, handling, storage, emergency response, and gas properties. It emphasizes the importance of proper use, storage, and handling of compressed gases to ensure safety in industrial, medical, and citizen applications.
0 views • 91 slides
Advances in Full-Text Indexing Using Suffix Arrays
Explore the evolution of full-text indexing techniques leveraging suffix arrays, from SA-hash to FBCSA, with insights on experimental results, suffix trees, and compressed indexes like CSA and FM-index. Discover efficient search strategies and data structures for pattern matching in text processing.
1 views • 28 slides
Understanding Re-Finding Behavior in Yahoo Search Logs
Explore a study on re-finding behavior in Yahoo search logs, focusing on quantifying user re-finding actions, known patterns, methodology, and challenges in inferring re-finding intent. The research sheds light on the commonality and stability of re-finding, emphasizing the significance of identifyi
0 views • 22 slides
The Top Advantages of Switching to Oil-Free Compressors for Your Business
It enhances the lifespan of your air system by removing humidity, ensuring your compressed air is clean and dry for all applications.\n
0 views • 6 slides
The Top Advantages of Switching to Oil-Free Compressors for Your Business
It enhances the lifespan of your air system by removing humidity, ensuring your compressed air is clean and dry for all applications.\n
0 views • 6 slides
Efficient Maintenance of Indexed String Sequences in Compressed Space
The Wavelet Trie, Prefix Operations, and Dynamic Sequences are explored in maintaining an indexed sequence of strings efficiently. Various operations like access, rank, select, and dynamic updates are discussed with the aim of storing strings in minimal space while supporting polylog operations effe
0 views • 20 slides
Dictionary Compression and Deep Packet Inspection (DPI) Overview
This content discusses Decompression-Free Inspection (DPI) for shared dictionary compression over HTTP, the challenges and solutions in deep packet inspection (DPI), compressed HTTP methods, examples of intra-response and inter-response compression, and current operations of Network Intrusion Detect
0 views • 33 slides
SPC Algorithm: Shift-based Pattern Matching for Compressed Web Traffic
Victor Zigdon presents the SPC Algorithm, a simpler and more efficient approach to pattern matching in compressed web traffic. By applying an accelerating idea on pattern matching algorithms, the SPC Algorithm skips bytes and achieves throughput improvements. The background includes information on G
0 views • 21 slides
Overview of Large Scale Log Studies in HCI
This presentation from the CHI 2011 course delves into the design and analysis of large-scale log studies, highlighting the benefits and drawbacks of utilizing logs to understand user behaviors. It explores the insights logs provide, the challenges faced, and strategies to generate relevant logs for
0 views • 146 slides
Analysis of Unique URLs Retrieval Patterns in Web Logs
This analysis delves into the retrieval patterns of unique URLs from web logs, revealing that a significant percentage of URLs are re-presented from different client IP addresses. The study identifies top repeaters and examines instances of potential proxy device usage based on AS locations.
0 views • 15 slides
Exploring a Compressed Academic Calendar: A Detailed Examination by the Alternative Academic Calendar Committee
The Alternative Academic Calendar Committee at Chabot College and Las Positas College District Office is diligently studying the potential adoption of a compressed academic calendar. With careful consideration of stakeholder input and thorough analysis of the benefits and challenges involved, the co
0 views • 10 slides
Key Choices in Compressed Academic Calendar Design
Review the fundamental requirements for designing a compressed academic calendar, including minimum days and weeks of instruction, mandated holidays, and the integrity of credit hours. Explore key decisions needed for a successful alternative academic calendar project by John Mullen, Consultant.
0 views • 13 slides
Improving Performance of Compressed Earth Blocks Through Pozzolanic Reaction
Enhancing the strength and durability of compressed earth blocks for modern construction using chemical stabilization methods involving materials like calcium carbide residue and rice husk ash. Experimental approaches and raw material processing are detailed in the study, focusing on binder addition
0 views • 18 slides
Unsupervised Relation Detection Using Knowledge Graphs and Query Click Logs
This study presents an approach for unsupervised relation detection by aligning query patterns extracted from knowledge graphs and query click logs. The process involves automatic alignment of query patterns to determine relations in a knowledge graph, aiding in tasks like spoken language understand
0 views • 29 slides
Analyzing EZproxy Logs with ezPAARSE
This presentation delves into the analysis of EZproxy logs using ezPAARSE, a free and open-source software with a GPL-compatible license. It covers log formats, examples, benefits, and drawbacks of locally-created logs, offering insights and value for usage statistics. Explore other options like AWs
0 views • 10 slides
Big Data-Based Security Analytics for Protecting Virtualized Infrastructures in Cloud
This paper proposes a novel big data-based security analytics approach to detect advanced attacks in virtualized infrastructures in cloud computing. By utilizing network logs and user application logs collected from virtual machines, attack features are extracted through graph-based event correlatio
0 views • 54 slides
Application Log Processing Methodologies in Service-Oriented Architecture
Understanding the methodologies for processing application logs in a service-oriented architecture, including data collection, purpose, programming language toolkits, centralized log collection, non-discardable logs collection, event/enterprise bus integration, cloud platform data collection, and Ku
0 views • 13 slides