Rational Expectations and the Efficient Market Hypothesis
The importance of expectations in various sectors and markets of the economy, including asset demand, risk and term structure of interest rates, asymmetric information and financial structure, financial innovation, bank management, money supply process, Federal Reserve, foreign exchange market, dema
6 views • 51 slides
Public key encryption, Digital signature and authentication
Understand the concept of public key encryption, asymmetric encryption, and the widely used RSA algorithm. Explore how public key cryptography revolutionized the field of encryption and its applications in confidentiality, authentication, and key distribution.
4 views • 12 slides
Understanding Security Threats and Public-Key Cryptosystems
Explore the world of security threats, passive and active attacks, and the importance of asymmetric encryption through the terminology related to asymmetric encryption, public-key cryptosystems, and public-key cryptography. Learn about the key components of public-key encryption schemes and the proc
0 views • 46 slides
Key Management and Distribution Techniques in Cryptography
In the realm of cryptography, effective key management and distribution are crucial for secure data exchange. This involves methods such as symmetric key distribution using symmetric or asymmetric encryption, as well as the distribution of public keys. The process typically includes establishing uni
1 views • 27 slides
Understanding Computer System Architectures
Computer systems can be categorized into single-processor and multiprocessor systems. Single-processor systems have one main CPU but may also contain special-purpose processors. Multiprocessor systems have multiple processors that share resources, offering advantages like increased throughput, econo
2 views • 25 slides
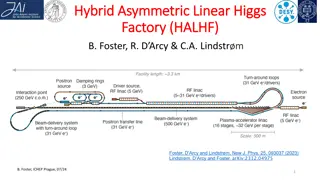
Innovative Hybrid Asymmetric Linear Higgs Factory (HALHF) Proposal
Cutting-edge proposal for the HALHF facility aiming to revolutionize particle acceleration technology by utilizing a hybrid asymmetric approach for electron-positron colliders. The design focuses on cost-efficiency and performance optimization, showcasing potential for significant advancements in hi
0 views • 18 slides
Overview of Cryptography Techniques and Algorithms
Exploring the diverse realm of cryptography, this chapter delves into both nonmathematical and mathematical encryption methods. It covers substitution and transposition ciphers, steganography, hybrid systems, hashing, symmetric algorithms like DES and AES, as well as asymmetric algorithms utilizing
7 views • 21 slides
Strong vocational interest blank
Strong Vocational Interest Blank, introduced in 1927 by Edward Kellog Strong Jr., assesses individuals' career preferences based on their likes and dislikes across various dimensions. The Strong-Campbell Interest Inventory, a revised version, includes 124 occupational scales and 23 Basic Interest Sc
0 views • 12 slides
Fundamentals of Asymmetric Catalysis: Energetics and Principles
Exploring the principles and energetics of asymmetric catalysis, this study delves into the importance, classes of transformations, stereoselectivity, and transmission of asymmetry. It discusses reaction coordination diagrams, transition state stabilization, and the terminology of catalysis. The Cur
2 views • 20 slides
Overview of Basic Security Properties and Cryptography Fundamentals
This content provides an introduction to basic security properties such as confidentiality, authenticity, integrity, availability, non-repudiation, and access control. It also covers the fundamentals of cryptography, including symmetric and asymmetric encryption, public-key cryptography, and the imp
1 views • 41 slides
Understanding Security Goals and Cryptographic Algorithms
Introduction to security goals such as privacy, data integrity, authentication, authorization, and availability, along with the usage of cryptographic algorithms like symmetric and asymmetric key algorithms, keyed hashing, and digital signatures for achieving different security objectives in communi
0 views • 13 slides
Start Strong Fall 2022 Administration District Test Coordinator Training
Delve into the comprehensive training agenda for the Start Strong Fall 2022 Administration, focusing on key aspects such as testing requirements, technology setup, reporting groups, accessibility features, and more. Understand the differences between Start Strong and NJSLA assessments, key dates, an
0 views • 58 slides
Cryptography Concepts and Encryption Methods Overview
Exploring elementary cryptography concepts such as encryption, cryptanalysis, symmetric and asymmetric encryption algorithms like DES, AES, and RSA. Delve into key exchange protocols, digital signatures, cryptographic hash functions, and the process of encryption and decryption in a cryptosystem.
0 views • 23 slides
Understanding Silicon Detector Technology
Silicon is a remarkable material with low energy requirements for creating e-hole pairs, long mean free paths, high mobility for fast charge collection, and well-developed technology for fine lithography. Silicon detectors operate based on carrier band diagrams, density of states, and Fermi-Dirac di
0 views • 21 slides
Understanding Public Key Cryptosystems in RSA Encryption
Public key cryptosystems, like RSA, use two keys for encryption and decryption, with one key made public and the other kept secret. This asymmetric system allows secure communication, where the encryption key (E) is used to encrypt messages into ciphertext (C), which can only be decrypted back to th
0 views • 11 slides
Key Distribution and Management in Cryptography
This presentation discusses key distribution and management in cryptography, covering symmetric and asymmetric key cryptography, methods for sharing symmetric and public keys, as well as key distribution techniques such as manual delivery, initial key distributions, and the use of trusted third part
0 views • 30 slides
Understanding the Role of Financial Institutions in the Global Economy
Explore the significance of financial institutions in facilitating the flow of funds from savers to productive investments, essential for a healthy economy. Delve into topics like transaction costs, asymmetric information, adverse selection, and moral hazard in the financial system, along with basic
0 views • 19 slides
The Physics of Supernovae and Neutron Stars
Explore the fascinating world of supernovae and neutron stars through historical postulations, Nobel Prize-worthy discoveries, multi-dimensional simulations, and paradigm shifts in understanding asymmetric supernovae. Dive into the complexities of core-collapse mechanisms, jet formations, and the po
0 views • 35 slides
Exploring Nuclear Symmetry Energy with QCD Sum Rule
This study delves into the concept of nuclear symmetry energy through the lens of QCD Sum Rule, discussing its implications in Rare Isotope Accelerator Plan and nucleon-nucleus scattering. Utilizing mean field approximation and Borel transformation, the research aims to understand asymmetric nuclear
0 views • 21 slides
Understanding Cryptography Basics and Toolbox
Cryptography serves the goals of managing who can view data, ensuring data integrity, and verifying the origin of data. It involves dramatis personae like Alice, Bob, Eve, and Oscar. The toolbox includes hash functions, symmetric encryption, and asymmetric encryption. Hash functions play a crucial r
0 views • 32 slides
Dynamic Core Boosting for Heterogeneous Computing
Exploring the challenges of workload heterogeneity in parallel programming, focusing on the impact of asymmetric hardware on performance and synchronization. Insights on modeling workload imbalance and boosting critical paths for efficient computation in heterogeneous multicores.
0 views • 22 slides
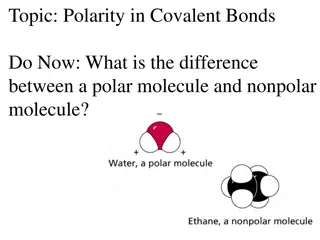
Understanding Polarity in Covalent Bonds
The difference between a polar molecule and a nonpolar molecule lies in the distribution of electrons. A polar molecule has an asymmetric electron distribution due to a significant difference in electronegativity, while a nonpolar molecule has a symmetric electron distribution. You can predict polar
0 views • 15 slides
Understanding the Traveling Salesman Problem and Its Formulation
The Traveling Salesman Problem (TSP) is a classic optimization problem seeking the shortest route visiting a set of points exactly once. This involves symmetric and asymmetric cases, ILP models, subtours, and quadratic assignment formulations. By employing decision variables and constraints, optimal
0 views • 38 slides
Bank Loan Markups and Adverse Selection: Market Concentration Analysis
This research presentation by Beyhaghi, Fracassi, and Weitzner explores the impact of market concentration on bank loan markups and adverse selection. It delves into how asymmetric information across lenders influences interest rates in local banking markets, shedding light on the relationship betwe
0 views • 44 slides
Understanding Strong Asymmetric PAKE Protocols
Explore the intricacies of strong asymmetric PAKE (Password-Authenticated Key Exchange) protocols, including their security notions, possible attacks, and implementations. Learn about the challenges in constructing such protocols, the significance of universally composable security, and the limitati
0 views • 15 slides
Understanding Asymmetric Information and Externalities in Microeconomics
Explore the concepts of adverse selection, market inefficiency, signaling, and moral hazard arising from asymmetric information in microeconomics. Delve into scenarios like the Market for Lemons and health insurance to grasp how information deficiencies impact economic outcomes. Additionally, analyz
0 views • 22 slides
Insights into Persuasion and Equilibrium in Multidimensional Cheap Talk
Explore the dynamics of multidimensional cheap talk, focusing on sender-receiver interactions, influential equilibrium, welfare rankings, and fragility to asymmetries. Lessons touch on bubbling equilibrium, influential equilibrium issues, welfare rankings preferences, and the impact of asymmetric pr
0 views • 20 slides
AERO: Mobile Routing & Addressing System for IP Internetworks
AERO, Asymmetric Extended Route Optimization, is a mobile routing and addressing system designed for IP internetworks like aviation, enterprise, and campus networks. It enables stable IPv6 prefixes for mobile devices, treating them as routers to connect to the Internet of Things. AERO offers feature
0 views • 26 slides
Cryptographic Algorithms and Hash Collisions Overview
Explore the world of cryptographic algorithms and hash collisions. Learn about various hashing algorithms like MD5, SHA-1, SHA-256, and more. Dive into the concepts of symmetric and asymmetric key algorithms and understand the risks associated with hash collisions. Discover the implications of post-
0 views • 58 slides
Proposed Changes to School Week: Asymmetric Week Implementation
Proposed changes to the school week involve introducing an Asymmetric Week structure, with 4.5 days per week. This adjustment aims to modernize and enhance the educational provision in schools, with potential benefits for student health, well-being, and curriculum flexibility. The proposal is based
0 views • 14 slides
Asymmetric Socialization and Resource Transfers in Welfare States
Exploring intergenerational resource transfers in the context of welfare states, this study examines three main channels: families, the government, and markets. It delves into different institutional arrangements governing asset-based reallocations, public transfers, and familial transfers. The leve
0 views • 12 slides
Understanding Non-Optimal Routing and 32-Bit ASN Compatibility
Explore the challenges caused by the incompatibility of 32-bit ASN with old router software, leading to non-optimal routing issues. Learn about Autonomous Systems, AS Numbers, BGP asymmetric routing, and the importance of routing software supporting 32-bit ASN. Discover how outdated software replace
0 views • 8 slides
Fundamentals of Cryptography and Network Security
Explore the basics of cryptography, including classical encryption techniques, terminology definitions, types of encryption operations, cryptanalysis objectives and attacks, and the concept of cipher strength. Uncover the principles and methods behind encryption and decryption, key distinctions betw
0 views • 52 slides
Understanding Secure Messaging and Encryption Techniques
Explore the possibilities of sending secure messages through encryption without the need for advanced degrees in Computer Science or Math. Learn about symmetric and asymmetric key encryption methods, the use of PGP for secure messaging, and the concept of shared-key encryption. Discover the intricac
0 views • 16 slides
MTD-Based Self-Adaptive Resilience in Cloud Systems
Cloud systems face increasing attack surfaces, requiring resilient and self-healing mechanisms. This study explores a Moving Target Defense (MTD) approach for cloud systems, aiming to construct an attack-resilient framework through dynamic network configuration and continuous replacement of virtual
0 views • 36 slides
Understanding Random Walk in Finance: A Visual and Theoretical Exploration
Exploring the concept of random walk in finance through visual examples and theoretical breakdown. Discusses symmetric vs. asymmetric random walk, applications in various fields, and the probability of returning to the starting point in 1D, 2D, and 3D spaces.
0 views • 14 slides
Overview of MPEG: Video Compression Standard
The MPEG video compression standard revolutionized multimedia applications by enabling full-motion video over networks. Introduced in 1988 by the Motion Picture Experts Group, MPEG-1 focused on video compression but also included audio, with notable advancements like MP3. This standard addressed the
0 views • 29 slides
Advanced Concepts in Association Analysis: Handling Categorical Attributes
Explore advanced concepts in association analysis, focusing on the handling of categorical attributes. Learn how to apply association analysis to non-asymmetric binary variables, including examples and potential solutions for skewed attribute value distributions. Discover techniques for managing att
0 views • 48 slides
Strong Support, Strong Futures NDIS Provider Brisbane Righteous Community Care
Strong Support, Strong Futures NDIS Provider Brisbane Righteous Community Care
0 views • 6 slides
Competition Among Asymmetric Sellers with Fixed Supply - Research Overview
This research focuses on competition among sellers with fixed supply in markets for ads, where publishers determine slot allocations to advertisers based on given budgets. The study explores how publishers can maximize revenue by choosing allocation policies strategically, considering symmetric adve
0 views • 21 slides