Comprehensive Bug Hunting Toolkit for Cybersecurity Enthusiasts
Explore a detailed guide on bug hunting tools, techniques, and resources by expert bug hunter Orwa Atyat from Jordan. Learn valuable tips on finding high/critical bugs, conducting basic recon, subdomain enumerations, collecting URLs/endpoints, and searching for backup files. Enhance your cybersecuri
2 views • 14 slides
Insect Identification for FFA Agronomy Skills Contest
Explore a variety of insects including the Alfalfa Weevil, Aphid, Army Worm, Assassin Bug, Bean Leaf Beetle, Black Cutworm, Chinch Bug, Colorado Potato Beetle, Common Stalk Borer, Corn Earworm, Corn Rootworm, Cricket, Cucumber Beetle, European Corn Borer, Flea Beetle, Grasshopper, Green Lacewing, Gr
1 views • 37 slides
Bug Out Bags https://www.survivalsuppliesaustralia.com.au/Categories/Emergency-S
Bug Out Bags for Emergency Evacuations\nEmergency can arise anytime anywhere, hence it becomes important to find the best bug out bag that helps you stay prepared without too much hassle. At Survival Supplies Australia, we understand emergencies can strike suddenly. That is why we offer bug out bags
1 views • 1 slides
The Best Bed Bug Removal & Control Service Provider in Sydney
Turn to us for professional Bed Bug Removal in Sydney and get rid of spooky bugs in one go. We resort to safe and eco-friendly methods to minimise the impact on your health and pets.
28 views • 6 slides
Fighting Bed Bugs NYC Bed Bug Treatments and Exterminators
Infestations of bed bugs in NYC must be dealt with quickly and effectively to stop them from growing and causing more discomfort. Both homeowners and businesses may reclaim their spaces from these stubborn pests by selecting the best bed bug exterminator, implementing tried-and-true treatment proced
2 views • 8 slides
Get the Best Pest Control Bed Bug in MacPherson
Get the Best Pest Control Bed Bug in MacPherson at Pestopia Pest Control, a locally established pest control company in MacPherson, Singapore, that provides pest control services to residential, commercial, and industrial sectors. With over 10 years of experience, they are committed to providing sa
0 views • 6 slides
Effective Workflow for Vulnerability Research in Production Environments
Professional vulnerability research involves finding bugs efficiently through fuzzing techniques. The main goal is to develop a comprehensive workflow and toolset for effective bug discovery and triaging. Ancillary goals focus on determining exploitability, optimizing human and CPU efficiency, and e
0 views • 69 slides
Bed Bug Bites Symptoms | healthcare360
This comprehensive guide will delve into bed bug bite symptoms, offering insights on identification, treatment, and prevention.
0 views • 6 slides
Machine Learning Techniques for Intrusion Detection Systems
An Intrusion Detection System (IDS) is crucial for defending computer systems against attacks, with machine learning playing a key role in anomaly and misuse detection approaches. The 1998/1999 DARPA Intrusion Set and Anomaly Detection Systems are explored, alongside popular machine learning classif
0 views • 36 slides
Automated Melanoma Detection Using Convolutional Neural Network
Melanoma, a type of skin cancer, can be life-threatening if not diagnosed early. This study presented at the IEEE EMBC conference focuses on using a convolutional neural network for automated detection of melanoma lesions in clinical images. The importance of early detection is highlighted, as exper
0 views • 34 slides
Colorimetric Detection of Hydrogen Peroxide Using Magnetic Rod-Based Metal-Organic Framework Composites
Nanomaterials, particularly magnetic rod-based metal-organic frameworks composites, are gaining attention for their exceptional properties and various applications in different fields. This study by Benjamin Edem Meteku focuses on using these composites for colorimetric detection of hydrogen peroxid
0 views • 16 slides
Real-World Concurrency Bugs and Detection Strategies
Explore the complexities of real-world concurrency bugs through a study of 105 bugs from major open-source programs. Learn about bug patterns, manifestation conditions, diagnosing strategies, and fixing methods to improve bug detection and avoidance. Gain insights from methodologies evaluating appli
0 views • 20 slides
Real-Time Cough and Sneeze Detection Project Overview
This project focuses on real-time cough and sneeze detection for assessing disease likelihood and individual well-being. Deep learning, particularly CNN and CRNN models, is utilized for efficient detection and classification. The team conducted a literature survey on keyword spotting techniques and
1 views • 15 slides
Real-Time Cough and Sneeze Detection Using Deep Learning Models
Detection of coughs and sneezes plays a crucial role in assessing an individual's health condition. This project by Group 71 focuses on real-time detection using deep learning techniques to analyze audio data from various datasets. The use of deep learning models like CNN and CRNN showcases improved
0 views • 15 slides
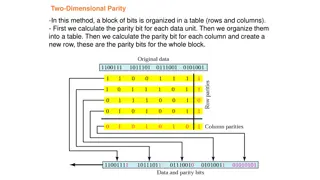
Data Error Detection Techniques Overview
Two-dimensional parity and Cyclic Redundancy Check (CRC) are data error detection methods used to ensure data integrity during transmission. Two-dimensional parity involves organizing bits in a table to calculate parity bits for data units and columns, while CRC appends a string of zeros to the data
0 views • 20 slides
Last Mile Project Evaluation and Aftermath Guidelines
The Last Mile Project V1.5 and Week 13 Evaluation involve submission deadlines, tutorial and lecture timeslots, user acceptance testing, peer evaluations, and bug resolution processes. Peer evaluations are essential for testing multiple products with varied features, providing insights and improving
0 views • 6 slides
Overview of GRANDproto Project Workshop on Autonomous Radio Detection
GRANDproto project workshop held in May 2017 focused on improving autonomous radio detection efficiency for the detection of extensive air showers (EAS). Issues such as detector stability and background rates were discussed, with the goal of establishing radio detection as a reliable method for EAS
1 views • 14 slides
Timely Leak Detection San Diego | Professional Leak Detection Services
Protect your home with expert leak detection services in San Diego. Avoid costly water damage and health risks with timely detection of hidden leaks. Schedule today!\n\nKnow more: \/\/ \/san-diego-slab-leak-detection\/
0 views • 7 slides
How Professional Leak Detection Can Save Your San Diego Home | Leak Detection Sa
Protect your home from costly damage with professional leak detection in San Diego. Learn about expert services like slab leak detection, non-invasive testing, and more. Save money and prevent water damage with top San Diego leak detection services.\
0 views • 8 slides
Discovering Techniques for Detecting Deadlock Bugs in Concurrent Programs
This analysis delves into various bug detection techniques for concurrent programs, focusing on deadlock bugs. It explores model checking and testing techniques, discussing their precision, error detection capabilities, and scalability challenges. The prevalence of deadlock bugs in real-world applic
0 views • 35 slides
System-Specific Static Analysis for Bug Finding in Real Code
Explore the methodology of system-specific static analysis as a powerful tool for detecting bugs in real code. This approach involves implementing extensions dynamically linked into the compiler, enabling the identification of errors across intricate program structures without the need for actual ex
0 views • 35 slides
Understanding Intrusion Detection Systems (IDS) and Snort in Network Security
Intrusion Detection Systems (IDS) play a crucial role in network security by analyzing traffic patterns and detecting anomalous behavior to send alerts. This summary covers the basics of IDS, differences between IDS and IPS, types of IDS (host-based and network-based), and the capabilities of Snort,
0 views • 34 slides
Understanding the Dynamics of Collision: Bug vs. Windshield
Explore the intriguing physics behind a bug hitting a windshield, delving into concepts like Newton's third law, momentum conservation, and the differences in force, time of impact, and change in velocity. Discover why a bug goes splat while a windshield remains intact in a collision scenario, with
0 views • 19 slides
Investigating Biases in Bug Localization Studies: A Critical Analysis
This research delves into potential biases affecting bug localization studies in software development. It explores misclassification of bug reports, pre-localized reports, and issues with ground truth files, shedding light on the challenges in accurately predicting and localizing software bugs.
0 views • 47 slides
Understanding Probabilistic Concurrency Testing for Bug Detection
Explore the concept of probabilistic concurrency testing and how randomized scheduling algorithms can help detect bugs efficiently. Learn about bug depth, randomized algorithms, and the development of PCT to improve the effectiveness of stress testing tools like Cuzz.
0 views • 23 slides
Investigating Biodiversity in the Schoolyard Garden
The Bug Blitz project aims to investigate the biodiversity of the schoolyard garden by capturing and documenting different bug species. The project involves identifying bugs, taking detailed photographs, and ensuring data accuracy. Specific procedures and methods are outlined for data collection wit
0 views • 15 slides
Formal Guarantees for Localized Bug Fixes: A Methodological Review
This review delves into a formal method for verifying bug fixes, specifically focusing on ensuring robustness and scalability in bug identification and classification. The OpenSPARC Story unfolds a methodology for bug fix verification, emphasizing bug resurfacing prevention and fix classification ba
0 views • 16 slides
Techniques for Detecting and Analyzing Deadlock Bugs in Concurrent Programs
Analysis of deadlock bug detection techniques in concurrent programs, highlighting the prevalence of deadlock bugs in real-world applications. The content discusses various bug detection approaches, including model checking and testing techniques, along with the challenges and solutions related to s
0 views • 32 slides
Challenges and Solutions in Concurrency Testing with Randomized Algorithms
Concurrency testing in complex cloud services presents challenges such as bugs, performance problems, and data loss. Randomized algorithms, like Probabilistic Concurrency Testing (PCT), offer effective bug-finding solutions. PCT provides probabilistic guarantees and scalable bug detection for distri
0 views • 37 slides
Kiwanis BUG Program - Empowering Students for Academic Success
The Kiwanis BUG Program aims to empower students to excel academically by recognizing their efforts in improving or maintaining good grades. Through a structured program, students are motivated to set goals, show perseverance, engage in peer mentoring, and receive support from teachers. Governor Mar
0 views • 45 slides
Understanding Anomaly Detection in Data Mining
Anomaly detection is a crucial aspect of data mining, involving the identification of data points significantly different from the rest. This process is essential in various fields, as anomalies can indicate important insights or errors in the data. The content covers the characteristics of anomaly
0 views • 50 slides
Lessons Learned from Commercializing a Bug Finding Tool
Coverity, a brand of software tools, transitioned static code analysis to the real world through customer interactions, bug finding laws, and bug handling strategies. Lessons include the impact of lab vs industry settings, customer trials, and understanding bugs in a code base. The importance of acc
2 views • 8 slides
Detection Methods for GMOs and LMOs in Molecular Biology
Techniques in Molecular Biology lecture discusses GMOs and LMOs, transgenic plants, examples like Bt cotton and Golden rice, detection methods, purpose of detection, and how transgenic plants are created. The content emphasizes the need to differentiate GM crops from non-GM crops and the importance
2 views • 40 slides
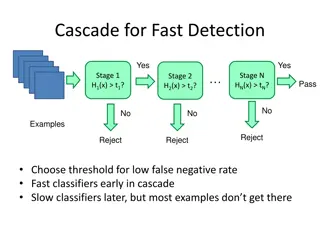
Object Detection Techniques Overview
Object detection techniques employ cascades, Haar-like features, integral images, feature selection with Adaboost, and statistical modeling for efficient and accurate detection. The Viola-Jones algorithm, Dalal-Triggs method, deformable models, and deep learning approaches are prominent in this fiel
0 views • 21 slides
Understanding Face Detection via AdaBoost - CSE 455.1
Face detection using AdaBoost algorithm involves training a sequence of weak classifiers to form a strong final classifier. The process includes weighted data sampling, modifying AdaBoost for Viola-Jones face detector features, and more. Face detection and recognition technology is advancing rapidly
0 views • 49 slides
Understanding Idempotence Bugs in Intermittent Systems
Energy-harvesting devices enable computing in inaccessible environments, but intermittent execution can lead to bugs and inconsistent updates. The impact of I/O-dependent idempotence bugs in intermittent systems is explored, highlighting the challenges and the need for tools like IBIS for bug detect
0 views • 28 slides
Software Bug Localization with Markov Logic
Software bug localization techniques like Tarantula focus on finding likely buggy code fragments in a software system by analyzing test results, code coverage, bug history, and code dependencies. The lack of an interface layer in existing techniques leads to handcrafted heuristics, posing a persiste
0 views • 17 slides
Exploration of Patch Generation Search Spaces using Software Metrics
This research focuses on improving the exploration of patch generation search spaces by utilizing software metrics in the context of bug generation. The study investigates the threat of malicious code insertion in third-party code construction for military projects and explores the concept of Patch
0 views • 8 slides
Overview of Static Bug Detection in Software Quality Assurance
Static bug detection is a less popular but effective approach for software quality assurance compared to traditional testing methods. It involves tools like Findbugs that help identify potential issues in code before deployment, such as bad coding styles, null pointer dereferences, and malicious cod
0 views • 36 slides
Practical Lock/Unlock Pairing for Concurrent Programs
The research discusses the challenges of concurrency in parallel programming and the importance of proper lock/unlock pairing to avoid bugs and non-determinism. Tools for bug detection and automated bug fixing are explored, along with examples illustrating the process. The issue of unpaired locks an
0 views • 20 slides