Famous Sexologist in Patna and Lakhisarai over phone | Dr. Sunil Dubey
Do you live in Lakhisarai city which is the administrative headquarters of Lakhisarai district in Bihar, India? Actually, this city is famous for its Ashok Dham temple in India. Right now you are sad because of your sexual problem. This sexual problem not only troubles you but is also spoiling your
17 views • 6 slides
Exploring Germanic Tribes and Languages in History
Delve into the ancient Germanic tribes and languages, their territories, movements during the Migration Period, surviving languages, writing systems, and encounters with prominent historical figures like Roman generals. Learn about the earliest mentions of Germans by Greek travelers and astronomers,
3 views • 35 slides
Overview of Distributed Systems: Characteristics, Classification, Computation, Communication, and Fault Models
Characterizing Distributed Systems: Multiple autonomous computers with CPUs, memory, storage, and I/O paths, interconnected geographically, shared state, global invariants. Classifying Distributed Systems: Based on synchrony, communication medium, fault models like crash and Byzantine failures. Comp
9 views • 126 slides
Solving the Missionaries and Cannibals River Crossing Problem
Consider the classic problem of three missionaries and three cannibals needing to cross a river using a canoe that can hold up to two people. The challenge is to transport everyone safely without leaving more cannibals than missionaries on either side of the river. Learn about search problem formula
0 views • 124 slides
Understanding Byzantine Fault Tolerance in Distributed Systems
Byzantine fault tolerance is crucial in ensuring the reliability of distributed systems, especially in the presence of malicious nodes. This concept deals with normal faults, crash faults, and the challenging Byzantine faults, where nodes can exhibit deceptive behaviors. The Byzantine Generals Probl
0 views • 29 slides
Understanding the LIBRE Model Stick Figure Tool for Scoring and Engagement Style Analysis
The LIBRE Model Stick Figure Tool is designed for problem-solving exchanges between a problem-solver and a facilitator. It involves five prompts - Listen, Identify, Brainstorm, Reality-test, and Encourage - aimed at self-reflection and behavior modification. The model emphasizes self-regulated atten
0 views • 34 slides
Comprehensive Overview of Problem-Oriented Medical System in Physiotherapy Assessment
In the realm of physiotherapy assessment, the Problem-Oriented Medical System (POMS) plays a vital role in accurately defining patient problems, creating treatment plans, and monitoring progress. This system, pioneered by Weed in 1968, consists of Problem-Oriented Medical Records (POMR), auditing, a
2 views • 34 slides
Engaging Paper-Based Problem Solving for Computational Thinking Skills
Implementing paper-based problem-solving activities using puzzles, riddles, and pattern recognition can effectively introduce computational thinking without the need for complex technology or terminology. Through real-life scenarios like transporting a fox, chicken, and corn across a river or encodi
0 views • 23 slides
Federal Audit Executive Council FY2021 Data Act Working Group Overview
The Federal Audit Executive Council's Data Act Working Group assists Inspector Generals in meeting oversight requirements. Established in 2015, it includes a Common Methodology Team and a Governance Team to ensure compliance. The teams work on soliciting feedback, developing audit guides, conducting
0 views • 22 slides
Understanding Implications of IG Empowerment Act and Paperwork Reduction Act
The IG Empowerment Act provides beneficial provisions for Inspector Generals (IGs) such as exemptions from certain acts, including the Computer Matching Act and Paperwork Reduction Act. The Paperwork Reduction Act requires federal agencies, including IGs, to obtain OMB clearance before conducting su
1 views • 25 slides
Understanding Complex Computing Problem (CCP) and Complex Computing Activity (CCA)
Dr. Saman Hina, along with Dr. Farrukh Arif and Dr. Maria Waqas, presents information on Complex Computing Problem (CCP) - a problem involving technical, computing, and other issues with no obvious solution, requiring deep knowledge and analytical thinking. CCP is evaluated through predefined rubric
4 views • 19 slides
Overview of Research Problem Identification and Formulation
Understanding the importance of defining a research problem, this content delves into the selection and formulation of research problems, the definition of a research problem, reasons for defining it, methods for identifying research problems, sources of research problems, and considerations in sele
1 views • 11 slides
Understanding Byzantine Fault Tolerance: A Comprehensive Overview
Byzantine Fault Tolerance (BFT) is a critical concept in computer science, addressing faults in distributed systems. This summary covers the types of faults (normal, crash, Byzantine), implications of Byzantine faults, Byzantine Generals Problem, impossibility results, and the complexity of solving
3 views • 29 slides
Understanding the MECE Framework for Efficient Problem-Solving
The MECE (Mutually Exclusive, Collectively Exhaustive) framework is a powerful tool used by business leaders and consultants like McKinsey to structure information, reduce complexity, and gather comprehensive data without overlaps. It involves creating issue trees that subdivide problem elements int
1 views • 4 slides
Exploring "Sailing to Byzantium" by W.B. Yeats: Symbolism and Themes
Delve into W.B. Yeats' iconic poem "Sailing to Byzantium" as it explores themes of art, transcendence, and the ideal state of mind beyond life. Discover the symbolism of Byzantium as an aesthetic haven where artists strive for perfection and transcendence. Unpack the impersonal nature of Byzantine a
0 views • 10 slides
Uninformed Search Chapter 3 - Goal-based Agents and Problem Solving
Discussing goal-based agents and problem solving in artificial intelligence, the chapter covers topics such as representing states and actions, various search algorithms like breadth-first and depth-first search, as well as the problem space principle developed by Allen Newell and Herb Simon. Exampl
2 views • 52 slides
Solving the Professors to Coffee Lounge Problem: A Graph Theory Approach
An intriguing mathematical problem is presented where new faculty members at TIMS must be assigned to coffee lounge alcoves in a way that ensures no two new members meet after the first day. By constructing a graph based on meet-up timings, analyzing clashes, and determining intervals, this scenario
1 views • 19 slides
Round-Efficient Byzantine Broadcast Under Strongly Adaptive and Majority Corruptions
This paper discusses a round-efficient Byzantine broadcast protocol that addresses strong adaptive adversaries and majority corruptions. The protocol involves unique and unbreakable peer signatures, committees for message verification, and time-locking mechanisms to prevent message tampering. By uti
1 views • 5 slides
Economic Models of Consensus on Distributed Ledgers in Blockchain Technology
This study delves into Byzantine Fault Tolerance (BFT) protocols in the realm of distributed ledgers, exploring the complexities of achieving consensus in trusted adversarial environments. The research examines the classic problem in computer science where distributed nodes communicate to reach agre
0 views • 34 slides
Byzantine Failures and CAP Theorem Overview
Byzantine failures refer to arbitrary patterns of failures where nodes exhibit inconsistent behavior. This lecture discusses Byzantine agreement and the challenges in reaching consensus with faulty nodes. It explores the minimum number of processes needed for consensus and extends the concepts to ge
1 views • 32 slides
Distributed Consensus Models in Blockchain Networks
Economic and technical aspects of Byzantine Fault Tolerance (BFT) protocols for achieving consensus in distributed ledger systems are explored. The discussion delves into the challenges of maintaining trust in adversarial environments and the strategies employed by non-Byzantine nodes to mitigate un
0 views • 34 slides
Divide and Conquer: A Strategy for Problem Solving
Divide-and-conquer is a powerful problem-solving technique in Computer Science where a large problem is divided into smaller sub-problems, conquered individually, and then combined to solve the original problem. Through three steps - Divide, Conquer, and Combine - complex problems can be efficiently
3 views • 18 slides
Geometric Routing Concepts and Byzantine Fault Tolerance
Geometric Routing enables routing without overhead, where each node knows its global coordinates and forwards messages based on proximity to the destination. Byzantine Faults pose challenges with arbitrary node behavior, but a Byzantine-Robust Geometric Routing algorithm addresses this in a 3-connec
2 views • 33 slides
Comprehensive Guide to Problem Oriented Medical Record (POMR) and Master Problem Lists
Delve into the world of Problem Oriented Medical Records (POMR) and Master Problem Lists (MPL) through the insightful teachings of Dr. Lawrence Weed. Learn the systematic approach, SOAP writing, and the significance of maintaining a patient-focused perspective. Understand the challenges in diagnosis
0 views • 35 slides
Exact Byzantine Consensus on Undirected Graphs: Local Broadcast Model
This research focuses on achieving exact Byzantine consensus on undirected graphs under the local broadcast model, where communication is synchronous with known underlying graphs. The model reduces the power of Byzantine nodes and imposes connectivity requirements. The algorithm involves flooding va
0 views • 7 slides
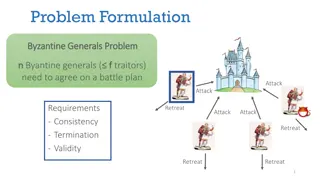
Byzantine Generals Problem in Distributed Systems
The Byzantine Generals Problem addresses how a group of generals, some of whom may be traitors, can reach a consensus on a battle plan while ensuring consistency, termination, and validity. Various protocols are explored to handle challenges such as faulty leaders, consistency violations, and cheati
0 views • 23 slides
The Impact of Music During the Civil War
Music played a significant role during the Civil War, with soldiers singing and carrying song books, creating a sense of camaraderie. Over 10,000 pieces of music were published by the end of the war, providing comfort and hope to those on the front lines and those at home waiting for their loved one
0 views • 12 slides
Understanding the Knapsack Problem in Dynamic Programming
Explore the concept of the Knapsack Problem in dynamic programming, focusing on the 0/1 Knapsack Problem and the greedy approach. Understand the optimal substructure and greedy-choice properties, and learn how to determine the best items to maximize profit within a given weight constraint. Compare t
0 views • 23 slides
Insights into Polynomials Vanishing on Cartesian Products and the 3POL Problem
This joint work explores polynomials vanishing on Cartesian products, focusing on the 3POL problem involving three sets of points and a 6-variate polynomial. It discusses the running time of solving the explicit 3POL problem and compares it to the well-studied 3SUM problem in theoretical computer sc
0 views • 29 slides
Influence of Mary in Byzantine and Western Art Through the Ages
The influence of Mary, the mother of Jesus, in Byzantine and Western art is explored through various historical events and artworks. From early visions of Mary to the declaration of Feast of Dormition, the devotion to Mary has shaped artistic representations and church dedications. Iconic cathedrals
0 views • 18 slides
Byzantine Faults and Consensus on Unknown Torus
The discussion revolves around achieving consensus in the presence of dense Byzantine faults on an unknown torus. Various challenges and impossibility theorems are explored, highlighting the complexities of reaching an agreement in such fault-prone environments. The content delves into the limitatio
0 views • 23 slides
Enhancing Problem-Solving Skills in Mathematics Workshops
In this workshop focused on problem-solving in mathematics, participants engage in various tasks and activities to develop a deep understanding of problem-solving strategies. The key messages emphasize the importance of integrating problem-solving into daily mathematics learning, utilizing multiple
0 views • 34 slides
Sync HotStuff: Practical Synchronous State Machine Replication
Sync HotStuff is a practical synchronous protocol that tolerates Byzantine replicas and handles weaker synchrony models. It overcomes issues of requiring a large number of rounds and lock-step execution. The protocol ensures safety by committing blocks and guarantees liveness by continuing to commit
0 views • 15 slides
The Stab in the Back Theory: Rise of the Nazis After WWI
The Stab in the Back Theory originated in Germany post-WWI, where people felt betrayed by politicians and generals for surrendering prematurely. Hitler used this theory to blame Socialists, Communists, and Jews, gaining followers by offering someone to blame for Germany's defeat.
0 views • 8 slides
Byzantine Fault Tolerance: Protocols, Forensics, and Research
Explore the realm of Byzantine fault tolerance through protocols like State Machine Replication and HotStuff, discussing safety, liveness, forensic support, and the impact of Byzantine faults. Dive into decades of research on achieving fault tolerance and examining forensic support in the face of By
0 views • 24 slides
The Contributions of the Byzantine Empire to Civilization
The Byzantine Empire made significant contributions to civilization through art, law, religion, and centralization of government. The empire's legacy includes the preservation of Roman laws, promotion of Christianity, accumulation of church wealth, and establishment of Constantinople as a key center
0 views • 22 slides
Three Stages of Christian Spiritual Growth: A Journey of Faith
Exploring the gradual progress of the Christian life through three stages - from the leap of faith to walking the spiritual path guided by method and tradition. This journey entails learning, understanding, and reaching enlightenment, drawing insights from Byzantine spiritual traditions and ancient
0 views • 12 slides
Perspectives on the Historiography of the Crusades
The historiography of the Crusades explores diverse viewpoints from western and eastern sources throughout different periods. Various leaders, including Byzantine emperors, Muslim sultans, and indigenous populations, had unique perspectives. The evolving attitudes towards the Crusades reflect changi
0 views • 25 slides
Optimally Resilient Asynchronous Multi-Valued Byzantine Agreement
Exploring the challenges and solutions in achieving optimally resilient asynchronous multi-valued Byzantine agreement protocols. This work presents a novel construction meeting key requirements and delves into round-preserving parallel composition of agreements, shedding light on probabilistic termi
0 views • 19 slides
Quantum Distributed Proofs for Replicated Data
This research explores Quantum Distributed Computing protocols for tasks like leader election, Byzantine agreement, and more. It introduces Quantum dMA protocols for verifying equality of replicated data on a network without shared randomness. The study discusses the need for efficient protocols wit
0 views • 28 slides