Cryptography,.Quantum-safe Cryptography& Quantum Cryptography
Dive into the world of cryptography, quantum-safe cryptography, and quantum technology as discussed in Maurizio D. Cina's presentation at CYBERDAYS in Prato. Topics include current cryptosystems, post-quantum cryptography, quantum key distribution, and future cryptosystems based on quantum algorithm
5 views • 17 slides
Importance of Public Sector Auditing in Enhancing Accountability and Governance
The Auditor-General of South Africa plays a critical role in strengthening democracy through auditing public sector institutions. Public sector auditing ensures compliance, performance evaluation, and governance transparency, ultimately building public confidence. Key stakeholders include government
1 views • 11 slides
Proposed Legislative Amendments for Professionalization of Public Service
This presentation outlines proposed legislative reforms to enhance the professionalization of the public service in South Africa. Key areas targeted include managing the political-administrative interface, training and development of employees, promoting ethical conduct, and more. Priority legislati
1 views • 8 slides
India Alliance Clinical & Public Health fellowship in India
India Alliance Clinical & Public Health fellowship in India\n\nIndia Alliance Clinical and Public Health Research Fellowships are for Health researchers with an MD, MS, MPH, or an equivalent clinical or public health degree, who can apply for the DBT\/Wellcome Trust India Alliance Clinical and Publi
1 views • 5 slides
Security Threats and Public-Key Cryptosystems
Explore the world of security threats, passive and active attacks, and the importance of asymmetric encryption through the terminology related to asymmetric encryption, public-key cryptosystems, and public-key cryptography. Learn about the key components of public-key encryption schemes and the proc
0 views • 46 slides
Introduction to RSA Cryptography and Public Key Encryption
Explore the fundamentals of RSA cryptography and public key encryption, including shift ciphers and affine ciphers. Learn how public key encryption solves the challenges of implementing secure communication on a large scale. Discover the key components of RSA, its development history, and the mathem
3 views • 37 slides
Introduction to Public Key Cryptography
Public key cryptography, exemplified by algorithms like Diffie-Hellman and RSA, revolutionizes secure communication by allowing users to encrypt messages with public keys known to all and decrypt them with private keys known only to the intended recipient. This advanced encryption method ensures sec
1 views • 44 slides
Comparative Analysis of Municipal Services in Public Sector Evolution
Explore the evolution and role of public services in the municipal sector through a comparative analysis presented in a block seminar by Prof. István Hoffman. Delve into the general theory of public services, the traditional and changing approaches of public administration, and government expenditu
0 views • 74 slides
Enhancing Public Health Workforce for COVID-19 Response Grant Program
This cooperative agreement aims to strengthen public health departments by expanding staff, hiring school nurses, and developing public health leaders. It includes major goals like creating a Public Health AmeriCorps and modernizing the public health workforce. The grant terms specify funding distri
2 views • 17 slides
Judicial Review in Suing Public Authorities
Judicial review is the inherent right of courts to review decision-making processes of public bodies. It allows for challenging and analyzing decisions, granting public law remedies like declaration, certiorari, mandamus, prohibition, and quo warranto. Those adversely affected by public duty actions
0 views • 13 slides
Public Integrity and Ethics in Civil Service
This module on public integrity and ethics delves into key instruments for strengthening ethical practices in public organizations, challenges faced, analyzing codes of ethics, and managing integrity risks. The agenda includes activities like structured ethical reflection, understanding public value
2 views • 13 slides
Public Expenditure Management and Performance Evaluation
This content discusses the importance of Public Expenditure Review (PER) as a core diagnostic tool in evaluating government finances and guiding spending decisions. It emphasizes the analysis of public expenditures over time to align with policy priorities and achieve desired outcomes, highlighting
0 views • 33 slides
Induction Pack for New Registrars in Public Health - FPH August 2019
Welcome to the Specialty Training Scheme in Public Health! This induction pack introduces you to the Faculty of Public Health and outlines the key elements of the Training Programme. Learn about the strategic vision of FPH, membership benefits, and how to maximize effective public health action at d
3 views • 16 slides
RSA Algorithm in Public-Key Cryptography
The RSA algorithm is a crucial public key cryptography method used for key exchange, digital signatures, and data encryption. It involves generating public-private key pairs using prime numbers, encryption with the public key, and decryption with the private key. The algorithm's strength lies in the
0 views • 5 slides
Introduction to Cryptography: The Science of Secure Communication
Cryptography is the study of methods for sending and receiving secret messages securely. This lecture explores the application of number theory in computer science, focusing on the design of cryptosystems like public key cryptography and the RSA cryptosystem. The goal of cryptography is to ensure th
0 views • 53 slides
Introduction to Cryptography and Its Applications in Computer Science
Cryptography is the study of methods for sending and receiving secret messages. In this lecture, we explore the design and application of cryptosystems, such as the RSA cryptosystem and Turing's Code. The goal is to securely encrypt and decrypt messages using number theory to protect communication f
2 views • 53 slides
Public-Key Cryptography and Its Applications
Public-Key Cryptography revolutionized secure communication by introducing the concept of using separate keys for encryption and decryption. Initially explored by researchers like Diffie, Hellman, and Merkle in the 70s, it addressed key distribution challenges faced by symmetric cryptography. This m
0 views • 34 slides
Public Procurement Processes and the Public Procurement Act of 2007
Public procurement involves the systematic acquisition of goods, works, and services using public funds through a fair and transparent process. The Public Procurement Act of 2007 outlines the procedures for procurement, ensuring value for money, efficiency, and equity. This process aims to instill p
0 views • 37 slides
Indiana's Open Door Law: Public Access and Governance
The Indiana Open Door Law ensures transparency in public agency actions by requiring open meetings unless exempted. The Public Access Counselor provides guidance on public access laws, emphasizing the importance of public information accessibility. Meetings under the law must be open to the public,
1 views • 17 slides
Role of Public Health Practitioners in London's Workforce Development
Public Health Practitioners (PHPs) play a crucial role in implementing and delivering public health services, programs, and interventions. They focus on promoting health and wellbeing within communities, addressing health inequalities, and protecting the public from environmental hazards. Learn abou
0 views • 23 slides
Public Goods in Higher Education
This text delves into the concept of public goods in higher education, examining the distinctions between public and private forms, the economic and political dimensions, and the normative value of public goods. It discusses the economic definition of public goods, emphasizing their non-rivalrous an
2 views • 18 slides
Public Interest in Water Law
The public interest plays a crucial role in various aspects of water law, particularly in determining new appropriations, permit extensions, filing adjudications, and managing water resources. Water law requires consideration of public welfare, existing rights, and beneficial uses when granting perm
0 views • 16 slides
Public Key Cryptosystems in RSA Encryption
Public key cryptosystems, like RSA, use two keys for encryption and decryption, with one key made public and the other kept secret. This asymmetric system allows secure communication, where the encryption key (E) is used to encrypt messages into ciphertext (C), which can only be decrypted back to th
0 views • 11 slides
New Jersey's Open Public Meetings Act (OPMA)
This presentation outlines the Open Public Meetings Act (OPMA) in New Jersey, emphasizing the importance of public access to government meetings and decision-making processes. Sen. Byron M. Baer's Sunshine Law ensures transparency and democracy by allowing the public to attend and observe public bod
0 views • 66 slides
Limits on the Efficiency of Ring LWE-based Key Exchange
This study explores the limitations of Ring LWE-based key exchange protocols and their impact on non-interactive key exchange mechanisms. It discusses the LWE assumption, noise distribution, and the practical implications of small moduli q and noise-to-modulus ratio r. Additionally, it delves into P
0 views • 71 slides
Enhancing Public Services through Open Government Partnership in Georgia
The National Agency of State Property in Georgia, in partnership with the Open Government Partnership (OGP) and supported by the United Nations Development Programme (UNDP), has undertaken a project to improve transparency, accountability, and citizen engagement in public services. The 2014-2015 Act
0 views • 9 slides
Overview of Knapsack Cryptosystems and Related Problems
The Merkle-Hellman knapsack cryptosystem is a cryptographic system that was initially proposed by Merkle, and later iterated versions were both broken by Shamir and Brickell in the early 1980s and 1985, respectively. This system is related to the classical knapsack problem, subset-sum problem, and e
0 views • 18 slides
Ensuring Transparency in Public Governance: The Brown Act and Public Records Act
This content emphasizes the importance of transparency in public governance by discussing key laws such as the Brown Act and Public Records Act. It highlights the necessity for public officials to conduct business transparently, allowing the public to monitor and participate in decision-making proce
0 views • 22 slides
The Role of Public Opinion in the Political Process
The political process involves the interaction of public opinion, interest groups, and political parties. Public opinion, shaped by factors like media and socialization, influences government actions. This chapter discusses the significance of public opinion, its formation, and measurement through p
0 views • 39 slides
Overview of Public Procurement System in Lithuania
The public procurement system in Lithuania is governed by various laws and regulations, covering different sectors such as concessions, defense/security, utilities, and classical sector. The system includes procedures for different monetary value procurements, including international, simplified, an
0 views • 44 slides
Region IV Public Health Training Center Overview
The Region IV Public Health Training Center (PHTC) is dedicated to strengthening the competence of the public health workforce in HHS Region IV. It provides professional development opportunities for both current and future public health professionals through training programs, field placements, and
1 views • 33 slides
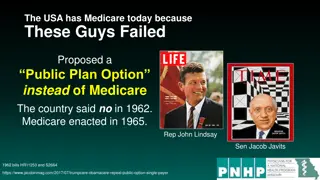
Evolution of Healthcare Policy: From Failed Public Plan Option to Medicare
In 1962, a public plan option was proposed, but the idea was turned down, leading to the enactment of Medicare in 1965. The concept of a public option as a pathway to universal coverage is explored, highlighting its merits, challenges, and risks. A best-case scenario for a public option strongly tie
0 views • 4 slides
Public Services in Modern Democracies
Public services play a crucial role in modern democracies, encompassing a wide range of essential services provided by the government to its citizens. These services, whether directly provided or publicly financed, are integral to ensuring equal access and upholding fundamental human rights. Public
1 views • 10 slides
Evolution of Public Policy: From Seeds Sown in 1940s to Academic Discipline in Social Science
The lives of citizens are shaped by public policies, often unnoticed. The analysis of current public policy in America carries a unique 20th-century essence. Beginning in the 1940s, these policy seeds have profoundly influenced government and academic institutions. By the early 1950s, public policy
0 views • 6 slides
Cryptographic Center in Novosibirsk: Advancements in Cryptography and Research
The Cryptographic Center in Novosibirsk, established in 2011, focuses on advancing cryptography through research, education, and international collaborations. With a team of researchers and students, the center explores various aspects of cryptography, including cryptographic Boolean functions, ciph
0 views • 33 slides
Key Exchange and Public-Key Cryptography Overview
Explore the challenges of key management, the use of trusted third parties in generating shared keys, the limitations of toy protocols in secure key exchange, and the evolution of public-key cryptography techniques like Merkle Puzzles, Diffie-Hellman, and RSA. Learn how to achieve secure key exchang
1 views • 36 slides
Withdrawal of Public Lands for Military Use: Overview and Legal Framework
Public lands across various states have been withdrawn for military use, with the Department of the Interior managing these lands primarily reserved for Department of Defense (DOD) use. Legal requirements such as the Engle Act and Federal Land Policy and Management Act govern the process of withdraw
0 views • 16 slides
Protection of Political Speech and Criticism: Ensuring Freedom of Expression for Public Officials
Understanding the importance of freedom of speech in political discourse, this workshop focuses on the legal framework protecting political speech and criticism of public officials. Highlighting the rights and responsibilities in democratic societies, the content emphasizes the necessity of open deb
0 views • 14 slides
Quantum Public-Key Encryption with Tamper-Resilient Public Keys
Explore the concept of Quantum Public-Key Encryption with Tamper-Resilient Public Keys from One-Way Functions. Learn about the essentials of Public-key Encryption (PKE), computational assumptions, and the implications of realizing PKE from OWFs in the quantum world. Delve into topics like statistica
0 views • 20 slides
Securing Communication in the Quantum Computing Era
Embracing Post-Quantum Cryptography (PQC) is essential to counter the threat posed by large-scale quantum computers to current public key cryptosystems. Russ Housley, a prominent figure in the field, highlights the urgency to deploy PQC algorithms before a quantum computing breakthrough occurs. The
0 views • 9 slides