Ascon: The Lightweight Cryptography Standard for IoT
The November 2023 document IEEE 802.11-23/2069r2 discusses the importance of secure data storage and communication in IoT devices due to the increasing number of connected devices and potential security threats. It introduces Ascon as a lightweight cryptography standard selected by NIST for protecti
0 views • 26 slides
Lightweight Cryptography Standard for IoT - November 2023 IEEE Presentation
IEEE 802.11-23/2069r1 presents Ascon as a lightweight cryptography standard for IoT devices. With the increasing number of connected devices, protecting data on IoT devices becomes crucial. NIST selects Ascon to safeguard small devices, offering authenticated encryption and hashing efficiently. Asco
3 views • 26 slides
Understanding SHA-256 Algorithm and History
SHA-256 is a secure hashing algorithm that produces 256-bit hash values and is more secure than MD5, SHA-0, and SHA-1 due to fewer collisions. Created in 2001 by the NSA, it is widely used in various applications like cryptocurrency, SSL certificates, and blockchain. This summary provides insights i
0 views • 17 slides
Best Acupuncture in Tanjong Pagar
If you\u2019re looking for an Acupuncture in Tanjong Pagar, contact La Guerison TCM Pte Ltd \u7597\u6108\u4e2d\u533b. They offer many services promoting overall well-being and healing. They specialize in various TCM therapies including tuina massage, acupuncture, cupping, TCM ear-picking services, G
0 views • 6 slides
Get the Best Acupuncture in Tanjong Pagar
Get the Best Acupuncture in Tanjong Pagar at Healing Health TCM Therapy Pte Ltd! Specializing in Health, Beauty & Body Wellness, their team of registered TCM physicians and skilled therapists are dedicated to providing top-quality medical consultation and treatments. They offer a range of services i
0 views • 6 slides
Caterpillar Cat 416E BACKHOE LOADER (Prefix SHA) Service Repair Manual Instant Download
Please open the website below to get the complete manual\n\n\/\/ \n
0 views • 32 slides
Caterpillar Cat 416E BACKHOE LOADER (Prefix SHA) Service Repair Manual Instant Download
Please open the website below to get the complete manual\n\n\/\/
0 views • 32 slides
Overview of Cryptography Techniques and Algorithms
Exploring the diverse realm of cryptography, this chapter delves into both nonmathematical and mathematical encryption methods. It covers substitution and transposition ciphers, steganography, hybrid systems, hashing, symmetric algorithms like DES and AES, as well as asymmetric algorithms utilizing
7 views • 21 slides
Cryptographic Hash Functions in Data Security: Mustansiriyah University Course Overview
Cryptographic hash functions play a crucial role in ensuring data integrity and security. This course at Mustansiriyah University's Faculty of Engineering covers the SHA-512 algorithm and its applications in various fields such as message authentication, digital signatures, and intrusion detection.
0 views • 6 slides
Maximizing HDL Repository Management Efficiency with Hog Toolset
Explore the benefits of using Git for HDL repositories with Hog toolset. Ensure reproducibility and absolute control of HDL files, constraint files, and settings. Learn how to embed Git SHA into firmware registers automatically for traceability. With Hog, developers can integrate version control sea
1 views • 22 slides
Overview of Git Commit Workflow
Explore the Git Commit Workflow, including commands like git log, git diff, git status, git add, git commit, and git show. Learn about the importance of the .git folder in a repository and how to identify commits using their SHA-1 hashes.
0 views • 23 slides
Kompetisi Fungsi Hash NIST (SHA-3): Proses Pemilihan Finalis dan Detail Desain
Seperti sejarah AES, National Institute of Standards and Technology (NIST) menyelenggarakan kompetisi terbuka untuk mengembangkan fungsi hash baru yang disebut SHA-3. Kompetisi ini diadakan dari tahun 2007 hingga Oktober 2012. Proses pemilihan terdiri dari 2 putaran dan babak final dengan total 64 s
0 views • 17 slides
Freelance digital marketing strategist in Calicut
Iam Febin Sha Freelance Digital Marketing strategist in Calicut,Kerala,India I build Custom Websites that are both Playful and Efficient and I help Grow your business With Creative Solutions \n\/\/febinsha.com\/\n
0 views • 8 slides
Computer Forensics: Capturing and Verifying Evidence
This guide focuses on the process of capturing and verifying digital evidence in computer forensics. Topics include creating forensic images of hard drives, using forensically sound methods, imaging internal hard drives, utilizing hardware write blockers, different types of forensic images, hashing
0 views • 28 slides
Best Practices for Secure Password Storage - OWASP Foundation Guidelines
Learn about secure password storage techniques recommended by OWASP Foundation, including adding salt, slowing down hashing functions, using HMAC isolation, and imposing difficult verification processes on attackers. Remember to use proper encoding, avoid limiting password types or lengths unreasona
0 views • 10 slides
Cryptographic Algorithms and Hash Collisions Overview
Explore the world of cryptographic algorithms and hash collisions. Learn about various hashing algorithms like MD5, SHA-1, SHA-256, and more. Dive into the concepts of symmetric and asymmetric key algorithms and understand the risks associated with hash collisions. Discover the implications of post-
0 views • 58 slides
Comparative Analysis of Health Systems: Insights from SHA and Irish Health Policy
This policy researcher's perspective delves into the key roles of SHA and Irish health policy, exploring similarities, differences, and the relationship between expenditure levels, service provision, financing patterns, and health outcomes. Through detailed analyses, the paper highlights the importa
0 views • 9 slides
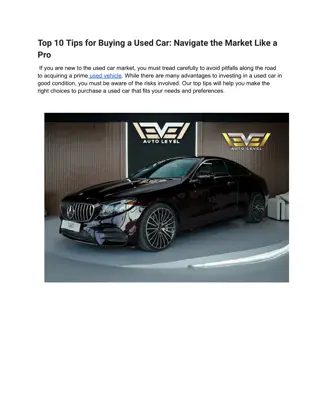
Top 10 Tips for Buying a Used Car_ Navigate the Market Like a Pro
Purchasing a used car can be an excellent investment, offering value for money and a wide variety of options. However, navigating the used car market requires caution to avoid potential pitfalls. Whether you\u2019re buying in Abu Dhabi, Dubai, or Sha
0 views • 4 slides
Expert Guide_ Top 10 Tips for Buying a Used Car Like a Pro
Purchasing a used car can be an excellent investment, offering value for money and a wide variety of options. However, navigating the used car market requires caution to avoid potential pitfalls. Whether you\u2019re buying in Abu Dhabi, Dubai, or Sha
0 views • 4 slides