Cryptography and Authentication Course Information
Dive into the world of modern cryptography and authentication with this detailed course overview. Join Instructor Gorjan Alagic in exploring concepts, strategies, and applications of cryptography. Get assignment guidelines, access course materials, and engage with TAs for assistance. Equip yourself with the knowledge and skills needed for secure communication in today's digital age.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
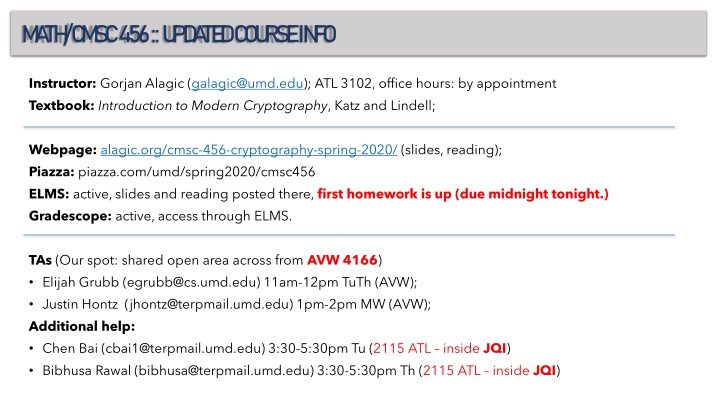
M A TH /C M SC 456 :: U PD A TE D C OU RSE IN FO Instructor: Gorjan Alagic (galagic@umd.edu); ATL 3102, office hours: by appointment Textbook: Introduction to Modern Cryptography, Katz and Lindell; Webpage: alagic.org/cmsc-456-cryptography-spring-2020/ (slides, reading); Piazza: piazza.com/umd/spring2020/cmsc456 ELMS: active, slides and reading posted there, first homework is up (due midnight tonight.) Gradescope: active, access through ELMS. TAs (Our spot: shared open area across from AVW 4166) Elijah Grubb (egrubb@cs.umd.edu) 11am-12pm TuTh (AVW); Justin Hontz (jhontz@terpmail.umd.edu) 1pm-2pm MW (AVW); Additional help: Chen Bai (cbai1@terpmail.umd.edu) 3:30-5:30pm Tu (2115 ATL inside JQI) Bibhusa Rawal (bibhusa@terpmail.umd.edu) 3:30-5:30pm Th (2115 ATL inside JQI)
H OM E W ORK RU L E S A N D G U ID E L IN E S : First homework is up (due midnight tonight.) Rules collaboration ok, solutions must be written up by yourself, in your own words; late homeworks will not be accepted (no exceptions, but lowest grade will be dropped.) Explanations and proofs correct answers with no explanation will get a zero score; explain your ideas clearly and completely; write in complete sentences, use correct and complete mathematical notation (as in lectures and book); proofs need to be rigorous, clear, and complete (consider all cases, prove counterexamples, etc.) Suggestions work on your own at least some of the time for each assignment work in 25+ minute chunks of uninterrupted, distraction-free, device-free time develop intuition: try lots of examples, ask yourself questions, play with the concepts
RE C A P : IS C R YPTO JU ST SE C RE C Y? Secrecy: protects against Eve learning our message. Eve What else could go wrong? Eve could interfere! Is this possible? The message is encrypted! Alice Bob Consider OTP: Eve observes a ciphertext ? = ????? = ? ?; She flips some bits: ? ? ?; Bob decrypts: ????? ? = ? ? ? = ? ? ? = ? ?. Eve s attack was directly applied to the message! If ? was a bank deposit, Eve could flip the bits that add thousands (or millions) to the amount!
RE C A P : W H A T A B OU T F A N C IE R E N C RYPTION ? What about PRG and PRF encryption? Eve Both based on OTP! So same attacks work! Alice Bob For example, interference against PRF scheme: Eve observes a ciphertext ?,? ????? = (?,? ?k? ); She flips some bits: ?,? (?,? ?); Bob decrypts: ?????,? ? = ? ? ??? = ? ?. Eve s attack was directly applied to the message! All the extra secrecy protection of the PRF scheme did not help at all!
V . A U TH E N TIC A TION Reading: (p.107-126, 142-145)
RE C A P : A U TH E N TIC A TION We now change tasks: forget secrecy for the moment! and instead consider authenticity. (we will talk about combining them later.) The task: Alice wants to send a message to Bob; Bob s goal: make sure message is really from Alice and nobody else! Eve Alice Bob Assumptions: Alice and Bob can share a secret in advance (and have private spaces); Alice can send only one transmission (for now); Eve can change (or replace) the transmission however she likes! ( but we don t care if she can learn the message.)
RE C A P : M E SS A G E A U TH E N TIC A TION C OD E S Message authentication code (MAC): generate key: generate tag: verify (message, tag) pair: ? ?????,? [ ? = 1 (valid) or ? = 0 (invalid) ] Correctness: ?????,????? ? ?????? ? ????? = 1. ? ?????? Eve Alice Bob ? ? Pick message ?. Set ? = ????? Compute ? = ?????,? ? = 1 : YES message was from Alice! ? = 0 : NO it was tampered with! (?,?)
RE C A P : U N FORG E A B IL ITY How to define security for MACs? Unforgeability. Let s use a game: MacForge ,? , where is a MAC and ? the security parameter. 1. A key is sampled: ? ??????(1n) ; 2. Adversary ? is given oracle access to ????; 3. ?outputs a pair (?,?); set ? = ?????,? ; ???? (?,?) ? ? ???? We say ? wins the experiment if: ? = 1 (valid), and ? is not in the set of queries ?made to the oracle. Definition. A message authentication code is existentially unforgeable under chosen message attack (EUF-CMA) if, for every PPT adversary ?, Pr ? wins MacForge ,? negl ? .
RE C A P : C ON STRU C TIN G SE C U RE M A C s Definition. A keyed function family ?:? ? ? is pairwise independent if, for every ? ? in ? and all ?,? in ?, we have 1 ?2 ? ???? = ? ??? = ? = Pr Construction (Carter-Wegman). Let ?:? ? ? be a pairwise-independent function family. Define a MAC (with canonical verification) as follows: ??????: output uniformly random ? ?; ???: on input a key ? and message ? ?, output tag ??(?). Theorem. The Carter-Wegman MAC with a pairwise-independent function is 1-EUF-CMA againstarbitrary adversaries. Proof idea. the first pair (?,?)is the adversary s query; the second pair (? ,? )is the adversary s claimed forgery; now apply definition of pairwise independent.
RE C A P : C ON STRU C TIN G SE C U RE M A C s Pairwise-independent functions: random lines in ?. Input and output spaces: ?= {0,1,2, ,? 1} for a prime?. Key space: ? ?. All arithmetic will be modulo ?. Recall: since ? is a prime, we have multiplicative inverses (and can easily compute them.) ? ,? ? ?,? ? For any pair ?,? ? ?, define ??,?? ? ? + ? Can extend this idea take random polynomials over ?; keys get a bit bigger, but now you need degree-many points to learn the function; get info-theoretic ?-time MACs for any fixed ?. ? ,? ? What about arbitrary-many queries? ?,? ?
RE C A P : PRF M A C Construction (PRF MAC). Let ?: 0,1? 0,1? 0,1 be a PRF. Define a MAC (with canonical verification) as follows: ??????: output uniformly random ? 0,1?; ???: on input a key ? and message ? 0,1?, output tag ??(?). Notes. messages are of fixed length; tags are of length ? ;we can pick this however we want (by selecting the right PRF) but careful: recall trivial tag-guessing attack, which succeeds with probability 2 ?. Proof. similar to IND-CPA proof: 1. show that a scheme with a perfectly random function is statistically unforgeable; 2. then show that a forger for the PRF MAC would imply a distinguisher for the PRF.
PRF M A C SE C U RITY Construction (PRF MAC). Let ?: 0,1? 0,1? 0,1 be a PRF. Define a MAC (with canonical verification) as follows: ??????: output uniformly random ? 0,1?; ???: on input a key ? and message ? 0,1?, output tag ??(?). Theorem. The PRF MAC is EUF-CMA (against PPT adversaries.) Proof. suppose we use a completely random function ? in place of ??; recall: the candidate forgery message ? has to be fresh; this means: ?(?) has yet to be queried; it follows that ? = ?(?) is uniformly random; ???? (?,? ) so ? loses against random scheme: Pr ? = ? = 2 ?. Now suppose ?wins against pseudorandom scheme then we build a distinguisher for ? a contradiction! ? ? ????
PRF M A C SE C U RITY ? Construction (PRF MAC). Let ?: 0,1? 0,1? 0,1 be a PRF. Define a MAC (with canonical verification) as follows: ??????: output uniformly random ? 0,1?; ???: on input a key ? and message ? 0,1?, output tag ??(?). ??? Theorem. The PRF MAC is EUF-CMA (against PPT adversaries.) (?,? ) Proof (continued.) How to build the distinguisher? Simulate EUF-CMA! ? ? ? ??? keep a list ? = {?1,?2, } of all queries made; when ? outputs (?,? ), check that it verifies, and that ? ?. Two cases: 1. ?sampled as a random function; (and ?loses, by last slide.) 2. ? sampled as ?? for random ?; (and ?wins, by assumption.) Result: a distinguisher between case 1 and case 2. If checks pass (i.e., ? won) output 1. Otherwise output 0.
PR A C TIC A L M A C s In practice one-time (or ?-time) MACs are not used much, except as building blocks; and the PRF MAC is too inefficient; in general, PRFs for arbitrary input/output lengths are quite inefficient; Block ciphers! are typically much more practical; these are PRFs with the same input and output length; [ another nice property we won t need for now: they are invertible! ] One of the most common MACs on the Internet is the CBC-MAC, which uses block ciphers; the CBC stands for cipher block chaining ; let s see how it works.
C B C -M A C Construction (CBC-MAC). Let ?: 0,1? 0,1? 0,1?be a PRF, and (?) any polynomial. Define a deterministic MAC as follows: ??????: output uniformly random ? 0,1?; ???: on input a key ? and message ? 0,1 ? ? , do: split ? up: ? = (?1,?2,?3, ,? ) into chunks of length ?; set ?0 0? and ?? ??(?? 1 ??) for 0 < ? . output ? . In pictures: ? = (?1,?2,?3, ,? ) ?1 ?2 ? ?3 . . . ?? ?? ?? ?? ?
C B C -M A C CBC-MAC is secure for fixed-length messages (see book.) What does this mean? at key generation time, everyone needs to agree on a fixed length; for CBC-MAC, this amounts to selecting the function ? ; after that point, all messages to be authenticated must be of length ? ?; any deviation might result in an attack! What happens if we use it to authenticate a message of different length anyway? ?1 ? ?2 ?3 . . . ?? ?? ?? ?? ?
C B C -M A C attacks do indeed become possible. CBC-MAC is not secure for variable-length messages. The trouble: there s nothing special about the start or the end of these chains; this introduces vulnerabilities. The so-called Encrypted-CBC-MAC fixes this: key generation now samples two keys ?,? for the PRF; the chain is capped with an application of ?? . ?1 ?2 ?3 ? . . . ?? ?? ?? ?? ?? ? ?
E N C RYPTE D -C B C -M A C Theorem. The Encrypted-CBC-MAC is EUF-CMA for arbitrary-length messages. Proof is somewhat involved (but mostly a matter of complicated bookkeeping.) ok, so now we can authenticate variable-length messages in a fairly efficient way; is CBC-MAC the only way? Could there be something even more efficient? maybe first, as a general matter: why should we care? In general, having multiple ways to achieve the same crypto goal is helpful! different efficiency tradeoffs; different computational assumptions; could lead to new ideas! Different approach: use hash functions.
MD5 1992 H A SH FU N C TION S What are hash functions? A hash function is just a function which compresses its input: : 0,1? 0,1 for < ?. SHA3 2015 In practice: is implementable with a very fast algorithm; this algorithm is completely public; is a fixed constant (e.g., 128) while ? might be arbitrary; How do you design them? a bit like PRGs: part art, part science; analysis is difficult.
H A SH FU N C TION S ? ? What are they good for? They compress their input: : 0,1? 0,1 for < ?. So obviously, some ? 0,1 have a lot of preimages: at least 2? . ? But, for a well-designed hash function: seems to be 1-to-1; typically hard to find two inputs ?,? with the same digest (?); typically also hard: given a digest ?, find an input ? such that ? = ?. This is why they are used, e.g., in git: files are not compared directly; instead, a hash (digest) of each file is stored, and the hashes are compared; this allows for all sorts of integrity checks without a massive computational overhead. They re also used, e.g., in blockchains (e.g., in Bitcoin) for similar reasons.
H A SH FU N C TION S This should remind you of something: authentication! if comparing files (messages) is basically equivalent to comparing their hash digests why not just MAC the digest? Huge efficiency gain! this actually works, and is called Hash-and-MAC. Actually, hash functions are even crazier For a well-designed hash function : seems to be indistinguishable from a random function! and the only interesting thing we know to do with them is just evaluate them! (Think back to our discussion on oracles!) But let s slow down. This is all very informal so far.
H A SH FU N C TION S , FORM A L L Y We will think about keyed hash functions. Definition. A hash function is a polynomial-time computable function family : 0,1? 0,1 0,1 equipped with a PPT algorithm ?????? which, on input 1?, outputs a key ? 0,1?. We write ?? (?,?). How to use it? Typically: 1. Sample ? ??????(1?); 2. Make ? public to everyone; 3. Now anyone can evaluate ? on any string ? and get the hash digest ?? . Why? In practice, anyone can look up hash function spec
C OL L ISION -RE SISTA N C E What security properties do we want? There are many. An important one: collision-resistance. as we saw, every hash function is necessarily many-to-one; but in a good hash function, it should be hard to find inputs with the same digest. ? ? ? If this sounds impossible: Think about a random function ?: 0,12? 0,1? it s true that each ? 0,1? has (roughly) 2? preimages; let ??= ? 0,12? ? ? = ? be the set of preimages of ?; Note: ?? is a random subset of size 2? in a set of size 22?; In other words: for any ?, Pr ?[? ??] 2 ?. So, there are indeed functions for which it s hard to find preimages and collisions. (Actually, in a certain sense, most functions have this property.)
C OL L ISION -RE SISTA N C E How to define? As usual: with a game! ? ? Let = The game HashColl ,? proceeds as follows: 1. Generate key: ? ??????; 2. ?receives ? and outputs ?,? 0,1 ; ??????, be a hash function, and ?an algorithm. ? We say ?wins if ?? = ?(? ) and ? ? . ??????, is collision-resistant if, for every PPT adversary ?, Definition. A hash function = Pr ? wins HashColl ,? negl ? .
W E A K E R PROPE RTIE S We could ask for weaker properties. target-collision resistance adversary has a harder task: given a fixed ?, ? must find ? ? such that ?? = ?? . clearly implied by collision-resistance. preimage resistance slightly different, but still harder task: given a random ?, find ? such that ?? = ?. implied by collision-resistance: if you can find preimages: (i.) pick a random ?; (ii.) run preimage-finding on ? ?? ; check: with good probability over ?, preimage-finding will yield ? such that ? ?.
W E A K E R PROPE RTIE S By the way: preimage resistance is something like a one-way property: 1. Easy to evaluate; 2. Hard to invert on random inputs. such one-way functions are very important in the foundations of crypto; we will (probably) define them formally later in the course; you can build PRGs out of them, so by extension almost everything we ve seen so far; and some cool things we haven t! (next lecture) But back to collision-resistance
H A SH -and-M A C What is collision resistance good for? Authentication! Construction (Hash-and-MAC). Let = (??????,???) be a fixed-length message authentication code (MAC), and H= ??????H, be a hash function. Define an arbitrary-length deterministic MAC = (?????? ,??? ) as follows: (key generation) ?????? : on input 1?, outputs ? ?????? 1n,??????H1? (tag generation) ??? : on key (?,?) and message ?, outputs ? ????( ?? ). . In pictures: ? ? ? ???? ? 0,1 ? 0,1 ?
H A SH -and-M A C Construction (Hash-and-MAC). Let = (??????,???) be a fixed-length message authentication code (MAC), and H= ??????H, be a hash function. Define an arbitrary-length deterministic MAC = (?????? ,??? ) as follows: (key generation) ?????? : on input 1?, outputs ? ?????? 1n,??????H1? (tag generation) ??? : on key (?,?) and message ?, outputs ? ????( ?? ). . Theorem. If is an EUF-CMA fixed-length MAC, and H is a collision-resistant hash function, then the Hash-and-MAC construction is an EUF-CMA arbitrary-length MAC. Proof idea: If adversary forges on message ? then either/or: 1. ? is mapped to same ? as some queried ?: collision! 2. ? is not mapped to same as any other: forgery on ! ? ? ???? ? ? ? ? ? ? ???? ?
H A SH -and-M A C ? ? Proof idea: If forgery on ? then either/or: 1. ? is mapped to same ? as some queried ?: collision! 2. ? is not mapped to same as any other: forgery on ! ???? ? ? ? ? ? ? ???? ? Recall EUF-CMA and MacForge experiment. let ? be the set of queries made by ?, and (? ,? ) its output; let ?be the green event: ? ? such that ?? = ?(? ); ???? ? (? ,? ) Calculate: Pr[? wins MacForge ] = = Pr ? wins MacForge ? + Pr ? wins MacForge ? Pr ? + Pr ? wins MacForge ? . ???(?,?) ? ? We will show that both of these terms are negligible. How?
H A SH -and-M A C ? ? Proof idea: If forgery on ? then either/or: 1. ? is mapped to same ? as some queried ?: collision! 2. ? is not mapped to same as any other: forgery on ! ???? ? ? ? ? ? ? ???? ? Controlling probability of ?: ?is the green event: ? ? such that ?? = ?(? ); want to show: Pr ? negl ? . how? Well, suppose it s not, and consider this algorithm: ???? ? (? ,? ) ???(?,?) ? ? 1. 2. 3. Receive hash key ? as input. Sample ???key ?; Run ?with oracle ???? ?; Output ? and a random ? ?. Check: the probability that this algorithm finds a collision in ? is at least Pr ? / ? .
H A SH -and-M A C ? ? Proof idea: If forgery on ? then either/or: 1. ? is mapped to same ? as some queried ?: collision! 2. ? is not mapped to same as any other: forgery on ! ???? ? ? ? ? ? ? ???? ? What s left: Control Pr ? wins MacForge ? . what is this quantity? probability that ?wins the forgery game and for all queried ?, ?? ?(? ). ???? ? (? ,? ) ???(?,?) ? ? Stated a bit differently: probability that ?wins the forgery game and for all inputs ? to ????oracle, ? ? ?(? ). Point: in this case, we should be able to win a MacForge game against !
H A SH -and-M A C ? ? Proof idea: If forgery on ? then either/or: 1. ? is mapped to same ? as some queried ?: collision! 2. ? is not mapped to same as any other: forgery on ! ???? ? ? ? ? ? ? ???? ? What s left: Control Pr ? wins MacForge ? .If it s large then we should be able to win a MacForge game against ! Here s how: 1. Receive ???? oracle. Sample hash key ?; 2. When queried with ? 0,1 i. Hash it: ? ?(m); ii. MAC it (using oracle): ? ????z ; return ?. 3. When ?outputs ? , output ?? . Check: probability this wins MacForge versus is exactly Pr ? wins MacForge ? . ???? ? (? ,? ) ???(?,?) ? ?
H A SH -and-M A C ? ? Proof idea: If forgery on ? then either/or: 1. ? is mapped to same ? as some queried ?: collision! 2. ? is not mapped to same as any other: forgery on ! ???? ? ? ? ? ? ? ???? ? Recall EUF-CMA and MacForge experiment. let ? be the set of queries made by ?, and (? ,? ) its output; let ?be the green event: ? ? such that ?? = ?(? ); ???? ? (? ,? ) Calculate: Pr[? wins MacForge ] = = Pr ? wins MacForge ? + Pr ? wins MacForge ? Pr ? + Pr ? wins MacForge ? negl ? + negl ? negl ? . ???(?,?) ? ?