Understanding Computer Organization and Architecture
A computer system is a programmable digital electronics device that processes data as per program instructions to provide meaningful output. It comprises hardware and software components, with hardware being the physical parts and software essential for driving the hardware. Computer organization fo
14 views • 71 slides
Evolution of IBM System/360 Architecture and Instruction Set Architectures
The IBM System/360 (S/360) mainframe computer system family, introduced in 1964, revolutionized computing by offering forward and backward compatibility, a unified instruction set architecture (ISA), and a balance between scientific and business efficiency. The critical elements of this architecture
1 views • 18 slides
Understanding P&IDs and Symbols in Process Engineering
An insightful primer on P&IDs and symbols for students unfamiliar with EMEC125 and EMEC130 courses. The article delves into the definition of P&IDs as schematic diagrams illustrating the relationship between instruments, controllers, piping, and equipment. It explores the widely understood acronym "
1 views • 32 slides
MIPS CPU Design Using Verilog and Instruction Set Architecture Overview
Explore the world of MIPS CPU design using Verilog with a deep dive into Instruction Set Architecture (ISA), SPIM instruction formats, addressing modes, and more. Learn about the key components such as Program Counter (PC), Instruction Memory (IM), Register Files (RF), Arithmetic Logic Unit (ALU), D
1 views • 29 slides
Unit 4: Non-Examination Assessment Overview
The Unit 4 Non-Examination Assessment from 2017 focuses on working as a historian, with tasks including source evaluation and discussion of different historical interpretations. The assessment is marked out of 40 and is worth 20% of the qualification. It assesses knowledge, understanding, source ana
1 views • 14 slides
Texas Senate Bill 792: Disabled Parking Requirements and Penalties
Texas Senate Bill 792, effective January 1, 2022, outlines the requirements for parking in disabled spaces, including the need for a disabled person license plate or a placard featuring the International Symbol of Access (ISA). Veterans with Disabled Veteran plates must also meet specific criteria t
1 views • 10 slides
Understanding Instruction Set Architecture and Data Types in Computer Systems
In computer architecture, the Instruction Set Architecture (ISA) level is crucial in defining how a processor executes instructions. This includes the formal defining documents, memory models, registers, and various data types that can be supported. The ISA level specifies the capabilities of a proc
2 views • 13 slides
IBM System/360 Architecture Evolution
The IBM System/360 (S/360) mainframe computer system family, introduced in 1964, revolutionized computing with its forward and backward compatibility, ISA family concept, and efficient integration of scientific and business applications. The critical elements, including compatibility design consider
0 views • 18 slides
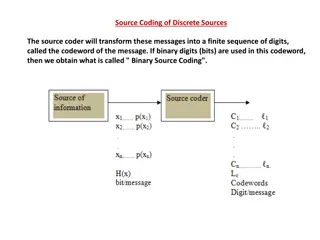
Understanding Source Coding for Discrete Sources
Source coding involves transforming messages into codewords, with considerations for minimizing code length and ensuring unique decodability. Binary source coding and efficiency are key concepts explored in this process. Check out the details and examples provided to deepen your understanding of sou
0 views • 14 slides
Uncovering Business Models for Linked Government Data
Delve into the exploration of business models for linked government data through a comprehensive study under the European Commission's ISA Programme. Discover key stakeholders, methodologies like the Business Model Canvas, case studies, and the potential value of Linked Open Government Data. Uncover
0 views • 19 slides
Evaluation of Source Usefulness through Multiple Criteria
In this evaluation task, you will assess the effectiveness of questions based on various criteria such as authorship, type of source, purpose, and relevance of information. By carefully analyzing the source content and rubric, you will provide an overall judgment on the source's utility while evalua
3 views • 10 slides
Miracles of Prophets: Divine Wonders and Prophetic Signs
Explore the profound significance of miracles in Islam, showcasing the extraordinary events granted by Allah to His Prophets as a testament to their truthfulness and divine approval. Delve into the greatest miracle, the Holy Quran, which offers unparalleled knowledge and insight into the miraculous
2 views • 36 slides
Exploring Source-Routed Forwarding in SDN-Based WANs
Software-Defined Networking (SDN) in Wide Area Networks (WANs) utilizes source routing methods to address performance concerns related to network convergence time. Challenges such as latency constraints and controller placement impact performance, highlighting the need for efficient path computation
0 views • 24 slides
Customize Your Game with Slot Machine Source Code
Customize your game with slot machine source code and enhance its features. Discover how using customizable source code can help you build engaging and profitable slot machine games.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 5 slides
Understanding RISC, CISC, and ISA Variations in Computer Science
Explore the differences between RISC and CISC architectures, along with variations in Instruction Set Architecture (ISA). Dive into the intricacies of processor design, performance factors, and assembly languages. Get insights into the concepts of control units, memory units, pipelines, and datapath
0 views • 37 slides
Variations in Computer Architectures: RISC, CISC, and ISA Explained
Delve into the realm of computer architectures with a detailed exploration of Reduced Instruction Set Computing (RISC), Complex Instruction Set Computing (CISC), and Instruction Set Architecture (ISA) variations explained by Prof. Kavita Bala and Prof. Hakim Weatherspoon at Cornell University. Explo
0 views • 55 slides
Exploring Challenges and Opportunities in Processing-in-Memory Architecture
PIM technology aims to enhance performance by moving computation closer to memory, improving bandwidth, latency, and energy efficiency. Despite initial setbacks, new strategies focus on cost-effectiveness, programming models, and overcoming implementation challenges. A new direction proposes intuiti
0 views • 43 slides
Practical Implementation of Embedded Shadow Page Tables for Cross-ISA System Virtual Machines
This research focuses on the practical implementation and efficient management of embedded shadow page tables for cross-ISA system virtual machines. It discusses the framework, evaluation, and conclusions regarding system virtualization, particularly addressing memory virtualization overhead and opt
0 views • 33 slides
Contrast and Development in "Men Should Weep" Act Three
Act Three of "Men Should Weep" by Ena Lamont Stewart portrays a contrast in atmosphere from the start of the act, characterized by a cheerier and more positive ambiance. It delves into complex family dynamics, plot strands, and character developments that culminate in a climactic resolution, offerin
0 views • 39 slides
Laplacian Deformation in Engineering and Applied Science
Laplacian deformation is a technique used in non-rigid registration to account for shape variance and improve fitting between source and target shapes. This method involves minimizing the distance and distortion terms to achieve accurate alignment. Intrinsic and extrinsic methods are discussed, wher
0 views • 53 slides
Understanding Unit Cost and the Trunk Formula Technique
Explore the Trunk Formula Technique (TFT) for calculating unit cost based on trunk area, functional limitations, and external considerations. Learn about Basic Reproduction Cost, LCANT, and selecting Unit Cost for various scenarios and regions like ISA Ontario and PNW Chapter.
0 views • 39 slides
Introduction to Y86 Instruction Set Architecture
Y86 Instruction Set Architecture is a simplified pseudo-language based on x86 (IA-32) architecture. It involves implementing the Fetch-Decode-Execute cycle, where instructions are fetched from memory, decoded, and executed. The Y86 ISA offers a simpler set of instructions and formats compared to x86
0 views • 25 slides
Understanding Computer Organization: Instruction Set Architecture and Interrupts
Explore the critical concepts of Computer Organization focusing on Instruction Set Architecture (ISA) and Interrupts. ISA serves as the interface between hardware and software, enabling programmers to write machine language programs effectively. Learn about Application Binary Interface (ABI), interr
0 views • 26 slides
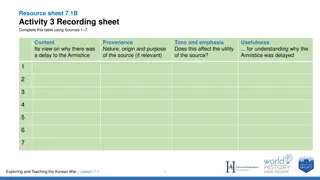
Understanding Delay in the Korean Armistice Negotiations
Sources 1 to 4 provide insights into the reasons behind the delay in reaching an armistice during the Korean War. Source 1 discusses the POW question's impact, Source 2 presents Eisenhower's stance on peace efforts, Source 3 outlines Syngmam Rhee's opposition to a divided Korea, and Source 4 reflect
0 views • 9 slides
The Impact of Open Source Library Automation Systems
Marshall Breeding discusses the rise of open source library automation systems globally, comparing them to proprietary alternatives. He explores the adoption of open source products in the US and their coverage in international library reports, highlighting how libraries of different budgets utilize
0 views • 38 slides
Understanding X86 ISA Flags in System Security
This article delves into the details of various flags in the X86 ISA architecture, such as CF (Carry Flag), PF (Parity Flag), AF (Auxiliary Flag), ZF (Zero Flag), SF (Sign Flag), TF (Trace Flag), IF (Interrupt Flag), DF (Direction Flag), OF (Overflow Flag), and IOPL (Input Output Privilege Level). T
0 views • 16 slides
Overview of Off-Site Source Recovery Program Capabilities
The Off-Site Source Recovery Program (OSRP) aids in recovering radioactive sealed sources for national security and public health. OSRP focuses on recovering TRU and non-TRU sources, with over 38,500 sources retrieved globally. Services include source registration, consultancy, and training for vari
0 views • 25 slides
Exploring HiAP Implementation for Health Equity
This content explores the implementation of Health in All Policies (HiAP) at local, regional, and global levels, discussing challenges, examples, key results, and conceptual frameworks towards achieving health equity. Various studies and training sessions conducted by WHO and PAHO in collaboration w
0 views • 27 slides
Implementation of RISC-V in Protium: Overview and Analysis
RISC-V, a royalty-free open-source Instruction Set Architecture (ISA), has gained popularity since its inception in 2010. This article delves into the historical background, extensions, integer registers, and the Pulp platform's RISC-V cores. The implementation of RISC-V in Protium is discussed, pro
0 views • 13 slides
Awareness and Use of Open Source Software Among Library Professionals in Bangalore City
This study presented by Podili Anjaneyulu, Kaviha B, Sreya Gopinath, and K.G. Jayarama Naik from Bangalore University focuses on identifying the awareness and usage of open source software among library professionals in Bangalore. The study explores different open source software available for libra
0 views • 18 slides
Understanding Instrument Air Quality Standards in Industrial Applications
TESCORP, based in Tulsa, Oklahoma, specializes in distributing, fabricating, and servicing compression systems globally. Instrument air quality standards are crucial for pneumatic instruments in various industries. ANSI/ISA 7.0.0.1996 sets the standard for instrument air quality, focusing on pressur
0 views • 17 slides
Understanding the Characters and Themes in "Men Should Weep" by Ena Lamont Stewart
The introduction to the play "Men Should Weep" by Ena Lamont Stewart sets the stage for a tumultuous story as Alec and Isa arrive to stay with John and Maggie after a tragic event. The dynamics between the characters, particularly Alec, Jenny, and the rest of the family, reveal layers of complex rel
0 views • 7 slides
The Life of Sayyidatuna Maryam (alayhassalam) in Islam
Sayyidatuna Maryam (alayhassalam) is renowned in Islam for her piety, purity, and devotion to Allah. Born into the noble family of `Imran, she was granted the honor of being the mother of Prophet `Isa (Jesus). Her miraculous birth and upbringing under Prophet Zakariyyah (alayhissalam) highlight her
0 views • 10 slides
Why Slot Machine Source Code is Key to Fast-Track Game Development
Discover why slot machine source code is essential for fast-tracking game development. Learn how slot machine scripts, PHP slot machine source code, and online casino script full source code free can save time and boost efficiency.\n\nSource>>\/\/ \/
0 views • 4 slides
Understanding Fund-Source Pairings in ConnectCarolina Chartfields
Explore the Fund-Source pairings in the new ConnectCarolina chartfield structure. Learn how to avoid errors by correctly matching Funds and Sources, and understand the interaction between Fund, Source, and Department. Gain insight into the major fund groups and their specific Source ranges for effic
0 views • 17 slides
OpenACC Compiler for CUDA: A Source-to-Source Implementation
An open-source OpenACC compiler designed for NVIDIA GPUs using a source-to-source approach allows for detailed machine-specific optimizations through the mature CUDA compiler. The compiler targets C as the language and leverages the CUDA API, facilitating the generation of executable files.
0 views • 28 slides
Create Profitable Casino Games with Expert Slot Machine Source Code
Develop successful games with Slot Machine Source Code, php slot machine source code, slot game script, and slot machine script for gaming industries and businesses.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 3 slides
Boost Your Game’s Success with Our Reliable Slot Machine Source Code
Discover premium Slot Machine Source Code to build engaging games. Explore reliable source code slot machine options for ultimate success.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 4 slides
Maximize Efficiency_ How Slot Machine Source Code Makes Updates a Breeze
Simplify updates and customization with slot machine source code. Perfect for casino slot game source code, slot game script, and iGaming innovation. Contact AIS Technolabs.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 5 slides
Unraveling the Mystery of Slot Machine Source Code_ A Developer’s Guide
Learn the intricacies of slot machine source code to develop captivating games. Explore source code slot machine insights with this comprehensive guide.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 4 slides