Transform Your Outdoor Space with AAA Fence And Deck Company
Elevate your outdoor living with AAA Fence And Deck Company! Discover quality fencing and decking solutions for your Raleigh, NC home. Transform your space with our expert craftsmanship and a touch of elegance. Visit our website for inspiration!\n
1 views • 6 slides
Dynamic Pricing Algorithms with Privacy Preservation in Personalized Decision Making
Explore the challenges of preserving privacy in dynamic personalized pricing algorithms for decision-making in business. The research focuses on nonparametric demand models and differential privacy to safeguard user data against various privacy attacks, addressing the growing concerns and the need f
3 views • 30 slides
Secure Your Property with Professional Fence Installation Services
Safeguard your property and loved ones with the help of AAA Fence & Deck, the leading Fence Company Raleigh NC. Our experienced team is dedicated to providing unmatched fence installation services that combine strength, durability, and style. Whether you're looking for a classic wooden fence or a mo
2 views • 6 slides
Thinking About Hidden Pet Fences Here's What You Need to Know
pet fence\n\nDIY Cat Fence\n\nFor more info, visit our site \/\/hiddenfence.com.au\/
1 views • 4 slides
Tips for Safe Hidden Dog Fence Installation
smart dog fence\n\nhidden dog fence professional installation\n\nFor more info, visit our site \/\/hiddenfence.com.au\/
1 views • 4 slides
Best Fence Contractor in Ormeau Hills
Are you looking for the Best Fence Contractor in Ormeau Hills? Then contact Wildman Homes & Renovations. They take pride in their work and demonstrate a high quality of craftsmanship. They specialise in all aspects of renovation, from retaining walls and fences to bathrooms, kitchens, and even lands
0 views • 6 slides
If you are searching for a Fence contractor in Long Bay
If you are searching for a Fence contractor in Long Bay, Elite Fencing and Landscape is based in Dairy Flat, Torbay. We have over 20 years of experience in fencing, decking, retaining walls, and landscaping. Whether it\u2019s fencing to keep the kids or pets in or a privacy screen or deck for that n
0 views • 6 slides
Signs You Should Install a Hidden Pet Fence
pet fence\n\nDIY Cat Fence\n\nFor more info, visit our site \/\/hiddenfence.com.au\/\n
1 views • 4 slides
Reasons to Install Hidden Dog Fences
hidden dog fence professional installation\n\nsmart dog fence\n\nFor more info, visit our site \/\/hiddenfence.com.au\/\n
2 views • 4 slides
The Benefits of Hidden Fences for Pets
Wireless pet fence installation\n\nwireless dog fence installation\n\nFor more info, visit our site \/\/hiddenfence.com.au\/\n
1 views • 4 slides
How Does a Wireless Dog Fence Work
wireless dog containment \n\nwireless dog fence\n\nFor more info, visit our site \/\/hiddenfence.com.au\/\n
1 views • 4 slides
Pool Vinyl Fence for Safety and Style
A Pool Vinyl Fence is the perfect choice for your pool area. It provides safety for children and pets, ensuring peace of mind. Durable and low-maintenance, these fences can withstand various weather conditions, staying strong and looking great for ye
2 views • 5 slides
Understanding Privacy in Information Security Training
Privacy awareness training is crucial, covering topics such as the definition of privacy, importance of privacy protection, Personally Identifiable Information (PII), and Sensitive PII. Discover why privacy is vital to maintaining public trust, preventing identity theft, and complying with laws. Lea
0 views • 55 slides
NCVHS Subcommittee on Privacy Comments on HIPAA Privacy Rule for Reproductive Health Care
NCVHS Subcommittee on Privacy, Confidentiality, and Security provided comments on the Notice of Proposed Rulemaking (NPRM) to modify the HIPAA Privacy Rule for reproductive health care privacy. The NPRM aims to address concerns post-Dobbs ruling, introducing new provisions for prohibited uses and di
0 views • 13 slides
Privacy-Preserving Analysis of Graph Structures
Explore the world of graph structures and differential privacy in data publishing networks, focusing on preserving privacy while releasing structural information about graphs. Differential privacy techniques such as edge privacy and subgraph counts are discussed in detail, highlighting the challenge
0 views • 20 slides
FMCSA Privacy Awareness Training Overview for 2022
Understanding the importance of privacy and Personally Identifiable Information (PII) in the context of the Federal Motor Carrier Safety Administration (FMCSA). The training covers topics such as the definition of privacy, why privacy is crucial, what constitutes PII, the significance of sensitive P
0 views • 55 slides
Understanding Data Privacy Laws and Regulations in Saudi Arabia
This content provides an overview of data privacy laws and regulations, focusing on the landscape of data protection laws, examples of comprehensive regulations like FIPPS and GDPR, and sector-specific laws in Saudi Arabia. It includes a homework assignment to explore Fair Information Practices Prin
0 views • 28 slides
Suitable Methods For Building A Power Fence
Hebel fence is a great alternative to brick-wall fencing. It is sturdy and durable, and it can tolerate noise pollution in your home. It is the most popular choice for both commercial and residential building projects due to its tremendous strength,
2 views • 2 slides
Understanding Breach of Confidence and Privacy Rights in English Law
English law does not provide a specific right to privacy, but breach of confidence laws offer protection against unauthorized disclosure of private information. While there is no overarching invasion of privacy tort, legal controls exist to balance freedom of expression with respect for individual p
0 views • 18 slides
Custom Fence and Deck_ Expert Fence Fixing Services
Is your fence in need of repair? Custom Fence and Deck specializes in expert fence fixing services, ensuring your fence is not only functional but also aesthetically pleasing. Whether your fence has suffered from weather damage, wear and tear, or oth
0 views • 2 slides
Custom Fence and Deck:Expert Fence Repair Services
At Custom Fence and Deck, we understand the importance of a sturdy and well-maintained fence for your property\u2019s security and aesthetic appeal. Our expert fence repair services are designed to restore and enhance the functionality and appearance
0 views • 4 slides
Privacy Considerations in Data Management for Data Science Lecture
This lecture covers topics on privacy in data management for data science, focusing on differential privacy, examples of sanitization methods, strawman definition, blending into a crowd concept, and clustering-based definitions for data privacy. It discusses safe data sanitization, distribution reve
0 views • 23 slides
Proposal for Play Area Signage Improvement
Playground inspection reports highlighted the need for signage improvements in play areas across the parish. Tony has researched guidelines and proposed a set of possible signs with cost estimates from Wicksteed. The options include various sign types and sizes, with two signs suggested for each pla
0 views • 15 slides
Understanding Encryption Techniques: From Transposition Ciphers to Rail Fence Ciphers
Explore the world of encryption techniques, diving into transposition ciphers and rail fence ciphers. Learn about encryption, decryption, plaintext, ciphertext, keys, and the art of secret writing. Discover how transposition ciphers reorder letters without changing their values and how rail fence ci
0 views • 26 slides
How to Apply Online for Fence Approval without City Hall Visit
Access the online permit system to apply for a fence approval without visiting City Hall. Create an account, enter your property details, validate your email, and start your permit application packet all from the comfort of your home. Follow the step-by-step guide provided to complete the process ef
0 views • 14 slides
Optimal Pathfinding in the Shortest Race
The problem involves finding the optimal point to touch a fence while racing from tree A to tree B to minimize the distance run. By reflecting point A in the fence line to point A' and joining A' to B, the point where AB crosses the fence line gives the solution. This approach is based on the princi
0 views • 25 slides
Memory Fence Synthesis and Algorithm Verification
Abstract interpretation is utilized for sequential consistency in memory fence placement. The correctness of algorithms, such as Dekker's Algorithm, is verified by synthesizing minimal fence placements. The goal is to use existing tools to ensure the mutual exclusion of critical sections effectively
0 views • 32 slides
Legal Update on Fence Law, Livestock Liability, and Zoning Regulations
Understanding the legal aspects of fence laws, livestock liability, and zoning regulations is crucial for growers and farmers. This update covers key points such as personal liability limits, compliance with exemptions, and the implications of livestock escaping. It also delves into boundary fencing
0 views • 28 slides
Addressing Environmental Justice for Fence-line Communities
Partnership and collaboration between government agencies, communities, and industries are crucial in achieving Environmental Justice for fence-line communities impacted by air pollution. Access to air monitors, data analysis, and regulatory oversight are essential in protecting public health and ho
0 views • 4 slides
Wildlife Fence and Gate Project Overview
The project involves final planning and design in January 2021, with estimated construction starting in June 2021. It includes the installation of a 6-foot high wildlife fence, gates, new cattle guard, roadway entry gate, combination view fence and masonry wall, pedestrian gates, and maintenance gat
0 views • 12 slides
Understanding the Privacy Paradox: Attitudes vs. Behaviors
Social scientists have identified a Privacy Paradox where individuals with strong privacy concerns may not always engage in behaviors that protect their privacy. While some studies show a discrepancy between attitudes and behaviors, others suggest that privacy-concerned individuals do employ privacy
0 views • 14 slides
Understanding Privacy Rights in Europe: A Comprehensive Overview
This content delves into the common definitions of privacy and the constitutional protection of privacy in Europe. It explores the right to privacy in individual, company, and government contexts, as well as ways to analyze the correlation between individual rights and others' duties. The discussion
0 views • 25 slides
Understanding Breach of Confidence and Privacy Rights in Legal Context
The legal landscape regarding breach of confidence and privacy rights, especially in the context of English law and the European Convention on Human Rights, is complex and ever-evolving. While English law traditionally does not recognize a right to privacy, recent developments and landmark cases hav
0 views • 18 slides
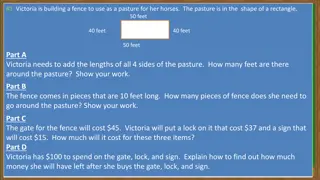
Mathematics Problem Solving Tasks
Victoria is building a rectangular fence for her horses, Raul is counting his coins, Peta is solving expressions, James is managing his wallet money, Jackie is dealing with pennies, and Hanna is working with different types of coins. The tasks involve calculating fence perimeter, counting coins, sol
0 views • 38 slides
Data Privacy Best Practices Training for Libraries
Explore a comprehensive data privacy training program for libraries led by Becky Yoose, a renowned Library Data Privacy Consultant. Supported by the U.S. Institute of Museum and Library Services, this training covers privacy fundamentals, current issues, risk assessment, vendor relations, patron pri
0 views • 33 slides
Enhancing Online Patron Privacy in Library Websites
This assessment by Marshall Breeding emphasizes the importance of maintaining online patron privacy on library websites. It covers key aspects such as the use of HTTPS, encryption, and privacy protection measures against vulnerabilities like tracking bots and unsecured transactions. The significance
0 views • 45 slides
Student Privacy Laws and Best Practices in Education Sector
Legislatures across various states are actively introducing and considering new student privacy laws, focusing on safeguarding online personal information and enhancing data transparency and security. Key themes include the introduction of privacy bills, the passing of data privacy laws, and the est
0 views • 30 slides
Privacy Awareness Week 2017: Understanding the Australian Privacy Act
Explore the key aspects of the Australian Privacy Act 1988 during Privacy Awareness Week 2017. Learn about the Australian Privacy Principles, regulatory powers of the Commissioner, and the importance of managing personal information transparently. Discover how the Act covers sensitive information, t
1 views • 31 slides
The Challenges of Protecting Privacy with Differential Privacy
The article discusses the motivation behind using differential privacy to protect sensitive data while enabling useful queries. It highlights the promise of differential privacy, challenges faced, attacks on existing systems like PINQ and Airavat, and introduces a defense system called The Fuzz. The
0 views • 24 slides
Privacy Fence: Enhance Your Outdoor Space with Security and Style
A privacy fence is the perfect solution for adding security and seclusion to your outdoor space. Available in various materials and styles, privacy fences create a private retreat while enhancing the look of your yard. Explore durable and stylish opt
1 views • 8 slides