Holistic Rating Training Requirements 2023-2024 by Texas Education Agency
Holistic Rating Training Requirements for TELPAS components for grades K-12 in Texas include calibration, basic training, and responsibilities for raters. Raters and verifiers are educators assigned to rate students eligible for special holistic administrations. Rater credentials mandate valid Texas
1 views • 36 slides
Mirai Botnet
The Mirai Botnet, created by Maneth Balasooriya and Jacob Gottschalk, is a notorious IoT botnet known for Distributed Denial-of-Service attacks on devices like IP cameras and DVRs. It originated from a Minecraft server protection racket and has been involved in major incidents. The botnet operates v
1 views • 8 slides
Overcoming the UX Challenges Faced by FIDO Credentials in the Faced by FIDO Credentials in the Consumer Space
Many websites are vulnerable to phishing attacks due to traditional authentication methods. To address this, the utilization of cryptographic authentication, such as key pairs, is recommended to enhance security and prevent MITM attacks.
0 views • 17 slides
NIH Data Management and Sharing Policy Overview
This content provides a detailed overview of the NIH Data Management and Sharing Policy, focusing on the importance of sharing scientific data, the scope of the policy, reasons for data sharing, application of the policy, and differences between Data Management Plans and Resource Sharing Plans. It a
2 views • 25 slides
Understanding the Importance of Data Sharing in Scientific Research
Data sharing plays a crucial role in scientific research to uphold transparency, reproducibility, and legitimacy. Skepticism of science due to fraud, publication bias, and challenges underscores the necessity for sharing confidential data. Professional associations, funding agencies, and journals ad
2 views • 39 slides
Bluetooth SIG September 2023 Update on Spectrum Sharing Plans
Bluetooth SIG provided an update on their actions and plans for sharing the 5 and 6 GHz bands with incumbents and unlicensed devices. They aim to collaborate with the Wi-Fi industry to enable equitable sharing for Bluetooth, particularly focusing on the 6 GHz band. The overall plan includes forming
4 views • 8 slides
Supreme Court Raps SBI For Not Sharing Complete Data On Electoral Bonds
Supreme Court Raps SBI For Not Sharing \"Complete Data\" On Electoral Bonds\n\nThe Supreme Court today came down hard on the State Bank of India for not sharing the complete data on electoral bonds, a scheme that allowed individuals and businesses to donate anonymously to political parties. The cour
2 views • 4 slides
Update on Bluetooth SIG's Spectrum Sharing Plans
This update discusses Bluetooth SIG's actions and plans for sharing the 5 and 6 GHz bands with incumbents and unlicensed devices. It highlights the goals, the overall plan, recent actions, and collaboration with the Wi-Fi industry to enable equitable sharing of these bands. The detailed plan involve
0 views • 9 slides
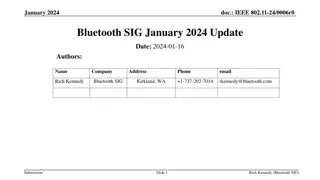
Update on Bluetooth SIG's Plans for Spectrum Sharing in January 2024
Bluetooth SIG presents an update on their actions and plans for sharing the 5 and 6 GHz bands with incumbents and unlicensed devices. Recognizing the need for future growth, they aim to collaborate with the Wi-Fi industry to develop optimal sharing mechanisms in the 6 GHz band. Their plan includes c
0 views • 11 slides
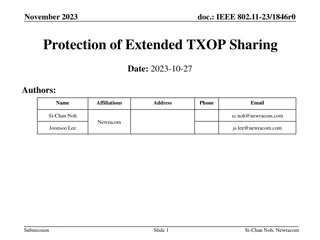
Protection of Extended TXOP Sharing in IEEE 802.11-23/1846r0
Reusing EHT's Triggered TXOP Sharing framework for extended TXOP sharing is discussed in this document, focusing on enabling sharing APs to distribute their obtained TXOP among other BSS(s). The document explores issues related to TXOP sharing for UHR STAs when a sharing AP allocates a portion of it
0 views • 12 slides
Understanding Market Sharing Cartel in Oligopolistic Markets
Market sharing cartels in oligopolistic markets involve firms entering agreements to share the market while retaining some autonomy in their operations. Two main methods are non-price competition and quota systems. Non-price competition involves firms agreeing on a common price to maintain profits w
0 views • 8 slides
Information Sharing Schemes and MARAM for Community Housing Organizations
These slides provide insights on information sharing schemes and the MARAM framework designed for community housing organizations to promote the wellbeing and safety of children, assess family violence risks, and enhance collaboration across service sectors. The Child Information Sharing Scheme (CIS
2 views • 15 slides
Enhancing Collaboration with User Stories Sharing Platform
Brief overview of a Jumpstart project involving a Sharing Platform prototype designed to address pain points related to transparency in sharing customer stories and feedback. User research insights and persona like Jane Smith, an Offering Manager, are highlighted to emphasize the need for an efficie
0 views • 26 slides
CNF-FSS and Its Applications: PKC 2022 March 08
Explore the Background, Applications, and Summary of CNF-FSS, focusing on Function Secret Sharing, Distributed Point Function, CNF Key-Sharing, and more. Learn about the efficiency of multiparty sharing and 1-out-of-3 CNF-FSS constructions for certain classes of functions. Discover how CNF Key-Shari
1 views • 33 slides
UVA Procedure for Managing Cost Sharing
The UVA Procedure for Managing Cost Sharing guides the handling of cost sharing at both proposal and award stages, ensuring compliance with sponsor requirements. It covers mandatory and voluntary cost sharing, tracking mechanisms, and third-party in-kind contributions, detailing the processes involv
0 views • 15 slides
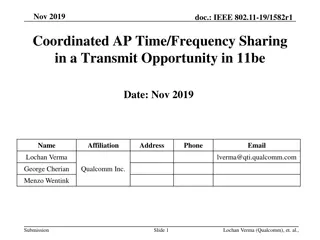
Coordinated AP Time/Frequency Sharing in IEEE 802.11be
The document discusses the concept of Coordinated AP (CAP) Time/Frequency Sharing within a Transmit Opportunity (TXOP) in the IEEE 802.11be standard. It explains the procedures of Frequency and Time resource sharing, highlighting the benefits such as latency improvement and throughput fairness. Deta
0 views • 16 slides
Safeguarding Your Digital Identity: Protecting Your Company's Most Valuable Asset
Cyber crime is escalating, with stolen credentials and compromised data being traded on the Dark Web. Small businesses are at high risk, yet many are unaware of being compromised. The human factor plays a critical role in password security. To combat these threats, consider utilizing Dark Web ID, a
0 views • 8 slides
Overview of TechCred Program in Ohio
TechCred.Ohio.gov provides information about the TechCred program in Ohio, which aims to help employers find the talent they need and offer opportunities for Ohioans to enhance their skills. The program has funded thousands of credentials for employers and individuals, with a focus on industry-recog
0 views • 15 slides
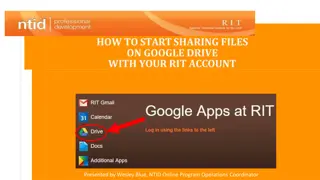
How to Start Sharing Files on Google Drive with Your RIT Account
Learn how to access Google Drive with your RIT account credentials, create folders and files, share them with specific individuals or a wider audience, and explore different sharing options. Consider the pros and cons of sharing links with anyone or assigning access to specific users. Find out about
4 views • 10 slides
Understanding Market Sharing Cartels in Oligopolistic Markets
Perfect collusion in oligopolistic markets often involves market-sharing cartels, where member firms agree to share the market while allowing some degree of freedom in their decisions. This can be done through non-price competition or quota agreements. Non-price competition cartels involve setting a
8 views • 8 slides
DevOps Certification Safari Exploring Lesser-Known but Powerful Credentials
In the dynamic world of DevOps, standing out requires more than just experience\u2014it requires the right credentials. While the well-known certifications provide a solid foundation, the lesser-known but powerful certifications explored in this safa
0 views • 10 slides
Guidance for CTE Pathway Credential Recommendation SB.123
The document outlines the requirements and processes related to career and technical education credentialing in Kansas, focusing on industry-sought credentials, high-value and standard credentials, and surveys conducted by the Kansas State Department of Education. It highlights the importance of app
0 views • 8 slides
Enhancing Diversity and Productivity Through Job Sharing in the Insurance Sector
Advertising roles as open to flexible working, including job sharing, is crucial for attracting diverse talent and reducing the gender seniority gap in the insurance industry. Job sharing benefits both employees and employers, increasing productivity and well-being. Evidence suggests that job sharin
0 views • 9 slides
Reflections on Sharing: The Rhythm of Life Advent Journey
Explore the theme of sharing through a series of images and reflections. Discover the joy of sharing your gifts with others and embrace the practice of giving back each day. Join in today's challenge to spread kindness and love through simple acts. Say a prayer for guidance in learning the art of sh
0 views • 8 slides
Enhancing Information Sharing in Australian Meat Supply Chains
This research delves into the value of information and information sharing within the beef and sheep meat supply chains in Australia. It explores the benefits of improved decision-making, reduced costs, and enhanced supply chain performance through strategic information sharing. The study also ident
1 views • 21 slides
Enhancing Career Opportunities for Youth with Disabilities in Virginia
This initiative in Virginia aims to create opportunities for youth with disabilities to explore careers in advanced manufacturing by implementing various programs such as academies, tours, credential fairs, and virtual information sessions. Over the years, the project has successfully served hundred
0 views • 20 slides
Exploring Secure Cooperative Sharing of Resources in Web Applications
This series of visual representations delves into the concept of secure cooperative sharing of JavaScript, browser capabilities, and physical resources in web applications. The images and descriptions cover topics such as web application security, browser functionality, and the principles of sharing
0 views • 22 slides
Addressing User Credentials and Security in CCSDS Service Interfaces
The discussion revolves around the need to define user credentials within CCSDS service interfaces for enhanced security. Various aspects such as the lack of specific specifications, authentication requirements, and proposed actions for securing service interfaces are highlighted. Suggestions includ
0 views • 11 slides
Guide to Logging in to SIRA UW with MAPFRE Credentials
Learn how to access SIRA UW platform using your MAPFRE credentials starting August 6th. Follow the steps for creating and resetting your password, ensuring a smooth login process. Utilize your MAPFRE username and be prepared to wait 10 minutes post password reset. Reach out to the dedicated support
0 views • 5 slides
Unlocking the Benefits of Job Sharing: Insights and Strategies
Discover the advantages of job sharing through insights from Beth Chaudhary, Head of Smart Energy Policy at BEIS. Learn why job sharing works, the key elements of a successful job share partnership, and real-world examples of smart and flexible job sharing practices in various organizations. Explore
0 views • 7 slides
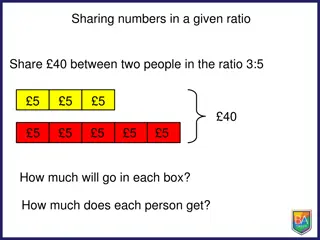
Ratio Sharing Practice Problems with Solutions
Solve various ratio sharing problems such as sharing numbers and sweets in given ratios between two people, finding equivalent ratios, and creating your own ratio sharing scenarios. Understand how to distribute quantities based on ratios and calculate each person's share accurately.
0 views • 9 slides
Determinants of Unlawful File Sharing: Insights and Implications
This comprehensive review delves into the determinants of unlawful file sharing behavior, exploring factors such as proximity to actual behavior, financial and legal considerations, and the impact on sales. It discusses the reasons behind illegal file sharing, including the influence of laws, pricin
0 views • 15 slides
Peer Learning Activities and Working Groups in Higher Education Qualifications Frameworks
Explore the upcoming peer-learning activities and working group discussions focusing on micro-credentials, qualifications frameworks, and ECTS in higher education. Discover key themes, such as the global approach to micro-credentials and the inclusion of micro-credentials in national qualification f
0 views • 11 slides
Advanced Techniques in Secret Sharing Schemes
Explore the advancements in polynomial secret-sharing schemes and their applications in cryptography. Discover how polynomial schemes provide efficient solutions for sharing secrets among multiple parties while maintaining security. Learn about the construction of polynomial conditional disclosure p
0 views • 16 slides
Enhancing Information Sharing: DISC and PISA Benefits
DISC (Dorset Information Sharing Charter) and PISA (Personal Information Sharing Agreement) facilitate improved information sharing among healthcare organizations in Dorset. DISC establishes robust principles for managing data flow and promoting best practices in information governance, while PISA t
0 views • 8 slides
Annual Report and Credentials Process Overview
The report from the Credentials Committee chaired by Jean-Philippe Billet highlights key committee members, deadlines for submissions, and statistics on credentials applications and annual reports. The document also provides insights into the recertification committee, responsibilities of program di
0 views • 23 slides
Ministry Sharing Information Session Overview
Explore the benefits and options of Ministry Sharing, a collaborative approach for sharing resources and personnel among congregations. Discover how Ministry Sharing can enhance affordability, stability, and the range of resources available for pastoral care, sacraments, and meetings. Consider vario
0 views • 17 slides
Tools and Techniques for Extracting Password Hashes and Credentials from Windows Systems
Explore various tools and scripts such as ESEDBXTRACT, GPPPFinder, and PowerShell scripts for extracting password hashes and credentials from Windows systems, including NTDS.dit and SYSTEM files, Group Policy Preferences, and more. Learn how to handle different Windows versions and access encrypted
0 views • 19 slides
Impact of Remittances on International Risk Sharing
Higher remittances in Emerging Market/Developing Economies (EMDEs) between 1990-2018 positively impact risk sharing between consumption and income growth, unlike other types of capital flows. Remittances contribute significantly to enhancing risk-sharing effects, offering about 15% of risk sharing i
0 views • 12 slides
Credentialing Requirements for Faculty and Teaching Assistants in Undergraduate Studies
Credentialing for instructors in the Division of Undergraduate Studies ensures adequate preparation to teach assigned courses, aligning with institutional accreditation standards. Policies and procedures are outlined for faculty and staff members, including TAs, emphasizing the need for specific qua
0 views • 17 slides