Recent public health emergency trends in Africa
The recent public health emergency trends in Africa, as highlighted by Ayesha Kadir from Save the Children, reveal concerning issues such as climate change exacerbating crises, collective violence affecting communities, and millions of children dying annually from preventable causes. The Greater Hor
0 views • 11 slides
DOWNLOAD/PDF The Pregnancy Test (Erie-sistible Stories - Romances set in Erie P
13 minutes ago - COPY LINK TO DOWNLOAD = http:\/\/cupangbalapmope.blogspot.com\/?cread=B0CTDFYHPY | Read ebook [PDF] The Pregnancy Test (Erie-sistible Stories - Romances set in Erie PA Book 2) | Aleksandr Ivanov was my person. We helped each other through the worst of our childhoods. I thought we
0 views • 4 slides
Overview of Distributed Systems: Characteristics, Classification, Computation, Communication, and Fault Models
Characterizing Distributed Systems: Multiple autonomous computers with CPUs, memory, storage, and I/O paths, interconnected geographically, shared state, global invariants. Classifying Distributed Systems: Based on synchrony, communication medium, fault models like crash and Byzantine failures. Comp
10 views • 126 slides
Normal Conditions of Use for New Propulsion Technologies in Vehicles
Explore the concept of normal conditions of use for vehicles with new propulsion/charging technologies. Learn how to assess and define normal conditions, operating modes, worst case scenarios, and overview of current technologies. Discover the approach to measure normal conditions and testing requir
2 views • 8 slides
Heart Treatment in India
Treatment for the heart focuses on reducing excess fluid volume and edema and boosting the heart's pumping ability. The immediate goals include preventing progressive failure or in the worst case, sudden death. The aggressiveness in therapy is proportionate to levels of heart failure. As a common po
0 views • 2 slides
TSA Security Guidelines and Risk Reduction Strategies
Explore the legal requirements for security coordination, assessments, and training as mandated by TSA. Discover what services and resources TSA offers, learn how to protect your company through risk assessment, planning, and training, and understand risk reduction strategies using the risk formula.
1 views • 19 slides
COVID-19 Overview: Guam Department of Public Health
COVID-19, caused by the SARS-CoV-2 virus, is a rapidly evolving situation. Information and guidance provided may be outdated. Coronaviruses can spread between animals and humans. Planning considerations for Guam include the likelihood of spread, high-risk populations, healthcare facility risks, PPE
0 views • 5 slides
Effective Software Project Planning for Strategic Decision-Making
Software project planning involves making key decisions under limited resources throughout the project lifecycle. Analyzing risks, uncertainties, and uncertainties allows for better decision-making, often through buying information like prototyping. Project estimation is a crucial initial step that
0 views • 47 slides
Amortized Analysis in Data Structures: Insights and Implementations
Amortized analysis plays a crucial role in understanding the average running time per operation in worst-case scenarios for data structures. This content delves into implementing lists using circular arrays with resizing strategies, lazy deletions in singly linked lists, and explores the costs assoc
1 views • 29 slides
Sorting Techniques in Data Structures
Sorting is the process of arranging elements in a specific order, be it ascending or descending, for efficient data access. This content covers internal and external sorting, types of sorting techniques like Bubble Sort and Quick Sort, factors influencing the selection of sorting techniques, efficie
7 views • 12 slides
Decidability and Tractability in CS21 Lecture
Explore the concepts of decidability and tractability in the CS21 lecture on January 24, 2024. The lecture covers topics such as converting context-free grammars into Chomsky Normal Form, algorithms for determining language generation, worst-case running times, dynamic programming strategies, and de
3 views • 31 slides
Safety Initiatives and Regulations in Offshore Energy Management
Discussions and updates from BOEMRE regarding new safety rules, reorganization efforts, and revised information requirements for oil spill responses in offshore energy management. Emphasis on blowout scenarios, worst-case discharge considerations, and compliance measures to enhance safety and preven
0 views • 35 slides
Additive Combinatorics Approach to Log-Rank Conjecture in Communication Complexity
This research explores an additive combinatorics approach to the log-rank conjecture in communication complexity, addressing the maximum total bits sent on worst-case inputs and known bounds. It discusses the Polynomial Freiman-Ruzsa Conjecture and Approximate Duality, highlighting technical contrib
0 views • 9 slides
Linear Search: A Detailed Guide
Linear search is a fundamental algorithm for finding a value in an array. This guide covers the concept, code implementation, examples, time complexity analysis, and comparison with binary search. Explore how linear search works, its best and worst-case scenarios, and why search time matters in prog
0 views • 34 slides
How to Minimize Damage with Early Slab Leak Detection in San Diego Commercial Buildings
San Diego is known for being a busy city and a common trouble that may happen within commercial premises are slab leaks which is one of the worst destructives. It\u2019s in a case of leakage from pipes found beneath concrete floors. Contact us now. \
0 views • 5 slides
Impact of Board Thickness Deviations on Wire Displacement
In this study by Lee Greenler at UW Physical Sciences Lab, the effect of side and foot board thickness deviations on wire position was analyzed. The displacement of the wire was found to vary based on the cosine factor, with potential displacements up to ~0.5mm near the pin. Different cases were con
0 views • 5 slides
Introduction to QuickSort Algorithm
Explore the QuickSort algorithm with details on the worst-case time complexity, partitioning process, recursive method, and example scenarios. Understand how QuickSort efficiently sorts arrays by choosing a pivot, comparing elements, and recursively partitioning the array until sorted. Dive into the
0 views • 19 slides
Signatures, Commitments, and Zero-Knowledge in Lattice Problems
Explore the intricacies of lattice problems such as Learning With Errors (LWE) and Short Integer Solution (SIS), and their relation to the Knapsack Problem. Delve into the hardness of these problems and their applications in building secure cryptographic schemes based on polynomial rings and lattice
2 views • 44 slides
Balanced Search Trees and Red-Black Trees
Balanced Search Trees ensure efficient data retrieval by maintaining balancedness properties within the tree structure. Red-Black Trees are a type of binary search tree with specific coloring rules that help in balancing and efficient searching. Learn about the structure, properties, and worst-case
1 views • 75 slides
Big-Oh Notation in Time Complexity Analysis
Big-Oh notation in algorithm analysis signifies how the runtime of an algorithm grows in relation to the input size. It abstractly characterizes the worst-case time complexity, disregarding constants and lower-order terms. The concept of Big-Oh, along with Big-Omega and Big-Theta, helps in comparing
0 views • 18 slides
Data-Parallel Finite-State Machines: A Breakthrough Approach
This research discusses a new method for breaking data dependencies in data-parallel finite-state machines. It highlights the importance of FSMs in various algorithms and the need for parallel versions in processing large data sets. The study explores breaking data dependences with enumeration and t
0 views • 19 slides
Overview of Sorting Algorithms and Quadratic Sorting - CS 330 Lecture Notes
Sorting algorithms play a crucial role in computer science and computing tasks, consuming a significant portion of computing power. Various algorithms such as Bubble Sort, Selection Sort, and Insertion Sort are discussed for sorting a list of values efficiently. Quadratic sorting algorithms like Sel
0 views • 30 slides
Program Verification Using Templates Over Predicate Abstraction
This research explores a technique that allows for inferring invariants with arbitrary quantification and boolean structure, improving the state-of-the-art in program verification. It can infer weakest preconditions, helping with debugging and analysis by discovering worst-case inputs and missing pr
0 views • 32 slides
VMware High Availability Deep Dive Concepts
Dive into the world of VMware High Availability with in-depth modules covering admission control policies, slot sizing, advanced settings, and failover capacity. Learn about cluster tolerance, slot reservations, resource fragmentation, and worst-case scenarios to optimize your virtual environment fo
0 views • 32 slides
Latency Measurement in IEEE 802.11 for Low Latency Applications
IEEE 802.11-20/0484r0 discusses the importance of latency measurement for low latency applications in WLAN technologies. The document emphasizes the need for improved worst-case latency and jitter, addressing interference issues to ensure guaranteed latency for scheduled transmissions. Various contr
0 views • 13 slides
Trial Process in Court
Learn about the various stages of a trial, from pre-trial hearings to jury deliberations, including the roles of judges, attorneys, and witnesses. Explore concepts such as evidence presentation, impeachment, courtroom placement, scripted mock trials, and debriefing sessions. Dive into the difference
0 views • 7 slides
Importance of Security in Web Development
Our perception of security has evolved to acknowledge the presence of malicious actors and potential vulnerabilities in web applications. To write secure code, developers must assume the worst-case scenario and adopt a security mindset that trusts no one. Attackers have various goals, such as steali
0 views • 18 slides
Measurement-based WCET Analysis for Multi-core Architectures
This research focuses on providing an inexpensive multi-core solution for safety-critical systems by utilizing unmodified production chips and measurement-based WCET analysis tools. The goal is to enable WCET analysis on multi-core setups while preserving cost, performance, and time-to-market benefi
0 views • 25 slides
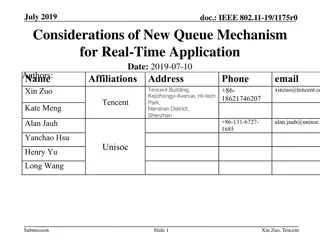
New Queue Mechanism for Real-Time Application Considerations in July 2019
In July 2019, considerations were made for a new queue mechanism for real-time applications. The focus was on improving worst-case latency and jitter for latency-critical traffic, such as in online mobile gaming and manufacturing control. The proposed design aims to link access delay directly to req
0 views • 9 slides
Comprehensive Guide to Election Day Registration Process
This content covers essential aspects of Election Day Registration (EDR) for the ROVAC 2020 event. It includes topics such as the basics of EDR, ID requirements, staffing considerations, handling worst-case scenarios, public awareness strategies, and preparation for COVID-19 challenges. The guide em
0 views • 11 slides
Dystopian Societies and Controls
Dystopian societies, like Union Grove High School, exaggerate worst-case scenarios to criticize current trends or systems. Characteristics include propaganda, restricted freedom, and banished natural world. Types of control include corporate, bureaucratic, technological, philosophical, or religious.
0 views • 11 slides
Dystopian Worlds in Literature
Marrow Thieves presents a dystopian universe where societal control is oppressive. Dystopias criticize current trends by exaggerating worst-case scenarios. Characteristics include propaganda, limited freedom, and dehumanization. Types of control range from corporate to technological. Dystopian prota
0 views • 15 slides
Workplace Violence Prevention Training & Discrimination in the Workplace
Workplace violence prevention training is crucial to ensure safety in the workplace. This training covers the definition of workplace violence, types of violence, actions that must be reported, and worst-case scenarios. It emphasizes avoiding disruptive behaviors like verbal abuse and outlines incid
0 views • 23 slides
Approximate Computing in Hardware Design: A Comprehensive Overview
Explore the groundbreaking concepts of approximate computing in hardware design, which involves embracing errors to enhance resource efficiency and performance. Delve into topics such as avoiding worst-case design, criteria for approximate HDL, safety in hardware, and relaxing accuracy requirements
0 views • 31 slides
ConnectWise Incident Response Service: Expert Help for Security Incidents
ConnectWise Incident Response Service offers expert assistance 24/7 for handling worst-case security incidents. Gain direct access to incident response analysts, real-time management, recovery procedures, insights on attacker tactics, and post-incident monitoring. Choose from flexible service option
0 views • 13 slides
Simons Workshop on Learning and Algorithm Design: Beyond Worst-Case Analysis
Simons Workshop on Learning, Algorithm Design, and Beyond Worst-Case Analysis in 2016 featured top organizers and discussed algorithm analysis, instance structures, worst-case scenarios, average-case analysis, and more. The workshop included social events and informative talks.
0 views • 31 slides
AVL Trees: Balanced Search Trees for Efficient Operations
AVL Trees are balanced search trees that ensure efficient insertion, deletion, and retrieval operations with a worst-case time complexity of O(log N). Named after their inventors Adelson-Velskii and Landis, AVL Trees maintain balance by limiting the height difference between left and right subtrees
0 views • 28 slides
Algorithm Analysis: Understanding Efficient Problem Solving
Algorithm analysis is a methodology used to predict the computational resources an algorithm requires, focusing on computational time rather than memory. It involves assessing the efficiency of different algorithms in solving a single problem. The analysis covers functions like Constant, Logarithm,
0 views • 34 slides
Analysis of Algorithms
Explore the world of algorithms through the lens of analysis. Learn the criteria for evaluating algorithms, understanding running time and memory space, and conducting experimental studies. Delve into limitations of experiments, algorithms and inputs, average case vs. worst case analysis, and the be
0 views • 29 slides
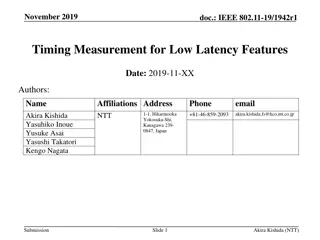
IEEE 802.11-19/1942r1 Timing Measurement for Low Latency Features
The document discusses the necessity of measuring latency and jitter for IEEE 802.11be low-latency functions. It emphasizes the importance of precise measurement methods to evaluate quality and control low-latency features effectively. The presentation highlights the need for timing measurement to r
0 views • 13 slides