Lattice Reduction Techniques in Cryptography
Learn about lattice reduction techniques, such as BKZ, Gaussian Heuristic, and Gram-Schmidt Orthogonalization, used in lattice cryptography to solve Unique and Approximate Shortest Vector Problem (uSVP and ?-SVP). Discover how tools like determinant and QR factorization help in bounding and estimating vectors in lattices.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
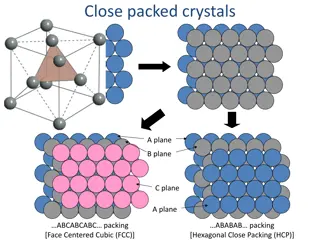
BKZ Overview SVP asks to find the shortest nonzero vector, in an arbitrary lattice Algorithms for SVP (Sieving, Enumeration) Not the topic of this presentation In lattice crypto, best attacks come from solving Unique SVP (?-uSVP) Find the shortest nonzero vector (length ?1) In a lattice where the shortest nonzero vector is unusually short (?1< ? ?2) Approximate SVP (?-SVP) Find a short nonzero vector (length at most, ??1) In an arbitrary lattice Unique SVP and Approximate SVP are solved using BKZ BKZ needs to Solve SVP on lower dimensional lattices (dimension aka Block Size, ?) Polynomially many times We will call this subroutine an SVP oracle
Tools for reasoning about BKZ Lattice Determinant Minkowski s theorem Gaussian Heuristic Gram-Schmidt Orthogonalization QR factorization Geometric Series Assumption
Lattice Determinant det() What it says on the tin: Write lattice basis vectors as row vectors Stack them on top of one another making a ? ? square matrix Take the determinant of said matrix What it means The volume of the unit cell of the lattice i.e. the density of points in the lattice is Density of points in lattice does not depend on choice of basis So neither does the lattice determinant 1 det( )
Using det() to Bound/Estimate ?1 Minkowski s theorem 1 ? ?1 ? (det( )) Gaussian Heuristic ? 1 ? ?1 2?? (det( ))
Gram Schmidt Orthogonalization Start with a basis, (?1,?2, ,??) Create a set of orthogonal vectors (?1 of ??onto the space orthogonal to (?1,?2, ,?? 1) i.e. ?1 ?2 Etc. |?? lower dimensional space Since ?=1 |?? Bases where |?1 So, if you want short vectors in your basis, you will want |?? is the projection ), where ?? ,?2 , ?? = ?1 ?2,?1 |?1|?1 = ?2 | tends to decrease with increasing ?, as ??is projected onto an ever ? | = det( ) is independent of basis, | = |?1| is small, will have |?? | for other ? larger to compensate | to decrease slowly
Lattice reduction and Gram-Schmidt norm Bad Basis Good Basis ?? ?
QR factorization Related to Gram-Schmidt orthogonalization Let ? be a basis matrix with vectors as columns Can factor as ? = ?? ? is orthogonal ? is upper triangular Compute by rotating ?? onto the coordinate axes: ??,?1 ?1 ??,?2 ?2 ?? ?2,?1 ?1 ?2 ?1 ? = 0 0 0
HKZ reduction (What to do with an SVP oracle) Use QR factorization ??,?1 ?1 ??,?2 ?2 ?? ?2,?1 ?1 ?2 ?1 Note from the form of: ? = 0 0 0 1 Can subtract off vectors to the left of ?? so that ??,?? A basis is HKZ reduced if ??,?1 2 ?1 The projection of ?2, ?? orthogonal to ?1 2 1 = ?1 is HKZ reduced
BKZ algorithm HKZ reduce square submatrices of size ? Tour: Start at the top left and move down to the bottom right May require multiple tours before basis stops improving XXXput in estimates for number of SVP calls and basis quality from https://wheat2016.lip6.fr/HEAT_Paris_Damien.pdf https://wheat2016.lip6.fr/HEAT_Paris_Damien.pdf if we don t find anything better XXX
Attacks and Lattice Problems LWE and NTRU style cryptosystems get unique SVP and approximate SVP instances via primal and dual attack strategies LWE NTRU Primal uSVP uSVP Dual Approximate SVP uSVP (Hybrid MITM) We will study these strategies in the next few slides
Product LWE (Typical LWE cryptosystem) KeyGen: Generate random matrix/module/polynomial: ? and short matrix/module: ?? Public key components: Dec: Calculate ?? ?? ?? ?? ?? ????= ? + ? ?? ?? ? ? ??= ?? ?? Main variant: Recover ? using noise tolerant encoding/ public ECC ??= ? Enc: Ouroboros Variant: Let ? = ? ?? ?? ?? Generate short matrix/module: ?? ?? ?? Instead Recover Using: Encode message noise tolerantly as ? MDPC decoder (BIKE-3) LRPC decoder (ROLLO-III) Ciphertext components: ?? ?? ??+ ? ?? ?? ? ? ? ? ?? ?? =
Primal Attack (1/3): A lattice associated with LWE ? ? ?? from ??= ?? = ??? + ?? (mod ?) ?? Want to recover short ?? (We only need to find one row at a time if it s a matrix, so treat as a single row vector) Note that ? ??? + ??(mod ?)is close to: ???(mod ?)) ?? = ? (?? A lattice point in the lattice given by basis (vectors are rows): ? ? ? ??
Primal attack (2/3) LWE as BDD Note that ? ??? + ??(mod ?)is close to: ???(mod ?)) ?? = ? (?? A lattice point in the lattice given by basis (vectors are rows): ? ? Finding an unusually close lattice point to a non-lattice point is called Bounded Distance Decoding (BDD) BDD can be converted to uSVP (finding an unusually short nonzero lattice vector) ? ??
Primal Attack (3/3) LWE recovery as uSVP Increase the dimension by 1 and add ? resulting in: ?? ? to the lattice basis, ? ? ? ?? ? ?? ? ? ? ? is called the embedding factor, and its value can be adjusted Optimal value is typically ? 1 Now ?? ?? ?can be found as an unusually short vector in the above lattice.
Dual Attack ? ? Want distinguish ??= ?? random Dual attack strategy: Reduce a lattice that only depends on ? The lattice is defined as solutions ? Basis (vectors are columns): ?? = ??? + ?? (mod ?) from ? to ?? = ? (mod ?) ? ? ?? ? Distinguisher: If we have a short solution ? (??? + ??) ? = ??? + ??? (mod ?) is short ? to ?? = ?(mod ?):
Quotient LWE (NTRU) KeyGen: Generate short matrix/module: Dec: Calculate ?? ?? ?? ?? ?? ?? ??? = Public key: ??? ? = ?? Recover ?? Using: Enc: Generate short matrix/module: ?? NTRU Trapdoor (NTRU, sNTRUprime) MDPC decoder (BIKE-1,2, LEDAcrypt) LRPC decoder (ROLLO-I, II) ?? ?? Ciphertext: ?? ?? ? = ? ?
Primal attack on NTRU Want to recover short ?? ?? ?? ?? from ? = ? ? Recall the primal attack for (Product LWE) ? ? ?? from ??= ?? ?? Want to recover short ?? This is the same up to matrix transpose, assuming ? can be treated as a random matrix, like ?.
Dual Attack on NTRU (Hybrid MITM)