Airport Security Market to be Worth $25.27 Billion by 2031
\u00ae, the airport security market is projected to reach $25.27 billion by 2031, at a CAGR of 8.6% from 2024 to 2031. Some of the major factors driving the growth of this market are stringent government regulations for airport security and the growing number of air passengers. In addition, increasi
6 views • 5 slides
KEERTHI SECURITY - Best Security Agencies In Bangalore
Keerthi Security is a security and facility management services provider in Bangalore. We are committed to offering top-notch security services for commercial and residential places. We aim to offer very secure and reliable security services to everyone. Our best-trained security guards are very sha
9 views • 11 slides
Overview of Enforcement Initiatives and Outcomes at National Conference of Enforcement Officers
Delve into the insights shared at the National Conference of Enforcement Officers on 4th March 2024, focusing on enforcement initiatives such as National Special Drive, actions by the Centre and State, technology interventions, and policy changes. Uncover details on fake billing structures, motives
3 views • 32 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
0 views • 6 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
1 views • 6 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
1 views • 6 slides
National Conference of Enforcement Chiefs: Enhancing Tax Compliance and Enforcement Practices
The National Conference of Enforcement Chiefs held by the Commercial Taxes Department, Government of Andhra Pradesh, focused on nurturing tax compliance, targeting evasion cases, preventing harassment, and overseeing tax administration to curb high-pitch demands. The enforcement wing emphasized data
0 views • 16 slides
Understanding the Role of Security Champions in Organizations
Security Champions play a vital role in decision-making concerning security engagement, acting as a core element in security assurance processes within a team. They foster a security culture, reduce dependency on the CISO, and promote responsible autonomy and continuous security education in the org
3 views • 13 slides
Occupational Safety and Health Enforcement in Nigeria: Challenges and Recommendations
This paper discusses the enforcement of occupational safety and health (OSH) regulations in Nigeria, highlighting the key issues affecting compliance and suggesting ways to improve enforcement. The study emphasizes the importance of maximum enforcement and organizational compliance with OSH regulati
2 views • 23 slides
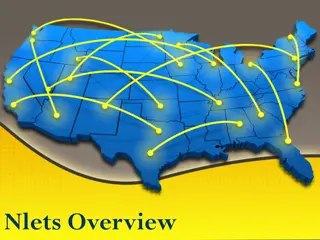
Nlets - Connecting Law Enforcement Across States
Nlets, established in the mid-60s, is a vital interstate communications system linking law enforcement agencies across 50 states, D.C., territories, and federal agencies for secure data exchange. It is crucial for law enforcement, justice, and public safety missions. Nlets differs from NCIC and is g
0 views • 21 slides
Understanding the Roles of a Security Partner
Learn about the roles and responsibilities of a Security Partner, including requesting changes to security roles, approving security requests, and initiating access requests. Explore the overview of Workday Security, the security access request process, and the pre-request process flow. Discover how
1 views • 17 slides
Enforcement of Aviation Safety Regulations: Policies and Procedures
Industry actions should resolve safety issues; enforcement by CAA if needed. CAA empowered to take actions like limitations, revocations, penalties. Enforcement ensures compliance with laws, regulations, and standards. Clear policies for effective, fair, and transparent enforcement. Aim is to mainta
2 views • 11 slides
Understanding Fines Enforcement Registry and Court Processes
The Fines Enforcement Registry, operating under the Sheriff's directorate, enforces infringements and court fines in accordance with the Fines, Penalties, and Infringement Notices Enforcement Act 1994 (WA). The Registrar's discretion is limited, and clients must follow specific procedures to dispute
0 views • 19 slides
The Global Code of Digital Enforcement: Embracing Innovation in Justice
The Global Code of Digital Enforcement introduces modern concepts and principles to govern the use of digital technology in enforcing court decisions. It promotes a balanced enforcement system by addressing the impact of digitalization on enforcement professionals and offering guidelines on e-enforc
0 views • 18 slides
Virginia State Police Gaming Enforcement Coordinator
The Office of the Gaming Enforcement Coordinator within the Virginia State Police Bureau of Criminal Investigation is responsible for coordinating the enforcement of gaming laws in the Commonwealth. They collaborate with various state agencies, federal law enforcement, and provide outreach and educa
0 views • 9 slides
Understanding Homeland Security Stakeholders and Preparedness
Homeland security is defined by stakeholders from government, non-government, academics, private sector, and communities. It involves securing physical spaces, American values, and way of life. The importance of a local approach with dedicated Homeland Security Officers is highlighted to improve pre
0 views • 13 slides
Insights into Joint Purchasing Alliances in Competition Enforcement
Review the main characteristics, benefits, and potential issues related to joint purchasing alliances in the context of competition enforcement. Delve into the scope of activities, geographical considerations, potential benefits supported by economic evidence, and enforcement records regarding joint
0 views • 11 slides
Enforcement & Compliance Presentation to New CA Employees
This presentation by Daniel K. Waturu, a Telecoms Specialist at AFRALTI, focuses on discussing various aspects related to enforcement and compliance in the ICT sector, including dealing with technological challenges, improving ICT laws, suggesting enforcement models, qualities of an effective enforc
0 views • 7 slides
Understanding Security in World Politics
Security studies delve into the intricate processes of defining and addressing security threats in global politics. It explores the contested nature of security definitions, emphasizes the political significance of security, and challenges the conventional boundaries of International Relations. The
0 views • 8 slides
MEHA Body Art Enforcement Presentation Summary
In the "MEHA Body Art Enforcement Presentation of 3-16-2016," the implementation by Deborah Garcia focuses on reporting social media unlicensed body art facilities, cost estimates for tattoo equipment and supplies, legal affairs communications, and the agencies involved in Michigan's enforcement eff
0 views • 14 slides
2020 State Legislation on Law Enforcement Use of Force: Impact & Trends
The Senate Study Committee on Law Enforcement Reform highlights legislation enacted by 14 states in 2020 regarding law enforcement use of force. Common themes include restricting chokeholds, requiring peace officers to intervene and report excessive force, bodycams, and managing demonstrations. Spec
0 views • 8 slides
Simplifying Middlebox Policy Enforcement Using SDN
Middlebox management is a complex task for network operators, with challenges in security, performance, and compliance. This research explores how Software-Defined Networking (SDN) can simplify middlebox management by enforcing middlebox-specific steering policies through a centralized controller. T
0 views • 27 slides
Strategies for Combatting Charity Fraud: Insights and Enforcement Approaches
Explore key enforcement issues in combating charity fraud, including areas of authority, common enforcement focuses, fundraising methods regulated, enforcement approaches, and inter-office cooperation. Gain insights into regulatory efforts to protect consumers and charitable contributions.
0 views • 33 slides
Comprehensive Course Review: Security Research Cornerstones at Carnegie Mellon University
Dive into the essential topics of software security, network security, OS security, and cryptography in the course offered by Vyas Sekar at Carnegie Mellon University. Explore control flow hijacks, cryptography terminology, and the importance of network security in protecting data transmissions. Lea
0 views • 41 slides
UIC Security Division Overview and International Activities
The UIC Security Division plays a crucial role in supporting the security platform of the International Union of Railways (UIC). Headed by Jacques Colliard, the division is based in Paris and consists of key personnel like Marie-Hélène Bonneau, Jos Pires, and Laetitia Granger. The division's activ
0 views • 12 slides
Transparent and Efficient CFI Enforcement with Intel Processor Trace
This research discusses Control Flow Integrity (CFI) enforcement to combat control flow hijacking attacks. It explores methods for runtime CFI enforcement, including instrumented checking and transparent monitoring. The study delves into trace mechanisms, buffer management strategies, and when to tr
0 views • 32 slides
Utah Division of Water Rights Enforcement Procedures Overview
Utah Division of Water Rights underwent changes in enforcement procedures in 2005, granting the State Engineer direct enforcement authority. The new statutes and rules outline powers for enforcement actions in cases of water violations, non-compliance with orders, and safety concerns. Enforcement ac
0 views • 33 slides
Automating Security Operations Using Phantom
Isabella Minca, an intern for 4 months in the Security Team at Adobe, presents an overview of automating security operations using Phantom. The presentation covers goals, security alerts, Phantom playbooks, handling security data, and the capabilities of Phantom in orchestrating security responses.
0 views • 28 slides
Understanding HTTP Security Headers for Web Apps
Explore the importance of HTTP security headers on web applications through a detailed breakdown of headers like HSTS, XFO, XSS, CSP, CTO, RH, and FP. Learn how these headers enhance security by instructing browsers on handling website content, preventing various attacks. Gain insights on configurin
0 views • 68 slides
Law Enforcement and School Activities Report - November 2022
In November 2022, law enforcement activities recorded various incidents, including theft, assault, drug offenses, and more. Criminal investigations in November 2022 revealed cases related to theft, assault, sex offenses, and other crimes. Additionally, schools were actively focused on administrative
0 views • 15 slides
New Generation Network Security System Evolution and Implementation
The presentation outlines the evolution of network security systems, focusing on the transition from traditional firewalls to next-generation systems like intrusion detection systems. It highlights the limitations of current systems in detecting internal threats and the need for advanced solutions t
0 views • 9 slides
OSHA Enforcement Update - MACOSH Washington, DC Summary
OSHA's Enforcement Update discussed various initiatives including the Severe Violator Enforcement Program (SVEP), Novel Cases, and enforcement strategies for ergonomics and workplace violence. The presentation highlighted statistics on SVEP cases, novel enforcement cases, ergonomic inspections, and
0 views • 27 slides
Guide to Law Enforcement Career: Recruitment Strategies & Qualities
Evaluating employment agencies, desired qualities of law enforcement officers, challenges in finding qualified applicants, and effective recruiting strategies are essential elements of a successful law enforcement recruitment process. The Law Enforcement Recruitment Toolkit provides valuable insight
0 views • 34 slides
Modular Security Analysis for Key Exchange and Authentication Protocols
Explore the modular security analysis approach used to examine the security of key exchange and authentication protocols, focusing on the universally composable authentication with a global Public Key Infrastructure. The analysis involves splitting the system into smaller components, separately anal
0 views • 15 slides
Comprehensive DevOps Security Training Overview
This Certified DevOps Security Practitioner course provides a deep dive into implementing DevSecOps, integrating security into the DevOps processes. Covering topics like security testing, Docker security, automation, and more, the training aims to equip participants with the necessary skills to embe
0 views • 5 slides
Exploring Careers and Education in Law Enforcement Pathway
Discover various careers in law enforcement such as Border Patrol Agent, FBI Agent, and Police Officer. Understand the roles of individuals in enforcing laws, investigating crimes, and ensuring public safety. Learn about certifications and educational pathways for a successful career in law enforcem
0 views • 6 slides
Comparative Study of Law Enforcement and Military Efforts in Homeland Security
This comparative study delves into the perceived militarization of American law enforcement and its implications for homeland security efforts. It explores differing missions, approaches, government forms, threats, and efforts to minimize militarization, highlighting the blurring line between milita
0 views • 23 slides
Understanding Security Testing and Architecture
Explore the fundamentals of security testing, computer security goals, software security approach, and security architecture. Learn about securing computer assets, verifying trustworthiness of security mechanisms, and validating security architecture through threat modeling. Enhance your knowledge o
0 views • 57 slides
Simplifying Middlebox Policy Enforcement Using SDN
Middlebox management is a challenging task for network operators due to its complexity and cost. This research explores how Software-Defined Networking (SDN) can streamline middlebox policy enforcement, making it more efficient and easier to manage. By centralizing control and incorporating market v
0 views • 26 slides
Underground Storage Tank Enforcement Update - October 2, 2019
The Underground Storage Tank Enforcement Update provides information on current enforcement cases, types of enforcement cases, and status definitions for Enforcement Action Requests (EARs) and Orders. It includes details on the number of EARs received, active EARs, and status definitions for EARs an
0 views • 9 slides