Understanding Ethereum Token Standards: ERC-20, ERC-721, and ERC-1155
Delve into the world of blockchain, cryptocurrencies, and decentralized technologies with a focus on Ethereum token standards ERC-20, ERC-721, and ERC-1155. Learn about the differences between fungible and non-fungible tokens, smart contracts, and examples of popular tokens in the space. Explore how
0 views • 9 slides
Update on Computing and IAM Service Developments in WLCG/HSF Workshop
Details about the update campaign for HTCondor CEs, APEL support for tokens, and IAM service developments presented at the WLCG/HSF Workshop on May 14, 2024. Highlights include HTCondor CE upgrades, APEL support discussions, and advancements in IAM services for LHC experiments.
1 views • 12 slides
Exploring Helium: A Decentralized IoT Network Revolution
Delve into the world of Helium, a blockchain-based IoT network revolutionizing connectivity. Managed by a community of crypto investors, this global network offers innovative solutions for telecom industry challenges through decentralized deployment and mining of HNT tokens.
0 views • 17 slides
Real World Asset Tokenization in Blockchain Technology
Tokenization of real-world assets in blockchain technology digitizes physical assets into blockchain tokens, increasing liquidity, transparency, and accessibility by transforming traditional markets through fractional ownership and automated smart contracts.
1 views • 9 slides
Layer 2 Token Marketing Services
Layer-2 token marketing promotes tokens built on scalable layer-2 solutions, highlighting benefits like faster transactions and lower fees. Get connected with our experts today and launch a lucrative \ntoken platform.
0 views • 3 slides
Comprehensive School Quality Assurance and Evaluation Process
A detailed insight into the Quality Assurance Department's role in school evaluation and improvement processes, including Whole School Evaluation (WSE), Follow-through initiatives, Teaching and Learning assessments, Resumption and Examination Monitoring. The process involves both internal self-evalu
1 views • 20 slides
Expand Advantages with Hamster Tokens on Hamster Trade
Hamster Trade on Message is a progressive decentralized cryptographic money exchanging stage that consolidates the comfort of virtual entertainment with cutting-edge blockchain innovation. Clients benefit from secure, minimal expense exchanges, impro
0 views • 4 slides
Token Economies and Behaviour Modification in Custody: Evaluating Efficacy
This article explores the application of token economies in prisons as a behaviour modification technique based on operant conditioning. Token economies involve exchanging tokens for desired behaviours, aiming to replace undesirable actions with positive reinforcement. The use of increments, consist
0 views • 19 slides
Managing Risks and Leveraging Opportunities in Digital Asset Space
Explore the dynamics of crypto compliance in the Caribbean region, delving into blockchain technology, remote work trends, algorithm challenges, and the transformation of tech and tokens. Discover how the financial services sector navigates risks and harnesses opportunities in the digital asset land
1 views • 10 slides
ELECTRA: Pre-Training Text Encoders as Discriminators
Efficiently learning an encoder that classifies token replacements accurately using ELECTRA method, which involves replacing some input tokens with samples from a generator instead of masking. The key idea is to train a text encoder to distinguish input tokens from negative samples, resulting in bet
0 views • 12 slides
Understanding JSON Web Tokens (JWT) in Web Development
JSON Web Tokens (JWT) are a simple and commonly used type of token that is self-contained, meaning the data is stored within the token itself. They consist of three parts: Header, Payload, and Signature. JWTs are signed by the server using a secret key, allowing clients to read the data without bein
3 views • 6 slides
California LifeLine Third Party Administrator Presentation Summary
The California LifeLine Third Party Administrator presented to the ULTS Administrative Committee on September 20, 2022. The presentation covered results of preemptive recertification, renewal process resumption data, updates on the CalFresh Confirm Hub, and success stories related to program improve
0 views • 21 slides
Secure Access to OAuth-Based Services in HTCondor Jobs
Enhance the security of HTCondor job submissions by leveraging OAuth tokens for secure access to file storage services. Learn how the Credd and Credmon architecture facilitates the management and secure transfer of credentials, ensuring sensitive data remains protected during job execution.
0 views • 23 slides
Scouts Queensland Roadmap for Resumption of Face-to-Face Scouting
Scouts Queensland has released a roadmap for the gradual resumption of face-to-face scouting activities in stages, aligning with the easing of COVID-19 restrictions by the Queensland Government. The roadmap outlines specific restrictions, general guidelines for gatherings, equipment use, distances,
0 views • 8 slides
Enhancing Library Accessibility: Request Alternate Formats for Print Disabled Users
This project focuses on providing accessible library services for print-disabled users by allowing them to request alternate formats, reducing their workload and promoting awareness of available services. The workflow involves users accessing the library website, logging in with ACE tokens, populati
1 views • 24 slides
SHAKEN and STIRed: Current State of Anti-Spoofing and Robocall Mitigation
Exploring the challenges and efforts in combatting robocalls and caller spoofing in the telecommunications industry, focusing on restoring trust in voice networks through initiatives like SHAKEN (Secure Handling of Asserted information using toKENs) and STIR (Secure Telephone Identity Revisited). Th
0 views • 22 slides
Expression Tree Construction: Building Fully Parenthesized Expression Trees
In the process of building expression trees, nodes are inserted based on operators and operands, creating a fully parenthesized expression. The construction involves parsing the expression, inserting new nodes as tokens are examined, and linking nodes accordingly. By following the steps for handling
0 views • 17 slides
California LifeLine Third Party Administrator Presentation Summary
California LifeLine Third Party Administrator presented on June 28, 2022, highlighting the Renewal Process Resumption and Improvements. Pre-emptive recertification has benefitted 350,345 subscribers, representing 28.56% of active LifeLine subscribers. The process includes distributing anniversary da
0 views • 25 slides
Dumping Data from Alma Using PERL and the Alma Analytics API
Learn how to extract data from Alma using PERL programming language and the Alma Analytics API. Get insights on API calls, required parameters, optional parameters like setting row limits, and using resumption tokens for handling large data sets efficiently.
0 views • 16 slides
Project Fox: A Statically Typed Embeddable Programming Language Overview
Project Fox is a captivating journey into the development of a statically typed, embeddable programming language. Explore how the compiler and interpreters work, from source code to tokens and Abstract Syntax Trees, culminating in code generation. Dive into the nuances of semantic analysis and learn
0 views • 11 slides
Introduction to Lex and Yacc: Compiler Design Essentials
Lex and Yacc are essential tools in compiler design. Lex serves as a lexical analyzer, converting source code to tokens, while Yacc is a parser generator that implements parsing based on BNF grammars. Through these tools, strings are processed, and code is generated for efficient compilation. This i
0 views • 10 slides
Understanding Scanner Class in Java: Reading User Input and Processing Files
The Scanner class in Java's java.util package allows reading input from the keyboard or files. It looks for tokens in the input, reads different types of values, and has methods like nextInt() and nextLine(). You can also read from files by creating a File object. Learn how to use Scanner to interac
0 views • 21 slides
Understanding User Identity and Access Tokens in Windows Security
Delve into the intricate world of user identity and access tokens in Windows security. Explore how user identities are represented, the structure of access tokens, and the significance of processes running under different user contexts. Gain insights into advanced Windows security principles and lea
1 views • 13 slides
Understanding C++ Parallelization and Synchronization Techniques
Explore the challenges of race conditions in parallel programming, learn how to handle shared states in separate threads, and discover advanced synchronization methods in C++. Delve into features from C++11 to C++20, including atomic operations, synchronization primitives, and coordination types. Un
0 views • 48 slides
Analysis of US National Security Issues on the Korean Peninsula
The polling data addresses various crucial questions related to US national security and the Korean Peninsula, including the potential resumption of military exercises in South Korea, readiness of US troops, North Korea's neutron bomb capability, leadership strategies, and alliance considerations. I
0 views • 12 slides
Evolution of Numerical Systems: From Pale Blue Dot to Babylonian Numbers
Tracing back to the Pale Blue Dot photograph of Earth, discover the evolution of numerical systems from scratch marks on bones to sophisticated Babylonian base-60 system. Sumerians used tokens for counting, leading to the birth of arithmetic, while Babylonians utilized a positional number system. Ex
0 views • 41 slides
Disaster Recovery Operations and Maintenance Overview
Organizations face key challenges in disaster recovery operations, such as widespread disruptions affecting various levels, communities, and suppliers. Prompt reactions and preparedness are essential to navigate through the phases of a disaster recovery plan - preparation, response, recovery, resump
1 views • 48 slides
Emergency Preparedness Plan for Saskatchewan Legislative Library
Enhance and revise emergency preparedness plan for the Saskatchewan Legislative Library by aligning with strategic priorities, enhancing response procedures, defining roles and responsibilities, and incorporating recognized standards. Training and research phases cover developing effective plans, ri
0 views • 32 slides
California LifeLine Third-Party Administrator Presentation Key Statistics and Results
The presentation provides a detailed overview of the renewal processes and results for the California LifeLine program, including statistics on renewal process resumption, renewal approval decisions, renewal rates, and impact on subscribers. Key data covers the periods from July 1, 2022, to March 3,
0 views • 22 slides
California LifeLine Third-Party Administrator Renewal Process Analysis
The presentation focuses on the renewal process statistics and progress of the California LifeLine program, emphasizing recertification rates and outcomes. It discusses the resumption statistics, national verifier's impact, and catchup period analysis in achieving renewal success rates. The data and
0 views • 27 slides
Community Prayers and Blessings for Town Pastors in Felixstowe
Community prayers and blessings were shared on the occasion of 15 years of town pastors in East Anglia. The celebration highlighted the impact of kind acts, new ways to serve, and fostering relationships towards peace on the streets. The upcoming resumption of patrols in Felixstowe was prayed for, a
0 views • 10 slides
Occupational Therapy Guidelines for Adults Undergoing Total Hip Replacement
This practice guideline from the Royal College of Occupational Therapists focuses on occupational therapy intervention for adults undergoing total hip replacement. It outlines evidence-based recommendations to maximize functional independence, reduce anxiety, support role resumption, prevent readmis
0 views • 23 slides
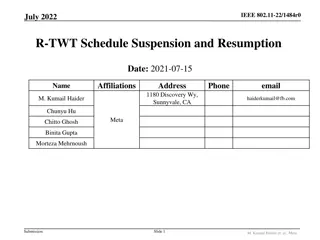
IEEE 802.11-22/1484r0 - R-TWT Schedule Suspension and Resumption
For supporting latency-sensitive traffic, the IEEE 802.11-22/1484r0 standard discusses the suspension and resumption of R-TWT schedules. It explores existing signaling for TWT suspension/resumption in R-TWT operation, identifies gaps, and proposes enhancements. The document addresses TWT Information
0 views • 12 slides
Understanding Session Management Challenges in Web Applications
Session management is crucial in web applications to maintain user authentication and authorization. This presentation delves into the evolution of session management, highlighting issues with HTTP authentication, the use of session tokens, and challenges in storing and securing session data. Variou
0 views • 18 slides
Reactive Tokens and Prosodic Features in Korean Conversation Analysis
This study delves into Reactive Tokens (RTs) and their role in Korean conversation, focusing on prosodic cues that elicit RT usage. It explores RT placement, differing functions, and the impact of boundary tones on RT utilization. Data collected through telephone conversations between young male spe
0 views • 20 slides
Understanding LL(1) Grammars and Computing First & Follow Sets
Exploring LL(1) grammars and the computation of First and Follow sets for non-terminals. This involves defining FIRST(.) as the set of tokens that appear as the first token in strings derived from a non-terminal and FOLLOW(A) as the terminals that can appear immediately to the right of A in the sent
0 views • 33 slides
Animal Facility Operations Resumption Guidelines Amid SARS-CoV-2 Pandemic
Amid varying impacts of the SARS-CoV-2 pandemic on animal research facilities, guidelines have been issued to help resume normal operations. Emphasis is on ensuring animal care, staff health, and effective separation of research and care activities through strategies like social distancing and PPE u
0 views • 15 slides
Integrating Hashicorp Vault with HTCondor for Secure Oauth Credential Management
Exploring the use of token-based authentication over X.509 certificates for improved security in HTCondor workflows. The transition to tokens offers enhanced control and flexibility, with a focus on utilizing JWTs and Scitokens. Leveraging Hashicorp Vault alongside HTCondor streamlines the managemen
0 views • 18 slides
Understanding Differences Between Federal and State Death Sentences
Exploring the absence of executions in North Carolina from 1976 to 1984, this analysis delves into factors affecting the resumption of executions and the history of death penalty sentencing in the state. Additionally, it distinguishes federal and state death sentences, shedding light on the distinct
0 views • 35 slides
Enhancing Security with Two-Factor Authentication (2FA) at University Library
Explore the implementation of Two-Factor Authentication (2FA) at the University Library for heightened security measures. This comprehensive system involves hardware tokens, mobile devices, and temporary passcodes, ensuring secure access to sensitive data and systems. Learn about the processes and r
0 views • 9 slides