Scam / Fraud Awareness & Prevention
Learn about common scams, basic steps to avoid scams, and how to protect yourself from cyber scams, IRS scams, and charity scams. Stay vigilant and prevent fraud in your daily life.
0 views • 10 slides
Phishing and Social Media Scam Protection | Scam Killnet Switch
The best online parental control tool is Scam Killnet Switch; protect your family against phishing and social media scams. Watch out for your family members while they play around on the internet. Your online interactions are kept safe by our cutting-edge technology, which recognises and stops harmf
3 views • 2 slides
Recognizing Online Scams and Seeking Support
Understanding the nature of online scams and learning how to identify them is crucial in protecting oneself from cyber threats. This lesson covers the tactics used by scammers such as phishing, smishing, and vishing, along with ways to spot scam emails or messages. It also emphasizes the importance
1 views • 30 slides
Protect Yourself: Identifying and Avoiding Scams
Learn how to recognize scams, understand why they work, explore types of scams, and discover warning signs to build defenses against scammers. Explore the profiles of scammers, how they find victims, and the emotional tactics they use. Find out about various scams such as giveaways, imposter scams,
0 views • 23 slides
Protect Your Community: National Slam the Scam Day
Help spread awareness and fight against government imposter scams on March 7, 2024. Join the initiative to #SlamTheScam during National Consumer Protection Week and learn how to detect and report suspicious activities. Utilize the provided templates to share valuable information on social media plat
2 views • 18 slides
Understanding Blood Groups and Their Significance
Human blood types are determined by specific antigens and antibodies present on red blood cells, influencing crucial aspects like blood transfusions and familial relationships in forensic medicine. The ABO system, with its four main blood types (A, B, AB, O), plays a vital role in categorizing blood
7 views • 14 slides
Scams Awareness Week 2021: Real or Fake Scam Radar Activity
This post discusses Scams Awareness Week 2021 and presents an interactive activity to test your scam radar. It includes images where you have to distinguish between real and scam content. Additionally, it highlights the role of Scamwatch in combating scams, recent scam trends like phishing and inves
1 views • 26 slides
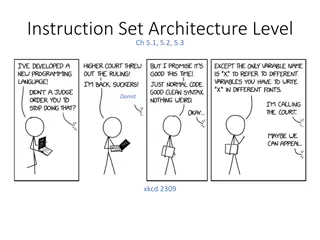
Understanding Instruction Set Architecture and Data Types in Computer Systems
In computer architecture, the Instruction Set Architecture (ISA) level is crucial in defining how a processor executes instructions. This includes the formal defining documents, memory models, registers, and various data types that can be supported. The ISA level specifies the capabilities of a proc
2 views • 13 slides
Understanding Hotel Classification and Types
Hotel classification and types cover various aspects such as facilities, services, amenities, guest types, and factors influencing hotel classification. From resort hotels to airport hotels and city center accommodations, each hotel type serves different purposes and caters to diverse guest preferen
0 views • 44 slides
Business Email Compromise (BEC) Overview
Explore the ins and outs of Business Email Compromise (BEC) - from common attacks and end goals to ways to secure Office 365 with multi-factor authentication and audit logging. Understand who is affected by BEC and discover methods to detect and mitigate this type of scam targeting companies.
0 views • 20 slides
Comprehensive Guide to Wound Care: Types, Dressings, and Practices
Understanding wound care is crucial for proper healing. This guide covers types of wounds, purposes of wound dressing, different dressing types, and helpful practice guidelines. Learn about intentional and unintentional wounds, dressing purposes like protection and absorption, and types of dressings
1 views • 10 slides
Phishing Survival Guide: How to Recognize and Respond to Suspicious Emails
Learn how to spot a phishing email and what steps to take if you receive one or fall victim to a phishing scam. Find out how to identify suspicious links, recognize phishing attempts, and protect yourself from giving out personal information or losing money. Stay informed and secure in the digital a
2 views • 5 slides
Hamster Kombat Scam Alert_ How to Protect Your Investments
Hamster Kombat Scam Alert: How to Protect Your Investments
5 views • 3 slides
Understanding Contract Types and Incentives Under ProTech
Explore the factors influencing contract types selection, including price competition, cost analysis, and technical capability. Learn about different contract types like fixed-price and cost-reimbursable, each with unique characteristics and risks. Discover the spectrum of contract types and incenti
0 views • 21 slides
Best Binary Options Forex Crypto Scam Recovery 2024
RHS provides a reliable recovery solution for victims of binary options, forex, and crypto scams. Their dedicated team works tirelessly to recover stolen funds and hold scammers accountable. By following their tips and seeking professional advice, in
0 views • 15 slides
How To Recover Money Lost To Binary Options Broker Scam
Fraudsters steal hundreds of millions of pounds from innocent victims every minute using various methods such as phishing links and bogus investment schemes. That is why Recuva Hacker Solutions , a Cyber organized foundation, is equipped with sophist
0 views • 15 slides
Beware of the Fake Government Agency Scam: Protect Yourself from Fraud
The Fake Government Agency Scam involves fraudsters posing as government officials to extort money from victims under false pretenses. They use convincing tactics, demand immediate payment in various forms, and try to keep victims on the phone throughout transactions. Learn how to recognize and prot
0 views • 8 slides
How to Recover Your Money from Binary Options Scam: Ultimate Guide
Binary options trading has gained significant attention in recent years as an easy form of online trading involving stocks, currencies, commodities, and indices. However, with its popularity has come a surge in binary options scams. In 2019 alone, re
0 views • 15 slides
Recover Lost Funds From Binary Options Fraud Brokers
Are you a victim of a binary options fraud? You can fight back and recover your funds. Report to MychargeBack today! We have helped thousand of binary options fraud victims to get their money back. You can get your funds back from binary options scam
0 views • 15 slides
What is the best way to recover my stolen Bitcoin wallet?
If you've fallen victim to a Bitcoin scam, recovering your stolen funds can be a daunting task. However, with the right steps and the assistance of a professional recovery company, you can increase your chances of success. Here is a guide to help you
0 views • 15 slides
How can I recover my money from a fake bitcoin investment website?
The rise of Bitcoin and other cryptocurrencies has unfortunately led to an increase in fraudulent investment websites. If you find yourself a victim of such a scam, it's crucial to act quickly and methodically to recover your funds. Here\u2019s a ste
0 views • 15 slides
Scammed bitcoin recovery made easy with Recuva Hacker Solutions
Recuva Hacker Solutions is an exceptional service that deserves every bit of praise it receives. As a user who experienced the devastating consequences of a crypto scam, I can attest to the sheer brilliance and professionalism displayed by Recuva Hac
0 views • 15 slides
Recover Money Lost In Binary Options Scams Cryptocurrency Scams
Losing your cryptocurrency to a scam can be a devastating experience. However, recovering your stolen cryptocurrency is possible with the right approach and assistance. One reliable option is using the services of Recuva Hacker Solutions. Here's a co
0 views • 15 slides
Beware of the Grandparent Scam - Protect Yourself from Fraud
The Grandparent Scam is a prevalent form of fraud where scammers impersonate a grandchild in distress, seeking financial assistance. The criminals exploit emotions and pressure victims into sending money through various means. Learn how to spot and avoid falling victim to this scam to safeguard your
0 views • 9 slides
Romance Scams: A Growing Threat in Chesterfield
The Chesterfield Police Department investigated 45 reports of scams and frauds in 2020, resulting in over $1.5 million in losses. One prevalent scam discussed in the slides is Romance Scams, where suspects build fraudulent online relationships to exploit victims emotionally and financially. The susp
0 views • 9 slides
Join the Fight Against Scam Calls with Free Call Blocker Units! #ScamAware #CallBlocker
Engage with the 2023 Call Blocker Project by Friends Against Scams to combat scam and nuisance calls effectively. Use the suggested posts to spread awareness, share resources, and empower your community to protect themselves. Help your loved ones secure their landlines with free call blocker units a
0 views • 15 slides
Exploring C Program Refinement Types with Liquid Types and Invariant Discovery
Discover the integration of Liquid Types and Refinement Types in C programming through Invariant Discovery, leading to automatically adapting C programs to fit Liquid Types. Explore challenges and solutions in expressing invariants, handling unknown aliasing, and implementing strong updates within t
0 views • 24 slides
Atlas HR eServices - Leave Types and Application Procedures
This content provides detailed information on various leave types and application procedures within the Atlas HR eServices platform. It covers topics such as Jury Duty Leave, Compensatory Day Off, Floating Holiday (NY), Official Business, Rest & Recuperation, along with guidelines on how to apply fo
0 views • 12 slides
Unpacking the Punjab National Bank Scandal: Insights into the Nirav Modi Case
Delve into the intricate details of the Punjab National Bank scam involving Nirav Modi and company, shedding light on the Letter of Undertaking, SWIFT system, Core Banking System, key players, modus operandi, control failures, post-scam measures, and valuable lessons learned. Explore the dimensions
0 views • 17 slides
Unveiling the Truth Behind a Suspiciously Cheap Mobile Kitchen Deal
A series of images and text unveil a questionable mobile kitchen offer found online for $4,599, compared to industry averages of $50,000-$180,000. Further investigation reveals a similar trailer from another dealer for $2,399 and a custom-made trailer from a company in Virginia. The content prompts
0 views • 9 slides
Beware of the Lottery Scam: Protect Yourself from Fraud
The Chesterfield Police Department investigated numerous scams in 2020, including the lottery scam which targets victims by falsely claiming they have won a large sum of money. The scammers manipulate victims into paying processing fees and taxes, ultimately leading to financial loss. It is crucial
0 views • 9 slides
Beware of the Puppy Scam: Protect Yourself from Online Fraud
Scams involving online puppy sales have led to significant financial losses for victims in Chesterfield. Fraudulent breeders advertise puppies on fake websites, offering enticing deals that turn out to be scams. Victims are asked to make online payments for the puppy and additional fees for shipping
0 views • 9 slides
Understanding Java Data Types and Variable Declaration
Dive into the world of Java data types and variable declaration with this comprehensive guide. Learn about primitive data types, declaring variables, integer types, floating-point data types, character data type, and boolean data type. Master the art of assigning names and data types to efficiently
0 views • 31 slides
Cybersecurity Awareness: Phishing Investigations Practitioner Notes and Game Instructions
This content focuses on teaching children to identify phishing tactics used by individuals and organizations through activities and lesson notes. It emphasizes recognizing scam attempts, understanding safe online practices, and evaluating suspicious messages. The interactive game instructions instru
0 views • 4 slides
Exposing Scams and Frauds: Unveiling the Dark Side of Hustling
This content delves into the shady world of hustling, shedding light on scams, frauds, and deceptive practices aimed at cheating individuals out of their money. It aims to raise awareness and educate readers on various hustles such as the WiFi Scam, Credit Card Scam, and Bluetooth Scam. Through imag
0 views • 4 slides
Data Types, Expressions, and Operators in Java
This resource provides information on data types, expressions, and operators in Java. It covers topics such as data types (int, double, String, boolean), operator precedence, and practice problems to work on expressions and types. The content includes announcements, reminders, a recap of data types,
0 views • 20 slides
Understanding Haskell Types, Classes, Functions, and Polymorphism
In Haskell, types are collections of related values, ensuring type safety through compile-time type inference. Type errors occur when functions are applied to arguments of the wrong type. Annotations help define types, and Haskell offers basic types like Bool, Char, String, Int, Integer, Float, and
0 views • 30 slides
Understanding Types and Classes in Haskell Programming
Types in Haskell are names for collections of related values, allowing for safer and faster programs by catching errors at compile time. Haskell supports basic types like Bool, Char, String, Int, Integer, and Float, as well as list and tuple types. Type errors occur when functions are applied to arg
0 views • 27 slides
Introduction to Python Data Types, Operators, and Expressions
Understanding data types, expressions, and operators is fundamental in Python programming. Learn about Python's principal built-in types such as numerics, sequences, mappings, and classes. Explore numeric types, strings, and their operations like concatenation, escape sequences, and conversions betw
0 views • 20 slides
Safeguarding Devices and Edge Computing: A Responsive Anti-Scam Approach
The article discusses the prevalence of scamming in the digital landscape, emphasizing the financial harm and security risks it poses. It explores the challenges in detecting scam messages, particularly in short messaging platforms, and proposes a comprehensive and adaptive strategy to address this
0 views • 20 slides