Real-World Evidence Analytics Market Poised for Staggering Growth
Data management & integration enhancements help improve the speed & quality of drug discovery and clinical trial processes. Artificial intelligence (AI) is employed in real-world data (RWD) to enhance data anomaly detection, standardization, and quality check at the pre-processing stage. AI is expec
1 views • 3 slides
SAFETY TRAINING FOR NEW RECRUITS
This detailed safety training course for new recruits covers a wide range of topics such as group vision, commitment, safety values, HSE risks, golden rules, anomaly reporting, and more. The course is divided into three sections: D1 & D2, D3 to D90, and D3 to D90 continued. Each section includes cla
1 views • 8 slides
Netdata - The Open Source Observability Platform: A Comprehensive Overview
Netdata is an open-source observability platform created by Costa Tsaousis. It enables real-time, high-resolution monitoring with auto-discovery of integrations, unsupervised machine learning for metrics, alerting, visualization, and anomaly detection. With easy installation on any system, Netdata p
1 views • 54 slides
Automated Anomaly Detection Tool for Network Performance Optimization
Anomaly Detection Tool (ADT) aims to automate the detection of network degradation in a mobile communications network, reducing the time and effort required significantly. By utilizing statistical and machine learning models, ADT can generate anomaly reports efficiently across a large circle network
8 views • 7 slides
Real-world Evidence (RWE) Analytics Market Worth $2.93 billion by 2029
Data management & integration enhancements help improve the speed & quality of drug discovery and clinical trial processes. Artificial intelligence (AI) is employed in real-world data (RWD) to enhance data anomaly detection, standardization, and quality check at the pre-processing stage. AI is expec
0 views • 2 slides
Understanding Similarity and Dissimilarity Measures in Data Mining
Similarity and dissimilarity measures play a crucial role in various data mining techniques like clustering, nearest neighbor classification, and anomaly detection. These measures help quantify how alike or different data objects are, facilitating efficient data analysis and decision-making processe
1 views • 51 slides
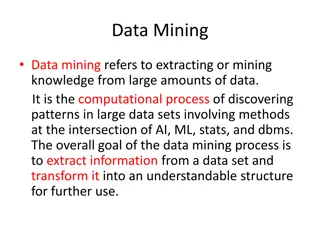
Understanding Data Mining: Processes and Applications
Data mining involves extracting knowledge from large data sets using computational methods at the intersection of AI, ML, stats, and DBMS. It aims to discover patterns and transform data into actionable insights for various applications such as predictive modeling and anomaly detection.
0 views • 11 slides
Understanding Transaction Management in DBMS
In this lecture, Mohammad Hammoud covers the key aspects of transaction management in database management systems (DBMS). Topics include locking protocols, anomaly avoidance, lock managers, and two-phase locking. The session delves into the rules, data structures, and processes involved in maintaini
1 views • 56 slides
Machine Learning Techniques for Intrusion Detection Systems
An Intrusion Detection System (IDS) is crucial for defending computer systems against attacks, with machine learning playing a key role in anomaly and misuse detection approaches. The 1998/1999 DARPA Intrusion Set and Anomaly Detection Systems are explored, alongside popular machine learning classif
0 views • 36 slides
The Art and Science Behind Audubon's Bird Illustrations
Explore the intricate art and scientific accuracy of Audubon's bird illustrations. Discover the techniques and passion behind his iconic works.\n
1 views • 5 slides
Understanding Outlier Analysis in Data Mining
Outliers are data objects that deviate significantly from normal data, providing valuable insights in various applications like fraud detection and customer segmentation. Types of outliers include global, contextual, and collective outliers, each serving distinct purposes in anomaly detection. Chall
0 views • 44 slides
Overview of Unsupervised Learning in Machine Learning
This presentation covers various topics in unsupervised learning, including clustering, expectation maximization, Gaussian mixture models, dimensionality reduction, anomaly detection, and recommender systems. It also delves into advanced supervised learning techniques, ensemble methods, structured p
1 views • 37 slides
Efficient Anomaly Detection for Batch Systems Using Machine Learning
Explore a lightning talk session focusing on using Collectd metrics and job data in HTCondor batch systems for anomaly detection. Challenges with raw historical data are addressed through data collection, manipulation, and application of anomaly detection techniques using ML. Various algorithms such
0 views • 14 slides
Semantics-Aware Intrusion Detection for Industrial Control Systems by Mer Yksel
Mer Yksel, a PhD candidate at Eindhoven University of Technology, specializes in intrusion detection and data analytics with a focus on industrial control systems. His research covers targeted attacks, threat modeling, protection of ICS networks, and innovative anomaly-based approaches for cybersecu
0 views • 31 slides
An Overview of Evading Anomaly Detection using Variance Injection Attacks on PCA
This presentation discusses evading anomaly detection through variance injection attacks on Principal Component Analysis (PCA) in the context of security. It covers the background of machine learning and PCA, related work, motivation, main ideas, evaluation, conclusion, and future work. The content
1 views • 19 slides
Analysis of Gathering Patterns from Trajectories - ICDE 2013
Prevalence of trajectory data due to location acquisition technology enables understanding movement behaviors, group travel patterns, and anomaly detection. Co-travellers patterns like Flocks, Convoys, and Swarms are defined based on group characteristics. Gathering patterns involve events with cong
2 views • 20 slides
Understanding Choledochal Cysts: A Congenital Anomaly of the Biliary Tract
Choledochal cysts are congenital anomalies of the biliary tract characterized by cystic dilatation at various segments. They can lead to complications like biliary cirrhosis and recurrent pancreatitis. Clinical features include jaundice, abdominal pain, and right epigastric mass. Early detection is
0 views • 22 slides
Understanding Enamel Pearl Anomaly in Dentistry
Enamel Pearl is a developmental anomaly where small nodules of enamel form below the cemento enamel junction, mainly on permanent teeth. This anomaly, detected radiographically, can lead to bacterial accumulation, periodontal issues, and inflammation if left untreated. Dental hygienists play a cruci
0 views • 8 slides
Wavelet-based Scaleograms and CNN for Anomaly Detection in Nuclear Reactors
This study utilizes wavelet-based scaleograms and a convolutional neural network (CNN) for anomaly detection in nuclear reactors. By analyzing neutron flux signals from in-core and ex-core sensors, the proposed methodology aims to identify perturbations such as fuel assembly vibrations, synchronized
3 views • 11 slides
Troubleshooting AEP Port Number Display Issue during Call Transfers
A problem occurs where the AEP port number is displayed as the ANI on the Agent CTI client when calls are transferred from an IVR application. This issue arises specifically when calls are transferred to a hunt group instead of a VDN. The VDN, which stands for Vector Directory Number, plays a crucia
0 views • 19 slides
Lessons Learned from On-Orbit Anomaly Research
The On-Orbit Anomaly Research workshop held at the NASA IV&V Facility in 2013 focused on studying post-launch anomalies and enhancing IV&V processes. The presentations highlighted common themes like Pseudo-Software Command Scripts, Software and Hardware Interface issues, Communication Protocols, and
0 views • 55 slides
On-Orbit Anomaly Research at NASA: Causes and Solutions
On-Orbit Anomaly Research (OOAR) at NASA's IV&V Facility involves studying mishaps related to space missions, identifying anomalies, and improving IV&V processes. The research delves into the causes of anomalies, such as operating system faults, and proximate causes like software deficiencies. Detai
0 views • 20 slides
NCEP GEFS Sub-Seasonal Forecasting Exercise
In this exercise, you will generate NCEP GEFS deterministic week 1 and week 2 forecasts for precipitation and temperature anomaly. The practical steps include downloading the necessary data and scripts, extracting the files, and accessing the GEFS model guidance. This exercise focuses on understandi
0 views • 12 slides
Mitigating IoT-Based Cyberattacks on the Smart Grid
Exploring the challenges of cybersecurity in the Smart Grid, focusing on IoT-triggered threats and security challenges. Discusses the need for reliable information access, confidentiality, and privacy protection in the context of evolving attack vectors. Highlights related works in intrusion detecti
0 views • 25 slides
Understanding Tongue Disorders: Ankyloglossia, Black Hairy Tongue, Geographic Tongue
Ankyloglossia, also known as tongue-tied, is a congenital anomaly affecting tongue mobility. Black hairy tongue is the lengthening of papillae on the tongue surface, often temporary and resolve without treatment. Geographic tongue presents as white patches and is usually asymptomatic. Treatment opti
0 views • 10 slides
Nephis Courage Yellow Sign Song Illustrations
Experience the vibrant illustrations for the "Nephi's Courage" yellow sign song, featuring classroom-sized pictures on yellow and goldenrod paper. Created by Bill N. Hansen Jr. and Lisa T. Hansen, these visuals bring the inspiring lyrics to life, encouraging courage and providing a visual aid for te
0 views • 20 slides
Anomaly-Based Network Intrusion Detection in Cyber Security
An overview of the importance of network intrusion detection, its relevance to anomaly detection and data mining, the concept of anomaly-based network intrusion detection, and the economic impact of cybercrime. The content also touches on different types of computer attacks and references related to
0 views • 32 slides
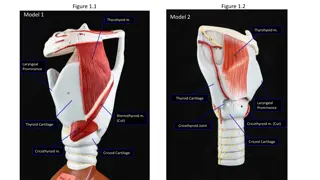
Anatomy of the Larynx: Detailed Illustrations and Muscle Actions
Detailed illustrations and descriptions of the anatomy of the larynx, including structures such as the thyroid cartilage, epiglottis, vocal folds, and muscles like the cricothyroid and posterior cricoarytenoid. The images depict the laryngeal landmarks, ligaments, and nerves, providing a comprehensi
0 views • 5 slides
LD-Sketch: Distributed Sketching Design for Anomaly Detection in Network Data Streams
LD-Sketch is a novel distributed sketching design for accurate and scalable anomaly detection in network data streams, addressing challenges such as tracking heavy keys in real-time across a vast key space. By combining high accuracy, speed, and low space complexity, LD-Sketch enables efficient heav
0 views • 25 slides
Understanding Anomaly Detection in Data Mining
Anomaly detection is a crucial aspect of data mining, involving the identification of data points significantly different from the rest. This process is essential in various fields, as anomalies can indicate important insights or errors in the data. The content covers the characteristics of anomaly
0 views • 50 slides
Anomaly Detection in Data Mining: Understanding Outliers and Importance
Anomaly detection is crucial in data mining to identify data points significantly different from the norm. This technique helps in recognizing rare occurrences like ozone depletion anomalies. Understanding the distinction between noise and anomalies is key, as anomalies can provide valuable insights
0 views • 35 slides
Anomaly Detection Using Process Behavior Charts
Explore the philosophy behind understanding variation and key principles in anomaly detection using process behavior charts. Learn about preparing data, creating SAS charts, running tests for special causes, and executing a plan for anomaly detection and reporting processes. The material draws heavi
0 views • 41 slides
Study on Ionospheric Perturbation Due to Solar and Geomagnetic Activity in Odessa Magnetic Anomaly
Research conducted in the area of the Odessa magnetic anomaly investigates ionospheric perturbations caused by solar and geomagnetic activity. The study utilizes radio astronomical and magnetometric observations from various observatories, highlighting the significance of the geomagnetic anomaly nea
0 views • 18 slides
Supporting Military Veterans with PTSD at End of Life: Insights and Video Illustrations
Video illustrations and insights from hospice and palliative care clinicians, focusing on supporting military veterans with PTSD at the end of life. The team of professionals provides tips and personal insights, along with three videos showcasing veterans discussing trauma and compassionate care. Vi
0 views • 21 slides
Detecting Performance Anomalies in Cellular Networks via Regression Analysis
The study focuses on detecting performance anomalies in cellular networks using regression analysis. It addresses challenges such as labeling, rare anomalies, and correlated factors. The tool CellPAD is introduced for anomaly detection, supporting various prediction algorithms and offering insights
0 views • 19 slides
Solving Cosmic Gamma Background Anomaly: Ekaterina Shlepkina's Research Insights
Explore the quest to find a solution for the cosmic gamma background anomaly in cosmic rays through Ekaterina Shlepkina's research presented at the XXII International Workshop. Learn about the investigations into cosmic rays fluxes, antiparticle studies, and possible interaction types of Dark Matter
1 views • 19 slides
Lactase Film Activity Illustrations from Got Lactase? Educator Materials
Explore the engaging illustrations from the Got Lactase? film activity, showcasing figures and visuals related to lactase activity. These detailed images provide a visual aid for understanding the concepts presented in the educational materials. Dive into the world of lactase with these informative
0 views • 4 slides
Book Analysis: Illustrations and Character Insights
Exploring the front and back covers of a variety of children's books with a focus on crayons, animals, squirrels, cats, buses, fairytales, and koalas. Analyzing the emotions and characteristics depicted through illustrations and discussing potential reasons behind the creative choices made by the au
0 views • 15 slides
Effects of Illustrations on Systematic Thinking in Expository Text Understanding
Understanding how illustrations impact the development of mental models when processing expository text is explored in Mayer's study. The experiment with novice college students shows that text paired with illustrations promotes better recall and transfer of explanatory information compared to text
0 views • 15 slides
Anomaly Detection Methods for Alternative Data in CPI Statistics
Anomaly detection is crucial in ensuring the accuracy of Consumer Prices Indices (CPI). This article explores various anomaly detection methods, including distance-based, density-based, Gaussian mixture modeling, principle component analysis, and entropy-based approaches. Each method has its advanta
0 views • 24 slides