Enhancing Cybersecurity with Bluedog VAPT Services
Bluedog Security Monitoring offers essential cybersecurity services, including Vulnerability Assessment and Penetration Testing (VAPT). Their automated VAPT combines External Vulnerability Scanning and WebApp Scanning to provide comprehensive testing solutions that help businesses prioritize risks,
0 views • 16 slides
The Basic Principles of Surveying for Building and Structural Projects
Surveying plays a crucial role in ensuring accurate positioning and alignment of structures such as buildings, bridges, and roads. This article delves into the definition of surveying, stages in the surveying process including reconnaissance, field work and measurement, and office work. Understandin
1 views • 60 slides
Convoy Commander Certification Program Overview
The Convoy Commander Certification Program introduces the agenda, requirements, duties, and responsibilities of convoy commanders in detail. It covers aspects such as conducting risk assessments, safe driving practices, operational hazards, and convoy planning procedures. The program emphasizes the
7 views • 35 slides
The Battle of Vimy Ridge in the First World War
The Battle of Vimy Ridge in 1917 was a significant event where all 4 Canadian Divisions joined forces, marking a historic victory and symbolizing the birth of Canada. The battle was a breakthrough for Britain and France, as Vimy Ridge was a crucial German stronghold that had resisted previous attack
10 views • 22 slides
Insights into Application Security Testing and Best Practices
Dive into the world of application security testing with a seasoned practitioner's advice and musings. Explore the basics, types of testing, initial steps like reconnaissance, user inputs, test cases, attack strategies, and useful tools. Learn about code reading techniques and key hints for securing
0 views • 27 slides
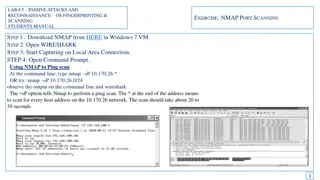
Passive Attacks and Reconnaissance using NMAP for Network Scanning
Learn how to use NMAP for passive attacks and reconnaissance through port scanning techniques like ping scan, TCP port scan, and stealth scan. Understand how to analyze the output in Wireshark to identify open ports and version numbers on target systems.
2 views • 7 slides
Passive Attacks and Reconnaissance in Network Security
Passive attacks involve monitoring target systems through port scanning or other means to locate vulnerabilities. Scanning is the first active action taken against a target network based on information gathered through footprinting, allowing deeper penetration. It includes scanning ports and service
0 views • 24 slides
Triangulation Survey in Land Surveying
Triangulation survey is a method used to determine precise coordinates of fixed points in the field, especially in hilly areas. It involves establishing stations at reasonable distances apart to form a framework of triangles covering the entire survey area. Key operations include reconnaissance, ere
1 views • 20 slides
Comprehensive Guide to Hacking Techniques & Intrusion Detection
This guide by Ali Al-Shemery provides insights into reconnaissance, intelligence gathering, target selection, and open-source intelligence for successful attacks. It covers the importance of OSINT, rules of engagement, and different forms of information gathering in the realm of cybersecurity.
4 views • 46 slides
Sensor References and Procedures for NBCRV Operations
This document provides a detailed guide on sensor references, startup, and shutdown procedures for the Nuclear, Biological, and Chemical Reconnaissance Vehicle (NBCRV). It includes information on various sensors, deployment techniques, operating under different conditions, and mission planning consi
0 views • 25 slides
Wake Island: Strategic Importance and Military Defense in World War II
Wake Island, located in the Northern Pacific Ocean, played a crucial role in World War II as a strategic outpost for both the United States and Japan. The island's military significance was highlighted by its defensive capabilities, long-range reconnaissance opportunities, and potential for offensiv
0 views • 18 slides
Exploring Water on the Moon: Research Insights from Lunar Missions
Uncover the intriguing research on water presence on the Moon through the Lunar Reconnaissance Orbiter and the Lunar Exploration Neutron Detector. Discover how remote sensing and neutron detection technologies have shaped our understanding of lunar water distribution, challenging previous theories.
0 views • 23 slides
Employee Vigilance Campaign: Strengthening Security Awareness in the Workplace
This employee vigilance campaign emphasizes that security is everyone's responsibility. It aims to raise awareness about hostile reconnaissance, educate staff on identifying suspicious behavior, and promote a culture of vigilance. Through various mediums like briefings, posters, and reminders, the c
0 views • 7 slides
Reconnaissance in Cybersecurity: Methods and Techniques
Reconnaissance is a crucial initial step in cyber attacks, involving gathering information about targets through active or passive methods. Active reconnaissance techniques include host discovery, port scanning, service version detection, and OS fingerprinting. This process aids in identifying vulne
0 views • 14 slides
Selecting Landing Sites for Humans on Mars: HLS2 Study Update
The Human Landing Sites Study (HLS2) aims to identify suitable landing sites for human exploration on Mars, focusing on Exploration Zones (EZs) that meet scientific, engineering, and human criteria. Leveraging data from the Mars Reconnaissance Orbiter (MRO), the study establishes a database of high-
0 views • 15 slides
Comprehensive Guide to Hacking Techniques and Intrusion Detection
This guide by Ali Al-Shemery provides insights into hacking techniques, intrusion detection, fingerprinting, external and internal footprinting, passive reconnaissance, WHOIS lookups, and various online tools for intelligence gathering during penetration tests. It covers identifying customer externa
0 views • 29 slides
Weak Points in Web Application Architecture
Information collected during the reconnaissance process can unveil critical aspects of a web application's architecture, including technologies used, API endpoints, functionality, domains, configurations, and authentication systems. Vulnerabilities in web applications often stem from poorly designed
4 views • 13 slides
Essential Steps in Attackers Incident Response Process
Explore the crucial phases of Attackers Incident Response, starting from Information Gathering to Post-Exploitation techniques. Learn about Passive and Active Reconnaissance, OSINT resources, DNS fundamentals, and Google Dorks for reconnaissance. Gain insights into gathering actionable intelligence
0 views • 29 slides
RECONNAISSANCE
Web application reconnaissance is a crucial phase in understanding and mapping the technical and functional aspects of a web application before initiating any hacking activities. This process involves collecting data, analyzing APIs, identifying weak points, and mapping the application's structure a
0 views • 10 slides
Operation Emily: Surveying Thor Rocket Bases in 1958-60s
Operation Emily involved surveying for Thor ICBM bases in eastern England from 1958 until the rockets were decommissioned in the early sixties. Led by the 13 Field Survey Squadron RE, the personnel undertook tasks such as reconnaissance, pillar building, Macca base measurement, triangulation, and as
0 views • 14 slides
Penetration Testing Reconnaissance Techniques
In this material, various reconnaissance tools and techniques used in penetration testing are discussed. Topics include website copying, email harvesting, and information gathering tools like HTtrack, Harvester, and Netcraft.com. The content provides insights into the methodologies and technologies
0 views • 18 slides