Campus Mail Services Package Shipping Tutorial
This tutorial guides you through the process of creating your ship request, validating return addresses, entering recipient addresses, verifying recipient addresses, providing package information, selecting a carrier, entering your cost account number, printing the ship request form, and attaching i
4 views • 8 slides
Understanding TCP/IP Networking Tools in Linux Administration
The iproute2 software suite in Linux provides utilities for network control and monitoring, replacing legacy tools like ifconfig, netstat, route, and arp. This lesson delves into displaying information about network interfaces, network addresses (IP addresses), routing tables, assigned DNS servers,
2 views • 22 slides
Implementing Address Spaces: Base + Limit Registers
Address spaces, base + limit registers, and contiguous allocation are essential concepts in operating systems. Real mode memory addresses lack isolation between processes and pose limitations on multitasking. Virtual memory introduces virtual address spaces, requiring translation to physical address
3 views • 11 slides
Amateur Radio Licensing Regulations and Call Signs in the UK
Learn about the licensing regulations, privileges, call sign formats, secondary identifiers, and addresses for amateur radio operators in the UK. Discover the differences between Foundation, Intermediate, and Full license classes, as well as the various call sign formats used in England. Explore the
0 views • 87 slides
Understanding Bluetooth Low Energy Addresses in IEEE 802.11-21/1535r0
The document explores the features of resolvable addresses in Bluetooth Low Energy (BLE) within the IEEE 802.11-21/1535r0 standard. It discusses the two types of addresses in BLE, Public and Random, and their usage. The emphasis is on Random addresses due to their popularity and privacy features. Th
2 views • 11 slides
Understanding Memory Virtualization in Operating Systems
Memory virtualization in operating systems involves mapping guest addresses to host addresses with an added level of indirection managed by the hypervisor. Virtualization extensions in x86 processors enhance efficiency by allowing safe execution of guest code in Ring 0 through supervisor mode. The a
1 views • 28 slides
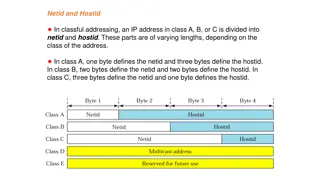
Understanding Netid and Hostid in Classful IP Addressing
In classful IP addressing, IP addresses in Class A, B, or C are divided into netid and hostid parts with varying lengths based on the class. Each class has a fixed number of blocks, causing issues with classful addressing. Network addresses play a crucial role, defining organization networks and fac
0 views • 14 slides
Understanding IPv4 Addresses and Classful Addressing in Computer Networks
Explore the basics of IPv4 addresses, address space, hierarchy in addressing, and classful addressing in computer networks. Learn about the unique 32-bit structure of IPv4 addresses, address space calculation, notation methods, and the hierarchical nature of network addressing. Dive into the concept
2 views • 14 slides
IEEE 802.11-20/0054r1 MLD MAC Address and WM Address
In the document IEEE 802.11-20/0054r1, the focus is on Multi-Link Framework for MLD address identification and differentiation. It explains the usage of MLD MAC address and STA WM medium address in wireless setups. The document also addresses the need for identifying different MLDs using MAC address
0 views • 16 slides
MAAP Protocol Overview in IEEE 1722: Address Acquisition and Message Format
The MAAP (Multicast Address Acquisition Protocol) is defined in IEEE 1722 for time-sensitive applications in bridged local area networks. It involves acquiring multicast addresses through claiming, probing, and defending messages. MAAP enables dynamic allocation of addresses and defending against co
1 views • 8 slides
Understanding Static Routing in Network Infrastructure Workshops
Explore the concepts of static routing in networking workshops, covering Unix and Cisco network interface configurations, static routes, default routes, and advantages and disadvantages of static routing. Learn about IP routing configuration, assignment of IPv4 addresses, and FreeBSD network interfa
4 views • 37 slides
Enhancing Privacy with Randomized MAC Addresses in 802.11 Networks
This presentation discusses the use of randomized MAC addresses as a privacy-enhancing measure in 802.11 networks. Passive observation of MAC addresses poses privacy risks, and the proposal suggests assigning random MAC addresses to portable devices to mitigate tracking risks. By periodically changi
0 views • 10 slides
Strategy for Migration of CE & ST Assessee to GSTN
This strategy outlines the process for migration of Central Excise (CE) and Service Tax (ST) assesses to the Goods and Services Tax Network (GSTN). It explains the issuance of provisional IDs, enrollment based on PAN and State, and the handling of multiple registrations under a single PAN. The proce
0 views • 48 slides
Discussion on Provisioning Servers Addressing Information in 3GPP TS 23.501
Background CT4 LS in S2-2200200 issue 2 discussed the interpretation and intention of the addressing information for Provisioning Servers (PVS) as stated in 3GPP TS 23.501. The focus was on whether the provided PVS IP addresses and/or FQDNs are for a single PVS server or multiple servers and how the
0 views • 4 slides
Understanding RARP and Transport Layer in Computer Networking
Exploring Reverse Address Resolution Protocol (RARP) for mapping physical addresses to logical addresses in networking, along with insights on the Transport Layer's role in providing communication services to application processes. Learn about RARP packet formats, encapsulation, and the significance
0 views • 41 slides
Privacy Issues in IEEE 802.11 Networks: Tracking and MAC Randomization
This presentation delves into the privacy concerns surrounding 802.11 networks, focusing on tracking vulnerabilities and the limitations of MAC randomization in preventing tracking. It discusses the ease of tracking devices, the risk of passive tracking due to MAC addresses being visible in frames,
0 views • 27 slides
Proposal for Establishing Epochs in IEEE 802.11-17/2059r1 Network
This proposal by Stephen Rodriguez from Cisco suggests partitioning time into epochs based on network trust levels to determine when clients should change their MAC addresses dynamically. The idea involves rotating MAC addresses at specified intervals depending on the trust level of the network conn
0 views • 5 slides
Understanding Pointers in Computing
Exploring the concept of pointers in computing, this content delves into the fundamentals of storing memory addresses, the size of variable types, managing memory, and utilizing pointers effectively. It discusses how pointers are used to store memory addresses and provides examples of pointer usage
0 views • 10 slides
IEEE 802.11-21/1585r10: Identifiable Random MAC Address Presentation Summary
This presentation discusses the concept of Identifiable Random MAC (IRM) addresses in the IEEE 802.11-21/1585r10 standard. It covers the purpose of IRM addresses in preventing third-party tracking while allowing trusted parties to identify specific devices. The presentation outlines the use of Ident
0 views • 24 slides
Addressing Privacy Concerns in IEEE 802.11-21: Changing MAC Addresses for Improved Security
The document discusses the implications of changing STA MAC addresses per association in IEEE 802.11-21 standard to enhance privacy and security. It explores the challenges of maintaining persistent identifiers in data frames and the risks associated with sending source/destination addresses in clea
0 views • 11 slides
Contact Information and Email Addresses
This content provides a list of contact information and email addresses for various individuals. It includes details such as email addresses, websites, and names. It emphasizes the importance of checking for updates in the school newsletter and emails. The information is presented in a structured fo
0 views • 22 slides
Understanding Address Translation in Computer Systems
Explore the concept of address translation in computer systems, covering topics such as converting virtual addresses to physical addresses, different translation methods, goals of address translation, bonus features, and a preview of MIPS address translation. Learn about the benefits and limitations
0 views • 60 slides
IEEE 802.1CQ: Address Assignment and Validation Protocols
This document explores the assignment and validation of unicast addresses within IEEE 802 networks, emphasizing the need for uniqueness to prevent operational errors and security breaches. It discusses the challenges of ensuring globally-unique addresses, proposing the implementation of a single val
0 views • 6 slides
Understanding Computer Networking: Broadcast and Multicast Protocols
In this lecture on computer networking, we explore the concepts of broadcast and multicast protocols. The discussion covers topics such as BGP routing, IPv4 anycast hack, IP multicast, and the role of broadcast in small-to-moderate sized ad hoc networks. Learn about the differences between unicast,
0 views • 20 slides
Understanding IPv4 Addressing and Classes
Explore the fundamentals of IPv4 addressing including subnetting, VLSM, summarization, subnet masks, CIDR values, available host addresses, and broadcast addresses. Learn about IPv4 classes A, B, C, and D, their formats, usage for different network sizes, netmask details, IP address ranges, and more
0 views • 38 slides
Enhancing Name and Address Parsing for Data Standardization
Explore the project focused on improving the quality of name and address parsing using active learning methods at the University of Arkansas. Learn about the importance of parsing, entity resolution, and the token pattern approach in standardizing and processing unstructured addresses. Discover the
0 views • 11 slides
Understanding IP Addressing in Computer Networks
IP addressing provides a seamless network for users by abstracting and providing a uniform addressing scheme used by higher-layer protocols and applications. IP addresses identify connections rather than specific computers, with IPv4 using 32-bit integers and IPv6 using 128-bit addresses. The divisi
0 views • 19 slides
Local MAC Address Assignment Protocol (LAAP) and 802.1CQ
The Local MAC Address Assignment Protocol (LAAP) in conjunction with 802.1CQ specifies protocols and procedures for locally unique assignment of MAC addresses in IEEE 802 networks. LAAP operates in two modes - Server Mode and Peer-to-Peer Mode, ensuring efficient allocation of MAC addresses while av
0 views • 15 slides
Understanding Virtualization: Hardware Abstraction and Hypervisor Concepts
Dive into the world of virtualization with a focus on hardware abstraction and hypervisor technology. Explore the definitions and examples of hardware virtualization, hypervisors, and hardware abstraction, shedding light on how they enable multiple operating systems to coexist on a single physical m
0 views • 21 slides
Evolved Addressing and Forwarding in Information-Centric Networks
The content discusses Evolved Addressing and Forwarding in Information-Centric Networks, focusing on an accountable Internet protocol (AIP) that addresses vulnerabilities at the IP level, such as source spoofing, DoS attacks, and route hijacking. AIP utilizes a hierarchy of self-certifying addresses
0 views • 16 slides
Understanding IPv6 ISP Performance: A Detailed Analysis by Geoff Huston
This comprehensive study explores the reliability and speed of IPv6 connections, highlighting factors affecting connection failures. It compares datasets from 2011 and 2015/2016, revealing insights on Teredo, 6to4, and unicast address failures. The findings underscore the importance of addressing is
0 views • 37 slides
Privacy Address Requirements for Wireless Personal Area Networks
This document discusses the privacy address requirements for IEEE P802.15 Working Group's TG4ab standard for Wireless Personal Area Networks (WPANs). It covers the need for 48-bit addresses with collision resistance, the use of different privacy addresses for each frame, and the adequacy of 12-bit c
0 views • 8 slides
IEEE 802.11-22/0955r0 TGbh Pre-association Schemes Exploration
The document explores the pre-association schemes NGID, MAAD, and IRM within the IEEE 802.11-22 standard. It discusses how the schemes operate, comparing RRCM to MAAD and IRM, and addresses the use of Probes and MAC addresses in pre-association scenarios. The presentation clarifies the allocation of
0 views • 15 slides
Understanding Network Security Part 2: Link Layer and ARP
Exploring the vulnerabilities in simple network topologies with hubs and the need for examining the link layer to prevent eavesdropping. Dive into MAC addresses, ARP (Address Resolution Protocol), and how machines translate IP addresses to physical Ethernet addresses. Learn about ARP tables, the tra
0 views • 61 slides
Understanding IP Addresses and Their Classification
IP Addresses, short for Internet Protocol addresses, are unique identifiers assigned to devices on a network. They can be IPv4 or IPv6, with IPv4 having 32 bits and IPv6 being 128 bits. IP addresses are classified into classes A, B, and C, each with specific range and usage. Understanding IP address
0 views • 14 slides
Understanding IP Addressing in Networking
IP addressing plays a crucial role in providing unique addresses to machines on the internet, identifying networks and hosts, enabling routing, and ensuring proper packet delivery across networks. This content covers the need for IP addresses, their role in routing, address parts, classful IP addres
0 views • 36 slides
County Election Administration Training Conference 2022 - IP Addresses & Account Management
This content provides information on IP addresses, account management, and multifactor authentication (MFA) for the County Election Administration Training Conference 2022. It covers topics such as staff introduction, requesting assistance, IP address management, ERS & SVRS account assistance, and t
0 views • 12 slides
Understanding Address Resolution Protocol (ARP) in Computer Networks
Address Resolution Protocol (ARP) is essential for translating IP addresses to MAC addresses in computer networks. ARP facilitates communication between devices on the same network by resolving addresses and enabling efficient data transmission. This protocol involves message exchanges, hardware bro
0 views • 20 slides
IPv6 Public Policy Considerations - Addressing the Global IP Address Shortage
In light of the global shortage of IPv4 addresses, there is a pressing need for a fair policy for the allocation of remaining addresses. The rapid growth of the Internet has further increased demand for IP addresses, with IPv4 expected to run out soon. The deployment of IPv6 has become a critical is
0 views • 23 slides
Understanding NAT and IPv6 in Computer Networking
This lecture covers Network Address Translation (NAT) and IPv6 basics in computer networking. It explains how NAT helps in connecting multiple devices to the internet with limited IPv4 addresses, the concept of public and private IP addresses, and the transition to IPv6 for addressing constraints. V
1 views • 31 slides