Identity Theft Prevention Program
Ensure staff understand their responsibility to protect sensitive information and know the steps to prevent, detect, and respond to identity theft. This training is required as part of the Montana Tech Identity Theft Prevention Program.
1 views • 31 slides
Buy Clone Cards Online - Telegram -@Eurneosbillsnotes
Order Clone ATM Cards dump with the Pin Sell CVV, CC full. All cards are verified and cash out is sure and secured with a secure and safe method Dumps Track 1 2 with pin 101, 201 worldwide dumps With Pin CVV Dumps Shop. Dumps Pin\u2013CCV Shop PRICE: SKIMMER PIN PAD (OR CAMERA PANEL) ATM SKIMMERS
3 views • 2 slides
BUY MASTERCARDS CLONE ATM CARDS ONLINE - @EUROSBILLSNOTES
Buy Mastercards Clone ATM Cards dump with the Pin Sell CVV, CC full. All cards are verified and cash out is sure and secured with a secure and safe method Dumps Track 1 2 with pin 101, 201 worldwide dumps With Pin CVV Dumps Shop. Dumps Pin\u2013CCV Shop PRICE: SKIMMER PIN PAD (OR CAMERA PANEL) ATM
4 views • 2 slides
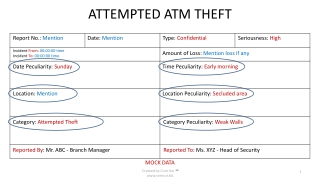
Attempted ATM Theft Incident Report
An attempted theft at an ATM located in a bank branch was unsuccessful but resulted in significant damage. Quick action by bank staff, including retrieving screenshots from backup, aided in the apprehension of the perpetrators. Recommendations were made to enhance security measures at ATM locations.
0 views • 4 slides
Protecting Against Financial Scams: Insights & Prevention
Learn how to safeguard your finances from scams and identity theft. Discover the impact of scams on US citizens in 2019, the age group most affected by identity theft, the state with the highest identity theft reports, and the common delivery methods of scams. Gain valuable insights to protect yours
0 views • 27 slides
ATM and SAR Inspector Qualifications and Responsibilities
An ATM/SAR inspector plays a crucial role in ensuring aviation safety by overseeing providers' compliance with national laws and regulations. States delegate authority to inspectors, who must meet specific criteria for knowledge, training, and competency. The effectiveness of safety oversight depend
3 views • 41 slides
Understanding the Red Flags Rule for Identity Theft Prevention
Learn how the Red Flags Rule aims to detect, prevent, and mitigate identity theft. Explore the goals of this training, identify red flags of potential fraud, and understand the application of the rule to financial institutions and creditors. Discover what covered accounts are and how to create unit-
2 views • 15 slides
Overview of ATM Committee at BUSM
Boston University School of Medicine (BUSM) is committed to providing a supportive learning environment free from mistreatment. The ATM Committee at BUSM focuses on investigating reports of student mistreatment and ensuring prompt, respectful responses. The committee's charge includes identifying an
0 views • 12 slides
If truly stolen crypto can be recovered in some way, can someone share the steps
1. Identify the Theft\n\nThe first step in recovering stolen cryptocurrency is to accurately identify and document the theft. This involves:\n\nNoticing unauthorized transactions in your wallet or exchange account.\nRecording all relevant transaction IDs, wallet addresses, and timestamps.\nCollectin
0 views • 15 slides
Protect Yourself from Identity Theft: Tips and Information
Learn about identity theft, how to spot it, major credit bureaus, keeping personal information secure, identity monitoring services, and ways to protect yourself from becoming a victim of identity theft.
0 views • 8 slides
Police Report: Theft of Amazing Robot
Mr. Silvester reported the theft of his 12-speed metallic blue Trek mountain bike, detailing the circumstances and security measures taken prior to the incident. The locked garage was found forced open with the missing bike bearing a security tag. The police investigation uncovered evidence suggesti
0 views • 10 slides
Global Air Navigation Plan Framework Overview
The International Civil Aviation Organization (ICAO) is developing a revised Global Air Navigation Plan (GANP) to enhance global planning mechanisms. The plan includes strategic documents for regional and national air navigation infrastructure planning, with a focus on CNS/ATM systems and discipline
1 views • 19 slides
Challenges and Impact of Stock Theft in Kenya: Lessons and Future Directions
Agricultural crime, particularly stock theft in Kenya, poses significant challenges affecting rural communities and the national economy. Livestock theft, a prevalent form of agricultural crime, not only results in financial losses but also undermines rural livelihoods and community cohesion. Despit
2 views • 15 slides
Safeguarding Against Identity Theft: Prevention and Remediation
Identity theft is a serious threat where personal information is stolen for malicious purposes like setting up accounts or accessing funds in your name. This guide explains what identity theft is, why you should be concerned, how thieves obtain information, signs of being a victim, and preventive me
0 views • 22 slides
Protect Yourself: Identity Theft and Consumer Protection Insights
Explore the realms of identity theft, consumer protection laws, and fraud prevention strategies. Learn about consumer rights and responsibilities, ways to avoid financial scams, and agencies providing assistance. Discover the importance of safeguarding personal information to prevent fraud and ident
0 views • 21 slides
State Level Bankers Committee Meeting for the Quarter Ended March 2022
The State Level Bankers Committee (SLBC) meeting for the quarter ended March 2022 was held at the State Bank of India Administrative Office in Shillong. The agenda included discussions on various actions taken reports, deployment of banking services in rural areas, ensuring financial inclusion and c
0 views • 30 slides
iQ-Banks Security and Operations Solutions Overview
iQ-Banks offers a range of advanced solutions for ATM security, branch operations, face recognition, and mobile agent communication. These solutions include features such as detecting theft, vandalism, skimming devices, and intrusions, as well as providing access control, license plate recognition,
0 views • 6 slides
Understanding Theft Offences: Elements and Case Law
Theft offences, including theft and robbery, are defined under the Theft Act 1968. A person is guilty of theft if they dishonestly appropriate property belonging to another with the intention to permanently deprive them of it. The elements of theft involve actus reus (appropriation) and mens rea (di
0 views • 26 slides
Cash Assistance Card System Overview in Bekaa Valley, Lebanon
This presentation provides details on the dual card system for cash assistance in Bekaa Valley, Lebanon. It explains the two cards - CSC ATM Card and WFP E-Card, their purposes, features, usage instructions, and what to do in case of issues. The WFP E-Card is for food assistance, whereas the CSC ATM
0 views • 9 slides
Innovative ATM Protection System by 3SI Security Systems
3SI Security Systems offers a cutting-edge solution for protecting static ATMs in non-regulated markets. Their system includes standard components like the NCR S1 IN LID General Control Unit and GCU with various features and sensors for enhanced security. The system works by automatically detecting
0 views • 16 slides
Understanding Fragmentation in Air Traffic: Case Studies and Impact on ATM Performance
Fragmentation, defined as being torn apart or crashed into pieces, is explored through case studies on air traffic fragmentation and its impact on ATM performance. The discussion delves into different industries' use of fragmentation, highlighting that it is not necessarily linked with efficiency an
0 views • 11 slides
Benefits of Transitioning to Trajectory-Based Operations (TBO)
Explore the operational benefits of Trajectory-Based Operations (TBO) in modernizing the ATM system, endorsed by IATA as the core of ICAO's Global ATM Operational Concept. Learn about performance improvement opportunities and the long-term advantages of integrating TBO into aviation operations.
0 views • 4 slides
Aviation Seminar: The Evolution of CNS in European ATM Network
Exploring the past and future of Communication, Navigation, and Surveillance (CNS) in Air Traffic Management (ATM), this presentation delves into the critical role of CNS technologies, including airspace management, air traffic flow, and aeronautical information services. It highlights developments
0 views • 13 slides
Understanding Robbery: Elements, Definition, and Distinctions
Robbery, defined under Section 8 of the Theft Act 1968, involves the act of stealing with the use of force or threat of force. This offense carries serious consequences, including a potential life imprisonment sentence. The key elements of robbery include the actus reus of theft and force, along wit
0 views • 11 slides
Protect Yourself from Identity Theft and Financial Crimes
Learn about identity theft, how it occurs, and steps you can take to protect yourself. Discover common methods used by fraudsters and the Equifax data breach incident. Find out what to do if you've been impacted by identity theft. Enroll in the TrustedID Premier credit monitoring service for free.
0 views • 23 slides
Addressing Vehicle Theft Crisis: Compulsory Engine Immobilisers in Queensland
Australia faces a significant vehicle theft issue, with Queensland being particularly affected. The societal and individual impacts are vast, highlighting the urgent need for implementing compulsory installation of engine immobilisers in passenger vehicles to combat theft, reduce crime rates, and pr
0 views • 21 slides
Understanding Wage Theft: A Closer Look at Violations and Consequences
Wage theft, a prevalent issue in the labor market, encompasses various violations such as not paying minimum wage, altering breaks, and misclassifying employees. The Fair Labor Standards Act of 1938 addresses these offenses with penalties, including imprisonment for repeat offenders. Studies indicat
0 views • 15 slides
Understanding Identity Theft: Risks for Teens and How to Protect Yourself
Explore the world of identity theft and its potential impact on teenagers. Learn what identity theft entails, why teens are at risk, and the evolving tactics used by criminals. Discover how stolen identities are misused and ways to prevent falling victim to such crimes.
0 views • 41 slides
Woodgrove Bank ATM Activity Overview
Woodgrove Bank currently operates over 275 ATMs across Central City and surrounding counties, with an average of 120 daily transactions per ATM. The top six locations generate significant revenue through monthly transactions, showcasing the popularity of services like cash withdrawals, account balan
0 views • 4 slides
Boston University School of Medicine ATM Committee Overview
Boston University School of Medicine (BUSM) is committed to providing a supportive and respectful environment for medical students. The ATM Committee investigates and responds to reports of student mistreatment, ensuring prompt and impartial handling of complaints. Processes include communication me
0 views • 12 slides
Eighth MIDANPIRG Air Traffic Management Sub-Group Meeting in Amman, Jordan
The Eighth ATM SG Meeting in Amman, Jordan will discuss follow-up on MIDANPIRG/19 conclusions, planning and implementation issues related to ATM/SAR, air navigation priorities, future work program, and more. Updates on ATM/SAR implementation, airspace enhancements projects, and status of approved Pf
0 views • 4 slides
Analyzing ATM-LVIS Difference Statistics for Greenland
The presentation discusses the analysis of ATM-LVIS difference statistics for Greenland, highlighting proposed processing refinements that are expected to have a minimal impact. The data editing process for ATM and LVIS measurements, histogram of slope-corrected differences, differences by slope and
0 views • 10 slides
COMBACTE-CARE: Combatting Bacterial Resistance in Europe - Study Overview
A Phase III study comparing the efficacy, safety, and tolerability of aztreonam avibactam (ATM-AVI) and meropenem colistin (MER-COL) for treating serious infections caused by Gram-negative bacteria, including MBL-producing pathogens. Approximately 300 patients with complicated intra-abdominal infect
0 views • 9 slides
Contribution of HALA Network to ATM Community and SESAR 2020: Achievements and Future Directions
HALA network has been instrumental in fostering research and innovation in the field of automation for ATM systems, providing a platform for knowledge dissemination, collaboration, and advancement. The network has facilitated exploratory research, encouraged young scientists' participation, and crea
0 views • 12 slides
Understanding Gas Laws and Pressure Units
Gas laws relate pressure, volume, and temperature of gases in various units like atmospheres (atm), mmHg, kPa. Standard pressure is 1 atm with conversion factors. Understanding concepts such as STP, volume, temperature, and Dalton's Law of partial pressure is crucial for solving gas law problems. Ex
0 views • 38 slides
Global TBO Symposium 2024: Advancing Aviation Technologies
Explore the future of aviation at the Global TBO Symposium 2024 through discussions on enabling technologies, air-ground collaboration, data link for ATC/ATM functions, aircraft operational updates, and safety-critical decision-making processes. Dive into topics like trajectory sharing, dynamic capa
0 views • 4 slides
Understanding Asynchronous Transfer Mode (ATM) in Data and Computer Communications
Asynchronous Transfer Mode (ATM) is a packet transfer technology that supports multiple logical connections over a single physical interface. It uses fixed-sized packets called cells for data transfer. ATM bears similarities to packet switching and offers streamlined packet transfer with minimal err
0 views • 46 slides
Combating and Preventing Organised Vehicle Crime in Belgium
The project in Belgium aims to combat and prevent organised vehicle crime through the development of a barrier model funded by the European Union. Despite a steady decline in motor vehicle theft in Belgium, challenges persist with the absence of specific expertise in law enforcement agencies and hot
4 views • 17 slides
Understanding Robbery: Elements and Distinctions
Robbery, as defined in Section 8 of the Theft Act 1968, involves the act of stealing accompanied by the use of force or the threat of force to instill fear in order to commit the theft. This offense is considered more serious than theft and can lead to a life imprisonment sentence. The key elements
0 views • 11 slides
China SWIM Program Overview: Enhancing Air Traffic Management
The China SWIM program, initiated in 2011, is a sub-program under the China Civil Aviation Collaborative ATM Technology Program. Funded by the Ministry of Science and Technology (MOST) and the Civil Aviation Administration of China (CAAC), the project aims to study and evaluate SWIM concepts and key
0 views • 10 slides