Algorithm Analysis
Algorithm analysis involves evaluating the efficiency of algorithms through measures such as time and memory complexity. This analysis helps in comparing different algorithms, understanding how time scales with input size, and predicting performance as input size approaches infinity. Scaling analysi
1 views • 30 slides
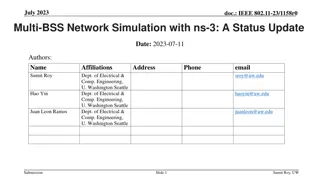
Multi-BSS Network Simulation in ns-3 with IEEE 802.11-23 Update
A status update on the WiFi module in ns-3 for IEEE 802.11-23 focusing on advancements like new protocol features, AI/ML integration, and runtime improvements for multi-BSS networks. The simulations cover throughput benchmarks, multi-BSS scenarios, interference parameters, and validation against ana
13 views • 33 slides
Line Segment Intersection
Geometric intersections play a crucial role in computational geometry for tasks such as solid modeling, collision detection in robotics, and overlaying subdivisions in geographic information systems. The problem of line segment intersection involves finding all intersection points between a set of c
0 views • 17 slides
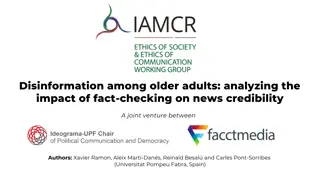
Impact of Fact-Checking on Credibility Among Older Adults
Analyzing the impact of fact-checking on news credibility among older adults reveals that age is a key factor in information credibility. Older adults tend to give more credibility to various kinds of information, leading to potential challenges in discerning between true facts and false news. Fact-
5 views • 31 slides
BTR: Binary Token Representations for Efficient Retrieval Augmented Language Models
Retrieval-augmented language models like BTR address issues such as hallucination by providing efficient solutions for encoding input passages and queries. By utilizing cacheable binary token representations, BTR offers a unique approach to decomposing and binarizing passage encoding to improve runt
0 views • 9 slides
Exploring 'Checking Out Me History' - A Poem Analysis Quiz
Unravel the layers of "Checking Out Me History" through a 10-question quiz delving into themes of identity, historical figures, and the narrator's sentiments towards education and heritage. Discover the hidden messages and insights within this powerful poem.
0 views • 12 slides
Overview of .NET Framework and CLR Architecture at Amity School of Engineering
Explore the .NET Framework and Common Language Runtime (CLR) architecture at Amity School of Engineering & Technology, covering topics such as .NET components, technical architecture, common language runtime, CLR execution model, and more. Discover the support for multiple languages and the .NET lan
0 views • 28 slides
Dynamic Memory Allocation in Computer Systems: An Overview
Dynamic memory allocation in computer systems involves the acquisition of virtual memory at runtime for data structures whose size is only known at runtime. This process is managed by dynamic memory allocators, such as malloc, to handle memory invisible to user code, application kernels, and virtual
0 views • 70 slides
Understanding Exceptions in Computer Science
Errors in programming, such as syntax, semantic, runtime, and logical errors, can disrupt the execution of a program. Syntax errors relate to grammatical violations, semantic errors occur when statements lack meaning, and runtime errors happen during program execution due to illegal operations. By i
1 views • 35 slides
Overview of Subprograms in Software Development
Subprograms in software development provide a means for abstraction and modularity, with characteristics like single entry points, suspension of calling entities, and return of control upon termination. They encompass procedures and functions, raising design considerations such as parameter passing
4 views • 25 slides
Quality Improvement Cycle: Plan, Do, Check, Act (PDCA)
The Quality Improvement Cycle follows the PDCA framework, involving planning, implementing, checking, and acting to continuously enhance processes. It begins with defining customer requirements, implementing processes effectively, checking for issues, and taking action to resolve any problems. The c
1 views • 6 slides
Understanding Debugging in Programming
Debugging is a crucial aspect of programming to identify and fix errors that can cause program failures, hangs, or unexpected results. There are different types of errors such as compile errors, runtime errors, and logic errors, each requiring a different approach to resolve. Learning about the mode
0 views • 20 slides
Runtime Checking of Expressive Heap Assertions
Motivated by the unreliability of large software systems due to concurrency bugs and limitations of static analysis, the goal is to enable runtime analysis of deep semantic properties with low overhead. This involves checking expressive heap assertions at runtime with minimal impact on performance,
0 views • 15 slides
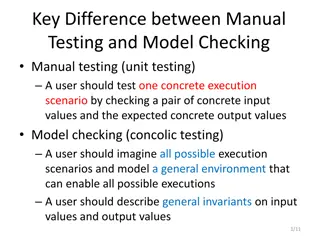
Difference Between Manual Testing and Model Checking
Manual testing focuses on testing specific scenarios with concrete inputs and outputs, while model checking involves imagining all possible scenarios to create a general environment for testing. In manual testing, users test specific execution scenarios, whereas in model checking, users envision and
2 views • 4 slides
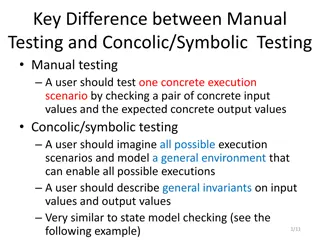
Difference Between Manual Testing and Concolic/Symbolic Testing in Software Development
Manual testing involves checking concrete input and output values for specific execution scenarios, while concolic/symbolic testing requires imagining all possible scenarios and modeling a general environment. General invariants on input and output values are described, similar to state model checki
0 views • 4 slides
Event Log Alignment for Conformance Checking
Approach based on ILP for aligning event logs and process models, ensuring multi-perspective conformance checking. Examples illustrate trace executions with and without problems, utilizing Petri Nets with data. Alignments between log and process traces are analyzed, showing the existence of multiple
0 views • 21 slides
Understanding .NET Framework Architecture and Common Language Runtime
This content delves into the intricacies of .NET architecture, highlighting its structure, common language runtime, and key components such as Common Type System (CTS) and Common Language System (CLS). It explains how .NET supports multiple languages, facilitates cross-language interoperability, and
0 views • 13 slides
Implementing Heaps: Node Operations and Runtime Analysis
Understanding the implementation of heaps involves knowing various node operations like finding the minimum node, last node, next open space, children, and parent. The runtime analysis of heap operations such as peekMin, removeMin, and insert are crucial for optimizing performance. This recap covers
0 views • 9 slides
Dynamic Memory Management Overview
Understanding dynamic memory management is crucial in programming to efficiently allocate and deallocate memory during runtime. The memory is divided into the stack and the heap, each serving specific purposes in storing local and dynamic data. Dynamic memory allocators organize the heap for efficie
0 views • 31 slides
Context-Aware Identification of Check-worthy Claims in Political Discussions
This work explores the intersection of man and machine in countering malicious communication in social networks, focusing on fact-checking in political discussions. The research investigates the need for technology to verify the accuracy of public figures' statements, considering the thriving field
0 views • 21 slides
Exploring Architecture and Challenges of Proof Assistants
Explore the architecture of proof assistants, discussing the use of tactics, formal proofs, and the difficulty in utilizing these tools. Discover the contribution of a new architecture for proof assistants, addressing extensibility and error checking, with a focus on soundness guarantees. Delve into
0 views • 41 slides
Bounded Satisfiability Checking for Early Legal Compliance Verification
Early verification of legal compliance is crucial to avoid consequences such as violating regulations like GDPR. Through bounded satisfiability checking using Metric First-order Temporal Logic (MFOTL), this research focuses on system design verification for regulatory compliance. The study addresses
0 views • 29 slides
Essential Guide to Opening and Managing a Checking Account
Learn the importance of opening a checking account, the process of choosing a bank, criteria to consider, and the steps to open an account. Understand the different services offered by banks and the key factors to keep in mind when selecting a financial institution. Discover the benefits and require
0 views • 39 slides
Differential Assertion Checking and Relative Correctness in Software Verification
Differential assertion checking compares two similar programs to identify errors, while relative correctness ensures all assertions pass, highlighting failed assertions. The content discusses the challenges and benefits of these techniques in software verification, with examples of correct and buggy
0 views • 17 slides
Divide & Conquer Approach to Model Checking
Addressing the state space explosion issue in model checking, this work by Canh Minh Do, Yati Phyo, and Kazuhiro Ogata introduces a divide & conquer approach focusing on until and until stable properties. The research extends techniques to handle these properties effectively, emphasizing mitigation
2 views • 17 slides
Understanding the Decision-Making Process of Checking Behaviors Among Doctors and Patients
Recent research by Ido Erev from Technion and University of Warwick, along with Alvin E. Roth and others, explores the coexistence of insufficient and over-checking behaviors among individuals, including doctors and patients. The study delves into the factors influencing checking decisions, highligh
0 views • 24 slides
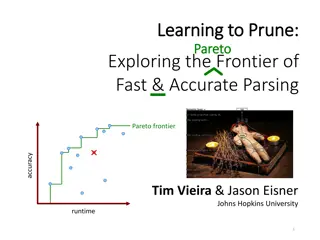
Exploring Fast & Accurate Parsing With Learning to Prune
In this informative content, the concept of learning to prune is discussed in the context of exploring the frontier of fast and accurate parsing. It delves into the optimization tradeoff between runtime and accuracy in end-to-end systems, showcasing a Pareto frontier of different system performances
0 views • 42 slides
MATLAB Workshop: Graphs, Runtime Analysis, and Plotting Techniques
MATLAB Workshop Part 3 delves into the creation of 2D and 3D plots, along with advanced plotting commands, runtime analysis using tic and toc functions, and the utilization of the MATLAB profiler. The content demonstrates techniques for plotting multiple curves, creating subplots, and visualizing da
0 views • 22 slides
Understanding Runtime Recovery of Web Applications under Zero-Day ReDoS Attacks
This detailed content discusses the critical issue of Runtime Recovery of Web Applications facing Zero-Day ReDoS Attacks. It delves into the significance of regular expressions (regex) in handling HTTP requests, highlighting vulnerabilities and real-world impacts. The research emphasizes the severit
0 views • 31 slides
Inferential Statistics Solutions for Challenging Problems in Section B
The provided statistical problems in Section B involve calculating the expected number of shoppers spending specific durations at a furniture shop and reasons for not checking the weight of each packet when filling corn flakes. Solutions include determining the shoppers expected to spend more than 4
0 views • 25 slides
Transparent and Efficient CFI Enforcement with Intel Processor Trace
This research discusses Control Flow Integrity (CFI) enforcement to combat control flow hijacking attacks. It explores methods for runtime CFI enforcement, including instrumented checking and transparent monitoring. The study delves into trace mechanisms, buffer management strategies, and when to tr
0 views • 32 slides
Input Elimination Transformations for Scalable Verification and Trace Reconstruction
This work introduces new input elimination techniques for scalable model checking in industrial applications, focusing on trace reconstruction. The transformations aim to make the netlist more tractable for solving, involving various algorithms such as retiming, phase abstraction, and bitwidth reduc
0 views • 27 slides
Conflict Checking Process in Heraldry: Armory 104 Overview
Delve into the intricacies of conflict checking using the ordinary in heraldry with Armory 104. Explore prerequisites, review key concepts, understand where SCA-registered armory is located, and learn the process of identifying and analyzing charge groups to ensure uniqueness in designs. Avoid commo
0 views • 28 slides
Efficient Job Scheduling and Runtime Management in DLWorkspace Cloud Computing and Storage Group
Explore the intricate system of job scheduling and runtime management in DLWorkspace, involving SQL server, K8s Master API, Web Portal, Restful API, Cluster Manager, NVIDIA driver plugins, and shared storage. Learn about the process flow from job submission to approval, status monitoring, and device
0 views • 11 slides
Understanding CILK: An Efficient Multithreaded Runtime System
CILK is a multithreaded runtime system designed to develop dynamic, asynchronous, and concurrent programs efficiently. It utilizes a work-stealing thread scheduler and relies on a directed acyclic graph (DAG) model for computations. With a focus on optimizing critical paths and total work, CILK enab
0 views • 44 slides
Subtyping and Type Checking in Programming Language Design
In the realm of programming language design, subtyping and type checking play crucial roles. This content delves into how syntax-directed rule systems evolve when dealing with subtyping, presenting the challenges and the solutions through a recursive algorithm approach. The discussion includes the t
0 views • 40 slides
Understanding Exception Handling in Object-Oriented Programming
Exception handling in object-oriented programming enables a program to manage and recover from exceptional situations during runtime errors. Java uses exceptions to represent errors, allowing methods to throw exceptions that can be caught and handled by the caller, thus separating error detection an
0 views • 21 slides
Understanding Python Exceptions for Handling Runtime Problems
Exceptions in Python are essential for handling runtime problems and preventing programs from crashing unexpectedly. By using try-except blocks, developers can catch and manage exceptions that occur during program execution, ensuring smooth functioning. Learn how to effectively utilize exceptions to
0 views • 15 slides
Orthogonal Vectors Conjecture and Sparse Graph Properties Workshop
Exploring the computational complexity of low-polynomial-time problems, this workshop delves into the Orthogonal Vectors Problem and its conjectures. It introduces concepts like the Sparse OV Problem, first-order graph properties, and model checking in graphs. Discussing the hardness of problems rel
2 views • 22 slides
Streamlining Technical Processing for Library Services
In the technical processing workflow of a library, utilizing tools like copy cataloging macros can significantly improve efficiency and accuracy. This involves checking for copy cataloging status, running fix routines, and updating catalog records. While these macros offer benefits such as saving ti
0 views • 17 slides