Domain-Agnostic Information Model for Vehicle Data Transformation
The push towards a domain-agnostic information model from a vehicle-centric data approach is explored due to emerging industry requirements. COVESA projects like AUTOSAR Vehicle API and EV charging necessitate a shift. The proposal introduces the Hierarchical Information Model (HIM) to organize data
0 views • 10 slides
Ensuring Credible Private Set Membership with Efficient Communication
Explore the concept of credible private set membership ensuring server privacy, client privacy, and data credibility through innovative protocols and approaches. The focus is on maintaining high-entropy passwords securely while optimizing rounds and leveraging underlying crypto primitives efficientl
1 views • 18 slides
Distributed Computation in Node-Capacitated Networks
Exploration of communication primitives and algorithms in node-capacitated networks, including Node-Capacitated Clique Model, communication on butterfly networks, orientation using Boruvka's algorithm, computing O(a)-orientation, and solving graph problems like BFS trees, maximal independent set, ma
0 views • 7 slides
Understanding Multi-Threading Concepts in Computer Systems
Exploring topics such as cache coherence, shared memory versus message passing, synchronization primitives, cache block states, performance improvements in multiprocessors, and the Ocean Kernel procedure for solving matrices.
0 views • 22 slides
APL - A Functional Language with Array Paradigms
APL, named after the book "A Programming Language Paradigms," is a functional language with a focus on array manipulation. Developed in the 1960s by Kenneth E. Iverson, it has had a significant impact on the development of spreadsheets and computer math packages. APL operates with chains of monadic
0 views • 11 slides
Understanding Provable Security Models in Cryptography
Cryptography and cryptology involve secure communication techniques to protect data from third-party adversaries. This article introduces provable security models, cryptographic goals like confidentiality and authenticity, and the approach of security by trial-and-error versus provable security meth
0 views • 48 slides
Understanding Small-State Noncryptographic Pseudorandom Number Generators
Explore the design and testing of small-state noncryptographic pseudorandom number generators, including definitions, rules of thumb, chisquare tests, existing and new generators, and more. Learn about block cipher encryption, hash functions, pseudorandom number generation, reversible mixing, and re
0 views • 46 slides
Robust Parity Test for Extracting Parallel Vectors in 3D
Fundamental primitives for visualizing 3D data include line features like ridges and valleys of a scalar field, stream lines of a vector field, vortices of a velocity field, and extremal curves of a tensor field. Parallel Vectors (PV) provide a unified representation of 3D line features, forming con
0 views • 27 slides
Understanding C++ Parallelization and Synchronization
Explore the challenges of race conditions in C++ multithreading, from basic demonstrations to advanced scenarios. Delve into C++11 features like atomic operations, memory ordering, and synchronization primitives to create efficient and thread-safe applications.
0 views • 51 slides
Portable Inter-workgroup Barrier Synchronisation for GPUs
This presentation discusses the implementation of portable inter-workgroup barrier synchronisation for GPUs, focusing on barriers provided as primitives, GPU programming threads and memory management, and challenges such as scheduling and memory consistency. Experimental results and occupancy-bound
0 views • 61 slides
Understanding Graphics Pipeline Clipping Techniques
Delve into the intricate process of graphics pipeline clipping in computer graphics, from breaking primitives into fragments to determining visible parts for rendering. Explore the necessity of clipping, culling, and endpoint conditions, as well as techniques like Cohen-Sutherland Line Clipping. Gai
0 views • 18 slides
Understanding Advanced Graphics and UIs Rendering Pipeline
Explore the intricate details of the rendering pipeline in advanced graphics and user interfaces, including clipping and culling processes. Learn about the sequence of operations involved in drawing primitives, the evolution of APIs like OpenGL and D3D, and the various stages from vertices to visibl
0 views • 52 slides
Understanding Weird Machines in Transient Execution
Weird machines refer to models exhibiting unintentional behaviors triggered by adversarial inputs. They serve as computation primitives, enabling tasks like program obfuscation and secret computations. TSX weird machines, computing with time, manipulate cache states through gates like Assign, AND, O
0 views • 18 slides
Understanding C++ Parallelization and Synchronization Techniques
Explore the challenges of race conditions in parallel programming, learn how to handle shared states in separate threads, and discover advanced synchronization methods in C++. Delve into features from C++11 to C++20, including atomic operations, synchronization primitives, and coordination types. Un
0 views • 48 slides
Communication Lower Bounds of Key-Agreement Protocols
Key-agreement protocols play a vital role in secure communication between parties. This document explores lower bounds of key-agreement protocols through density increment arguments, idealization of symmetric primitives, Merkle puzzles, and the impact of communication bits between Alice and Bob. Var
0 views • 10 slides
Understanding Fill Area Primitives in Computer Graphics
An overview of fill area primitives in computer graphics, including the concept of fill areas, polygon fill areas, and polygon classifications into convex and concave polygons. This module covers the efficient processing of polygons, approximating curved surfaces, and generating wire-frame views of
0 views • 63 slides
Understanding Attributes and Color Schemes in Graphics
Graphics systems utilize attributes to define how primitives are displayed, such as color and size, while color and grayscale can be stored in different ways like direct storage and indexed storage schemes. The RGB color components play a key role in determining the color shades, with various color
0 views • 51 slides
Geometric Pipeline Implementation Strategies: From Vertices to Fragments
The chapter delves into the process of converting vertices into primitives, clipping out objects outside the view frustum, and determining affected pixels by each primitive. Tasks such as rasterization, transformations, hidden surface removal, and antialiasing are discussed. Various algorithms for c
0 views • 68 slides
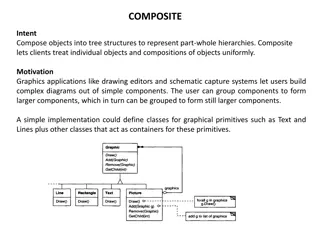
Understanding the Composite Design Pattern in Object-Oriented Programming
The Composite design pattern allows clients to treat individual objects and compositions of objects uniformly, enabling the representation of part-whole hierarchies in tree structures. This pattern is commonly used in graphics applications to create complex diagrams from simple components, allowing
0 views • 43 slides
Clear Approach to Cancellation of Asynchronous Operations
This resource discusses the concept of cancellation primitives, providing a clear and consistent approach to cancelling asynchronous operations. It emphasizes separating the source and sink, enabling synchronous and asynchronous observation of cancellation requests. The goal is to facilitate composa
0 views • 17 slides
Cryptography in Bounded Storage Model: Ensuring Secure Communication
Cryptography in the Bounded Storage Model provides insights into securing communication with secrecy and authenticity. The model limits adversaries' memory without runtime restrictions, ensuring unconditional security for various primitives. Explore how this model safeguards messages from eavesdropp
0 views • 42 slides
Embedded Systems: Introduction to Input and Output Devices
This material explores the essential concepts related to input and output (I/O) devices in embedded systems. It covers examples of I/O devices, such as keyboards, mice, and disk drives, along with the digital interface between these devices and the CPU. Specific focus is given to the 8251 UART as an
0 views • 55 slides
Understanding Scala's Class Hierarchy and Value Classes
Scala's class hierarchy includes Any, AnyVal, and AnyRef classes, with implicit conversions and implementations of primitives similar to Java. Learn about defining value classes, natural and reference equality comparisons, and more in Scala programming.
0 views • 24 slides
Understanding Remote Procedure Calls in Distributed Systems
Explore the concept of Remote Procedure Calls (RPC) in distributed systems, including the basic RPC approach, middleware layers, transport primitives, failure types, and more. Learn how RPC enables communication between sender and receiver seamlessly, without direct message passing visible to the pr
0 views • 19 slides
CS260 Parallel Algorithms: Theory and Practice Review
This review covers essential topics from the CS260 Parallel Algorithms course by Yihan Sun, focusing on key concepts such as scheduler programs, cost models, reduce and scan techniques, PRAM models, atomic primitives, small algorithms, the master theorem, and sorting algorithms like Quicksort and Me
0 views • 25 slides
I/O-Efficient Protection Against Silent Data Corruptions in RAID Arrays
This paper discusses the risks of silent data corruptions in RAID arrays, which are challenging to detect and can lead to serious consequences. It presents the concept of integrity protection to enhance RAID systems' ability to detect and recover from such corruptions efficiently. The paper investig
0 views • 26 slides
Exploring Array-Oriented Solutions in APL by Richard Park
Array Programming Language (APL) offers a powerful approach to problem-solving through array-oriented solutions. Richard Park delves into the intricacies of APL, highlighting its tools of thought, language primitives, and problem-solving techniques. The webinar covers the significance of notation as
0 views • 40 slides
Computer Graphics Rendering Pipeline Overview
Introduction to the forward rendering pipeline in computer graphics, covering clipping, culling, transformations, primitive assembly, rasterization, and fragment processing. Details on viewport transformations, vertex processing, and visible primitives are included. Clipping techniques for points, l
0 views • 52 slides
NetLogo - Programmable Modeling Environment for Simulating Natural and Social Phenomena
NetLogo is a powerful and versatile programmable modeling environment created by Uri Wilensky in 1999. It allows users to simulate natural and social phenomena by giving instructions to multiple agents operating independently, making it ideal for modeling complex systems evolving over time. NetLogo
0 views • 7 slides
Understanding Graphics Output Primitives and Coordinate Reference Frames
Graphics output primitives and coordinate reference frames play a crucial role in describing scenes and drawing basic geometric structures in 2D space. These concepts involve defining points, drawing lines, and understanding pixel coordinates within a coordinate system. Absolute and relative coordin
1 views • 35 slides
Understanding OpenMP Barriers and Locks in Parallel Programming
Exploring the concepts of OpenMP barriers and locks in parallel programming, this discussion covers the importance of synchronization through barriers, the use of lock variables for finer control over synchronization, and examples like the Dining Philosophers problem. Learn how these primitives faci
0 views • 22 slides
Update on USolids/VecGeom Integration in Geant4 by Gabriele Cosmo at CERN EP/SFT
Status update on the implementation and testing of shapes in Geant4 using USolids/VecGeom integration, highlighting open issues, VecGeom shapes usage, and expected geometry features in Geant4 10.3. The transition from USolids to VecGeom as a unified solids library in Geant4, aimed at enhancing geome
0 views • 19 slides
Accuracy Tradeoffs in Software-Defined Measurement
This research explores tradeoffs in accuracy when using software-defined measurement for tasks such as traffic engineering, accounting, and troubleshooting in network management. It discusses challenges such as limited resources and complexity in switches, and compares different measurement primitiv
0 views • 15 slides
Higher-Level Synchronization with Semaphores at Carnegie Mellon
Discover how Carnegie Mellon University explores higher-level synchronization primitives such as semaphores for effective thread management. Learn about the design and operations of semaphores, and compare them with traditional locking mechanisms. Dive into code examples and visual illustrations to
0 views • 40 slides
New Assumptions for Achieving Chosen Ciphertext Security in Cryptography
This research work focuses on presenting new assumptions for achieving chosen ciphertext security in public key encryption. The study aims to clarify the necessary and sufficient assumptions to realize general cryptographic primitives, particularly focusing on CCA secure PKE and KEM. The ultimate go
0 views • 27 slides
Geometric Construction in Engineering Drawing: Lecture Highlights
Geometric construction involves creating primitive geometric forms like points, lines, and planes to define objects in space. The lecture covers the basics of 2D geometric primitives, such as points, lines, circles, and arcs. It explains the significance of points and lines in technical drawings and
0 views • 18 slides