Revisiting LDPC Rate Matching in IEEE 802.11 for Improved Performance
The document discusses revisiting LDPC rate matching in IEEE 802.11, focusing on issues such as performance loss compared to previous standards, power consumption in LDPC decoding/encoding, and over puncturing. It covers preliminary concepts, packet size distribution in various devices like laptops
2 views • 17 slides
Local Plan for Housing Delivery Strategy in Borough
The Local Plan for Housing Delivery in the borough outlines a comprehensive strategy focusing on spatial locations, land supply, and housing trajectory. It identifies strategic locations for growth, promotes intensification, and details land ownership distribution. The plan includes the development
3 views • 11 slides
Understanding the 3 Ts of Trauma: Trajectory, Treatment, and Trust
This comprehensive guide delves into the critical aspects of trauma - Trajectory, Treatment, and Trust. It covers the definition of trauma, PTSD symptoms, potentially traumatic events, trajectories of traumatic stress, and the impact of trauma on mental health. Explore the effects on behavior, biolo
0 views • 29 slides
Understanding Contact Tracing in Public Health
Contact tracing is a crucial process in public health aimed at identifying and monitoring individuals who have been in close contact with those infected with infectious diseases. It involves tracking and managing potential outbreaks, monitoring symptoms, and preventing further transmission. The hist
1 views • 15 slides
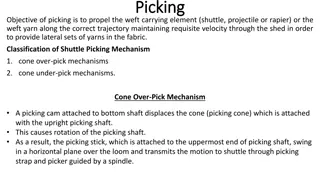
Understanding Shuttle Picking Mechanisms in Weaving
Shuttle picking mechanisms play a crucial role in propelling the weft carrying element to maintain the required trajectory and velocity in fabric weaving. Two common mechanisms are cone over-pick and cone under-pick, each offering unique adjustments for strength and timing. The cone over-pick involv
0 views • 14 slides
Tracing Requirements in Software Engineering
This chapter delves into requirements tracing, links, and dependencies in software engineering, emphasizing the importance of understanding and identifying necessary modifications to implement requirements changes. Motivations for tracing requirements, including finding missing or unnecessary requir
0 views • 10 slides
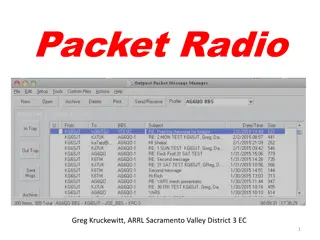
Understanding Packet Radio: A Comprehensive Guide
Packet radio, utilizing VHF FM technology, is a digital mode allowing keyboard-to-keyboard communication, messaging, mailboxes, bulletins, and more. It uses the AX.25 protocol and operates at varying data rates on VHF and HF bands. The system comprises basic stations and automated nodes, each requir
0 views • 20 slides
Overview of Fly and Trajectory Scans in Data Acquisition
Fly and trajectory scans in data acquisition involve software and hardware options for acquiring data while positioners move at constant speeds. Software fly scans enable periodic data acquisition triggered by software, while hardware fly scans rely on pulses from positioners. Hardware fly choices a
0 views • 14 slides
Enhancing Network Debugging with CherryPick in Software-Defined Datacenter Networks
Explore CherryPick, a technique for tracing packet trajectory in software-defined datacenter networks. It helps in debugging by ensuring data plane conforms with control plane policies, localizing network problems, and enabling packet trajectory tracing challenges like non-shortest paths. CherryPick
0 views • 14 slides
Trajectory Data Mining and Classification Overview
Dr. Yu Zheng, a leading researcher at Microsoft Research and Shanghai Jiao Tong University, delves into the paradigm of trajectory data mining, focusing on uncertainty, trajectory patterns, classification, privacy preservation, and outlier detection. The process involves segmenting trajectories, ext
0 views • 18 slides
Motion in a Uniform Electric Field Trajectory Analysis
Study the motion of a charge in a constant uniform electric field, deriving equations of motion, integrating for momentum and kinetic energy, using relativistic dynamics for velocity, and obtaining the trajectory in the XY plane. The trajectory is found to be a catenary shape when the velocity is mu
0 views • 10 slides
Understanding Internet Architecture and Networking Principles
The content explores the architecture and goals of the Internet, focusing on its original objectives, survivability in the face of failure, and evolving requirements. It delves into how networks function, describing behaviors and packet handling. Additionally, it discusses the framework for describi
0 views • 15 slides
Understanding the Impact of 1% Packet Loss on TCP and the Cubic Congestion Avoidance Algorithm
Delve into the surprising effects of even 1% packet loss on network flows, the methods TCP uses to mitigate loss, and how the CUBIC congestion avoidance algorithm works. Explore the researched but not quantified problem of packet loss and learn about a test methodology using Ubuntu hosts to measure
0 views • 24 slides
FY25 Title III Consortium Packet Overview
FY25 Title III Consortium Packet provides information on English Language Proficiency allocations, consortium formation, grant management, board approval requirements, and responsibilities of the lead fiscal agent. English Learner counts determine funding eligibility, with consortiums formed to reac
0 views • 15 slides
Creating a Repeat Pattern: Step-by-Step Guide for Tracing Designs
Learn how to make a repeat pattern by tracing designs on paper. Follow the steps provided to draw, trace, transfer, and enhance your patterns for a polished finish. No tracing paper? No problem! Find out alternative methods to achieve the same results without tracing paper.
0 views • 7 slides
Career Development and Funding Trajectory in LMIC-based Global Health Model
Kelika A. Konda, MHS, PhD, shares her career trajectory from Masters to Doctorate, Post-doc, and beyond, focusing on teaching, mentoring, and hosting global health programs. She discusses funding trajectories, creative ways to fund research projects, and highlights her assets in LMIC study populatio
0 views • 7 slides
Kelika A. Konda, PhD, MHS - Career Trajectory and Achievements
Dr. Kelika A. Konda, an Associate Professor at UCLA and Associate Researcher at UPCH, shares her career trajectory from obtaining a BA in environmental health to pursuing an MHS and PhD. She highlights her experiences with Peace Corps, Johns Hopkins, NIH funding, and post-doctoral work in global hea
0 views • 15 slides
Understanding Ray Tracing in Computer Graphics
In the world of computer graphics, ray tracing plays a crucial role in rendering realistic images by simulating the behavior of light rays in a scene. This involves determining visibility, casting rays from a viewpoint, implementing ray tracing algorithms, computing viewing rays, calculating interse
0 views • 20 slides
Bandwidth and Packet Type Detection Schemes for 40-50GHz Millimeter Wave Communication Systems
The document discusses bandwidth and packet type detection schemes for 40-50GHz millimeter wave communication systems in IEEE 802.11aj specifications. It proposes a preamble design for auto-detection of bandwidth and packet type to improve channel estimation and decoding efficiency. By utilizing dif
0 views • 27 slides
Understanding Ray Tracing Techniques in Computer Graphics
Explore the fundamentals of ray tracing, including concepts like intersections, speedups, fewer intersections strategies, object bounding hierarchies, and space partitioning methods for efficient rendering. Learn about bounding spheres, AABBs, OBBs, K-DOPs, uniform grids, BSP trees, and octrees in t
0 views • 30 slides
Understanding Ray Tracing Techniques in Computer Graphics
Explore the fundamentals of ray tracing including recursive ray casting, ray casting vs. ray tracing, basic algorithms, shadows, reflections, refractions, and advanced illumination models like Whitted model and OpenGL's illumination model. Learn about casting rays from the eye, handling reflections
0 views • 50 slides
Transforming Substance Use and Depression Trajectory in Virginia
Patty Ferssizidis, PhD, as the VA-SBIRT Project Manager at George Mason University, is spearheading efforts to alter the trajectory of substance use and depression in Virginia. The SBIRT model is being utilized to screen, identify, intervene, and connect individuals with substance use risks to appro
0 views • 20 slides
Enhancing Network Security Through Multi-Core Packet Scattering and Deep Packet Inspection
Explore the use of multi-core systems to tackle performance bottlenecks in network intrusion detection systems, specifically focusing on deep packet inspection. Techniques such as load balancing and pattern subset scanning are discussed to optimize DPI processes and improve overall network security
0 views • 43 slides
Trajectory Data Mining: Overview and Applications
Spatial trajectories represent moving objects in geographical spaces with examples from human mobility, transportation vehicles, animals, and natural phenomena. Sources of trajectory data include human mobility records, active/passive recordings, and sensor data. The paradigm of trajectory data mini
0 views • 8 slides
National COVID-19 Contact Tracing Fundamentals and Operations Overview
The document provides detailed information on the structure and operations of the national COVID-19 contact tracing in England, involving Tier 1, Tier 2, and Tier 3 contact tracing levels. It covers topics such as the role of different tiers, escalation criteria, infectious and incubation periods of
0 views • 15 slides
Recent Developments in English Law of Tracing & Unjust Enrichment
Recent decisions in English law show a shift in tracing & unjust enrichment practices. Cases like Brazil v. Durant and Bank of Cyprus v. Menelaou indicate a move towards a looser causal connection requirement. The discussion on backwards tracing and unjust enrichment has evolved from the Court of Ap
0 views • 18 slides
Exploring the Evolution of Data Communications: A Brief Overview
Delve into the progression of data communications from Morse code to modern radio email systems like Winlink. Discover the history of protocols, technologies, and the impact of the internet on amateur packet radio. Unravel the development of ARQ data protocols, X.25 packet switching, and the transit
0 views • 51 slides
Benefits of Transitioning to Trajectory-Based Operations (TBO)
Explore the operational benefits of Trajectory-Based Operations (TBO) in modernizing the ATM system, endorsed by IATA as the core of ICAO's Global ATM Operational Concept. Learn about performance improvement opportunities and the long-term advantages of integrating TBO into aviation operations.
0 views • 4 slides
Benefits of Trajectory-Based Operations for Military Aircraft
Trajectory-Based Operations (TBO) offer numerous benefits for military aircraft, including flexibility, efficiency, predictability, safety, and cost savings. TBO allows customized trajectories to meet unique operational requirements, reduces fuel consumption and emissions, enhances airspace usage, a
0 views • 7 slides
Efficient Parallelization Techniques for GPU Ray Tracing
Dive into the world of real-time ray tracing with part 2 of this series, focusing on parallelizing your ray tracer for optimal performance. Explore the essentials needed before GPU ray tracing, handle materials, textures, and mesh files efficiently, and understand the complexities of rendering trian
0 views • 159 slides
Understanding the Basics of Packet Radio for Amateur Communication
Explore the world of packet radio, a digital mode used by amateur radio operators to build wireless computer networks. Learn about its benefits, how it works using the AX.25 protocol, making connections, advantages such as error checking, and building a packet station with the necessary components.
0 views • 19 slides
Understanding Asynchronous Transfer Mode (ATM) in Data and Computer Communications
Asynchronous Transfer Mode (ATM) is a packet transfer technology that supports multiple logical connections over a single physical interface. It uses fixed-sized packets called cells for data transfer. ATM bears similarities to packet switching and offers streamlined packet transfer with minimal err
0 views • 46 slides
Understanding Ray Tracing in Computer Graphics
Explore the fascinating world of ray tracing in computer graphics through this comprehensive lecture series. From creating realism with effects like shadows, reflections, and transparency to delving into the history and evolution of ray tracing, this content covers it all. Discover the different app
0 views • 46 slides
Tracing in Animal Disease Control: Guidelines and Procedures
This presentation delves into the importance of tracing in animal disease control, covering trace-back and trace-forward methods, sources of information, collaboration services, and the role of livestock owners. It highlights the guidelines and operational procedures adapted from FAD PReP/NAHEMS, fo
0 views • 27 slides
Understanding SDN Switch Code Tracing Process
This content delves into the intricate process of tracing code within SDN switches. It covers topics such as the first packet handling, LLDP communication, flow table operations, and controller interactions. Through detailed images and descriptions, readers gain insight into the functionalities and
0 views • 14 slides
Re-Animator: Versatile System Call Tracing and Replaying
Re-Animator is a research project focusing on creating a high-fidelity system call capturing system with minimized overheads. The project aims to capture long-running applications and provide scalable and verifiable system call replaying. It introduces two prototype system call tracing systems and h
0 views • 39 slides
Enhancing Data Center Network Performance through Packet Scheduling and ECN
Explore the advancements in data center network performance improvement through techniques like packet scheduling, Explicit Congestion Notification (ECN), and strict priority for different types of flows. The research discusses the requirements of low latency for short messages and high throughput f
0 views • 48 slides
Understanding Wireshark Filters for Efficient Packet Analysis
Learn how to leverage Wireshark capture filters to customize packet analysis, enhance traffic visibility, and optimize network monitoring. Capture only the data you need, create custom filters, and streamline intrusion detection analysis with Berkeley Packet Filters (BPF). Discover the power of disp
0 views • 17 slides
Considerations on PHY Padding and Packet Extension in 11ax
The document discusses the proposed PHY padding and packet extension for IEEE 802.11ax, focusing on considerations for processing data within SIFS duration and relaxation of LDPC decoding processing time. It outlines the overview of the proposed padding scheme, considerations for LDPC implementation
0 views • 15 slides
Innovative Application Packet for ACE Solutions - Explore the Visual Journey
Dive into the visually captivating world of ACE Solutions with their cutting-edge application packet. From stunning visuals to advanced functionality, this packet showcases the power and versatility of ACE Solutions for modern applications. Discover the seamless navigation, engaging content, and ric
0 views • 59 slides