Infinite Impulse Response Filters
This lecture discusses the design and implementation of Infinite Impulse Response (IIR) filters using biquad structures. It covers topics such as stability, bounded-input bounded-output equalization, filter design, and filter implementation. The lecture also includes demos on filter design and concl
14 views • 29 slides
Sequential Logic Circuits in Digital Systems
Logic circuits in digital systems can be either combinational or sequential. Sequential circuits utilize storage elements along with logic gates, where outputs depend not only on present inputs but also on past inputs and internal states. They are essential building blocks, with storage registers pl
5 views • 20 slides
Overview of EV Infrastructure Load Model (EVIL) by Alexander Lonsdale
The EVIL model, developed by ADM, provides hourly electricity load shapes for transportation in commercial and residential sectors. It uses R executable scripts and static outputs to drive model output, facilitating scenario building for utility rate structures and energy forecasts. The model functi
3 views • 23 slides
Determinants of Total Production in Macroeconomics
An economy's total production of goods and services (GDP) is influenced by the quantity of inputs, known as the Factors of Production, and the ability to transform inputs into output through the production function. The key factors of production are capital and labor, and the production function det
1 views • 37 slides
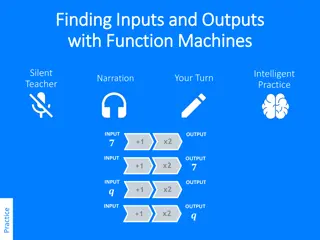
Function Machines: Finding Inputs and Outputs
Explore the concept of function machines, where inputs are transformed into corresponding outputs using a specific rule (in this case, x2 + 1). Engage in interactive exercises to practice finding missing inputs or outputs and solving for unknown values within the function machines.
4 views • 7 slides
E2E Test Framework 2.0 Gathering on OSC-RSAC Inputs and MVP Blueprints
This document discusses the gathering of OSC-RSAC inputs on MVP deployment blueprints and requirements for O-RAN Alliance, focusing on enabling deployments and developing critical functions for market needs. It outlines proposed agendas, candidate work items, and fits together various elements of th
2 views • 12 slides
Impact of Land-Use Consolidation Program on Farm Inputs in Rwanda
The study evaluates the effects of Rwanda's land-use consolidation program on farm input uptakes, specifically focusing on hybrid seeds, inorganic fertilizers, and pesticides. Results show significant increases in the adoption of hybrid seeds and inorganic fertilizers among participating households
0 views • 10 slides
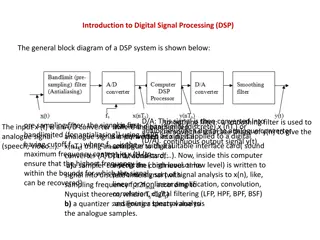
Digital Signal Processing (DSP) Systems: Linearity, Causality, and Stability
Digital Signal Processing (DSP) involves converting signals between digital and analog forms for processing. The general block diagram of a DSP system includes components like D/A converters, smoothing filters, analog-to-digital converters, and quantizers. DSP systems can be classified based on line
1 views • 12 slides
Wildfire R&D Related Opportunities and Statistics Overview
Comprehensive overview of wildfire-related research and development opportunities, outlining statistics on wildfire suppression costs, fire incidents, and acres affected. The content includes workshop goals, stakeholder needs assessment, and key challenges in the field. Insights from SME inputs, lit
0 views • 18 slides
Insights into Mars Sample Return Science Inputs for Landing Site Selection
The Mars Program Office at Jet Propulsion Laboratory has conducted a systematic survey to determine landing site priorities for sample return missions. Insights from the astrobiology and cosmochemistry/petrology communities reveal key interests such as geologic age, rock-water interactions, and dive
0 views • 16 slides
Costing Worksheet for Agriculture Inputs
Explore the costs associated with various agricultural inputs such as seed, nitrogen, and dry fertilizers per acre. The worksheet provides details on pricing, application rates, and calculations to determine the cost of inputs for efficient farming practices.
0 views • 12 slides
Cryptography in the Bounded Storage Model: Revisited - Eurocrypt 2023
Cryptography researchers revisit the Bounded Storage Model (BSM) to enhance security in transmitting messages while considering limited storage capacities. The BSM restricts adversaries to limited storage, enabling unconditional security. The model aims to address challenges in message transmission
0 views • 16 slides
Bounded Satisfiability Checking for Early Legal Compliance Verification
Early verification of legal compliance is crucial to avoid consequences such as violating regulations like GDPR. Through bounded satisfiability checking using Metric First-order Temporal Logic (MFOTL), this research focuses on system design verification for regulatory compliance. The study addresses
0 views • 29 slides
Achieving Bounded Latency in Data Centers: A Comprehensive Study
Data centers face challenges in providing consistent low latencies due to in-network interference and varying workloads. This study explores solutions to guarantee strong latency performance, mitigate latency variance, and minimize performance degradation for latency-sensitive applications. By analy
1 views • 18 slides
Lower Bounds on Sampling Good Codes in Bounded-Depth Circuits
Bounded-depth circuits are proven unable to sample or approximate good codes effectively. This work delves into lower bounds, showcasing that bounded families of circuits face limitations in computing specific functions or sampling distributions. The example of Parity in AC0 circuits illustrates the
1 views • 21 slides
Regret-Bounded Vehicle Routing Approximation Algorithms
Regret-bounded vehicle routing problems aim to minimize client delays by considering client-centric views and bounded client regret measures. This involves measuring waiting times relative to shortest-path distances from the starting depot. Additive and multiplicative regret measures are used to add
0 views • 28 slides
Definite Integrals in Mathematics
Explore the concept of definite integrals in mathematics, covering properties, solving methods, and applications in finding areas bounded by curves. Prior knowledge of functions, limits, derivatives, and indefinite integrals is essential to grasp this topic effectively. Dive into the unique value of
1 views • 32 slides
Cryptography in Bounded Storage Model: Ensuring Secure Communication
Cryptography in the Bounded Storage Model provides insights into securing communication with secrecy and authenticity. The model limits adversaries' memory without runtime restrictions, ensuring unconditional security for various primitives. Explore how this model safeguards messages from eavesdropp
1 views • 42 slides
Approximation Algorithms for Regret-Bounded Vehicle Routing
This research explores regret-bounded vehicle routing problems (VRPs) where the focus is on minimizing client delays based on their distances from the starting depot. The study introduces a client-centric view to measure regret and devises algorithms for both additive and multiplicative regret-based
1 views • 23 slides
Active Learning for Database Application Model Synthesis
Synthesizing models of applications that access databases involves leveraging active learning to select inputs, observing outputs, and regenerating programs. This approach helps in overcoming underspecification of program behavior and facilitates the migration of implemented functionality between pl
1 views • 59 slides
Graph Property Testing and Algorithms Overview
Explore testable bounded degree graph properties, sparse graphs, d-bounded degree graphs, hyperfinite graphs, arboricity, maximum matching algorithms, and sublinear time approximation algorithms in graph data streams. Learn about various graph models and properties with examples, showcasing the impo
3 views • 53 slides
Overview of E-Podium Specifications and Components
The E-Podium is equipped with a steel body, touch monitors, a PC with Intel i3 processor, controller, and various electronic components. The display includes a 19" touch monitor and a 10.4" sub-monitor. The PC features a motherboard with Intel H61 chipset, Intel HD2000 graphics, and dual-channel DDR
0 views • 8 slides
Profit Maximization Analysis with Milk Price Variation
Using a milk price of $10/cwt, grain price of $3/cwt, and hay price of $1.50/cwt, the profit-maximizing inputs for milk production are determined through mathematical calculations. The optimal weekly inputs are found to be 182.5 lbs of grain and 118.2 lbs of hay, resulting in a weekly profit of $23.
0 views • 4 slides
Bounded Arithmetic and Definable Functions in Complexity Theory
Bounded arithmetic, as explored in complexity theory, focuses on theories like PA but with restrictions on formulas. The comprehension axiom determines sets that can exist, and TC is a first-order arithmetic theory defining functions within a specific complexity class. The witnessing theorem in TC e
1 views • 16 slides
Robustness of Linear Sketches to Adaptive Inputs in Big Data Processing
Exploring the robustness of linear sketches in handling adaptive inputs in big data scenarios. The study covers applications like compressed sensing, data streams, and distributed computation. It delves into the challenges posed by adaptive inputs and the implications for correctness and efficiency
0 views • 27 slides
UCD90xxx Sequencer Portfolio Overview
UCD90xxx offers digital sequencers and analog sequencers with various advantages, including flexibility, reliability, and ease of use. The UCD90xxx selection guide provides detailed specifications for different models, highlighting features such as rails sequenced, monitor inputs, fan control, fault
0 views • 39 slides
Advanced Configurable Analog I/O Modules for Automation Systems
Explore a range of onboard analog I/O modules including BX10, BX18, and BX36 series, each offering high-speed discrete inputs and outputs along with analog input and output options. These modules are fully configurable with flexible voltage and current ranges. Additionally, learn about the new memor
0 views • 7 slides
Object-Oriented Design by Contract with Declarative Bounded Testing
Comprehensive overview of Object-Oriented Design by Contract (DbC) with Declarative Bounded Testing, exploring its background, principles, implementation in programming languages, and application through bounded exhaustive testing. Learn how DbC enhances software reliability and development practice
0 views • 31 slides
Stability Analysis in Control Systems
Stability analysis in control systems is crucial for ensuring the predictability and reliability of system responses. It involves assessing various stability criteria such as Routh Stability Criterion and investigating the behavior of systems under different conditions like bounded inputs. Understan
3 views • 29 slides
Theorems on Convergent Sequences with Proofs and Examples
The lecture covers theorems on convergent sequences, including the convergence of monotonic increasing and decreasing sequences when bounded. Detailed proofs for these theorems are provided, along with examples to determine if a sequence is bounded. The presentation includes step-by-step explanation
0 views • 6 slides
Quantum Space-Bounded Complexity in Logarithmic Space: A Comprehensive Overview
Quantum space-bounded complexity explores the memory requirements for solving problems in log space. Examples include matrix multiplication, undirected graph connectivity, and problems like inverting matrices and determining connectivity. The significance of deterministic log space (NL) and nondeter
0 views • 49 slides
Facade: A Compiler and Runtime for Object-Bounded Big Data Applications
Facade is a compiler and runtime designed to address challenges related to big data applications, focusing on reducing GC time, memory consumption, and access costs while improving scalability. The system utilizes off-heap native memory and bounded object pooling techniques to enhance performance an
1 views • 23 slides
Discussion on bounded delay in Industrial Scenarios
IEEE 802.11-24/0443r0 explores solutions to address bounded delay challenges in industrial scenarios, focusing on deterministic latency and high reliability requirements. The proposed options aim to improve performance for low-latency services.
0 views • 8 slides
Bounded Synthesis for Streett, Rabin, and CTL* Overview
Delve into the world of bounded synthesis for Streett, Rabin, and CTL*, exploring LTL synthesis problems, a bounded approach, SMT-based synthesizers, encodings, and the significance of Streett/Rabin and CTL*. Understand CoBuchi and Streett automata, model checking synthesis, and more. Discover the e
0 views • 14 slides
Optimal Input Use in Farm Management: Economics of Multiple Input Production
Explore the principles of using multiple inputs in agricultural production processes. Learn how to identify the optimal combination of inputs through the Equal Margin Principle and partial derivatives. Discover the tradeoffs and substitutions between inputs in farm management to maximize efficiency
0 views • 55 slides
Compact LPs for Orienteering and Regret-Bounded Vehicle Routing
Explore the concept of compact, provably good LPs for orienteering and regret-bounded vehicle routing in computational methods for solving vehicle-routing problems. Understand how regret-bounded VRPs adopt a client-centric view to minimize delays and enhance client satisfaction.
0 views • 26 slides
Process Control Stability: Concepts, Cases, and Definitions
Explore the concept of stability in process control systems, including different stability cases such as stable, critically stable, and unstable. Understand the definition of stability as the ability of a system to provide bounded output for bounded input, known as the BIBO definition.
0 views • 31 slides
Time-Bounded Kolmogorov Complexity and One-Way Functions
Explore the concept of time-bounded Kolmogorov complexity, one-way functions, and their relevance in complexity theory and cryptography. Understand the definitions, properties, and significance of one-way functions in various cryptographic applications like private-key encryption and digital signatu
0 views • 32 slides
Dynamic Collusion Bounded Functional Encryption Insights
Explore the realm of dynamic collusion bounded functional encryption, discussing its setup, security, limitations, and theoretical perspectives. Learn about key generation, encryption, decryption, and more in this innovative cryptographic domain.
0 views • 24 slides
Exploring C Bounded Model Checker: Verifying ANSI-C Programs
Dive into the capabilities of the C Bounded Model Checker (CBMC) designed for verifying arbitrary ANSI-C programs, including handling bit vector operators, dynamic memory allocation, and loop unwinding. Discover how CBMC assists in identifying bugs and ensuring code correctness.
0 views • 14 slides