Unlocking the Secret to Healthy Locs: The Power of Wild Growth Hair Oil
Discover the transformative benefits of wild growth hair oil for your locs. Rich in essential nutrients, this potent formula nourishes the scalp, promotes hair growth, and strengthens locs from root to tip. Say goodbye to dryness and breakage as you unlock the secret to healthier, more vibrant locs
2 views • 2 slides
WhatsApp Direct Message
With the greatest \"WhatsApp Direct Message\" app that we've brought to you, which allows users to message random numbers without needing to save them. While this feature may offer convenience for users who frequently communicate with unknown contacts.
8 views • 22 slides
The Truth of Righteousness by Faith Message in Laodicean Context
Understanding the significance of righteousness by faith message is crucial for Christians, especially in today's Laodicean condition. The message emphasizes justification through faith in Christ, leading to obedience to God's commandments and holy living. Encouraging believers to seek righteousness
0 views • 35 slides
Craft the Best WhatsApp Business Greeting Message Guide.
Read about the WhatsApp Business greeting message: tips and best examples to craft the perfect WhatsApp Business greeting message.\n
0 views • 7 slides
Steganography: Hiding Secrets in Plain Sight
Steganography, the art and science of concealing secret messages in such a way that no one suspects their existence, differs from cryptography in its goal of avoiding suspicion rather than rendering the message unreadable. This method involves hiding messages within seemingly innocuous data, such as
2 views • 76 slides
An Easy Way to Craft a 2024 Quick Message
\"Creating a quick message that stands out in 2024 requires brevity, relevance, and personalization. Ensure the subject line is concise and grabs the reader's attention. Be sure to keep the message short, focusing on the recipient's needs or interests. Engagement can be enhanced with emojis and visu
1 views • 5 slides
RPO Hiring Services The Secret to Building High-Performance Teams
RPO Hiring Services The Secret to Building High-Performance Teams
1 views • 4 slides
RPO Hiring Services The Secret to Building High-Performance Teams
RPO Hiring Services The Secret to Building High-Performance Teams
0 views • 4 slides
Traffic Analysis and Forensic Investigation Puzzle
In this scenario, Anarchy-R-Us suspects that their employee Ann is a secret agent leaking the company's secret recipe. By analyzing network traffic using Wireshark, specific questions are posed regarding Ann's activities, such as identifying her IM buddy and the contents of transferred files. The in
0 views • 21 slides
Unlock the Secrets of Ancient Egyptian Hieroglyphs with Fun Activities
Delve into the world of Ancient Egyptian hieroglyphs through engaging activities like decoding the names of Egyptian gods and creating a secret message in hieroglyphs. Explore the BBC website for more information, and even learn how to make tea-stained paper to mimic papyrus. Share your creations wi
0 views • 12 slides
Accessing Electronic Case Documents via mySocialSecurity Message Center
Learn how to access your electronic case documents through the mySocialSecurity Message Center. Follow these steps: sign in to mySocialSecurity, verify your cell phone number, enter the security code, agree to the terms, select messages, open the message, and click to view the PDF document. Retrieve
0 views • 8 slides
Guide to Using the EPR Message Centre for Electronic Patient Records
Learn how to efficiently navigate and utilize the Message Centre in the Electronic Patient Record (EPR) system for managing workflow, signing off letters, reviewing results, and handling notifications. Accessible through Cerner Millennium, the Message Centre allows healthcare providers to electronic
0 views • 45 slides
Comprehensive Guide to Message Evaluation, Testing, and Provisioning System (MVPS)
Explore the Message Evaluation, Testing, and Provisioning System (MVPS) used by the Center for Surveillance, Epidemiology, and Laboratory Services. MVPS streamlines data collection, collaboration, and provision of timely and accurate data, enhancing public health goals. Learn about the Components of
2 views • 13 slides
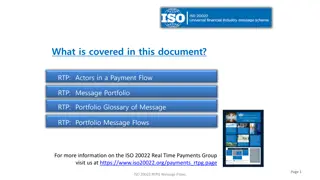
Real-Time Payments: Actors and Message Flows Overview
This document provides an overview of the actors involved in a payment flow and the message portfolio in Real-Time Payments (RTP). It includes details on various actors like Instructing agent, Forwarding agent, Ultimate Debtor, Reimbursement agents, and more. The provided message flows illustrate th
1 views • 12 slides
Using Chaos to Send Secret Messages
Chaos is a fundamental concept in creating secret messaging systems using deterministic systems with sensitive initial conditions. By implementing chaotic behavior in electrical circuits known as the "Talker" and "Copycat," messages can be encoded and decoded based on chaotic attractors and synchron
0 views • 21 slides
CNF-FSS and Its Applications: PKC 2022 March 08
Explore the Background, Applications, and Summary of CNF-FSS, focusing on Function Secret Sharing, Distributed Point Function, CNF Key-Sharing, and more. Learn about the efficiency of multiparty sharing and 1-out-of-3 CNF-FSS constructions for certain classes of functions. Discover how CNF Key-Shari
1 views • 33 slides
Understanding Sender, Message, Receiver Correspondence in Communication Process
Communication process involves sender, message, and receiver elements. The sender initiates communication, generates a message, and conveys it to the receiver. The message is encoded, transmitted through a channel, and decoded by the receiver. Noise can hinder the communication process by interferin
1 views • 13 slides
Understanding Message Passing in Distributed Systems
Explore the key concepts of message passing in distributed systems, covering inter-process communication, desirable features like simplicity, efficiency, and reliability, different methods for information sharing, and the importance of synchronization and buffering. Dive into the intricacies of enco
0 views • 68 slides
Understanding Internet Mail Architecture Components
The Internet mail architecture consists of key components including Message User Agents (MUA), Mail Submission Agent (MSA), Message Transfer Agent (MTA), Mail Delivery Agent (MDA), and Message Store (MS). These components work together to facilitate the sending, receiving, and storing of email messa
6 views • 4 slides
Understanding the Impact of Message Creation on Communication Processes
The process of communication begins with creating a message, which can significantly influence how it is received. Messages, conveyed through words, signs, or sounds, are interpreted by receivers based on the sender's delivery. Littlejohn (2018) emphasizes the importance of how senders initiate comm
1 views • 9 slides
Introduction to Cryptography: The Science of Secure Communication
Cryptography is the study of methods for sending and receiving secret messages securely. This lecture explores the application of number theory in computer science, focusing on the design of cryptosystems like public key cryptography and the RSA cryptosystem. The goal of cryptography is to ensure th
0 views • 53 slides
Round-Efficient Byzantine Broadcast Under Strongly Adaptive and Majority Corruptions
This paper discusses a round-efficient Byzantine broadcast protocol that addresses strong adaptive adversaries and majority corruptions. The protocol involves unique and unbreakable peer signatures, committees for message verification, and time-locking mechanisms to prevent message tampering. By uti
1 views • 5 slides
Implementing Your Budget & Message for Effective Media Partnership
This presentation delves into the crucial aspects of implementing a budget and crafting a message for effective collaboration with media partners. Learn how to strategize your spending across different outlets, work with media sales representatives to maximize audience reach, and identify the best t
0 views • 13 slides
Understanding Public Key Cryptosystems in RSA Encryption
Public key cryptosystems, like RSA, use two keys for encryption and decryption, with one key made public and the other kept secret. This asymmetric system allows secure communication, where the encryption key (E) is used to encrypt messages into ciphertext (C), which can only be decrypted back to th
0 views • 11 slides
Understanding Message Passing Models in Computer Science
Message passing models in computer science involve concepts like producer-consumer problems, semaphores, and buffer management. This content explores various scenarios such as void producers and consumers, as well as the use of multiple semaphores. The functions of message passing are detailed, high
0 views • 50 slides
The Importance of Secret Prayer in the Life of Jesus
Discover how Jesus emphasized the significance of secret prayer through instances from the Scriptures where He retreated to solitary places for intimate communion with the Father. These moments of seclusion enabled Him to deepen His relationship with God, teaching us the value of private prayer for
0 views • 26 slides
Unveiling Lily Owens' Struggles in "Secret Life of Bees
Delve into Lily Owens' journey as she navigates a web of lies for self-preservation in "Secret Life of Bees" by Sue Monk Kidd. Witness Lily's desperate attempts to hide her past, protect her newfound sanctuary, and grapple with the fear of losing her newfound family.
0 views • 6 slides
Secure Two-Party Computation and Basic Secret-Sharing Concepts
In today's lecture of "Foundations of Cryptography," the focus is on secure two-party and multi-party computation, emphasizing semi-honest security where Alice and Bob must compute without revealing more than necessary. Concepts such as real-world vs. ideal-world scenarios, the existence of PPT simu
0 views • 27 slides
Impact of Message Execution on Advertising Effectiveness
The impact of a message in advertising is not just about what is said, but also how it is said. Different cultures and ads have varying approaches, with some focusing on rational positioning while others appeal to emotions. The choice of headlines and copy can significantly influence the effectivene
0 views • 11 slides
Legal Battle: Monkey.See vs. Peach.Inc - Trade Secret Dispute
Monkey.See, a startup founded by Cornelius Heston, faces a legal battle against Peach.Inc and its former engineer Simon Zaius. The lawsuit involves allegations of trade secret misappropriation, unjust enrichment, and patent infringement, leading to a complex legal dispute and substantial damages sou
0 views • 18 slides
Advanced Techniques in Secret Sharing Schemes
Explore the advancements in polynomial secret-sharing schemes and their applications in cryptography. Discover how polynomial schemes provide efficient solutions for sharing secrets among multiple parties while maintaining security. Learn about the construction of polynomial conditional disclosure p
0 views • 16 slides
Dwelling in the Secret Place: Unveiling Wisdom and Trust
Psalm 91 presents profound wisdom, guiding believers to abide in God's protection through intimate communion, concentration, and confession. Embracing the truth that God is their refuge and fortress, the psalmist transitions from a general declaration to a personal confession of trust. This sermon s
0 views • 7 slides
Early Church Message and Format in Acts of the Apostles: Kerygmata by C. H. Dodd
The early church's message and format in Acts of the Apostles, particularly focusing on the kerygmata as elucidated by C. H. Dodd, with references to Acts 2:14-39 and 3:12-26. Explore the challenges to the kerygmata and the adaptation of the Christian message to various audiences. Additionally, insi
0 views • 17 slides
IPC Lab 2 MessageQ Client/Server Example
This MessageQ example demonstrates the client/server pattern using SYS/BIOS heap for message pool, anonymous message queue, and return address implementation. The example involves two processors - HOST and DSP, where the DSP processor acts as the server creating a named message queue, and the HOST p
0 views • 12 slides
Advances in Functional Encryption for Secure Data Handling
Explore the evolution from Cryptomania to Obfustopia through Secret-Key Functional Encryption, Public-Key Encryption, and the power of Secret-Key Functional Encryption. Discover the significance of different encryption schemes such as Public-Key Functional Encryption, Secret-Key Functional Encryptio
0 views • 36 slides
Understanding Message Passing Interface (MPI) Standardization
Message Passing Interface (MPI) standard is a specification guiding the development and use of message passing libraries for parallel programming. It focuses on practicality, portability, efficiency, and flexibility. MPI supports distributed memory, shared memory, and hybrid architectures, offering
0 views • 29 slides
Bulk SMS Providers in Australia [August 2024 Price Comparison]
Bulk text message pricing varies among SMS bulk providers. The cost of sending a bulk text message can be influenced by several factors, including the volume of messages being sent, the length of the message, and the destination country.
0 views • 7 slides
Bulk SMS Providers in Australia [August 2024 Price Comparison]
Bulk text message pricing varies among SMS bulk providers. The cost of sending a bulk text message can be influenced by several factors, including the volume of messages being sent, the length of the message, and the destination country.
0 views • 7 slides
Understanding Password-Protected Secret Sharing for Enhanced Data Security
Exploring the concept of password-protected secret sharing, this content delves into Shamir's Secret Sharing, ElGamal Public Key Encryption, and the importance of securing sensitive information with robust schemes. It highlights the challenges of offline attacks, properties of secret sharing, and th
0 views • 22 slides
Partial Key Exposure Attacks on BIKE, Rainbow, and NTRU
Explore the vulnerability of PQC candidates to partial key exposure attacks in schemes like BIKE, Rainbow, and NTRU. Learn about leakage resistance, modeling leakage, practical bounds, and secret key decoding methods. Dive into the erasure and error models, analyzing the security of secret keys in v
0 views • 19 slides































![Bulk SMS Providers in Australia [August 2024 Price Comparison]](/thumb/245322/bulk-sms-providers-in-australia-august-2024-price-comparison.jpg)
![Bulk SMS Providers in Australia [August 2024 Price Comparison]](/thumb/245325/bulk-sms-providers-in-australia-august-2024-price-comparison-245325.jpg)

