Understanding Non-Weighted Codes and Excess-3 Code in Binary Systems
Explore non-weighted binary codes like Excess-3 code, learn how to convert decimal numbers to XS-3 code, advantages and disadvantages of BCD codes, and steps to convert Excess-3 code to binary. Discover the intricacies of binary coding systems with practical examples.
5 views • 55 slides
How to Fix QuickBooks Error Code 12031?
How to Fix QuickBooks Error Code 12031?\nQuickBooks Error Code 12031 disrupts operations due to internet connection issues or firewall settings. Troubleshoot by checking your internet connection, updating QuickBooks, configuring firewall settings, and adjusting Internet Explorer settings. Utilize Qu
0 views • 6 slides
The Impact of No Code-Low Code on Startup Innovation
In the vibrant world of startups, innovation is the cornerstone of success. As these businesses aim to carve out their niches, they often face a common hurdle: the extensive resources required for traditional software development. However, the emergence of low code no code (LCNC) platforms is revolu
2 views • 12 slides
Improving Code Analysis Workflow with Jenkins, Sonar, and Gerrit
Enhance code analysis processes by analyzing source code before merging, enabling analysis in branches, and triggering Jenkins jobs. Sonar.cloud provides options to analyze branches using Maven build, while the proposal suggests using Jenkins plugin for code review. Addressing challenges with Gerrit
1 views • 12 slides
Getting Started with Visual Studio Code for Web Development
Visual Studio Code (VS Code) is a versatile text editor built with Electron.js that is ideal for developing static web pages and working on Asp.Net Core projects. Learn how to set up and use VS Code for building static web pages by following simple steps like downloading the latest version, organizi
4 views • 10 slides
Understanding Strata Corporations and the Human Rights Code
The Human Rights Code aims to prevent discrimination, promote equality, and provide redress for those discriminated against. It prevails over other legislation, including the Strata Property Act. Strata corporations are subject to various provisions of the Code, impacting areas such as publications,
0 views • 93 slides
Code of Professional Conduct and Ethics in Architectural Profession
The Code of Professional Conduct and Ethics in the architectural profession sets forth standards of honesty, integrity, and ethical behavior expected from registered architects. It outlines guidelines for professional conduct, practices, and ethics, emphasizing the need for transparency, disclosure
1 views • 29 slides
Understanding Distribution Design Issues in Databases
When designing a database, decisions regarding fragmentation, correctness rules, allocation alternatives, and information requirements play a critical role in optimizing performance. Factors such as the degree of fragmentation, correctness of fragmentation, and allocation choices impact query execut
2 views • 10 slides
Understanding Binary Coded Decimal (BCD) and Excess-3 Code
Binary Coded Decimal (BCD) is a binary code used to represent decimal numbers, with the popular 8421 BCD code and its conversion process explained. Additionally, Excess-3 Code, another BCD code, is detailed with an example of finding its code for a given decimal number. Different BCD codes like 4221
0 views • 11 slides
A New Complaint Handling Code for the Sector - Webinar Highlights
This webinar discusses the introduction of a new Complaint Handling Code for the sector, aiming to address issues in social housing complaint processes. It covers key points, the background leading to the code's development, the Ombudsman's experience, and the code's aims and framework towards high-
0 views • 14 slides
The Board of Taxation Voluntary Tax Transparency Code Overview
The Board of Taxation developed a voluntary Tax Transparency Code to address community concerns and promote greater tax transparency among large businesses. The Code outlines recommended disclosures for both large and medium businesses, encouraging adoption of higher disclosure standards. Internatio
0 views • 20 slides
Azalea Middle School Dress Code Guidelines
Azalea Middle School implements a strict dress code policy to maintain a positive educational environment. Students are required to adhere to the Pinellas County Code of Student Conduct, ensuring their clothing is neat, clean, and conducive to learning. The dress code specifies guidelines on pants,
0 views • 18 slides
Simplifying AI Development with Low-Code and No-Code Platforms
Explore the world of low-code and no-code AI development platforms, empowering experts to create applications with ease. Learn about the benefits, tools, and components of these innovative platforms, and discover popular AI tools for no-code development. Accelerate your digital transformation journe
0 views • 11 slides
Enhancing Blackboard Writing Skills for Effective Teaching
Blackboards play a crucial role in education by providing a visual aid that enhances the clarity and understanding of lessons. Maintaining neatness, correctness, and legibility in writing on the blackboard is essential. The size and alignment of letters, highlighting main points, and creating a brie
0 views • 13 slides
Understanding Pseudo Code and Flow Charts for Algorithm Analysis
Explore the concepts of pseudo code and flow charts for analyzing algorithms, problem-solving, and understanding space and time complexity. Learn about basic elements of pseudo code, assigning operations, and writing effective pseudo code statements in a clear and structured manner. Discover the imp
0 views • 26 slides
Enhancing Code Status Discussions in End-of-Life Care: A Quality Improvement Project
This project led by Dr. John Rutkowski aims to reduce inappropriate interventions for patients with DNR or Modified Code Status by implementing an improved code status documentation system. Data analysis reveals a need for better documentation practices, and survey responses highlight various challe
0 views • 18 slides
Code Assignment for Deduction of Radius Parameter (r0) in Odd-A and Odd-Odd Nuclei
This code assignment focuses on deducing the radius parameter (r0) for Odd-A and Odd-Odd nuclei by utilizing even-even radii data from 1998Ak04 input. Developed by Sukhjeet Singh and Balraj Singh, the code utilizes a specific deduction procedure to calculate radius parameters for nuclei falling with
1 views • 12 slides
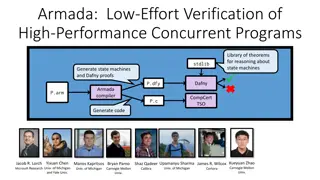
Armada: Low-Effort Verification of High-Performance Concurrent Programs
Armada is a library that enables developers to write high-performance concurrent code with flexibility. It supports automated proof generation for reasoning about state machines and synchronization mechanisms. The tool reduces the proof burden by using a weak-consistency memory model and provides gu
0 views • 17 slides
Software Bugs and Formal Verification in Critical Systems
Software bugs have caused catastrophic events like radiation overdoses and rocket explosions, emphasizing the importance of formal verification in ensuring software correctness. Formal verification uses mathematical models to prove software correctness, offering higher assurance, especially in safet
1 views • 26 slides
Automated and Modular Refinement Reasoning for Concurrent Programs
This research explores automated modular refinement reasoning for concurrent programs, focusing on safety and correctness in operating systems and applications. Projects like Verve and Ironclad aim to achieve end-to-end security through formal verification tools and small trusted computing bases. Th
1 views • 12 slides
Efficient Specification Mining for Trustworthy Software Development
Explore the approach of utilizing code trustworthiness measurements to mine specifications with minimal false positives. Understand the significance of specifications in software projects and how they contribute to debugging, testing, maintenance, refactoring, and documentation. The focus is on gene
0 views • 49 slides
Understanding the .NET Architecture Components
The .NET architecture comprises various key components such as the Common Language Specification, Code Manager, Managed Code, Unmanaged Code, and Native Code. These components play crucial roles in the development and execution of applications within the .NET framework. Managed code is executed by t
0 views • 21 slides
Introduction to Code Reasoning in CSE331 Lecture
In this lecture, we delve into the fundamentals of code reasoning, focusing on forward and backward reasoning techniques in straight-line and if-statement code. The session includes reviewing the practice of identifying the strongest assertions and understanding the dual purposes of proving code cor
0 views • 24 slides
Challenges in Code Search: Understanding, Matching, and Retrieval
Programming can be challenging due to the lack of experience and unfamiliar libraries. Code search engines struggle with representing complex tasks, while information retrieval techniques aim to bridge the gap between source code and natural language queries. The mismatch between high-level intent a
0 views • 21 slides
Software Quality and Source Code Management Best Practices
Effective source code management is crucial for software quality assurance. This involves locking down code, baselining milestones, managing code variants, and ensuring traceability. Software Configuration Management (SCM) is key, encompassing configuration items and core concepts like creating base
0 views • 34 slides
Differential Assertion Checking and Relative Correctness in Software Verification
Differential assertion checking compares two similar programs to identify errors, while relative correctness ensures all assertions pass, highlighting failed assertions. The content discusses the challenges and benefits of these techniques in software verification, with examples of correct and buggy
0 views • 17 slides
Verifying Functional Correctness in Conflict-Free Replicated Data Types
Explore the significance of verifying functional correctness in Conflict-Free Replicated Data Types (CRDTs), focusing on ensuring data consistency and program logic for clients. Learn about the importance of Strong Eventual Consistency (SEC) and the necessity of separate verification with atomic spe
0 views • 33 slides
Understanding Subtyping and Subclasses in Software Design
Subtyping in software design refers to the relationship between types where a subtype can be substituted for its supertype without affecting the correctness of the program. This concept ensures that objects of a subtype meet the specifications of its supertype. Subtypes should not surprise clients b
0 views • 32 slides
Multi-Label Code Smell Detection with Hybrid Model based on Deep Learning
Code smells indicate code quality problems and the need for refactoring. This paper introduces a hybrid model for multi-label code smell detection using deep learning, achieving better results on Java projects from Github. The model extracts multi-level code representation and applies deep learning
0 views • 10 slides
Actor-Based Services: Geo-Distribution Challenges and Solutions
Explore the complexities of geo-distributing actor-based services, handling multiple users, devices, data centers, and concurrent code execution. Delve into client app architecture, challenges of correctness under failures, and the quest for the right abstractions in composed services. Discover stra
0 views • 54 slides
Overview of CAIN Particle Tracking Code for High-Energy Colliders
CAIN is a particle tracking code used for high-energy collider simulations since 1984. Initially named ABEL, it evolved to include beam-laser interactions for gamma-gamma colliders. The code, written in FORTRAN 90, handles beam-beam and external fields, with a structure where all particles are store
0 views • 17 slides
Logical Reasoning in Software Design and Implementation
Logical reasoning in software development involves determining the truth of facts as a program runs under specific assumptions. This process complements testing by allowing programmers to reason about classes of inputs/states and verify program correctness. Hoare Logic is introduced as a method for
0 views • 35 slides
Lazy Code Motion and Partial Redundancy Elimination in Optimizing Compiler
Lazy code motion, partial redundancy elimination, common subexpression elimination, and loop invariant code motion are optimization techniques used in compilers to improve code efficiency by eliminating redundant computations and moving code blocks to optimize performance. These techniques aim to de
0 views • 35 slides
Interactive Theorem Provers: Ensuring Correctness in Programming
Explore the world of Interactive Theorem Provers, where you can write definitions, proofs, and automatically validate the correctness of your code. Learn about writing definitions in Coq, inductive definitions, and completing exercises to solidify your understanding.
0 views • 10 slides
Understanding Static Program Analysis
Static program analysis involves proving correctness, inferring invariants, and detecting errors in code before execution. Challenges include specifying program behavior, writing loop invariants, and using decision procedures for implications. This analysis can help ensure code reliability and ident
0 views • 73 slides
Superoptimization: Accelerating Code Performance through Conditional Correctness
Explore the concept of superoptimization, a technique to generate optimal code implementations for performance-critical systems. The process involves enumerating all possible programs, transforming them with loops, and proving equivalence with the original code. While optimizations are formally veri
0 views • 22 slides
Memory and Type Safety in System Design
Explore the concept of ensuring memory and type safety in system design, featuring safe systems, verified code, hardware specifications, and end-to-end safety measures. Learn about Verve, a type-safe OS, and the Verve Nucleus designed for partial correctness and safety verification at the hardware l
0 views • 19 slides
Unleash the Power of JavaScript Slot Machine Code for Your Online Casino (1)
Learn how to create captivating online slot machines with JavaScript Slot Machine Code, Casino game code, Casino game HTML code, HTML5 casino games source code, Slot machine JavaScript for your platform.\n\nKnow more>>\/\/ \/javascript-slot-machine-c
0 views • 4 slides
Plumbing Code Appeals and Interpretations Overview
This document provides information on the agenda, upcoming professional development events, Building Code Appeal Board, Appeal Board decisions, Code Interpretation Committee, code interpretations, and final thoughts related to plumbing code appeals and interpretations. It covers the appeal process,
0 views • 8 slides
Understanding Automatic Inference of Necessary Preconditions
This content delves into the concept of automatic inference of necessary preconditions in software development, emphasizing the importance of necessary preconditions over sufficient preconditions for ensuring program correctness. It discusses the distinction between necessary and sufficient precondi
0 views • 29 slides