Reporting Pilot Financial Remedies
Established practices of confidentiality in family financial remedy (FR) cases are being challenged by recent judicial opinions, suggesting a shift towards greater transparency. Exceptions to the general rule of non-reporting are identified, highlighting evolving attitudes towards media reporting an
0 views • 20 slides
Freedom of Speech-Topics 3.5 – 3.6
Delve into the realm of freedom of speech and anonymity through a series of thought-provoking questions on topics like the First Amendment, anonymity, online privacy, and net neutrality. Discover insights on how these concepts intersect with legal rights, law enforcement, and individual expression i
0 views • 26 slides
What Makes Banksy's Paintings So Popular
Banksy's paintings resonate due to their edgy, thought-provoking messages and innovative street art techniques. His anonymity creates a sense of mystery, and his works often appear in unexpected places, capturing public attention. The fusion of art and activism in Banksy's work drives its enduring p
0 views • 5 slides
What Makes Banksy's Paintings So Popular
Banksy's paintings resonate due to their edgy, thought-provoking messages and innovative street art techniques. His anonymity creates a sense of mystery, and his works often appear in unexpected places, capturing public attention. The fusion of art and activism in Banksy's work drives its enduring p
1 views • 5 slides
Unit 4: Non-Examination Assessment Overview
The Unit 4 Non-Examination Assessment from 2017 focuses on working as a historian, with tasks including source evaluation and discussion of different historical interpretations. The assessment is marked out of 40 and is worth 20% of the qualification. It assesses knowledge, understanding, source ana
1 views • 14 slides
Self-Care, Resilience, and Preventing Burnout: Essential Tips for Well-Being
This session focuses on the crucial aspects of self-care, resilience, and preventing burnout, emphasizing the importance of psychological personal protective equipment. Experts share valuable insights and actionable tips to help individuals maintain mental well-being amidst challenges. Engage in ful
0 views • 10 slides
Darknet Drug Trafficking Trends and Impacts in 2020
Darknet drug trafficking over the years has shown both upward and downward trends influenced by market shutdowns, exit scams, and the COVID-19 pandemic. Despite challenges, anonymity and cryptocurrency use drive transactions, with cannabis being a popular choice. The evolving landscape maintains ste
0 views • 13 slides
Compact Ring Signatures from LWE - CRYPTO 2021 Research
Research presented at CRYPTO 2021 introduces a compact ring signature scheme using components instantiated from LWE. The scheme allows each signer to sign on behalf of a ring of users, offering properties of unforgeability, anonymity, and compactness. The work explores the possibility of building co
0 views • 25 slides
Exploring a Poignant Holocaust Poem: A 6893 by Anna Sotto
Discover the powerful poem "A 6893" by Anna Sotto, reflecting on the heartbreaking experiences of a Jewish person during the Holocaust. Through the poignant verses, the poem delves into the stripping away of identity and humanity faced by many victims. The questions raised about the anonymity of wri
1 views • 12 slides
Understanding Ethics in Research: Principles and Major Issues
Ethics in research is crucial for ensuring the well-being of participants and upholding moral principles. Key aspects include beneficence, respect for autonomy, informed consent, and freedom from harm. Major ethical issues involve informed consent, beneficence, respect for anonymity and confidential
5 views • 18 slides
Strategic Tourism Demand Forecasting Methods
The chapter delves into qualitative and quantitative approaches for tourism demand forecasting, including the Delphi method and executive opinion juries. It explores advanced forecasting methods and the application of big data analytics in the tourism industry. The focus is on generating expert opin
1 views • 39 slides
Ethical Considerations in Reporting Violence Against Women: Interviewing Victims and Ensuring Consent
It is crucial for journalists reporting on violence against women to interview victims and survivors ethically and respectfully, ensuring informed consent is obtained before sharing their stories. This involves being sensitive to trauma, prioritizing the well-being of the interviewees, and assessing
3 views • 11 slides
Understanding Bitcoin and Cryptocurrency: A Comprehensive Overview
Delve into the world of Bitcoin and cryptocurrency with this comprehensive guide by Ethan Herdrich, an Experiential Learning Specialist. Learn about Bitcoin as a token and protocol, the concept of blockchain, mining, origins in the deep web, anonymity, other cryptocurrencies, and the volatile nature
0 views • 15 slides
Overview of ATM Committee at BUSM
Boston University School of Medicine (BUSM) is committed to providing a supportive learning environment free from mistreatment. The ATM Committee at BUSM focuses on investigating reports of student mistreatment and ensuring prompt, respectful responses. The committee's charge includes identifying an
0 views • 12 slides
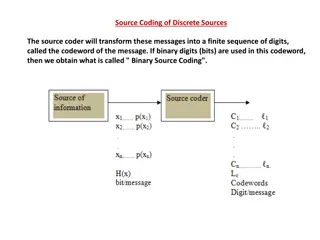
Understanding Source Coding for Discrete Sources
Source coding involves transforming messages into codewords, with considerations for minimizing code length and ensuring unique decodability. Binary source coding and efficiency are key concepts explored in this process. Check out the details and examples provided to deepen your understanding of sou
0 views • 14 slides
Student Experience of Learning and Teaching (SELT) at University of Adelaide
The Student Experience of Learning and Teaching (SELT) at the University of Adelaide is an online survey that allows students to provide valuable feedback on their learning experience. This feedback is instrumental in continuous improvement of courses and teaching methods. The survey is confidential
0 views • 8 slides
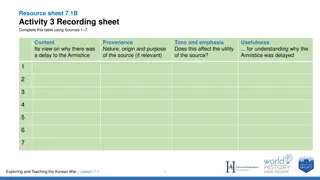
Evaluation of Source Usefulness through Multiple Criteria
In this evaluation task, you will assess the effectiveness of questions based on various criteria such as authorship, type of source, purpose, and relevance of information. By carefully analyzing the source content and rubric, you will provide an overall judgment on the source's utility while evalua
3 views • 10 slides
Privacy Considerations in Data Management for Data Science Lecture
This lecture covers topics on privacy in data management for data science, focusing on differential privacy, examples of sanitization methods, strawman definition, blending into a crowd concept, and clustering-based definitions for data privacy. It discusses safe data sanitization, distribution reve
0 views • 23 slides
Enhancing Crowd Anonymity with Dummy Jondos
Explore the concept of using dummy jondos to increase anonymity in crowds and mitigate common attacks like eavesdropping and collusion. Learn how the introduction of dummy jondos can impact crowd size and resistance against potential threats, along with considerations for implementation and ensuring
2 views • 30 slides
Proposal for IEEE 802.11-23/1984r1 TGbi Coordinated MAC Rotation
The document discusses a proposal for IEEE 802.11-23/1984r1 TGbi focusing on coordinated MAC rotation, EDP epochs, anonymity sets, and group epochs. It introduces concepts like individual and mass rotations, anonymity set size, and hiding in the crowd examples. The coordination for group epochs and
1 views • 10 slides
Student Safeguarding Engagement Session Facilitator Slides
This slide deck example is designed to facilitate student engagement sessions on safeguarding in schools, covering key areas like consent, confidentiality, and anonymity. The slides include activities created by the International Taskforce on Child Protection, Student Voice Committee, to gather stud
2 views • 28 slides
Exploring Source-Routed Forwarding in SDN-Based WANs
Software-Defined Networking (SDN) in Wide Area Networks (WANs) utilizes source routing methods to address performance concerns related to network convergence time. Challenges such as latency constraints and controller placement impact performance, highlighting the need for efficient path computation
0 views • 24 slides
Customize Your Game with Slot Machine Source Code
Customize your game with slot machine source code and enhance its features. Discover how using customizable source code can help you build engaging and profitable slot machine games.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 5 slides
Trust-Based Anonymous Communication Models and Routing Algorithms
This research paper discusses trust-based anonymous communication models and routing algorithms in the context of onion routing, emphasizing the importance of trust in mitigating security risks from adversaries with resources. The paper presents a model of trust and proposes trust-based routing algo
0 views • 65 slides
Laplacian Deformation in Engineering and Applied Science
Laplacian deformation is a technique used in non-rigid registration to account for shape variance and improve fitting between source and target shapes. This method involves minimizing the distance and distortion terms to achieve accurate alignment. Intrinsic and extrinsic methods are discussed, wher
0 views • 53 slides
MIYHS Teacher Training: Importance of Confidentiality and Consent
Maine Integrated Youth Health Survey (MIYHS) teacher training emphasizes the significance of maintaining student confidentiality and obtaining parental consent. Teachers play a crucial role in ensuring student anonymity during survey administration. Understanding the importance of consent and confid
0 views • 14 slides
Peer Evaluation Strategies in SALIS Language Module
Explore the peer evaluation methods used in the School of Applied Language & Intercultural Studies (SALIS) for the FR376 French module. The approach includes criteria such as linguistic quality, interaction management, and drawing lessons for future productions. Rubrics on Loop Forum aid in assessin
0 views • 21 slides
Understanding Delay in the Korean Armistice Negotiations
Sources 1 to 4 provide insights into the reasons behind the delay in reaching an armistice during the Korean War. Source 1 discusses the POW question's impact, Source 2 presents Eisenhower's stance on peace efforts, Source 3 outlines Syngmam Rhee's opposition to a divided Korea, and Source 4 reflect
0 views • 9 slides
Understanding Data Security and Privacy: An Overview of k-Anonymity, l-Diversity, t-Closeness, and Reconstruction Attacks
Delve into the realm of data security and privacy, exploring concepts such as k-Anonymity, l-Diversity, t-Closeness, and Reconstruction Attacks. Learn about the importance of privacy concerns, privacy-preserving data sharing, real threats of linking attacks, and specific instances like the GIC Incid
0 views • 44 slides
The Impact of Open Source Library Automation Systems
Marshall Breeding discusses the rise of open source library automation systems globally, comparing them to proprietary alternatives. He explores the adoption of open source products in the US and their coverage in international library reports, highlighting how libraries of different budgets utilize
0 views • 38 slides
Overview of Off-Site Source Recovery Program Capabilities
The Off-Site Source Recovery Program (OSRP) aids in recovering radioactive sealed sources for national security and public health. OSRP focuses on recovering TRU and non-TRU sources, with over 38,500 sources retrieved globally. Services include source registration, consultancy, and training for vari
0 views • 25 slides
Awareness and Use of Open Source Software Among Library Professionals in Bangalore City
This study presented by Podili Anjaneyulu, Kaviha B, Sreya Gopinath, and K.G. Jayarama Naik from Bangalore University focuses on identifying the awareness and usage of open source software among library professionals in Bangalore. The study explores different open source software available for libra
0 views • 18 slides
Why Slot Machine Source Code is Key to Fast-Track Game Development
Discover why slot machine source code is essential for fast-tracking game development. Learn how slot machine scripts, PHP slot machine source code, and online casino script full source code free can save time and boost efficiency.\n\nSource>>\/\/ \/
0 views • 4 slides
Understanding Fund-Source Pairings in ConnectCarolina Chartfields
Explore the Fund-Source pairings in the new ConnectCarolina chartfield structure. Learn how to avoid errors by correctly matching Funds and Sources, and understand the interaction between Fund, Source, and Department. Gain insight into the major fund groups and their specific Source ranges for effic
0 views • 17 slides
OpenACC Compiler for CUDA: A Source-to-Source Implementation
An open-source OpenACC compiler designed for NVIDIA GPUs using a source-to-source approach allows for detailed machine-specific optimizations through the mature CUDA compiler. The compiler targets C as the language and leverages the CUDA API, facilitating the generation of executable files.
0 views • 28 slides
Create Profitable Casino Games with Expert Slot Machine Source Code
Develop successful games with Slot Machine Source Code, php slot machine source code, slot game script, and slot machine script for gaming industries and businesses.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 3 slides
Boost Your Game’s Success with Our Reliable Slot Machine Source Code
Discover premium Slot Machine Source Code to build engaging games. Explore reliable source code slot machine options for ultimate success.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 4 slides
Maximize Efficiency_ How Slot Machine Source Code Makes Updates a Breeze
Simplify updates and customization with slot machine source code. Perfect for casino slot game source code, slot game script, and iGaming innovation. Contact AIS Technolabs.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 5 slides
Unraveling the Mystery of Slot Machine Source Code_ A Developer’s Guide
Learn the intricacies of slot machine source code to develop captivating games. Explore source code slot machine insights with this comprehensive guide.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 4 slides
Understanding the Importance of Anonymous Communication in Digital World
Explore the concept of information hiding, including digital watermarking, steganography, covert channels, and anonymous communication. Learn how anonymity can benefit journalists, whistleblowers, activists, executives, and more, while also providing privacy for everyday individuals. Discover the ch
0 views • 56 slides