In-Process Isolation with Memory Protection Keys
Secure and efficient in-process isolation with memory protection keys is crucial in preventing security vulnerabilities and bugs, such as the Heartbleed bug. By implementing techniques like language and runtime isolation, cryptographic secrets can be securely managed from native libraries, safeguarding sensitive data from attackers with capabilities including control-flow hijacks and memory corruption. Various state-of-the-art techniques such as ERIM and SFI play a vital role in enhancing application security and mitigating risks associated with untrusted applications.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. Download presentation by click this link. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
E N D
Presentation Transcript
ERIM: Secure, Efficient in ERIM: Secure, Efficient in- -process Isolation with Memory Protection Keys Isolation with Memory Protection Keys process Anjo Vahldiek-Oberwagner, Eslam Elnikety, Nuno O. Duarte, Michael Sammler, Peter Druschel, Deepak Garg
Applications in the Absence of Isolation Absence of Isolation All state accessible at all times to Bugs Security vulnerabilities Application 2
Applications in the Absence of Isolation Absence of Isolation Heartbleed Bug ~70% of CVE assigned by Microsoft are memory safety issues. Microsoft Security Response Center: A proactive approach to more secure code , 2019 3
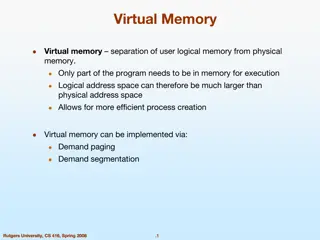
Example In-Process Isolation Use Cases Cryptographic Secrets Managed runtimes from native libraries Trusted Crypto Library Untrusted Application Native Library Managed Runtime 4
User-space Threat Model Untrusted Application Untrusted Trusted Compartment Trusted Operating System CPU Attacker s Capabilities include, but not limited to Control-flow hijacks Memory corruption (i.e., out-of-bounds accesses) Out of scope: Side-channel, row hammer or microarchitectural attacks 5
State of In-Application Isolation Techniques OS/VMM Technique Execution overhead Switch overhead Untrusted Trusted OS/VMM -based2 Lang. & Low Low Medium Sensitive Data Application Application Medium High None None RT3 ERIM Low None Low OS + VMM 1 LwC, SMVs, Shreds, Wedge, Nexen, Dune, SeCage, TrustVisor 2 SFI 6
State of In-Application Isolation Techniques Language and Runtime Techniques Execution overhead Switch overhead Untrusted Trusted OS/VMM- based2 Lang. & Application Low Low Medium Medium High None None Sensitive Data RT3 ERIM Low None Low Operating System 1 LwC, SMVs, Shreds, Wedge, Nexen, Dune, SeCage, TrustVisor 2 SFI 7
State of In-Application Isolation Techniques ERIM Execution overhead Switch overhead Untrusted Trusted OS/VMM- based2 Lang. & Low Low Medium Application Medium High Sensitive data None None RT3 ERIM ERIM Low None Low Operating System 1 LwC, SMVs, Shreds, Wedge, Nexen, Dune, SeCage, TrustVisor 2 SFI, Native Client, Memsentry-MPX 8
Memory Protection Keys (MPK) Address Space Available in Skylake server CPUs Tag memory pages with PKEY Page 3 Page 1 Page 2 Page Table Entry (PTE) PKEY 0 Page 1 9
Intel Memory Protection Keys (MPK) Address Space Available in Skylake server CPUs Tag memory pages with PKEY Page 3 Page 1 Page 2 Page Table Entry (PTE) PKEY 2 Page 1 10
Intel Memory Protection Keys (MPK) Address Space Available in Skylake server CPUs Tag memory pages with PKEY Permission Register (PKRU) Page 3 Page 1 Page 2 CPU Core PKRU Register Page Table Entry (PTE) 15 W 15 R 2 W 2 R 1 W 1 R 0 W 0 R PKEY 2 Page 1 0 0 0 0 0 1 1 0 11
Intel Memory Protection Keys (MPK) Address Space Available in Skylake server CPUs Tag memory pages with PKEY Permission Register (PKRU) Userspace instruction to update PKRU Fast switch between 11 260 cycles/switch Page 3 Page 1 Page 2 CPU Core PKRU Register Page Table Entry (PTE) 15 W 0 15 R 0 2 W 1 2 R 1 1 W 0 1 R 0 0 W 1 0 R 1 PKEY 2 Page 1 12
Intel Memory Protection Keys (MPK) Address Space Available in Skylake server CPUs Tag memory pages with PKEY Permission Register (PKRU) Userspace instruction to update PKRU Fast switch at 50 cycles/switch Page 3 Page 1 By itself, MPK does not protect against malicious attacks. Page 2 CPU Core PKRU Register Page Table Entry (PTE) 15 W 15 R 2 W 2 R 1 W 1 R 0 W 0 R PKEY 2 Page 1 1 1 1 1 1 1 1 1 13
Overview of ERIM Prevent MPK exploitation Safe call gates Prevent execution of permission register updates outside of call gates Untrusted Application PKEY 0 Trusted Compartment PKEY 1 48 83 c0 08 44 01 fa 83 fa 07 77 0f 01 ef 83 ff 07 0f 96 c2 80 Code: 14
Overview of ERIM Prevent MPK exploitation Safe call gates Prevent execution of permission register updates outside of call gates Untrusted Application PKEY 0 Trusted Compartment PKEY 1 48 83 c0 08 44 01 fa 83 fa 07 77 83 ff 07 0f 96 c2 80 Code: 0f 01 ef 15
Overview of ERIM Prevent MPK exploitation Safe call gates Prevent execution of permission register updates outside of call gates Creating usable binaries Inadvertent PKRU update instruction Rewrite strategy Untrusted Application PKEY 0 Trusted Compartment PKEY 1 48 83 c0 08 44 01 fa 83 fa 07 77 83 ff 07 0f 96 c2 80 Code: 0f 01 ef 0f 90 01 ef 16
Overview of ERIM Prevent MPK exploitation Safe call gates Prevent execution of permission register updates outside of call gates Creating usable binaries Inadvertent PKRU update instruction Rewrite strategy Evaluation Frequently-switching use cases 10% higher throughput compared to best existing technique Untrusted Application PKEY 0 Trusted Compartment PKEY 1 48 83 c0 08 44 01 fa 83 fa 07 77 83 ff 07 0f 96 c2 80 Code: 0f 90 01 ef 17
Updating the permission in PKRU register WRPKRU Write EAX into PKRU XRSTOR If bit 9 of EAX is set Load PKRU register from specified memory address 18
Safe switching using call gates call gates Trusted Compartment perm = UNTRUSTED WRPKRU (perm) perm = TRUSTED WRPKRU (perm) goto trusted_entry(T) perm = TRUSTED Untrusted Application 19
Safe switching using call gates call gates Trusted Compartment perm = UNTRUSTED WRPKRU (perm) if (perm != UNTRUSTED) exit; perm = TRUSTED WRPKRU (perm) goto trusted_entry(T) Untrusted Application 20
Prevent execution of WRPKRU/XRSTOR outside of call gates Trusted Compartment FAULT Prevent execution of unvetted pages by New Memory (No Execute) 1) Monitoring system calls and removing the execute permission Untrusted Application 2) ERIM s fault handler scans memory pages and ensures: WRPKRU is part of a call gate XRSTOR is followed by if(eax | 0x100) exit(); System Calls ERIM Operating System 21
Overview of ERIM Prevent MPK exploitation Safe call gates Prevent execution of permission register updates outside of call gates Creating usable binaries Inadvertent PKRU update instruction Rewrite strategy Evaluation Frequently-switching use cases 10% higher throughput compared to best existing technique Untrusted Application PKEY 0 Trusted Compartment PKEY 1 48 83 c0 08 44 01 fa 83 fa 07 77 83 ff 07 0f 96 c2 80 Code: 0f 01 ef 22
Creating usable binaries ERIM halts executables with inadvertent WRPKRUs/XRSTORs Inter-Instruction WRPKRU Intra-Instruction WRPKRU Instruction 1 Instruction 1 Instruction 2 0F 01EF 010F01EF0000 Eliminate inadvertent WRPKRU/XRSTOR by binary rewriting at compile time, runtime prior to enabling execute permission, or via static binary rewriting for pre-compiled binaries 23
Rewriting inadvertent WRPKRUs/XRSTORs Devise rewrite rules for inadvertent WRPKRUs Inter-Instruction: Instruction 1 Instruction 2 0F 01EF 0F 90 01EF Nop 24
Rewriting inadvertent WRPKRUs/XRSTORs Devise rewrite rules for inadvertent WRPKRUs Intra-instruction WRPKRU Simplified x86 instruction format: Prefix Opcode Mod R/M SIB Displacement Immediate Required Optional
Rewriting inadvertent WRPKRUs/XRSTORs Devise rewrite rules for inadvertent WRPKRUs Example rewrite rule: add ecx, [ebx + 0x01EF0000] Opcode 0x01 Mod R/M 0x0F Displacement 0x01EF0000 push eax; mov eax, ebx; add ecx, [eax + 0x01EF0000]; pop eax; Opcode 0x01 Mod R/M 0x07 Displacement 0x01EF0000 26
Overview of ERIM Prevent MPK exploitation Safe call gates Prevent execution of permission register updates outside of call gates Creating usable binaries Inadvertent PKRU update instruction Rewrite strategy Evaluation Frequently-switching use cases 10% higher throughput compared to best existing technique Untrusted Application PKEY 0 Trusted Compartment PKEY 1 48 83 c0 08 44 01 fa 83 fa 07 77 83 ff 07 0f 96 c2 80 Code: 0f 90 01 ef 27
Prototype implementation ERIM userspace library Call gates Memory allocator for trusted component overloading malloc-like functions Memory inspection (exclude unsafe WRPKRU/XRSTOR) Prevent execution on pages with unsafe WRPKRUs/XRSTOR a) P-Trace and seccomp BPF userspace monitor b) Linux Security Module Remove inadvertent WRPKRUs/XRSTORs Static binary rewrite tool based on DynInst 28
Evaluation How frequent are inadvertent WRPKRUs/XRSTORs? Inspected about 200,000 executable files of 5 Linux distributions Found 1213 inadvertent WRPKRU/XRSTOR in binary code DynInst disassembled 1,023 100% rewrite success What is ERIM s overhead in frequently-switching use cases? Isolating session keys in Nginx Isolating a managed runtime (node.js) from native libraries Isolating in-memory state of reference monitors (CPI/CPS) 29
Use case: Session Key Isolation Address Space OpenSSL & LibCrypto AES Compartment NGINX Connection Management Content HTTPS session Handshake protocol Cryptographic keys AES encrypt/decrypt AES key initialization 30
Nginx Throughput with protected session keys ERIM throughput within 5% of native. Normalized Throughput 1 Native 0.8 ERIM 0.6 0.4 0.2 0 0 1 2 4 8 16 32 64 128 File size in KB 31
Nginx Throughput with protected session keys 1.3 million switches per second Normalized Throughput 1 Native 0.8 ERIM 0.6 0.4 0.2 0 0 1 2 4 8 16 32 64 128 File size in KB 32
Comparison to Prior Art 95.4% ERIM 86.4% VMFUNC 73.2% MemSentry-MPX Throughput 1 0.8 0.6 0.4 0.2 0 0kb 1kb 2kb 4kb 8kb 16kb 32kb 64kb 128kb Native ERIM VMFUNC MemSentry-MPX Light-weight Context 33
Summary Prevent MPK exploitation Safe call gates Prevent execution of permission register updates outside of call gates Creating usable binaries Inadvertent PKRU update instruction Rewrite strategy Evaluation Frequently-switching use cases 10% higher throughput compared to best existing technique Untrusted Application PKEY 0 Trusted Compartment PKEY 1 48 83 c0 08 44 01 fa 83 fa 07 77 83 ff 07 0f 96 c2 80 Code: 0f 90 01 ef 34
Thank you! ERIM: Secure, Efficient in ERIM: Secure, Efficient in- -process Isolation with Memory Protection Keys process Isolation with Memory Protection Keys Anjo Vahldiek-Oberwagner, Eslam Elnikety, Nuno O. Duarte, Michael Sammler, Peter Druschel, Deepak Garg Code available at https://gitlab.mpi-sws.org/vahldiek/erim 35
Backup 36
Intel Memory Protection Keys (MPK) Tag memory pages with a memory domains (bits 62:59 in page table) Permission register (PKRU) enables R/W to a domain Update accessible permissions from userspace Fast switching, without context/PT switch By itself, protects against bugs only PKRU register (32 bit, 2 bits per domain) Page Table Entry 2 11 Domain (bits 62:59) 37
State of the art: Isolating State of the art: Isolating in in- -memory state memory state OS/VMM-Based ASLR-based Hiding Execution overhead Switch overhead Threat model Application Untrusted Trusted Sensitive data Application Application bugs only Any userspace Any userspace Any userspace ASLR1 Low None None OS/VMM -based2 Lang. & Operating System OS + VMM Low Low Medium Medium High Language and Runtime Techniques ERIM: Memory Isolation using Intel MPK None None RT3 ERIM Low None Low Application Sensitive data Application Sensitive data 1 ASLR-Guard, Near, XnR ERIM 2 LwC, SMVs, Shreds, Wedge, Nexen, Dune, SeCage, TrustVisor Operating System Operating System 3 MemSentry, SFI 38 38
Isolating sensitive state with Intel MPK Address Space Permission Register (PKRU) Sensitive State TRUSTED Domain 1 11 00 11 00 Domain 0 UNTRUSTED Untrusted Application State D0 D1 Domain switch is a user-mode register write: efficient but vulnerable to attack. 39
Using ERIM to isolate memory Inlined switches Function overwriting Function overloading via LD_PRELOAD fct_A( ) { . switch(Trusted) fct_A( ) { . } Shared library defines: fct_A( ) { f = dlsym(fct_A, ); switch(Trusted); ret = f(args); switch(Untrusted); return ret; } access sensitive data BUILD_BRIDGE(fct_A); switch(Untrusted) } fct_B( ) { CALL_BRIDGE(fct_A, args); } 40
How frequent are inadvertent WRPKRUs/XRSTORs? Debian 8 56035 Ubuntu 14 58548 Ubuntu 16 69907 Gentoo 9940 Gentoo Gold 9940 Elf files Elf files with WRPKRU/XRSTOR Executable WRPKRU/XRSTOR 665 603 720 73 34 4244 1147 2105 124 46 WPKRU/XRSTOR in code 481 276 384 41 31 Disassembled by Dyninst Inter-instruction Intra-instruction 420 30 390 215 29 186 332 44 288 32 5 27 24 5 19 44
How frequent are inadvertent WRPKRUs? Debian 8 56035 All 665 4244 481 420 30 30 390 199 191 Ubuntu 14 58548 All 603 1147 276 215 29 29 186 181 5 Ubuntu 16 69907 All 720 205 384 332 44 44 288 246 42 Gentoo 9940 All 73 124 41 32 5 5 27 27 0 Gentoo Gold 9940 All 34 46 31 24 5 5 19 19 0 Elf files WRPKRU XRSTOR 174 288 63 52 30 30 22 22 0 WRPKRU XRSTOR 215 442 66 55 29 29 26 26 0 WRPKRU XRSTOR 189 235 83 73 41 41 32 32 0 WRPKRU XRSTOR 22 26 9 9 5 5 4 4 0 WRPKRU XRSTOR 17 18 14 14 5 5 9 9 0 Elf files w/ WRPKRU/XRSTOR Executable WRPKRUXRSTOR WPKRU/XRSTOR in code Disassembled by Dyninst Inter-instruction 541 3956 418 368 0 0 368 177 194 435 705 210 160 0 0 160 155 5 580 1870 301 259 3 3 256 214 42 59 98 32 23 0 0 23 23 0 20 28 17 10 0 0 10 10 0 Number Rewritable by NOP Number Rewritable by rule 5 Rewritable by rule 4/6 Intra-instruction 45
ERIM Related Work Hardware-based Isolation: Trusted Execution Engines (TEE) [SGX, TrustZone] Reducing TCB of TEE [Flicker] Sandbox applications in TEE [Haven, Scone] Hypervisor/OS-based: Reference monitors [Dune, Wedge, LwC] Sandboxing Applications [Capsicum] Privilege Separation [PrivTrans] Hiding secrets in execute-only code [Redactor, Near] 46
ERIM Related Work Software-fault isolation: Compilation-based [NativeClient] Emulation [Vx32] Just-in-time compiled languages [NativeClient++] Inlined Reference Monitoring: Control-Flow Integrity [CPI] Sandboxing annotated code [Shreds] Intercepting Android framework [Aurasium] 47
Call Gates WRPKRU (RW_TRUSTED) Elevate privileges and transfer to trusted entry point // entry point to trusted WRPKRU (DIS_TRUSTED) cmp DIS_TRUSTED, EAX je continue exit continue: Remove privileges, check for reduced privileges and return from trusted component 48
Creating safe binaries Devise rewrite rules for WRPKRU in code segment Inter-instruction WRPKRU (0x0F01EF) Example rewrite rule: Instruction 1 Instruction 2 0F 01EF 0F Nop 01EF 49
Creating safe binaries Intra-instruction WRPKRU Simplified x86 instruction format: Prefix Opcode Mod R/M SIB Displacement Immediate Example rewrite rule: Opcode 0x01 Mod R/M 0x0F Displacement 0x01EF0000 add ecx, [ebx + 0x01EF0000] push eax; mov eax, ebx; add ecx, [eax + 0x01EF0000]; pop eax; Opcode 0x01 Mod R/M 0x07 Displacement 0x01EF0000 50