Conjunctive Searchable Symmetric Encryption From Hard Lattices
Discusses outsourcing storage and computing, encrypted data computing, and searchable symmetric encryption for data security in cloud environments. It touches on topics like data confidentiality, user revocation, and performance-oriented implementations.
2 views • 30 slides
AES Encryption in Computer Engineering
Advanced Encryption Standard (AES) is a powerful symmetric block cipher used in computer engineering for data encryption. Developed by NIST, AES supports key lengths of 128, 192, and 256 bits. The algorithm operates on a state array and consists of encryption phases like initial round, main rounds,
3 views • 8 slides
Columnar Transposition Cipher: Data Encryption Techniques at Mustansiriyah University Engineering College
Transposition ciphers, particularly the columnar transposition technique, are explored in the course "Data Encryption" at Mustansiriyah University Engineering College. The cipher involves rearranging message elements without changing their identities, making it crucial in modern block cipher designs
0 views • 4 slides
Key Management and Distribution Techniques in Cryptography
In the realm of cryptography, effective key management and distribution are crucial for secure data exchange. This involves methods such as symmetric key distribution using symmetric or asymmetric encryption, as well as the distribution of public keys. The process typically includes establishing uni
3 views • 27 slides
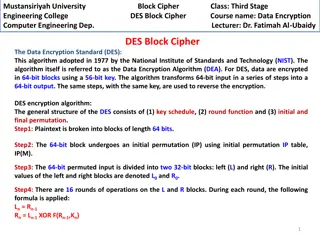
DES Block Cipher in Computer Engineering at Mustansiriyah University
Data Encryption Standard (DES) is a widely used algorithm for encrypting data in 64-bit blocks with a 56-bit key. This course at Mustansiriyah University covers the key components of DES, including the key schedule, round function, and initial/final permutation. Students learn about the encryption p
1 views • 8 slides
ADFGVX Cipher: Encryption and Decryption Techniques
Discover the ADFGVX cipher, a historical encryption method used to secure messages during World War I. Learn about Fritz Nebel and Gino Painvin, who played significant roles in its development. Explore the Polybius Square invented by Polybius in the 2nd century BC for converting letters to numbers.
0 views • 14 slides
Quantum Query Complexity Measures for Symmetric Functions
Explore the relationships between query complexity measures, including quantum query complexity, adversary bounds, and spectral sensitivity, in the context of symmetric functions. Analysis includes sensitivity graphs, the quantum query model, and approximate counting methods. Results cover spectral
0 views • 19 slides
Block Ciphers in Cryptography
Explore the principles of block ciphers in modern cryptography, focusing on the Data Encryption Standard (DES) and its design principles. Learn about block cipher encryption, Feistel block cipher structure, n-bit block ciphers, ideal block ciphers, key length considerations, and challenges with idea
1 views • 44 slides
Simplified Linear Transformation for N Application Rates in Corn and Wheat
Dr. Brenda Ortiz and Dr. Bill Raun led an investigation on predicting grain yield using optical sensors in corn and wheat. The challenges with the symmetric sigmoid model for yield prediction led to the development of a simplified linear transformation approach. Assumptions were made to create a mod
1 views • 28 slides
Hash Joins and Symmetric Hash Joins in Database Queries
Hash joins and symmetric hash joins are key techniques used in database queries to efficiently access and combine data from multiple tables. Hash joins load candidate records into hash tables for quick probing, while symmetric hash joins maintain two hash tables with two hash functions. Despite thei
1 views • 8 slides
Overview of Modern Cryptography and Data Encryption Standard (DES)
Exploring modern cryptography including symmetric key block ciphers, public key ciphers, stream ciphers, and post-quantum ciphers. Focus on Data Encryption Standard (DES), Simplified DES, Feistel cipher, key schedule, expansion function, S-Box, DES encryption, and decryption processes.
1 views • 37 slides
Cryptography Basics and Toolbox
Cryptography serves the goals of managing who can view data, ensuring data integrity, and verifying the origin of data. It involves dramatis personae like Alice, Bob, Eve, and Oscar. The toolbox includes hash functions, symmetric encryption, and asymmetric encryption. Hash functions play a crucial r
1 views • 32 slides
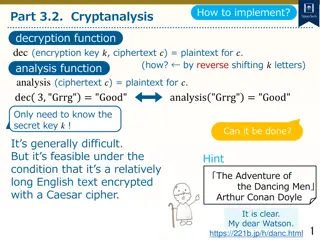
Cryptanalysis and Decryption Techniques for Caesar Cipher
Learn how to decrypt Caesar cipher text using cryptanalysis techniques by analyzing letter frequencies and determining the secret key through character analysis. Explore methods to count character frequencies and find the most common letter to decipher encrypted messages.
0 views • 11 slides
Symmetric Chains and Hamilton Cycles in Graph Theory
Delve into the study of symmetric chains, Hamilton cycles, and Boolean lattices in graph theory. Discover the relationships between chain decompositions, Boolean lattices, and edge-disjoint symmetric chain decompositions, exploring construction methods and properties such as orthogonality. Uncover t
0 views • 15 slides
Fun Spy Challenges for Beavers - Crack the Codes!
Dive into exciting spy missions with a group of clever beavers! Decode secret messages using various encryption techniques such as switching codes, letter grouping, Pig Pen cipher, Morse code, and Caesar cipher. Test your spy skills as you unravel each challenge to reveal hidden messages. Unleash yo
0 views • 6 slides
Fundamentals of Cryptography and Network Security
Explore the basics of cryptography, including classical encryption techniques, terminology definitions, types of encryption operations, cryptanalysis objectives and attacks, and the concept of cipher strength. Uncover the principles and methods behind encryption and decryption, key distinctions betw
0 views • 52 slides
Unlock the Challenges in Cipher Cove: A STEM Adventure
Explore Cipher Cove and tackle five cryptographic challenges involving different ciphers such as Caesar Shift, Pigpen, Transposition, Substitution, and Periodic Table. Put your problem-solving skills to the test by deciphering hidden clues and codes to progress through each challenge and ultimately
0 views • 6 slides
Competition Among Asymmetric Sellers with Fixed Supply - Research Overview
This research focuses on competition among sellers with fixed supply in markets for ads, where publishers determine slot allocations to advertisers based on given budgets. The study explores how publishers can maximize revenue by choosing allocation policies strategically, considering symmetric adve
0 views • 21 slides
Symmetric Encryption and Basic Terminology
This content covers symmetric encryption techniques, substitution and transposition methods, rotor machines, and basic cryptographic terminology such as plaintext, ciphertext, cipher, and key. It also discusses the requirements and assumptions for secure symmetric encryption, and the model of symmet
0 views • 49 slides
Classical Encryption Techniques Overview
Delve into the realm of classical encryption techniques with insights on symmetric encryption, basic terminology, symmetric cipher model, and requirements for secure encryption. Explore the foundations of cryptography, different encryption operations, and the central problem in symmetric cryptograph
0 views • 65 slides
Muddiest Point: Questions on RSA, DDoS Attacks, and Block Cipher Algorithms
In this collection of images, various concepts related to RSA encryption, DDoS attacks, block cipher algorithms like DES and AES, TCP protocols, and real-life applications of cryptography are explored. The images cover topics such as the Mirai-infected devices used in a DDoS attack on Dyn, differenc
0 views • 14 slides
Cryptography
Cryptography is the art of securing communication through the use of codes and ciphers. This overview covers fundamental concepts such as symmetric and asymmetric cryptography, hashes, attacks on cryptography, and best practices. Understand the terminologies in cryptography, the use of keys, and the
0 views • 63 slides
Cryptography: Modern Symmetric Ciphers
Explore the world of modern symmetric ciphers used in network security, from encryption basics to advanced techniques like Block vs. Stream Cipher and Autokeyed Vigenere Cipher. Understand the importance of encryption in providing protection for confidentiality, authentication, integrity, and non-re
0 views • 60 slides
Modern Cryptography: Algorithms and Their Applications
Cryptography involves securing and transmitting information through various techniques like encryption, decryption, and cipher text. It encompasses different security types, including communication security and transmission security. The history of cryptography systems is rich, spanning from letter
0 views • 26 slides
Cryptanalysis and Rail Fence Cipher Decryption Methods
In this discussion, we explored cryptanalysis techniques and the decryption process of the rail fence cipher. By mapping text to random letter permutations, breaking ciphers through histograms, and analyzing letter frequency distributions, we delved into deciphering encrypted messages. The session h
0 views • 27 slides
Modes of Operation in Block Cipher: Understanding ECB, CBC, CFB, and OFB
A block cipher encrypts fixed-length blocks of text with a key, and NIST has defined five modes of operation to enhance cryptographic algorithms. Explore ECB, CBC, CFB, and OFB modes in detail to understand their unique characteristics and applications.
0 views • 13 slides
Overview of Data Encryption Standard (DES)
Data Encryption Standard (DES) is a symmetric-key block cipher created in 1973 by NIST. It uses a 64-bit plaintext to generate a 64-bit ciphertext and vice versa. The same 56-bit cipher key is employed for encryption and decryption, utilizing rounds with S-box and P-box steps, ensuring confusion and
0 views • 29 slides
History of Cryptography: Techniques, Evolution, and Impact
Delve into the fascinating world of cryptography through the ages, from ancient substitution ciphers to modern cipher devices. Explore the birth of cryptanalysis, polyalphabetic substitution, black chambers, and the development of innovative cipher devices post-WWI. Uncover the pivotal role cryptogr
0 views • 10 slides
Randomized Half-Ideal Cipher on Groups: Applications to UC-PAKE Eurocrypt 2023
This paper introduces Half Ideal Cipher for group domains, a concept weaker than an Ideal Cipher, with applications in secure protocols such as UC-PAKE. It discusses the construction of HIC, its role in replacing IC in various protocols, and the significance of using Ideal Cipher on group domains.
0 views • 14 slides
Lightweight Cryptography: A New Cipher Choice for 802.11bn
Ascon, a lightweight cryptographic algorithm, is proposed as a new cipher choice for 802.11bn to enhance security and efficiency. NIST selected Ascon as the standard due to its authenticated encryption, minimal overhead, and energy efficiency on low-power devices. By comparing Ascon to AES-128 and S
0 views • 8 slides
Cryptography Evolution and Historical Cipher Systems
Explore the evolution of cryptography from Julius Caesar's Caesar Cipher to complex cryptographic systems used during the American Civil War. Understand the basics of symmetric key algorithms and the vulnerabilities of early ciphers. Dive into the significance of historical milestones in cryptograph
0 views • 58 slides
Cryptography Techniques: Caesar, Shift, and Affine Ciphers Explained
Explore classical cryptography methods including the Caesar cipher, shift cipher, and affine ciphers. Learn how these encryption techniques work and how to encrypt and decrypt messages using them.
0 views • 19 slides
Understanding Cryptography and Cipher Techniques
Dive into the world of cryptography with a focus on classic cipher techniques like the Caesar cipher and Vigenère cipher. Explore modern encryption algorithms such as AES and RSA, along with discussions on security concepts like cryptanalysis and cryptographic attacks. Discover how cryptography hel
0 views • 24 slides
Classical Encryption Techniques and Cryptography Overview
Explore classical encryption techniques, symmetric cipher models, conventional cryptosystems, and the fundamental concepts of cryptography and cryptanalysis. Learn about plaintext, ciphertext, secret keys, and decryption algorithms in this comprehensive guide.
0 views • 22 slides
Understanding the Shift Cipher Method for Cryptography
Dive into the world of cryptography with a focus on the Shift Cipher method, exploring encryption, decryption, the modulo operation, examples, and cryptanalysis techniques. Learn how to encrypt and decrypt messages using a shift in alphabets and understand the intricacies of breaking the cipher thro
0 views • 10 slides
RC4 Stream Cipher: Overview and Implementation at Mustansiriyah University
Explore the RC4 stream cipher, designed in 1987 by Ron Rivest, used in encryption protocols like WEP and WPA. Learn about the key initialization, permutation, and stream generation steps involved in RC4. Join the Data Encryption course at Mustansiriyah University to dive deeper into computer securit
0 views • 4 slides
Understanding Independent and Symmetric Channels in Information Theory
Explore the concepts of independent and symmetric transmission in information theory, including how they differ from noiseless channels. Learn about the properties of symmetric channels like Binary Symmetric Channels (BSC) and Ternary Symmetric Channels (TSC). Discover how to specify and model diffe
1 views • 5 slides
Exploring Parallel Caesar Cipher Implementation in RISC-V
Discover the uniqueness of RISC-V architecture through a tutorial on writing and testing a parallel Caesar cipher implementation. Learn about RISC-V, Caesar cipher, sequential and parallel implementations, vector extensions, and more. Engage in discussions and Q&A to enhance your understanding.
0 views • 22 slides
Understanding Cryptography: Basics to Galois Fields
Explore the fundamentals of cryptography, including binary conversion, file permissions, cipher types, symmetric vs. asymmetric encryption, and the significance of Galois Fields in AES algorithm. Gain insights into groups, rings, and fields, laying the foundation for a comprehensive understanding of
0 views • 39 slides
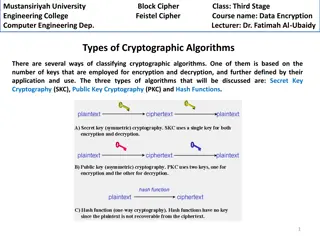
Understanding Cryptographic Algorithms Used in Data Encryption
Explore the classification of cryptographic algorithms based on key usage, including Secret Key Cryptography (SKC), Public Key Cryptography (PKC), and Hash Functions. Learn about Feistel Cipher, Block Cipher, and the structure of Feistel Cipher proposed by Feistel for creating block ciphers efficien
0 views • 6 slides