Active Directory Delegation, cionsystems.com
The Active Directory Manager Pro features active directory delegation which can help organizations to reduce the number of high privilege accounts thereby reducing risk and enhancing security. https:\/\/shorturl.at\/uLNP7
2 views • 7 slides
Active Directory Auditing, cionsystems.com
A very simple and cost effective solution that makes active directory auditing easy proactively tracking and giving change alerts. https:\/\/rb.gy\/ttey9o
2 views • 7 slides
Active Directory Penetration Testing, cionsystems
The partner plan of AD Guardian is used by professional services which include penetration testing to test if your AD is secure from such threats. http:\/\/tinyurl.com\/4yzps5xv
1 views • 2 slides
Arkansas Community Mental Health Center Directory
The Arkansas Community Mental Health Center Directory provides contact information for various mental health providers in different areas of Arkansas, including services offered and emergency contact numbers. The directory includes details for Ouachita Behavioral Health and Wellness, Counseling Asso
0 views • 7 slides
Active Directory Penetration Testing, cionsytems.com
The partner plan of AD Guardian is used by professional services which include penetration testing to test if your AD is secure from such threats. \/\/rb.gy\/2f1rq2
4 views • 7 slides
Understanding Active Directory: Key Components and Security Considerations
Active Directory is a crucial component in Windows networks, providing centralized resource management, authentication, and authorization services. Key components include objects, domains, domain controllers, OUs, forests, and group policies. Understanding the data store, NTDS.dit file, partitions,
6 views • 68 slides
Active Directory Penetration Testing, cionsystems.com
The partner plan of AD Guardian is used by professional services which include penetration testing to test if your AD is secure from such threats. \/\/rb.gy\/m1wkb8
2 views • 2 slides
Penetration Testing and Incident Response Technologies Overview
Explore the world of penetration testing, incident response technologies, and ethical hacking in the context of CIS 6395 course at UCF. Learn about tools like Metasploitable 2 VM for vulnerability testing and techniques such as Ping Sweep and Ping. Discover essential concepts for testing and securin
0 views • 32 slides
Comprehensive Guide to Penetration Testing Execution Standard (PTES)
Penetration Testing Execution Standard (PTES) is a crucial methodology to simulate attackers' methods for compromising security controls and gaining access to systems. The PTES process involves phases such as Pre-Engagement, Intelligence Gathering, Threat Modeling, Vulnerability Analysis, Exploitati
3 views • 14 slides
Polymeric Controlled Drug Delivery Systems
Polymeric controlled drug delivery systems play a crucial role in regulating drug release through diffusion, solvent penetration, and chemical mechanisms. These systems include diffusion-controlled, solvent-controlled, and chemically-controlled devices, each operating based on specific principles. S
0 views • 33 slides
Understanding Software Testing Metrics and Tools
Software testing metrics play a crucial role in evaluating the quality and progress of the testing process. Metrics provide valuable insights into the readiness, quality, and completeness of a product. By measuring attributes such as defects, testing efficiency, and productivity, organizations can m
3 views • 100 slides
Fundamentals of Software Testing Explained
Software testing is a critical process to ensure that software applications meet requirements and are free of defects. It involves various activities such as test planning, analysis, design, implementation, and execution. Testing approaches like the Bing bang approach and Total Quality Management ar
1 views • 48 slides
Disaster Recovery and Incident Response Concepts
This content covers the essential concepts of disaster recovery, incident response, penetration testing, vulnerability scanning, and business continuity planning in the context of cybersecurity. It explains the goals and steps involved in penetration testing, vulnerability scanning tasks, business c
2 views • 15 slides
Shopper Insight Report - Northern Ireland Region Analysis
This Shopper Insight Report covers a 52-week period from 02/05/2016 to 30/04/2017, focusing on key performance indicators like sales growth, customer penetration, and customer loyalty. Recommendations include focusing on core stores with high demand, increasing penetration and repeat rate, and utili
0 views • 23 slides
Understanding Equivalence Class Testing and Its Application in Software Testing
Equivalence class testing is a software testing technique that involves dividing input values into classes for effective testing coverage. Equivalence classes are defined mathematically as subsets of a given set, ensuring partitioning and mutual exclusivity. By applying equivalence partitioning, tes
1 views • 21 slides
Uganda's Successes in Reaching Men with HIV Testing Through Assisted Partner Notification Program
Uganda has successfully implemented an Assisted Partner Notification (APN) program to reach men for HIV testing, addressing the gender gap in testing rates. By utilizing various approaches such as index testing, self-testing, and social network testing, Uganda has achieved significant success in tar
0 views • 12 slides
Understanding Directory Structures in Operating Systems
Directory structures play a crucial role in operating systems, organizing files, and supporting essential operations like file search, creation, deletion, listing, and traversal. This content explores single-level and two-level directory structures, addressing their benefits and limitations in manag
2 views • 23 slides
Software Testing Foundation Level: Testing Throughout the SDLC Quiz
Explore key concepts in software testing throughout the Software Development Lifecycle (SDLC) with a quiz covering topics like white-box testing in acceptance testing, component testing vs. system testing, and regression testing purposes. Enhance your understanding of testing methodologies with samp
5 views • 17 slides
Importance of Software Testing in Preventing Catastrophic Failures
Software testing is crucial in ensuring the reliability and safety of software systems, as highlighted by catastrophic failures such as the Ariane 5 rocket incident and the Therac-25 radiation therapy machine disasters. These examples underscore the importance of thorough testing in identifying and
1 views • 42 slides
Automated Security Testing Using ZAP API
Explore how to automate security testing using the ZAP API, an integrated penetration testing tool, to find vulnerabilities in web applications. Learn how to set up Sahi to communicate with ZAP and conduct security testing efficiently with automated scripts.
0 views • 17 slides
Testing Approach in SCREAM for E3SM Fall All-Hands 2019
Major effort is focused on verification and testing in SCREAM for the E3SM Fall All-Hands. The initiative includes unit testing, property testing, regression testing, and leveraging various tools like Cmake, Python, Jenkins, AutoTester, and GitHub for Continuous Integration (CI). The emphasis is on
1 views • 21 slides
Understanding Penetration Testing Tactics and Techniques
In the realm of secure software engineering, penetration testing plays a crucial role in proactively identifying vulnerabilities. This involves delving deep to exploit potential weaknesses and simulate real-world attack scenarios. Skilled testers, both in-house and external, use frameworks like MITR
0 views • 16 slides
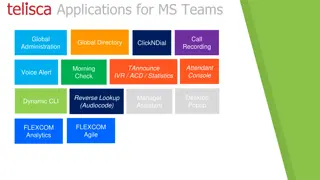
Telisca Suite: Enhancing MS Teams Integration with Advanced Tools
Explore the Telisca suite of applications and tools designed to enhance MS Teams functionality. From call recording to global directory management, Azure authentication, and gateway configurations, Telisca offers a comprehensive solution for optimizing communication and collaboration within the Team
0 views • 92 slides
Comprehensive Guide to Intelligence Gathering and Penetration Testing Stages
Understanding the importance of intelligence gathering in security and the stages of penetration testing - information gathering, scanning, exploitation, and reporting. Delve into tools like nslookup for server information and leverage Google Dorks for database vulnerabilities. Safeguard your system
0 views • 4 slides
Enhancing Insurance Penetration in Ghana Through Digital Innovation
Dr. Gideon Amenyedor explores how digital insurance can enhance insurance penetration in Ghana by leveraging technology to improve existing insurance models and create new ones. The strategic application of digital technology aims to address the low insurance penetration rate in the country by consi
0 views • 18 slides
Essentials of Penetration Testing: Expectations and Performance
This presentation delves into the realm of penetration testing, outlining the basic expectations and performance aspects. It emphasizes the importance of clear planning, client-side and auditor-side negotiations, and commencing the audit process diligently. With insights into the types of audits, sc
0 views • 32 slides
Mastering Active Directory Management with PowerShell
Learn essential tips and techniques for managing Active Directory using PowerShell, including starting tips, staying up-to-date with PowerShell versions, methods of management, exploring Active Directory commands, getting information from AD, and selecting, sorting, and exporting data efficiently.
0 views • 15 slides
Understanding User Accounts and Directory Services in Network Computing
Explore the role of user accounts and directory services in network-centric computing infrastructure. Learn about Directory Servers, User Administration in Unix, and the concept of Group Accounts in Unix. Discover how Directory Services provide centralized repositories for managing information, enab
0 views • 9 slides
Understanding Testing in Software Engineering
In the previous session, we discussed various aspects of software engineering, including modeling with UML diagrams, such as activity diagrams, use case diagrams, sequence diagrams, state diagrams, and class diagrams, as well as architecture patterns. Testing was emphasized as a key aspect, highligh
0 views • 35 slides
Understanding Gray Box Testing in Software Development
Gray Box Testing is a software testing technique that involves testing the software with partial knowledge of its internal workings. It combines aspects of White Box Testing and Black Box Testing, allowing testers to check both the presentation layer and the code part of an application. Gray Box Tes
0 views • 14 slides
Understanding Fine-Grained Password Policies in Active Directory
Explore the intricacies of Fine-Grained Password Policies (FGPP) in Active Directory, covering topics such as domain account policies, policy recovery methods, interpreting pwdProperties attribute, and implementing PSOs for granular password settings. Delve into the nuances of password complexity, h
0 views • 11 slides
Understanding Armitage and Metasploit for Penetration Testing
Explore the capabilities of Armitage and Metasploit in penetration testing, comparing their attack styles, advantages, and limitations. Learn how Armitage simplifies the process by providing a GUI front-end for Metasploit, making it user-friendly for conducting machine-gun style attacks. Discover th
0 views • 16 slides
SecDir: A Secure Directory to Defeat Directory Side-Channel Attacks
SecDir introduces a secure directory design to mitigate directory side-channel attacks, a critical security threat. By reassigning part of the conventional directory storage to per-core private directories, SecDir aims to block directory interference between processes and enhance security in cache h
0 views • 49 slides
Understanding Requirements-Based Testing in Software Development
Dive into the world of requirements-based testing in software development, exploring main concepts, test levels, testing roles, and the importance of testing your solution and modeling case. Learn about test cases, different testing activities, and the significance of acceptance testing in identifyi
0 views • 16 slides
Guidelines for HIV Testing During Pregnancy and Postpartum
These guidelines recommend HIV testing during pregnancy, at delivery, and postpartum. Testing should be done early in pregnancy and again in the third trimester. Expedited testing during labor is required for certain patients, and syphilis testing is recommended. Pre-exposure and post-exposure proph
0 views • 18 slides
Understanding Unit Testing in Software Engineering
Concept Software is a discipline comprising various code pieces. Testing these codes together is complex but vital in Software Engineering. The process includes early testing like unit tests, pairwise/multiple component testing, module testing, integration testing, user tests, alpha tests, beta test
1 views • 6 slides
Understanding Active/Active SQL Clusters for High Availability
Discover the importance of Active/Active SQL clusters for ensuring 24/7 availability of your database servers. Learn about the benefits, setup process, and the high availability solution it offers for the entire server instance. Follow a detailed step-by-step guide for setting up SQL Active/Active c
0 views • 18 slides
Analysis of Multi-Wall Penetration Loss Model for HEW System-Level Simulation
In December 2014, a multi-wall penetration loss model for HEW system-level simulation was proposed by Kejun Zhao, Yunxiang Xu, and Xiaoyuan Lu from the National Engineering Research Center for Broadband Networks & Applications. The model provides more accurate calculations of penetration loss in ind
0 views • 11 slides
Improving Penetration Testing Through Enhanced Input Vector Identification
Enhance your penetration testing efforts by improving information gathering and response analysis. This comprehensive guide explores various aspects of penetration testing, including information gathering, attack generation, and response analysis, offering valuable insights and strategies to bolster
0 views • 23 slides
Importance of Software and System Testing
Understanding the critical role of software and system testing in identifying and fixing errors before they lead to major failures. Various types of testing such as functional, usability, performance, and reliability testing are essential to ensure the quality of software products. Different classif
0 views • 52 slides