Rwanda HIE Patient Identity Management System Overview
The Rwanda Health Information Exchange (HIE) system focuses on patient identity management to uniquely identify individuals seeking healthcare across the country. By maintaining a set of identifiers in the client registry and avoiding duplication of patient records, the system ensures efficient and
12 views • 8 slides
Amateur Radio Licensing Regulations and Call Signs in the UK
Learn about the licensing regulations, privileges, call sign formats, secondary identifiers, and addresses for amateur radio operators in the UK. Discover the differences between Foundation, Intermediate, and Full license classes, as well as the various call sign formats used in England. Explore the
0 views • 87 slides
Management of Postpartum Patient with Persistent Tachycardia and Dizziness
A 33-year-old African American female at 39 weeks of gestation, G4P3, with possible ITP and anemia, was admitted for induction. Following delivery, her vital signs and labs were stable initially, but she developed persistent tachycardia and mild dizziness postpartum. After transfusion and monitoring
0 views • 19 slides
IEEE 802.11-20-0745r0 Identifier Privacy Service
In IEEE 802.11-20-0745r0, the focus is on protecting identifiers to enhance privacy in wireless networks. The proposal suggests using ECIES for identifier protection, covering various identifiers like password identifiers and PMKIDs. By implementing a scheme similar to 3GPP and IETF standards, the s
4 views • 7 slides
Federal Agencies Guidance on Ethics, Compliance, and Audit Services under NSPM-33
The White House OSTP released guidance for federal agencies to implement NSPM-33 focusing on disclosure requirements, digital identifiers, consequences for violations, information sharing, and research security programs. The guidance emphasizes supporting open scientific inquiry and nondiscriminator
0 views • 10 slides
Understanding Mode-S Radar Operations and Identifiers
This simplified explanation delves into the fundamental principles of radar operations, focusing on Primary and Secondary radar systems, including Mode A/C and Mode S functionalities. It covers radar interrogation, replies, and the significance of radar identifiers (II and SI codes) in managing over
0 views • 19 slides
Distributed Algorithms for Leader Election in Anonymous Systems
Distributed algorithms play a crucial role in leader election within anonymous systems where nodes lack unique identifiers. The content discusses the challenges and impossibility results of deterministic leader election in such systems. It explains synchronous and asynchronous distributed algorithms
2 views • 11 slides
Differential Diagnosis of Chronic Cough in Primary Care
A 54-year-old man with a persistent cough prompts consideration of initial investigations like chest X-ray and pulmonary function tests. For a 40-year-old woman with a persistent cough, initial management options include sequential trials of steroids, a proton pump inhibitor, and nasal spray. These
0 views • 20 slides
Detailed Guidance and Requirements for Implementing NSPM-33
The update provides detailed guidance on implementing NSPM-33's disclosure requirements and other provisions discussed in the January 2022 CLASP Meeting. It includes areas such as disclosure requirements, digital persistent identifiers, consequences for violations, information sharing, and research
1 views • 19 slides
Enhancing Crash Consistency in Persistent Memory Systems
Explore how ThyNVM enables software-transparent crash consistency in persistent memory systems, overcoming challenges and offering a new hardware-based checkpointing mechanism that adapts to DRAM and NVM characteristics while reducing latency and overhead.
0 views • 37 slides
Streamlining Customer Service Management with Digital Identifiers
Revolutionize your customer service experience by leveraging cloud-based digital identifiers for unique customer identification, service validation, and access control. Seamlessly create, personalize, and send identifiers to customers via mobile and email, enabling automated service activation post-
0 views • 15 slides
Understanding Data Linkages for DaVINCI
Explore the intricacies of patient identifier linkages and linking methodologies for direct care data in the context of DaVINCI. Learn about different systems such as CHCS, AHLTA/CDR, MHS Genesis, and how they utilize identifiers like EDIPN, SSN, and more to establish unique patient records. Discove
0 views • 29 slides
Unveiling the Realities of Privacy in App Usage
Exploring the complexities of privacy policies, the disclosure of user data by apps, and the implications of mobile tracking. Learn how AppCensus assists parents in understanding app data collection practices and the risks associated with sharing persistent identifiers. Discover how third parties ut
0 views • 25 slides
Ensuring Security in Persistent Key-Value Stores using Shielded Execution
This content discusses the challenges and solutions for securing LSM-based Key-Value stores in untrusted computing environments using Shielded Execution. It addresses the need for confidentiality, integrity, and freshness of data in persistent storage systems. The research explores Trusted Execution
0 views • 32 slides
Discussion on Device ID Renaming in IEEE 802.11-22/1665r0
The document explores the ongoing discussion on renaming the Device ID in IEEE 802.11-22/1665r0 standards. Various proposals, including Persistent Opaque Identifier and Persistent Identifier, are considered. The Device ID's role in the current specifications is analyzed, along with the opacity of th
0 views • 10 slides
Unified Approach to Combat Counterfeiting with Digital Object Architecture
The talk discusses terminology, managing the supply chain, obtaining information about devices, and using digital object architecture to combat counterfeiting. It covers physical and digital entities, Internet resources, and the importance of unique persistent identifiers. The focus is on ICT device
0 views • 13 slides
Framework for Research Data Management and Persistent Identifiers at Waipapa Taumata Rau
This research delves into the integrated framework for Research Data Management (RDM) and the initiatives around Persistent Identifiers (PIDs) and ORCID implementation at Waipapa Taumata Rau. It explores the background, aims, and priorities of the RDM Programme for 2022-2024, focusing on improving R
0 views • 9 slides
High-Performance Transactions for Persistent Memories
Explore the optimization of transactions for persistent memories, focusing on ordering constraints, synchronous vs. deferred commit transactions, persistency models, and performance evaluation. The study aims to improve transaction performance in the presence of high persistent memory latencies by m
0 views • 26 slides
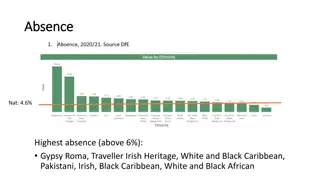
Education Disparities Among Ethnic Groups in Bristol
The data highlights varying levels of absence, persistent absence, suspensions, good level of development, and expected standards in Bristol schools across different ethnic groups. Gypsy Roma, Traveller Irish Heritage, White and Black Caribbean, and Pakistani communities show higher rates of absence
0 views • 11 slides
Understanding Persistent Memory Use with WHISPER by University of Wisconsin-Madison & Hewlett-Packard Labs
This analysis delves into the use of persistent memory with WHISPER, uncovering behaviors, system support enhancements, and the benefits of persistent memory technology. It discusses guarantees applications need, achieving consistency, and systems tailored for persistent memory utilization, providin
1 views • 24 slides
The Power of Prayer in Building Community Within the Church
Prayer plays a vital role in fostering intimacy and identity within the church as emphasized in 1 Thessalonians 5:13-17 and Luke 18:1-7. Through prayer, believers are encouraged to support, comfort, and uplift one another, creating a strong sense of community grounded in faith in Christ. The parable
0 views • 29 slides
Addressing Privacy Concerns in IEEE 802.11-21: Changing MAC Addresses for Improved Security
The document discusses the implications of changing STA MAC addresses per association in IEEE 802.11-21 standard to enhance privacy and security. It explores the challenges of maintaining persistent identifiers in data frames and the risks associated with sending source/destination addresses in clea
0 views • 11 slides
Unveiling the Parable of the Persistent Widow in Luke's Gospel
Delve into the cultural context of Jesus's teachings through the lens of the Second Temple Period. Explore the Parable of the Persistent Widow in Luke, analyzing the significance of prayer, justice, and faith as portrayed in this narrative. Uncover the timeless message of perseverance and trust in d
0 views • 28 slides
Understanding Health Plan Identifiers: HPID vs. OEID
Health Plan Identifiers (HPIDs) play a crucial role in the healthcare industry by uniquely identifying health plans during electronic transactions. This article delves into the significance of HPIDs, the distinction between Controlling Health Plans (CHP) and Subhealth Plans (SHP), and the comparison
0 views • 17 slides
Enhancing ROI through DOI, FAIR, and Data Sets
Explore the importance of DOI, FAIR Data Principles, and high-quality research data sets for enhancing return on investment in creating and curating research data. Learn about Persistent Digital Identifiers, the FAIR data initiative, and the significance of reproducibility, credit, and public metada
0 views • 4 slides
Italian Model of Distributed Research Information Management Systems
The case study discusses the adoption of Dspace-CRIS in Italy, highlighting the benefits such as open repositories, enhanced metadata quality, and increased national research visibility. The integration of persistent identifiers like ORCID has improved data quality and interoperability. Lessons lear
0 views • 17 slides
Understanding Persistent Pain: Challenges, Strategies, and Interventions
This collection of images and text delves into the challenges faced when treating individuals with persistent pain, covering themes like acceptance, change, and resources. It explores the bidirectional association between stress, distress, and pain, and provides insights into the complex nature of p
0 views • 28 slides
Understanding Naming Systems in Distributed Systems
Entities in distributed systems are uniquely identified using names, addresses, and identifiers. Naming systems assist in name resolution and can be categorized into flat, structured, and attribute-based naming. Flat naming uses random strings as identifiers, and various mechanisms such as broadcast
0 views • 21 slides
Key Concepts in AP Computer Science A Exam Review
Essential topics covered in AP Computer Science A Exam include identifiers, primitive data types, number representation, final variables, and arithmetic operators. Recognizing the basics, such as types, identifiers, operators, and control structures, is crucial for success in the exam. Understanding
0 views • 100 slides
Advancing Data Interoperability through DFIG Meeting Insights
Explore the key discussions and suggestions from a recent DFIG meeting chaired by Peter Wittenburg. Topics include addressing data heterogeneity, leveraging RDA for change, engaging with active groups, and proposing strategies for progress like defining data bundles and focusing on persistent identi
0 views • 10 slides
Challenges and Solutions in Research Information Systems
Research information systems face challenges in interoperability, data reusability, and organization. To address these, adopting standard metadata formats, authority files, and persistent identifiers is crucial. Implementing standard interfaces, data quality control, and certification are essential
0 views • 22 slides
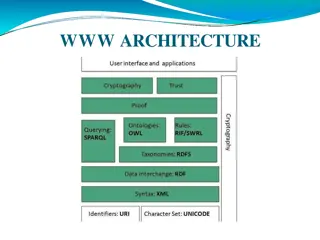
Understanding Web Technologies: From Identifiers to FTP
Explore the world of web technologies from identifiers and character sets to data interchange frameworks and ontologies like OWL. Learn about semantic web layers, cryptography, and FTP protocol objectives. Discover how these technologies work together to create a seamless online experience.
0 views • 72 slides
B2HANDLE: Managing Digital Object Identifiers for Data Persistence
B2HANDLE is a service for minting and managing persistent identifiers (PIDs) to facilitate common operations on digital objects across infrastructures. The system enables automated management of data objects and metadata, facilitates machine-driven workflows, and supports the construction of PID and
0 views • 17 slides
Understanding Persistent Identifiers (PIDs) and Handling Digital Objects
Explore the significance of Persistent Identifiers (PIDs) in assigning unique identifiers to digital objects, ensuring reproducibility, and facilitating reliable data management. Learn about versioning, PID binding, strategies for assigning PIDs, and the evolving role of repositories in managing dig
0 views • 6 slides
Understanding Persistent Identifiers (PIDs) in Research and Data Management
Persistent Identifiers (PIDs) play a crucial role in establishing long-lasting digital references for objects, contributors, and organizations in the realm of research and data management. This introduction delves into the significance of PIDs, focusing on their role in identifying and connecting di
0 views • 13 slides
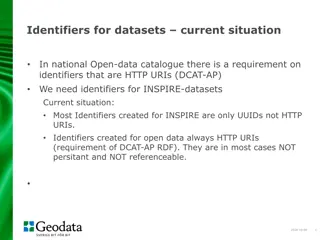
Recommendations for Creating Identifiers in Data Catalogues
National data catalogues have specific requirements for identifiers, such as using HTTP URIs for open data datasets. While most INSPIRE datasets only have UUID identifiers, adhering to the DCAT-AP standard recommends using HTTP URIs. Recommendations for creating identifiers in the geodata sector are
0 views • 5 slides
Understanding Data Modeling: Key Concepts and Applications
Explore the fundamentals of data modeling through concepts like entities, attributes, identifiers, and their real-world applications, including examples related to Greta Garbo, modeling reality, and global legal entity identifiers. Discover how to design data models for diverse scenarios, such as re
0 views • 57 slides
Piloting Unique Identifiers for Geospatial Data - Nordic Forum Presentation
Presentation at the Nordic Forum for Geography and Statistics on piloting unique identifiers for geospatial data by Tuuli Pihlajamaa. The agenda included terms used, background for the pilot, aims, results, and future plans. Detailed discussions on terms like URI, RDF, JHS 193, INSPIRE guidelines, a
0 views • 15 slides
Protecting Password Identifiers in IEEE 802.11-21
This submission addresses the need for safeguarding password identifiers in SAE to ensure privacy and prevent attackers from constructing personally identifiable information. The document presents two potential solutions, ultimately recommending the use of symmetric cryptography for efficient protec
0 views • 11 slides
Data Management, Curation, and Dissemination Strategies for Materials Science
Robert Hanisch, Director at the National Institute of Standards and Technology, discusses data management, curation, and dissemination strategies for materials science. The presentation covers topics such as bio sketches, the Office of Data and Informatics, standard reference data, and making the mo
0 views • 51 slides