Ensuring Credible Private Set Membership with Efficient Communication
Explore the concept of credible private set membership ensuring server privacy, client privacy, and data credibility through innovative protocols and approaches. The focus is on maintaining high-entropy passwords securely while optimizing rounds and leveraging underlying crypto primitives efficientl
1 views • 18 slides
Entropy in British Victorian Literature: A Scientific Analysis
Delve into the entropic nature of British Victorian Literature as Hannah Harris explores the concept of entropy in storytelling. Uncover how the lack of a defined center and the compulsion to repeat shape these works, validated by science as faithful reflections of life through realism.
8 views • 22 slides
Unit 4: Non-Examination Assessment Overview
The Unit 4 Non-Examination Assessment from 2017 focuses on working as a historian, with tasks including source evaluation and discussion of different historical interpretations. The assessment is marked out of 40 and is worth 20% of the qualification. It assesses knowledge, understanding, source ana
1 views • 14 slides
Understanding Maxwell Equations in Thermodynamics
In thermodynamics, Maxwell equations are derived using Euler's reciprocity relation. They involve characteristic functions such as internal energy, free energy, enthalpy, and Gibbs free energy, along with parameters like temperature, entropy, pressure, and volume. These equations form the foundation
0 views • 15 slides
Understanding Thermodynamics and Fluid Mechanics Fundamentals for Efficiency
Explore key concepts in thermodynamics and fluid mechanics such as the equation of continuity, the first law of thermodynamics, the momentum equation, Euler's equation, and more. Learn about efficiency, internal energy, and the laws governing energy transfer in various systems. Delve into topics lik
2 views • 12 slides
Thermodynamic Principles of Polymers in Solution: Flory-Huggins Theory and Macromolecular Solutions
Understanding the thermodynamic behavior of polymers in solution is crucial in various industrial and scientific applications. The Flory-Huggins theory provides insights into athermal macromolecular solutions, heat of mixtures, interaction parameters, and the concept of good vs. mediocre solvents. T
1 views • 77 slides
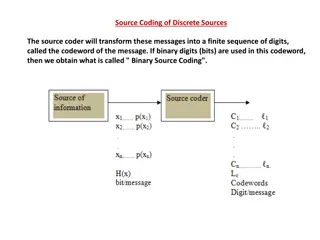
Understanding Source Coding for Discrete Sources
Source coding involves transforming messages into codewords, with considerations for minimizing code length and ensuring unique decodability. Binary source coding and efficiency are key concepts explored in this process. Check out the details and examples provided to deepen your understanding of sou
0 views • 14 slides
Evaluation of Source Usefulness through Multiple Criteria
In this evaluation task, you will assess the effectiveness of questions based on various criteria such as authorship, type of source, purpose, and relevance of information. By carefully analyzing the source content and rubric, you will provide an overall judgment on the source's utility while evalua
3 views • 10 slides
Understanding the Carnot Engine: Application of the Second Law of Thermodynamics
Exploring the Carnot engine as an ideal model to understand the Second Law of Thermodynamics, which highlights the efficiency of heat engines and the concept of entropy. The engine operates through a cyclic process, transferring heat from a high-temperature reservoir to a low-temperature one, produc
0 views • 15 slides
Understanding the C4.5 Algorithm in Machine Learning
Explore the C4.5 algorithm, a powerful tool in the realm of machine learning. Delve into topics such as numeric attributes, information gain, entropy calculations, and handling missing values. Learn about the importance of attribute selection, class-dependent discretization, and making optimal split
0 views • 17 slides
Analysis of Onion Routing Security and Adversary-based Metrics
In this comprehensive analysis, the security aspects of Onion Routing are scrutinized along with adversary-based metrics. Various security vulnerabilities such as compromised relays and potential attacks on the first and last routers are examined. Existing metrics like entropy coefficients and proba
0 views • 21 slides
Exploring Limited Randomness in Repeated Games
Dive into the world of randomness in repeated games through this insightful research by Moni Naor, Pavel Hubæk, and Jon Ullman. Discover the significance of randomness in algorithms, equilibria, and finitely repeated games. Explore the necessity of randomness in Nash Equilibrium and the computation
2 views • 28 slides
Understanding Thermodynamics: Energy and Heat
Explore the fundamental concepts of thermodynamics, including the conservation of energy, entropy, heat transfer, and the relationship between temperature and kinetic energy. Discover how energy transforms in natural events, the laws governing thermodynamics, and the role of heat in the motion of pa
0 views • 28 slides
Exploring Source-Routed Forwarding in SDN-Based WANs
Software-Defined Networking (SDN) in Wide Area Networks (WANs) utilizes source routing methods to address performance concerns related to network convergence time. Challenges such as latency constraints and controller placement impact performance, highlighting the need for efficient path computation
0 views • 24 slides
Understanding Kinetic Theory of Gases and Thermodynamics
Explore the fundamental principles of the kinetic theory of gases, including the five postulates and the relationship between macroscopic properties and microscopic phenomena. Delve into the concept of entropy and thermodynamics, along with the behavior of ideal and real gases. Gain insights into th
0 views • 116 slides
Understanding Mergers and Random Sources in Data Analysis
Exploring the concepts of mergers, minimal entropy, statistical distance, and somewhere random sources in data analysis. Discover how convex combinations play a crucial role in extracting randomness from different sources for improved data processing.
1 views • 31 slides
Customize Your Game with Slot Machine Source Code
Customize your game with slot machine source code and enhance its features. Discover how using customizable source code can help you build engaging and profitable slot machine games.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 5 slides
Space-Efficient Estimation of Statistics Over Sub-Sampled Streams
This research focuses on efficiently estimating statistics over sub-sampled streams, particularly in the context of IP packet streams for traffic monitoring. Various types of sampling methods are explored, such as Bernoulli sampling, to compute key metrics like frequency moments, number of distinct
0 views • 22 slides
Understanding Sensor-Based Mobile Web Fingerprinting and Attacks
This content discusses sensor-based mobile web fingerprinting, cross-site input inference attacks, smartphone sensors, motion sensor data collection, and HTML5 DeviceMotionEvent interface. It highlights the potential security risks associated with sensor data access on mobile devices and the need fo
0 views • 30 slides
The Influence of Lexical Functional Load on Phoneme System Changes
The study explores how the functional load of phoneme contrasts affects the trajectory of phoneme system changes over time. Researchers examine phoneme mergers in nine languages, finding an inverse correlation between the number of minimal pairs and mergers. The model is refined to investigate diffe
2 views • 26 slides
Laplacian Deformation in Engineering and Applied Science
Laplacian deformation is a technique used in non-rigid registration to account for shape variance and improve fitting between source and target shapes. This method involves minimizing the distance and distortion terms to achieve accurate alignment. Intrinsic and extrinsic methods are discussed, wher
0 views • 53 slides
Development of High Entropy Alloy-Based SOFC Anode for Controlled Reformation
Development and testing of a High Entropy Alloy-based Solid Oxide Fuel Cell (SOFC) anode for controlled reformation to improve thermal performance, reduce carbon deposition, and enhance durability. The project involves fabricating cells, electrochemical testing, modeling reformation rates, and scali
0 views • 32 slides
Exploring Entropy and the Second Law of Thermodynamics
This lecture delves into the concepts of entropy and the Second Law of Thermodynamics. It discusses the intuitive sense of energy, the nature of entropy, and the irreversibility of processes. The Second Law is highlighted in relation to heat transfer, work, and the increase of entropy in the univers
0 views • 23 slides
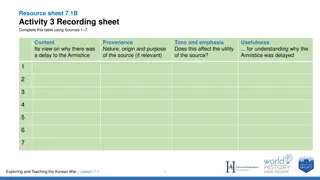
Understanding Delay in the Korean Armistice Negotiations
Sources 1 to 4 provide insights into the reasons behind the delay in reaching an armistice during the Korean War. Source 1 discusses the POW question's impact, Source 2 presents Eisenhower's stance on peace efforts, Source 3 outlines Syngmam Rhee's opposition to a divided Korea, and Source 4 reflect
0 views • 9 slides
The Impact of Open Source Library Automation Systems
Marshall Breeding discusses the rise of open source library automation systems globally, comparing them to proprietary alternatives. He explores the adoption of open source products in the US and their coverage in international library reports, highlighting how libraries of different budgets utilize
0 views • 38 slides
Overview of Off-Site Source Recovery Program Capabilities
The Off-Site Source Recovery Program (OSRP) aids in recovering radioactive sealed sources for national security and public health. OSRP focuses on recovering TRU and non-TRU sources, with over 38,500 sources retrieved globally. Services include source registration, consultancy, and training for vari
0 views • 25 slides
Understanding Information Entropy in Information Theory
Information entropy, a key concept in information theory, measures the average amount of information in a message. Source entropy and binary source entropy are explained with examples, along with maximum source entropy for both binary and non-binary sources. Learn how to calculate entropy for differ
0 views • 12 slides
Awareness and Use of Open Source Software Among Library Professionals in Bangalore City
This study presented by Podili Anjaneyulu, Kaviha B, Sreya Gopinath, and K.G. Jayarama Naik from Bangalore University focuses on identifying the awareness and usage of open source software among library professionals in Bangalore. The study explores different open source software available for libra
0 views • 18 slides
Understanding Normal Shock Waves in Gas Dynamics
In gas dynamics, normal shock waves occur when there is a significant pressure difference across a compression pulse, leading to increased entropy. This results in non-isentropic flow known as compression shock waves. The formation of compression and expansion waves can be likened to piston movement
0 views • 16 slides
Why Slot Machine Source Code is Key to Fast-Track Game Development
Discover why slot machine source code is essential for fast-tracking game development. Learn how slot machine scripts, PHP slot machine source code, and online casino script full source code free can save time and boost efficiency.\n\nSource>>\/\/ \/
0 views • 4 slides
Understanding Maximum Entropy Modeling in Environmental Science
Maximum Entropy modeling, also known as MaxEnt, is a technique that maximizes randomness by removing patterns in data. This method is widely used in environmental science to create models using covariates, occurrences, and probability density functions. The relationships between histograms and proba
0 views • 46 slides
Gibbs Paradox and Quantum Information: Understanding Entropy and Resolution
Description of the Gibbs problem of entropy mixing gases, conventional resolution, issues of (dis)continuity, the role of indistinguishability and quantum mechanics in resolution, dissenting views, necessity of quantum mechanics, and the relationship between statistical mechanics and entropy. Key di
0 views • 19 slides
Understanding Fund-Source Pairings in ConnectCarolina Chartfields
Explore the Fund-Source pairings in the new ConnectCarolina chartfield structure. Learn how to avoid errors by correctly matching Funds and Sources, and understand the interaction between Fund, Source, and Department. Gain insight into the major fund groups and their specific Source ranges for effic
0 views • 17 slides
OpenACC Compiler for CUDA: A Source-to-Source Implementation
An open-source OpenACC compiler designed for NVIDIA GPUs using a source-to-source approach allows for detailed machine-specific optimizations through the mature CUDA compiler. The compiler targets C as the language and leverages the CUDA API, facilitating the generation of executable files.
0 views • 28 slides
Thermodynamics of Materials: Experimental Verification and Entropy Analysis
Verification of the Third Law of Thermodynamics through the study of phase transitions in elements like sulfur, exemplifying the relationship between heat capacity, enthalpy, entropy, and the Third Law. Experimental data on entropy changes and molar entropies, as well as insights into the behavior o
0 views • 24 slides
Introduction to Data Engineering and Information Theory
This content delves into the fundamentals of data engineering and information theory, focusing on topics such as data communication, sharing, storage, and archiving. It explores key concepts like data representation, corruption prevention, historical milestones in communication technology, Shannon's
0 views • 24 slides
Create Profitable Casino Games with Expert Slot Machine Source Code
Develop successful games with Slot Machine Source Code, php slot machine source code, slot game script, and slot machine script for gaming industries and businesses.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 3 slides
Boost Your Game’s Success with Our Reliable Slot Machine Source Code
Discover premium Slot Machine Source Code to build engaging games. Explore reliable source code slot machine options for ultimate success.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 4 slides
Maximize Efficiency_ How Slot Machine Source Code Makes Updates a Breeze
Simplify updates and customization with slot machine source code. Perfect for casino slot game source code, slot game script, and iGaming innovation. Contact AIS Technolabs.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 5 slides
Unraveling the Mystery of Slot Machine Source Code_ A Developer’s Guide
Learn the intricacies of slot machine source code to develop captivating games. Explore source code slot machine insights with this comprehensive guide.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 4 slides