Types Cyber Attacks: Cyber Security Training Workshop
Join our Cyber Security Training Workshop to learn about different types of cyber attacks such as social engineering attacks, DDoS attacks, malware attacks, MitM attacks, APTs, and password attacks. Enhance your knowledge and skills in cyber security.
15 views • 45 slides
Adversarial Machine Learning
Evasion attacks on black-box machine learning models, including query-based attacks, transfer-based attacks, and zero queries attacks. Explore various attack methods and their effectiveness against different defenses.
21 views • 60 slides
Channel Design
Channel design involves creating a plan for the efficient distribution and movement of products and services from the producer to the customer. This process includes determining the channel flow, identifying channel members, setting channel objectives, and developing a channel strategy.
0 views • 13 slides
Understanding Malicious Attacks, Threats, and Vulnerabilities in IT Security
Malicious attacks, threats, and vulnerabilities in IT systems pose significant risks and damages. This chapter explores the types of attacks, tools used, security breaches, and measures to protect against cyber threats. Learn how security professionals safeguard organizations from malicious attacks
0 views • 24 slides
Principles of Cyber Security
Threat actors prioritize targeting networks to exploit vulnerabilities, leading to various attacks such as interception, DNS attacks, and MITM attacks. MITM attacks involve eavesdropping on communications or impersonating parties, with techniques like session replay to steal credentials. Implementin
0 views • 7 slides
Understanding Channel Design in Marketing
Channel design involves planning the distribution of products and services from producers to customers through different business entities or individuals. It encompasses elements like channel flow, channel members, objectives, alternatives, and strategy. Successful channel design aligns with busines
0 views • 13 slides
Managing Covid-19 Cyber and Data Protection Risks
Exploring the risks and challenges related to cyber attacks and data protection amidst the Covid-19 pandemic. The agenda covers an overview of cyber-attacks, recent developments, protections against cyber attacks, data protection concerns during lockdown, compliance steps, and employee rights issues
1 views • 35 slides
Mitigation of DMA-based Rowhammer Attacks on ARM
Practical strategies are presented in "GuardION: Practical Mitigation of DMA-based Rowhammer Attacks on ARM" to defend against Rowhammer attacks on ARM architecture. The paper discusses Rowhammer defenses, RAMPAGE attacks on Android OS, and introduces GuardION as a lightweight mitigation approach. I
0 views • 48 slides
Successful Channel Modification Techniques and Benefits
Channel modification projects aim to accelerate the recovery of stable, sustainable channel forms in dynamic balance with sediment, large wood, and flow regimes. Successful modifications lead to improved habitat quality, stability, and diversity, benefiting sediment transport and riparian zones. Phy
0 views • 15 slides
Cybersecurity Challenges: Attacks on Web Applications and Cost of Security Breaches
In the realm of cybersecurity, attacks on web applications pose a significant threat with 78% of attacks targeting applications. The consequences of these attacks are immense, with projected costs reaching $6 trillion annually by 2021. Notable breaches in recent years highlight the urgency for robus
8 views • 23 slides
Effective Channel Management Decisions for Marketing Success
The success of marketing channels lies in making right channel design decisions and effectively implementing them through channel management decisions. From selecting channel members to training and motivating them, companies must focus on building strong partnerships to drive success in the competi
5 views • 6 slides
Understanding Side Channels in Software Security
This content delves into the topic of side channels in software security, focusing on the leakage of sensitive information through timing side channels. It discusses the concept of covert channels, reference monitors, limitations of analysis, and prevention strategies to mitigate the risks associate
0 views • 25 slides
Understanding Denial-of-Service Attacks and Defense Strategies
Denial-of-Service attacks pose a serious threat where attackers flood networks with traffic, leading to system crashes and slowdowns. Explore the impact, expected results, and various categories of DoS attacks such as bandwidth attacks, protocol exceptions, and logic attacks. Learn how to defend aga
0 views • 61 slides
Understanding Network Denial of Service (DoS) Attacks
Network Denial of Service (DoS) attacks aim to disrupt services by overwhelming them with traffic. These attacks can occur at various layers of the network stack and exploit weaknesses to achieve their goal. Amplification attacks, such as the Smurf attack and DNS Amplification attack, can significan
2 views • 52 slides
Preventing Active Timing Attacks in Low-Latency Anonymous Communication
This research addresses the vulnerabilities of onion routing to timing attacks and proposes solutions to prevent active timing attacks, focusing on low-latency anonymous communication systems. Various problems related to timing attacks in onion routing are analyzed, including the role of adversaries
0 views • 52 slides
Understanding Control Hijacking Attacks in Software Systems
Control hijacking attacks, such as buffer overflows and format string vulnerabilities, allow attackers to take over a target machine by manipulating application control flow. Knowledge of C functions, system calls, CPU, and OS used is crucial for executing these attacks successfully. This summary pr
1 views • 55 slides
Effective Method to Protect Web Servers Against Breach Attacks
Abdusamatov Somon presents an effective method called HTB to protect web servers against breach attacks, focusing on secure computation and mitigation. The research addresses side-channel attacks based on compression and the CRIME BREACH issue, providing insights into implementing the breach attack
1 views • 13 slides
The THz Channel Model in Wireless Data Center
This contribution presents preliminary THz channel modeling results for future wireless data center scenarios. Ray tracing simulations are conducted for various channel types, utilizing RMS delay spread and RMS angular spread to measure multipath richness. A stochastic channel model is developed and
0 views • 33 slides
Strategies to Protect School Systems from Cyber Attacks
Schools are increasingly becoming targets of cyber attacks, making cybersecurity measures crucial. The article discusses the importance of responding to cyber attacks, creating incident response plans, and being vigilant against interception attacks. It outlines the steps to detect, document, and mi
0 views • 21 slides
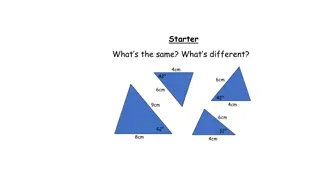
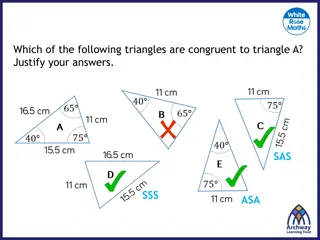
Understanding Triangle Congruence Properties
Delve into the principles of congruent triangles by exploring the properties of side-side-side (SSS), side-angle-side (SAS), angle-side-angle (ASA), and right-angle-hypotenuse-side (RHS) congruence. Visual explanations help clarify how these properties determine if triangles are congruent.
0 views • 18 slides
Cache-Based Attack and Defense on ARM Platform - Doctoral Dissertation Thesis Defense
Recent research efforts have focused on securing ARM platforms due to their prevalence in the market. The study delves into cache-based security threats and defenses on ARM architecture, emphasizing the risks posed by side-channel attacks on the Last-Level Cache. It discusses the effectiveness of si
0 views • 44 slides
Defending Against Cache-Based Side-Channel Attacks
The content discusses strategies to mitigate cache-based side-channel attacks, focusing on the importance of constant-time programming to avoid timing vulnerabilities. It covers topics such as microarchitectural attacks, cache structure, Prime+Probe attack, and the Bernstein attack on AES. Through d
0 views • 25 slides
Security Issues in Parallel and Distributed Computing - Side Channel Attacks and Defenses
Explore various security threats in parallel and distributed computing, focusing on side channel attacks and defenses. Learn about microarchitecture, cache hierarchy, popular attacks, defense mechanisms, and more. Discover how hardware vulnerabilities can lead to the compromise of sensitive data and
1 views • 30 slides
Understanding Spectre and Meltdown Security Vulnerabilities
Spectre and Meltdown are two critical security vulnerabilities that exploit microarchitectural features to gain unauthorized access to memory. These vulnerabilities enable attackers to read memory that should be inaccessible, targeting branch prediction and exception handling mechanisms. Side channe
0 views • 19 slides
Scatter-and-Gather Revisited: High-Performance Side-Channel-Resistant AES on GPUs
This research focuses on enhancing the security of AES encryption on GPUs by introducing the Scatter-and-Gather (SG) approach, aimed at achieving side-channel resistance and high performance. By reorganizing tables to prevent key-related information leakage, the SG approach offers a promising soluti
0 views • 34 slides
Automated Signature Extraction for High Volume Attacks in Cybersecurity
This research delves into automated signature extraction for high-volume attacks in cybersecurity, specifically focusing on defending against Distributed Denial of Service (DDoS) attacks. The study discusses the challenges posed by sophisticated attackers using botnets and zero-day attacks, emphasiz
0 views • 37 slides
Proposal for Improved Channel Access Efficiency in IEEE 802.11 Networks
The proposal addresses the inefficiencies in utilizing secondary channels in IEEE 802.11 networks, aiming to enhance access to wideband channels (>20 MHz) when the primary channel is busy. It introduces a mechanism for APs and STAs to access available secondary channels while the primary channel is
0 views • 7 slides
SecDir: A Secure Directory to Defeat Directory Side-Channel Attacks
SecDir introduces a secure directory design to mitigate directory side-channel attacks, a critical security threat. By reassigning part of the conventional directory storage to per-core private directories, SecDir aims to block directory interference between processes and enhance security in cache h
0 views • 49 slides
IEEE 802.11-24/0070r1 Presentation on Non-Primary Channel Access
This presentation discusses the concept of using secondary channels for PPDU transmission in IEEE 802.11 networks to improve efficiency in large bandwidth scenarios. It covers topics such as channel access, backoff mechanisms, and channel switching thresholds. Design principles emphasize minimal imp
0 views • 15 slides
Targeted Deanonymization via the Cache Side Channel: Attacks and Defenses
This presentation by Abdusamatov Somon explores targeted deanonymization through cache side-channel attacks, focusing on leaky resource attacks and cache-based side-channel attacks. It discusses the motivation behind these attacks, methods employed, potential defenses, and the evaluation of such att
0 views • 16 slides
Understanding Network Security Vulnerabilities and Attacks
Explore the world of network security vulnerabilities and attacks, including Denial-of-Service (DoS) and Distributed-Denial-of-Service (D-DoS), security flaws in the TCP/IP protocol suite, ICMP attacks, routing attacks, and TCP attacks. Learn about common security vulnerabilities such as address spo
0 views • 36 slides
Enhanced Distributed Channel Access (EDCA) for Non-Primary Channel in IEEE 802.11
Discussion on implementing EDCA for Non-Primary Channel Access (NPCA) in IEEE 802.11, focusing on mitigating frame collisions and enhancing medium efficiency. Various considerations for EDCA procedure on the Non-Primary Channel (NPCH) are explored to optimize channel access and reduce wastage. Topic
0 views • 13 slides
IEEE 802.11-23/1935r0 - Secondary Channel Usage Discussions
Explore the discussions on secondary channel usage in IEEE 802.11-23/1935r0, including topics like RU index, BW negotiation, avoiding medium synchronization loss, and single/multiple secondary backoff 20MHz channels. Discover insights on non-primary backoff 20MHz channel locations, transitioning del
0 views • 15 slides
Exploring Triangle Similarity and Congruence
This content delves into understanding triangle congruence and similarity through various scenarios and visual representations. It discusses how to determine congruence using side-side-side, side-angle-side, and angle-side-angle criteria, and explores the concept of similarity in triangles based on
0 views • 21 slides
Channel Generation Process for IEEE 802.11aj (45GHz) Based on Channel Measurement
This presentation by Haiming Wang and team from SEU/CWPAN discusses the process of channel realization and generation in the 45 GHz bandwidth. It covers the generation of the channel impulse response, modeling of parameters, statistical measurements, and future work related to the 802.11ad standard.
0 views • 27 slides
IEEE 802.11-15/0364: Channel Estimation Considerations in Wi-Fi Standards
Channel estimation in IEEE 802.11 standards, such as 11n, 11ac, and 11ax, is crucial for efficient MIMO systems. The noise impact during data reception affects the quality of the channel estimate, leading to SNR reduction post-equalizer. Techniques like channel smoothing and averaging of training se
0 views • 11 slides
Managing Channel Information for Wireless Communication Systems
This document from September 2015 discusses issues related to updating channel information in wireless communication systems, focusing on MU-MIMO and TxBF precoding techniques. It explains the challenges of channel aging, the importance of refreshing channel information, and the impact of different
0 views • 16 slides
Side Channel Monitoring in Additive Manufacturing for Cybersecurity and Quality Assurance
Side channel monitoring is crucial in the field of additive manufacturing to bridge cybersecurity and quality assurance. This process involves detecting physical domain data leakage through various side channels like acoustics, thermal, laser, vibration, electric current, optical, and pressure. By m
0 views • 10 slides
Side by Side Refrigerator in Pakistan: Best Picks for Spacious and Stylish Kitch
A Side by Side Refrigerator can be an exciting addition to modern kitchens that combine design space, efficiency, and space all in one piece. \/\/kinkedpress.com\/side-by-side-refrigerator-in-pakistan-best-picks-for-spacious-and-stylish-kitchens\/
1 views • 1 slides
Understanding Side Channels and Information Hiding Techniques in Advanced Information Assurance
This content covers various aspects of advanced information assurance, focusing on side channels and information hiding techniques such as digital watermarking, steganography, and covert channels. It discusses the concept of side-channel attacks, types of system and network channels, fault attacks,
0 views • 24 slides