Wireless Hacking
"Explore the world of wireless hacking, from understanding Wireless LAN concepts to building a war-drive kit and utilizing tools like Kismet and Wireshark for scanning and enumeration. Learn about gaining access in 802.11 networks and Kali Linux wireless attacks."
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
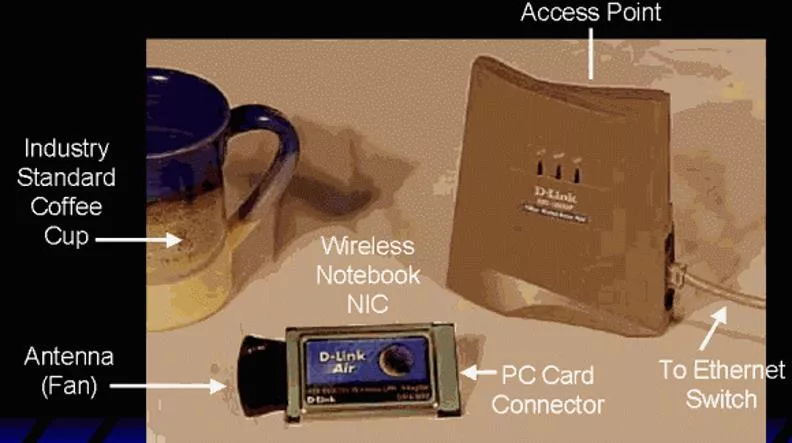
Wireless LANs and footprinting Wireless LANs see basic concepts Linux versus Windows footprinting you need a card that works with the tools the tools need to make the card work in promiscuous mode (sniffing) many cards and few chipsets
Building a war-drive kit Footprinting : locating APs passive: listening to AP broadcasts active: transmitting client beacons in search of AP responses Equipment cards (802.11.b, 11.g) -- choose the software first Antennas (e.g. HyperLink Tech) GPS Software (Windows and Mac) NetSpot Download and YouTube review. inSSID er Download and YouTube overview
More in footprinting software Linux Kismet : both war-drive and sniffer. Uses passive mode (counter-measures difficult). See a YouTube of Kismet in Kali Linux. GisKismet: GISKismet is a visualization tool to represent Kismet data. It currently uses SQLite for the database and GoogleEarth / KML files for graphing. It is a tool in Kali Linux. Wash: A Kali tool that checks if an Access Point is using WPS, the weak and vulnerable security protocol.
Wireless Scanning and Enumeration Packet-Capture and Analysis Review of sniffing: FAQ, tools, concept. Key tool Wireshark available for Linux, Windows and Macs. channel scanning, decryption of WEP (needs key) provides a Peer Map view of hosts found What you are looking for SSID --APs respond to a client ANY SSID with their SSID, and you are in if no username and password required. MAC access control Wireshark and OmniPeek maps MAC addresses WEP - war-drive tools indicate if used (e.g. NetSpot).
Gaining access in 802.11 SSID easy to setup from the ward-drive information just create a profile MAC Access Control use the sniff information to identify valid MAC addresses. spoof the MAC address of your wireless card (Read this article for counter-measures). WEP (Wired Equivalent Privacy) protects data from eavesdropping, not authentication uses key between AP and card transmissions brute-force, key and packet cracking off-line (e.g. Aircrack-ng) EAP (Extensible Authentication Protocol) Methods A client finds an AP and is prompted for a username and password Keys are create dynamically after login SXSW: 'Hot-spot honeypot' hacker's heaven
Kali Linux Wireless Attacks How to install Kali Linux in a Laptop VM Download and install VMware Player Download Kali Linux VM for the Player Start the Player and open the downloaded VM in the player as shown here. There are many attack tools as shown in this other image. Use Kismet, only, if you do not have authorization to test the WLAN. Only use the other tools if you have authorization to test the WLAN because they are invasive, cracking password, etc., tools. See a list of the top 10 Kali wireless attack tools.
Counter measures Some basic ideas: recommendations to secure a WLAN. suggestions to minimize WLAN threats. overview of weakness and solutions for WLANs (old, but good). some commercial solutions: AirDefense, Mojo, SmartPass . State-of-the-art solutions WPA and WPA2: review and Windows Using a Radius server for authentication The IAS Radius service in Windows. FreeRadius home page and tutorial Some WLAN security guides. George Ou guide NIST SP 800-53

 undefined
undefined