Solution for Active Directory Security, cionsystems
With easy management, advanced reporting, delegation, best workflow, GPO control, real time alerts for changes and many more feature makes it the best. https:\/\/cionsystems.com\/
3 views • 7 slides
Active Directory Delegation, cionsystems.com
The Active Directory Manager Pro features active directory delegation which can help organizations to reduce the number of high privilege accounts thereby reducing risk and enhancing security. https:\/\/shorturl.at\/uLNP7
2 views • 7 slides
Active Directory Auditing, cionsystems.com
A very simple and cost effective solution that makes active directory auditing easy proactively tracking and giving change alerts. https:\/\/rb.gy\/ttey9o
2 views • 7 slides
Active Directory Backup and Recovery, cionsystems
Sometimes human error, technology failures and malicious actions can easily corrupt the directory. \/\/rb.gy\/klwubf
1 views • 7 slides
Arkansas Community Mental Health Center Directory
The Arkansas Community Mental Health Center Directory provides contact information for various mental health providers in different areas of Arkansas, including services offered and emergency contact numbers. The directory includes details for Ouachita Behavioral Health and Wellness, Counseling Asso
0 views • 7 slides
Understanding the Role of Security Champions in Organizations
Security Champions play a vital role in decision-making concerning security engagement, acting as a core element in security assurance processes within a team. They foster a security culture, reduce dependency on the CISO, and promote responsible autonomy and continuous security education in the org
3 views • 13 slides
Reflecting on Catholic School Prayer and Liturgy: A Journey of Faith and Education
Explore the intersection of faith and education in Catholic schools through the lens of prayer and liturgy, guided by the new Prayer and Liturgy Directory. Delve into the essence of worship, the importance of holding onto our beliefs, and the role of Jesus Christ in shaping the ethos of Catholic edu
2 views • 37 slides
Enhancing Professional Learning Through Active Listening Framework
Explore a comprehensive professional learning resource focusing on inclusion, wellbeing, and equalities for Scotland's educators and learners. The resource includes slides on active listening, interconnectivity, and guidance on how to utilize the material effectively. Dive into the National Model fo
11 views • 24 slides
Understanding Active Directory: Key Components and Security Considerations
Active Directory is a crucial component in Windows networks, providing centralized resource management, authentication, and authorization services. Key components include objects, domains, domain controllers, OUs, forests, and group policies. Understanding the data store, NTDS.dit file, partitions,
6 views • 68 slides
Active Directory Backup and Recovery, cionsystems
Sometimes human error, technology failures and malicious actions can easily corrupt the directory. \/\/tinyurl.com\/5xpuutyd
3 views • 7 slides
Active Directory Security Solution, cionsystems.com
With easy management, advanced reporting, delegation, best workflow, GPO control, real time alerts for changes and many more feature makes it the best. \/\/cionsystems.com\/
2 views • 7 slides
School Staff Directory and Special Education Team at Terra Centre 2023-2024
Explore the comprehensive staff directory for Terra Centre 2023-2024, including teachers from Kindergarten to 6th grade, specialists, support staff, and the Special Education Team. Learn about key administrators, student monitors, and the PAC and ECCB teams. Dive into a dynamic educational environme
1 views • 123 slides
Understanding File and Directory Operations in Operating Systems
Explore the concepts of files and directories in operating systems, including persistent storage, file systems, directory structures, creating and accessing files, and reading/writing file data. Dive into the foundational elements essential for managing data effectively on computer systems.
0 views • 34 slides
Directory of Algerian Importers - Contact Information and Activities
Explore a comprehensive directory of Algerian importers showcasing a variety of products such as textiles, carpets, leather, rice, fruits, sports wear, spices, pharmaceuticals, and surgical equipment. Contact details and activities of various importers in Algeria provided.
1 views • 29 slides
Understanding Mandatory and Directory Statutes: A Legal Overview
Mandatory statutes compel specific actions with no discretion allowed, making non-compliance potentially void. Directory statutes outline procedures without affecting substantial rights, with compliance regarded as a matter of convenience. The interpretation of these statutes rests on legislative in
1 views • 18 slides
Understanding the Roles of a Security Partner
Learn about the roles and responsibilities of a Security Partner, including requesting changes to security roles, approving security requests, and initiating access requests. Explore the overview of Workday Security, the security access request process, and the pre-request process flow. Discover how
1 views • 17 slides
Oregon Teacher Loan Forgiveness Program Overview
The Oregon Teacher Loan Forgiveness Program is designed to incentivize individuals to pursue and remain in the teaching profession, particularly in high-poverty schools. The Oregon Department of Education plays a crucial role in determining school eligibility for the Teacher Cancellation Low Income
0 views • 19 slides
Approved Food Sources for Armed Forces Procurement
The Worldwide Directory of Sanitarily Approved Food Establishments provides a comprehensive list of approved food sources for Armed Forces procurement, audited for sanitation and quality. Suppliers seeking approval must follow specific requirements outlined in the directory to become eligible for bi
0 views • 14 slides
Understanding Directory Structures in Operating Systems
Directory structures play a crucial role in operating systems, organizing files, and supporting essential operations like file search, creation, deletion, listing, and traversal. This content explores single-level and two-level directory structures, addressing their benefits and limitations in manag
2 views • 23 slides
Active Schools Games: Fun Fitness and Sports Challenges Await!
Join the exciting Active Schools Games featuring Starlight Steps to Fitness (Beginner), Starlight Steps to Fitness (Advanced), and Starlight Sports Challenges Game. Roll the dice, complete challenges, earn points, and race to the finish line in these engaging fitness and sports activities. Choose op
0 views • 8 slides
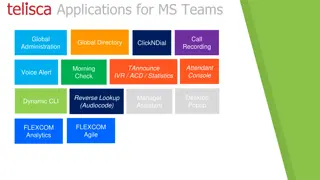
Telisca Suite: Enhancing MS Teams Integration with Advanced Tools
Explore the Telisca suite of applications and tools designed to enhance MS Teams functionality. From call recording to global directory management, Azure authentication, and gateway configurations, Telisca offers a comprehensive solution for optimizing communication and collaboration within the Team
0 views • 92 slides
Understanding Active vs Primary Status in Education System of British Columbia
In the education system of British Columbia, students classified as Active no Primary are those who are no longer active in their Primary School (School of Record) but are active in a Secondary School. This status affects reporting, tracking, and school record maintenance. Schools and Districts have
0 views • 8 slides
Enhancing Learning Through Active Engagement: Strategies and Insights
Explore the concept of active learning with Swati Ramani, Director of Faculty Development & Curriculum Management at the Southern California University of Health Sciences. Discover the practical applications of active learning, key learning outcomes, and strategies for effective implementation. Dive
1 views • 19 slides
Mastering Active Directory Management with PowerShell
Learn essential tips and techniques for managing Active Directory using PowerShell, including starting tips, staying up-to-date with PowerShell versions, methods of management, exploring Active Directory commands, getting information from AD, and selecting, sorting, and exporting data efficiently.
0 views • 15 slides
Insights from Residents on Active Travel in Doncaster
This report highlights findings from a survey on active travel in Doncaster, covering respondent demographics, levels of active travel, influencing factors, preferred transport methods, perceptions, future plans, and key insights. Key findings include the age groups and employment status of responde
0 views • 35 slides
Understanding User Accounts and Directory Services in Network Computing
Explore the role of user accounts and directory services in network-centric computing infrastructure. Learn about Directory Servers, User Administration in Unix, and the concept of Group Accounts in Unix. Discover how Directory Services provide centralized repositories for managing information, enab
0 views • 9 slides
NAU WordPress Unit Updates and Training Highlights - July 2019
NAU's WordPress Unit web coordinators conducted their monthly summit in July 2019, covering status updates, site level moves, directory updates, training, enterprise workshops, accessibility improvements, and more. Key highlights include the transfer of sites between platforms, launch of new sites,
0 views • 16 slides
Provider Directory Advisory Group Meeting Summary
The Provider Directory Advisory Group Meeting held on November 18, 2015, covered various topics including Clinical Quality Metrics, Registry Presentation, Procurement updates, and Common Credentialing. The meeting involved breakout sessions, group discussions, and group presentations focusing on ref
0 views • 48 slides
Understanding Fine-Grained Password Policies in Active Directory
Explore the intricacies of Fine-Grained Password Policies (FGPP) in Active Directory, covering topics such as domain account policies, policy recovery methods, interpreting pwdProperties attribute, and implementing PSOs for granular password settings. Delve into the nuances of password complexity, h
0 views • 11 slides
SecDir: A Secure Directory to Defeat Directory Side-Channel Attacks
SecDir introduces a secure directory design to mitigate directory side-channel attacks, a critical security threat. By reassigning part of the conventional directory storage to per-core private directories, SecDir aims to block directory interference between processes and enhance security in cache h
0 views • 49 slides
Essential Windows Enterprise Services Overview
Exploring Windows Enterprise Services, the Introductions to UNM Directory Services, the LAMB Authoritative Source of Information for AD processes, and the benefits of RSAT (Remote Server Administration Tools). Discover the delegation of responsibilities in OU structures and the nuances of Group Type
0 views • 16 slides
Comprehensive Overview of Forefront Identity Manager (FIM)
Forefront Identity Manager (FIM) is a Microsoft solution that applies business rules to manage Active Directory accounts effectively. It streamlines account provisioning, de-provisioning, and attribute management for various user categories like students, employees, alumni, and retirees. FIM central
0 views • 11 slides
New Generation Network Security System Evolution and Implementation
The presentation outlines the evolution of network security systems, focusing on the transition from traditional firewalls to next-generation systems like intrusion detection systems. It highlights the limitations of current systems in detecting internal threats and the need for advanced solutions t
0 views • 9 slides
Civic Directory and Citizen Inputs from Ward Sabha Meeting
The content provides information about the Ward Sabha meeting held in Madiwala Ward #172 on September 23, 2017. It includes details about Covered RWAs, Civic Directory listing agency contacts, and guidelines for referring to the minutes of the meeting. The slides showcase citizen inputs and agency r
0 views • 23 slides
Understanding Active/Active SQL Clusters for High Availability
Discover the importance of Active/Active SQL clusters for ensuring 24/7 availability of your database servers. Learn about the benefits, setup process, and the high availability solution it offers for the entire server instance. Follow a detailed step-by-step guide for setting up SQL Active/Active c
0 views • 18 slides
Comprehensive DevOps Security Training Overview
This Certified DevOps Security Practitioner course provides a deep dive into implementing DevSecOps, integrating security into the DevOps processes. Covering topics like security testing, Docker security, automation, and more, the training aims to equip participants with the necessary skills to embe
0 views • 5 slides
Managing and Updating R2 Source Codes and Data Documentation
Set the home directory to prevent future directory changes before running real-time processes. Two versions of run_gdas scripts are provided along with instructions for setting up directories, updating scripts, and accessing necessary data files. Various resources and tools are mentioned, including
0 views • 62 slides
Envirolink Tools Project - Decision Support Systems Directory
Envirolink Tools Project offers a web-based searchable directory of Decision Support Systems (DSS) with key metadata and case studies, aiding Councils in evaluating DSS opportunities. Created due to demand identified in workshops, the project aims to assist in meeting management needs effectively. V
0 views • 8 slides
Comprehensive Integrated Security Solution Overview by Microsoft
Ponemon Institute's Cost of Data Breach Study reveals the significant financial impacts of data breaches. Microsoft offers an intelligent, unified enterprise defense solution through Microsoft Threat Protection, Azure Security Center, and Azure Sentinel. This comprehensive array of integrated securi
0 views • 6 slides
Efficient Bucket Management in Extendible Hashing
In cases where a bucket (primary page) becomes full in extendible hashing, re-organizing the file by doubling the number of buckets can be costly in terms of resource utilization. An alternative approach involves using a directory of pointers to buckets and doubling the directory instead of all buck
0 views • 9 slides