Read⚡ebook✔[PDF] Linking the Space Shuttle and Space Stations: Early Docking Te
\"COPY LINK HERE ; https:\/\/getpdf.readbooks.link\/B073DZCNTR\n\n[READ DOWNLOAD] Linking the Space Shuttle and Space Stations: Early Docking Technologies from Concept to Implementation (Springer Praxis Books) | Linking the Space Shuttle and Space Stations: Early Docking Technologies from Concept t
1 views • 6 slides
READ⚡[PDF]✔ Emerging Space Powers: The New Space Programs of Asia, the Middle Ea
\"COPY LINK HERE ; https:\/\/getpdf.readbooks.link\/B004NNUV54\n\n[READ DOWNLOAD] Emerging Space Powers: The New Space Programs of Asia, the Middle East and South-America (Springer Praxis Books) | Emerging Space Powers: The New Space Programs of Asia, the Middle East and South-America (Springer Pra
1 views • 6 slides
Airport Security Market to be Worth $25.27 Billion by 2031
\u00ae, the airport security market is projected to reach $25.27 billion by 2031, at a CAGR of 8.6% from 2024 to 2031. Some of the major factors driving the growth of this market are stringent government regulations for airport security and the growing number of air passengers. In addition, increasi
6 views • 5 slides
KEERTHI SECURITY - Best Security Agencies In Bangalore
Keerthi Security is a security and facility management services provider in Bangalore. We are committed to offering top-notch security services for commercial and residential places. We aim to offer very secure and reliable security services to everyone. Our best-trained security guards are very sha
9 views • 11 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
0 views • 6 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
1 views • 6 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
1 views • 6 slides
Understanding the Role of Security Champions in Organizations
Security Champions play a vital role in decision-making concerning security engagement, acting as a core element in security assurance processes within a team. They foster a security culture, reduce dependency on the CISO, and promote responsible autonomy and continuous security education in the org
3 views • 13 slides
Conquer Clutter! Xtended Space: Your Storage & Organization Partner
Drowning in Stuff? Xtended Space offers secure storage solutions & organization hacks! Flexible plans, easy access, & top-notch security. Declutter your home & reclaim your space. Free consultation - Call Today at 9009000798. Our customizable storage units and modular systems offer flexibility to fi
5 views • 2 slides
Boost Your Restaurant's Efficiency and Growth with Xtended Space Storage Solutio
Does a lack of space hinder your restaurant's efficiency and growth? Xtended Space offers storage solutions that can help you organize your kitchen, free up space, and create a smoother workflow. This can lead to improved teamwork, happier customers, and even additional revenue streams. Let Xtended
10 views • 3 slides
United States Space Systems Command International Affairs Overview
The United States Space Systems Command's International Affairs division emphasizes partnership with countries worldwide to address the challenges of the current decade. The presentation highlights the growing threats in space, including developments by Russia and China, stressing the need for a res
0 views • 5 slides
Analysis of FY24 DoD Space Budget Requests for Space Force and Research & Development
The FY24 DoD Space Budget Requests show significant increases for the Space Force along with notable shortfalls and funding disconnects. The Space Force budget includes funding for core programs but also faces challenges in fully funding essential capabilities. The Research & Development budget sees
0 views • 18 slides
Four-Year Plan for WMO Space Weather Activities 2024-2027
Space Weather is a crucial aspect of the natural space environment affecting various technologies on Earth and in space. The plan outlines goals, historical context, and key recommendations by INFCOM-3 for monitoring and modeling solar, magnetospheric, and ionospheric activities. Integration of Spac
0 views • 9 slides
Sustainable Development of Outer Space Activities and Planet Earth: UN/Austria Symposium Insights
Discussion on the long-term sustainability of outer space activities and its impact on Earth at the UN/Austria Symposium. Highlights COPUOS's role in promoting peaceful space use, international space law development, and space debris mitigation. It addresses key areas like space exploration, safety,
0 views • 9 slides
National Aeronautics and Space Administration (NASA) Overview
The National Aeronautics and Space Administration (NASA) is America's leading civil space program focused on space exploration, scientific research, and technological advancements. With a workforce of nearly 18,000, NASA's mission includes human expansion across the Solar System, economic growth in
3 views • 9 slides
Understanding the Roles of a Security Partner
Learn about the roles and responsibilities of a Security Partner, including requesting changes to security roles, approving security requests, and initiating access requests. Explore the overview of Workday Security, the security access request process, and the pre-request process flow. Discover how
1 views • 17 slides
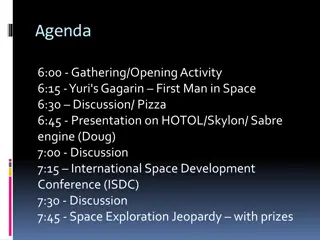
A Brief History of Space Exploration
Space exploration has seen significant milestones, from the German V2 rocket in 1942 to Yuri Gagarin becoming the first man in space in 1961 and the historic Apollo 11 moon landing in 1969. Animals like fruit flies and monkeys have ventured into space, contributing to scientific understanding. Russi
2 views • 14 slides
Exploring Space: From Yuri Gagarin to Modern Innovations
Discover the fascinating journey of space exploration from Yuri Gagarin's historic flight as the first man in space to modern innovations like the V-2 Rocket and the development of the Karman Line. Dive into key events such as the launch of the first intercontinental ballistic missile (ICBM) and the
2 views • 30 slides
Exploring Space: Pioneers, Missions, and the Role of Animals
Humans have a rich history of space exploration, with notable milestones including Yuri Gagarin's orbit in 1961, the Apollo 8 moon mission, and Sally Ride becoming the first American woman in space. Before human space travel, animals played a crucial role in understanding the effects of space on liv
4 views • 21 slides
European Deep Space Surveillance and Tracking Collaboration
EU Space Surveillance and Tracking program involves five European nations collaborating to assess and reduce risks to European spacecraft, provide early warnings for re-entries and space debris, and prevent space debris proliferation. Available deep space sensors, such as optical telescopes, are uti
1 views • 8 slides
Testing in Space Simulation Facilities: A Comprehensive Analysis
This webinar delves into testing in space simulation facilities, comparing the requirements at different stages of space missions such as launch, cruise, and operations. Presented by Miracle Israel Nazarious, it covers topics including space qualification testing involving static load, vibration, th
0 views • 12 slides
Ethics and Impacts of Space Expansion
Ethical considerations surrounding space exploration and expansion are discussed, highlighting both promising and problematic aspects. The debate includes the value of space science, environmental impacts, and the need for responsible expansion to mitigate potential damages. Topics such as launch si
0 views • 21 slides
Understanding Security in World Politics
Security studies delve into the intricate processes of defining and addressing security threats in global politics. It explores the contested nature of security definitions, emphasizes the political significance of security, and challenges the conventional boundaries of International Relations. The
0 views • 8 slides
Exploring Careers in the UK Space Sector
Discover the diverse job opportunities in the UK space industry and explore various disciplines of science involved. Learn about different roles such as design engineer, space business manager, space artist, and more. Find out how to enter these careers through university courses, apprenticeships, o
0 views • 20 slides
Managing Conflicts in Commercial Space Activities
Explore the challenges arising from the commercialization of space activities, the shift in focus towards sustainable space use, and the need to harmonize modern commercial ventures with traditional space laws to prevent conflicts among diverse space actors.
0 views • 14 slides
Development of GR740 Single Board Computer Reference Design by RUAG Space and Partners
RUAG Space collaborates with Gaisler and other partners in the development of a GR740-based single board computer reference design funded by ESA. The project aims to create an advanced technology platform for future space projects, leveraging RUAG's expertise in electronics and digital computers for
0 views • 12 slides
Overview of Fundamental Principles of Space Law and Outer Space Treaties
The content discusses the fundamental principles of space law highlighted at the United Nations Space Law Conference 2020, focusing on key treaties such as the Outer Space Treaty of 1967 and associated rights, duties, and obligations of states in space exploration and use, including non-appropriatio
0 views • 16 slides
Comprehensive Course Review: Security Research Cornerstones at Carnegie Mellon University
Dive into the essential topics of software security, network security, OS security, and cryptography in the course offered by Vyas Sekar at Carnegie Mellon University. Explore control flow hijacks, cryptography terminology, and the importance of network security in protecting data transmissions. Lea
0 views • 41 slides
UIC Security Division Overview and International Activities
The UIC Security Division plays a crucial role in supporting the security platform of the International Union of Railways (UIC). Headed by Jacques Colliard, the division is based in Paris and consists of key personnel like Marie-Hélène Bonneau, Jos Pires, and Laetitia Granger. The division's activ
0 views • 12 slides
The Manfred Lachs International Conference on Conflicts in Space and the Rule of Law
The 4th Manfred Lachs International Conference held in Montreal in 2016 explored the intersection of conflicts in space and the rule of law, specifically focusing on the legal framework surrounding outer space weaponry. Discussions highlighted the importance of upholding humanitarian values, promoti
0 views • 7 slides
FY23 DoD Space Budget Overview and Investments
The FY23 Department of Defense (DoD) budget continues to prioritize investments in national security space capabilities, with a $1.6B increase in funding for DoD space programs. The United States Space Force receives significant appropriations exceeding the request, emphasizing oversight and managem
0 views • 16 slides
Automating Security Operations Using Phantom
Isabella Minca, an intern for 4 months in the Security Team at Adobe, presents an overview of automating security operations using Phantom. The presentation covers goals, security alerts, Phantom playbooks, handling security data, and the capabilities of Phantom in orchestrating security responses.
0 views • 28 slides
Understanding HTTP Security Headers for Web Apps
Explore the importance of HTTP security headers on web applications through a detailed breakdown of headers like HSTS, XFO, XSS, CSP, CTO, RH, and FP. Learn how these headers enhance security by instructing browsers on handling website content, preventing various attacks. Gain insights on configurin
0 views • 68 slides
Personalized Celebrity Video Search: Cross-space Mining Approach
This study presents a novel approach for personalized celebrity video search based on cross-space mining, aiming to match user interests with celebrity popularity. By learning the interest space of users and the popularity space of celebrities, the framework correlates the two spaces to enhance sear
0 views • 23 slides
Modular Security Analysis for Key Exchange and Authentication Protocols
Explore the modular security analysis approach used to examine the security of key exchange and authentication protocols, focusing on the universally composable authentication with a global Public Key Infrastructure. The analysis involves splitting the system into smaller components, separately anal
0 views • 15 slides
Revolutionizing Security Testing with BDD-Security
Explore the innovative approach of Continuous and Visible Security Testing with BDD-Security by Stephen de Vries. Gain insights into how security testing can be integrated seamlessly into modern development practices, shifting the focus from reactive to proactive measures. Learn about the importance
0 views • 33 slides
Comprehensive DevOps Security Training Overview
This Certified DevOps Security Practitioner course provides a deep dive into implementing DevSecOps, integrating security into the DevOps processes. Covering topics like security testing, Docker security, automation, and more, the training aims to equip participants with the necessary skills to embe
0 views • 5 slides
Understanding Security Testing and Architecture
Explore the fundamentals of security testing, computer security goals, software security approach, and security architecture. Learn about securing computer assets, verifying trustworthiness of security mechanisms, and validating security architecture through threat modeling. Enhance your knowledge o
0 views • 57 slides
Quantum Space-Bounded Complexity in Logarithmic Space: A Comprehensive Overview
Quantum space-bounded complexity explores the memory requirements for solving problems in log space. Examples include matrix multiplication, undirected graph connectivity, and problems like inverting matrices and determining connectivity. The significance of deterministic log space (NL) and nondeter
0 views • 49 slides
Space Debris Removal - Towards Sustainable Space Traffic Management
The 3rd Annual Manfred Lachs Conference in Montreal discussed the pressing issue of space debris removal and the need for a legal framework for space traffic management. With the increasing number of objects in Earth's orbit posing a risk, international collaboration and regulatory initiatives are e
0 views • 9 slides
![Read⚡ebook✔[PDF] Linking the Space Shuttle and Space Stations: Early Docking Te](/thumb/21519/read-ebook-pdf-linking-the-space-shuttle-and-space-stations-early-docking-te.jpg)
![READ⚡[PDF]✔ Emerging Space Powers: The New Space Programs of Asia, the Middle Ea](/thumb/21554/read-pdf-emerging-space-powers-the-new-space-programs-of-asia-the-middle-ea.jpg)